Carrier-free text steganography method based on character features
A carrierless and text-free technology, applied in the field of information hiding, to avoid distortion and increase the effect of applicable scenarios
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
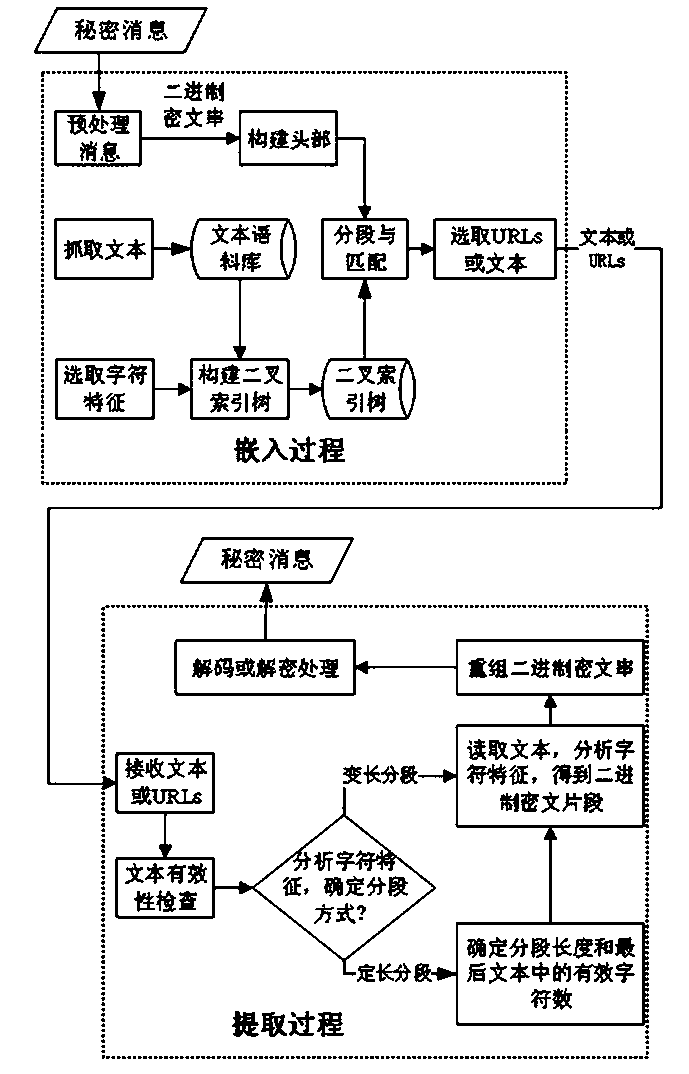
[0028] Such as figure 1 As shown, this method is divided into two parts, the embedding process and the extraction process. The specific process is as follows:
[0029] 1. Embedding process, including the following steps:
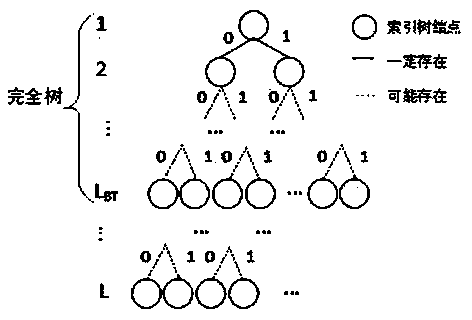
[0030] 1) Select the character features and encode the character features. There are many selections of character features, such as the number of character strokes and structure. Here, taking the parity feature of the number of strokes of a character as an example, an even number of strokes represents "0", and an odd number of strokes represents "1".
[0031] 2) Grab Internet text and create a large data corpus of web text. Crawl webpages through web crawlers and other methods, parse out the text or obtain texts in other ways, and build a general web text corpus; you can also get topic-related texts based on hobbies, topics, etc., and build a special text corpus. The corpus should at least contain the content of the text itself and its corresponding URL ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com