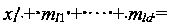Method for computing low-entropy universal high-order masks based on composite field
A calculation method and composite domain technology, applied in the field of masking schemes, can solve problems such as inability to realize high-order masks, large resources, complex algorithms, etc., and achieve the effect of reducing hardware implementation area, cost, and hardware resource occupancy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] A method for calculating a low-entropy general-purpose high-order mask based on a compound domain, the method comprising the following steps:
[0040] (1) Enter the masked value , the mask value
[0041] in: represents the sensitive variable, Indicates the input random mask value;
[0042] (2) Through isomorphic matrix will finite field The input values on map to the finite field superior;
[0043] (3) Will the finite field The inverse operation on transforms into a finite field Addition, multiplication, and inverse operations on
[0044] (4) Obtain The mask protection value of ;
[0045] (5) In finite fields upper pair Perform mask inversion, the inversion result is ;
[0046] (6) Obtain , mask protection value;
[0047] (7) Through the isomorphic inverse matrix , the finite field The inverse result on is mapped back to the finite field, and the finite field is obtained Inverse result .
[0048] will finite field The...
Embodiment 2
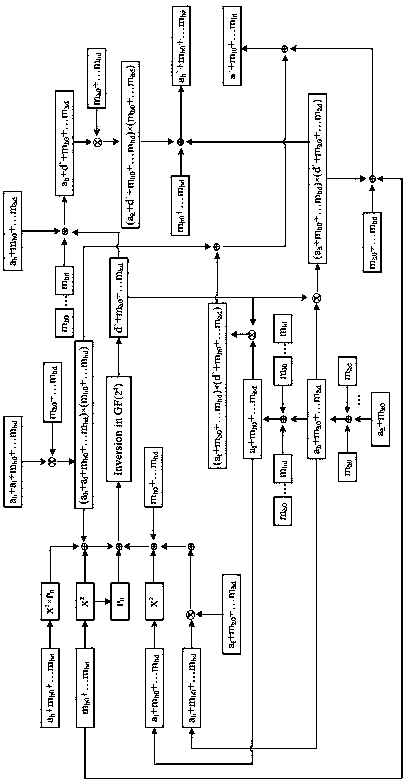
[0064] According to the calculation method of the low-entropy general-purpose high-order mask based on the compound domain described in Example 1, the calculation method is applied to AES, and the second-order mask algorithm of AES S-box is given in this paper, with two random masks value, the specific process of the algorithm is as follows: First, apply Algorithm 2, take n=4, in the finite field GF(2 8 ) to select two random mask values, the finite field GF(2 8 ) is the domain GF(2 4 ), the finite field GF(2 8 ) on the input and mask values are mapped to the field GF(2 4 ), use the domain GF(2 4 ) instead of the finite field GF(2 8 ) on the calculation (usually called the finite field algorithm), reducing the complexity of hardware implementation. Follow the steps of Algorithm 2 to execute the intermediate value d.
[0065] Second, the domain GF(2 4 ) to find the inverse of the middle value d, take n=1, and set the field GF(2 4 ) on the input unit is mapped to the f...
Embodiment 3
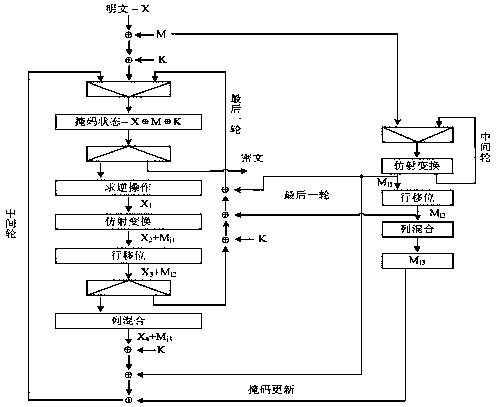
[0082] AES low-entropy high-order mask hardware implementation process is as follows figure 1 As shown, there are mainly two parts, one is the mask update module, and the other is the mask AES data path. Compared with non-masked AES, the masked AES algorithm data path is more complicated, and it is necessary to ensure that all intermediate values are masked. Therefore, when designing the entire AES algorithm hardware architecture, each module must add a mask, and the mask value of each round is different, so as to ensure the security of the algorithm. figure 1 The meaning of the mask correction module on the right is to update the mask for each round to ensure that the mask value of each round is different. exist figure 1 Where X represents the plaintext, M represents the initial mask value, K represents the key value, Xi and Mi are the intermediate results of the plaintext data and the mask update value, respectively, and Cipher out is the output of the ciphertext.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com