Method for optimizing performance of encryption card based on DEVICE MAPPER
An encryption card and encryption algorithm technology, applied in the protection of internal/peripheral computer components, instruments, electrical digital data processing, etc., to achieve the effects of saving CPU time, increasing speed, and reasonable design
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] A DEVICE MAPPER-based encryption card performance optimization method of the present invention will be described in detail below in conjunction with the accompanying drawings.
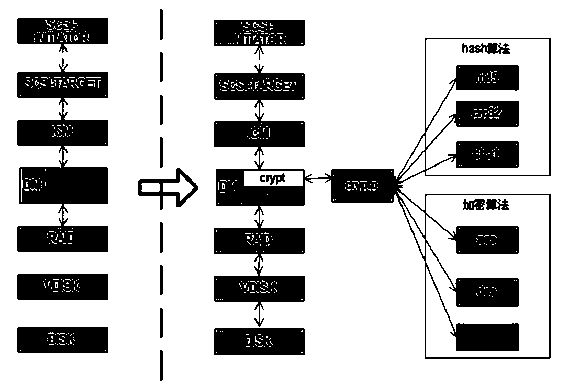
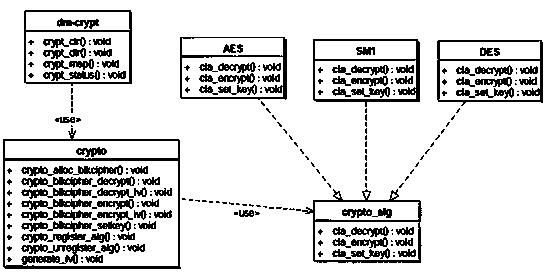
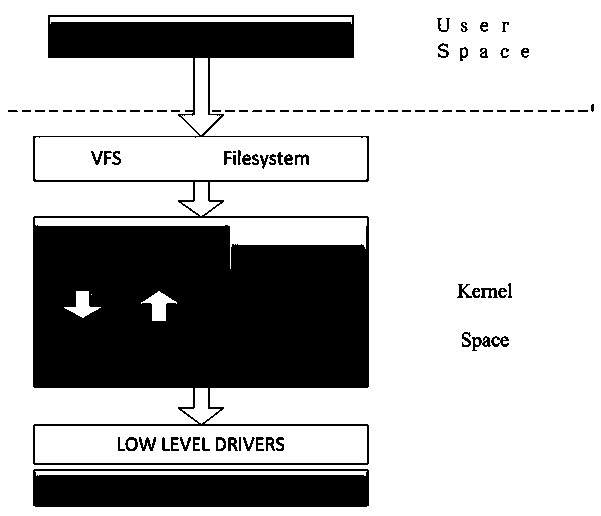
[0018] Such as Figure 1-4 As shown, a method for optimizing the performance of an encryption card based on DEVICE MAPPER of the present invention, the API of the encryption card in its structure is integrated into the general block device kernel framework of Device Mapper to realize the dm-crypt encryption block device suitable for the encryption card Module, which in turn can create an encrypted file system to protect confidential data at the disk storage level;
[0019] The encryption block device module adopts the synchronous block encryption and asynchronous block encryption of the domestic encryption algorithm sm1, and provides a method for registering the sm1 algorithm to the kernel password manager.
[0020] By adding modules suitable for encryption card drivers to the Device Mapper ker...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com