Secure key signature method based on block chain technology
A blockchain and security technology, applied in the blockchain field, can solve problems such as reduced security, low security, unfavorable automatic operation and maintenance of the system, and achieve the effect of protecting security, improving security, and realizing automatic operation and maintenance management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The specific embodiments of the present invention will be further described below in conjunction with the accompanying drawings.
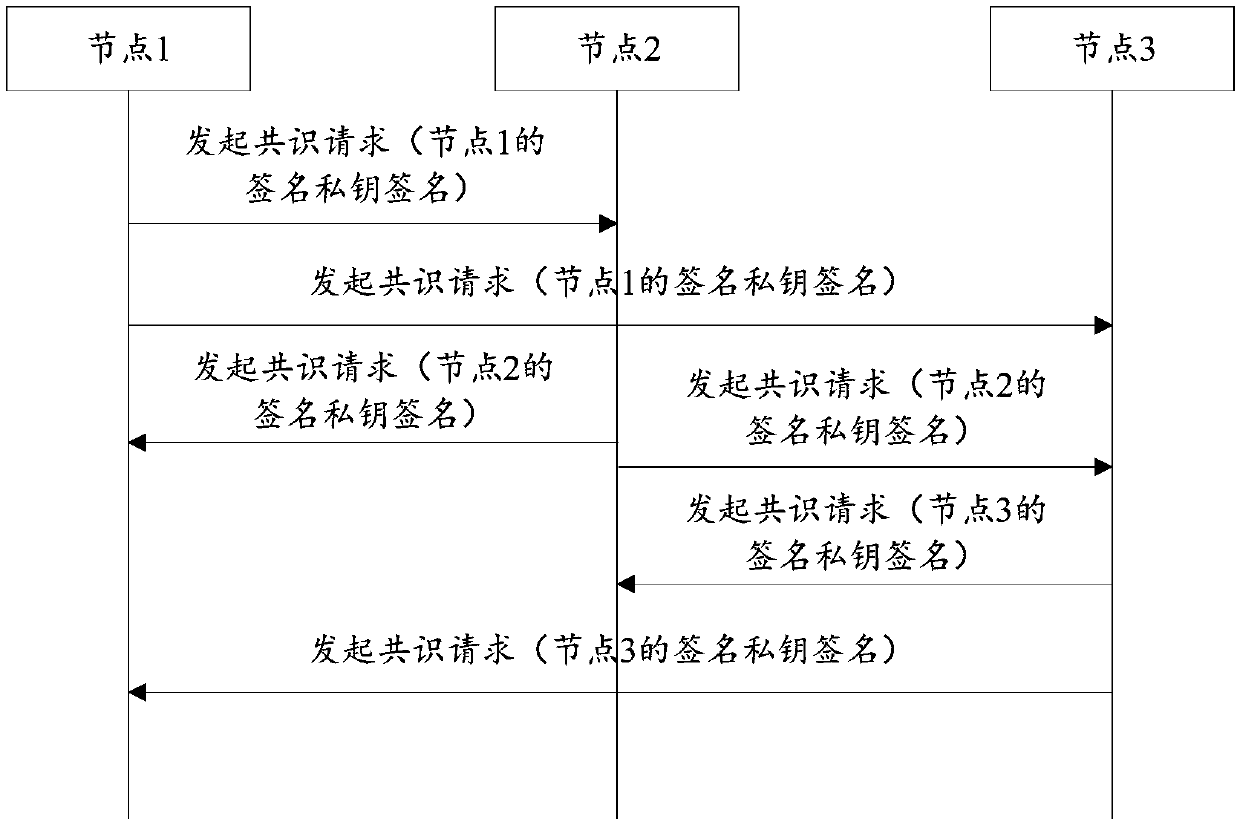
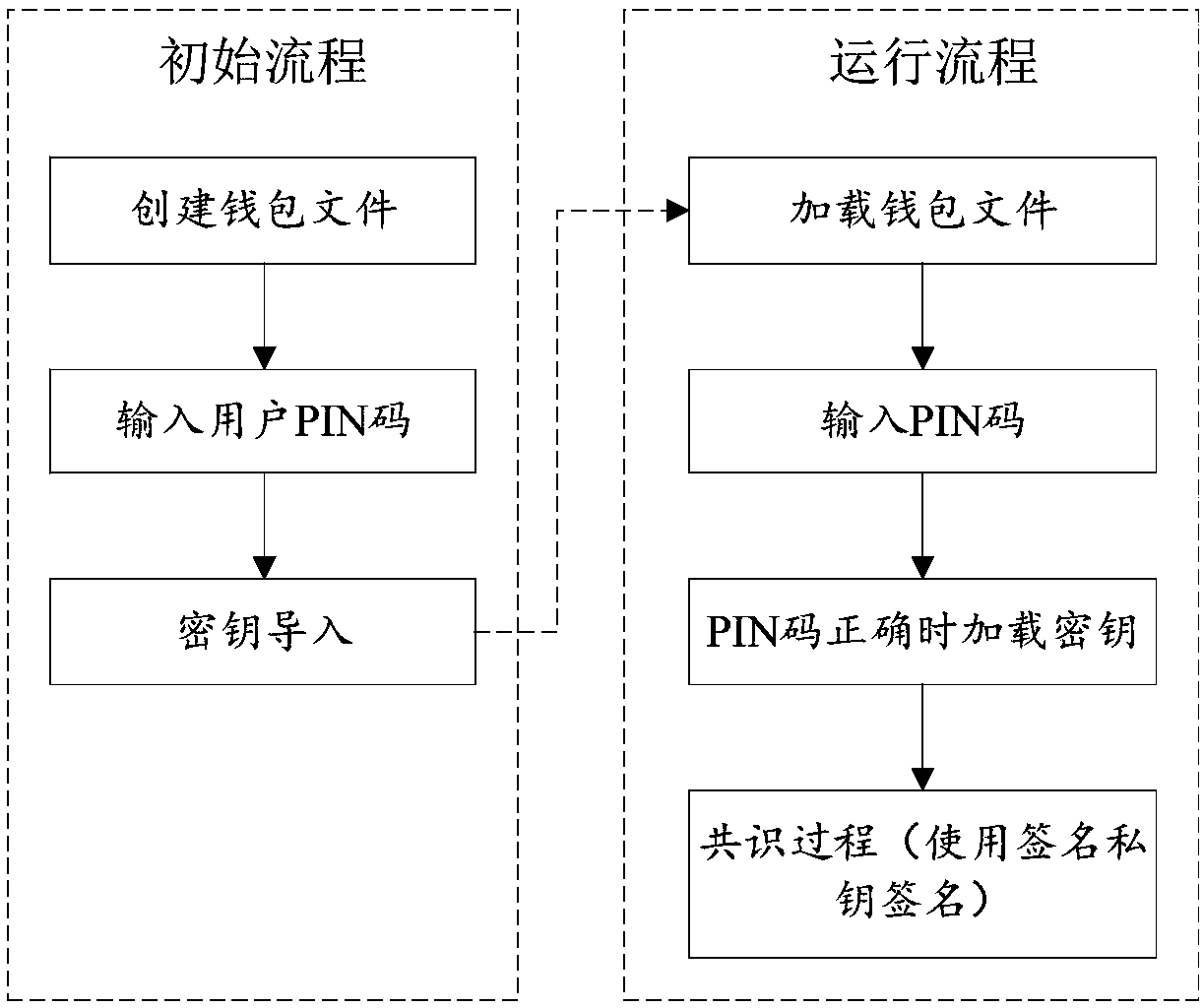
[0038] This application discloses a key security signature method based on blockchain technology. The method is used in a blockchain system. The blockchain system includes several nodes, usually at least three, and each node communicates with each other in pairs. Establish a communication connection. The nodes here can be various devices such as computers, servers, workstations, and printers. This method can be executed by any node in the blockchain system. This method mainly includes key import and key application. part.
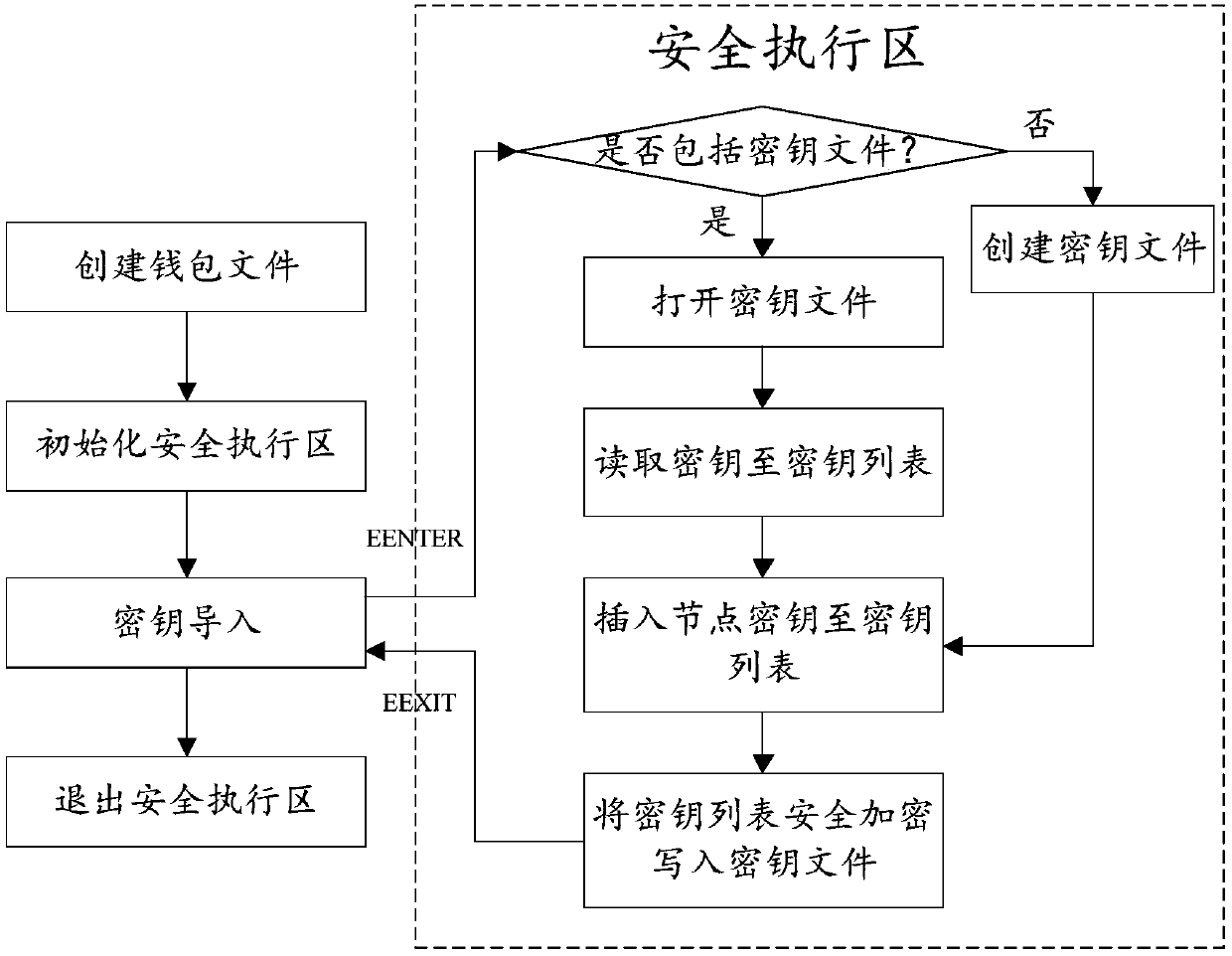
[0039] The first part is to execute the key import part when deploying the blockchain system on the node for the first time. This part includes the following steps, such as image 3 Shown:
[0040] First, create a wallet file. The wallet file includes at least the node key. The wallet file usually includes the wallet ad...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com