User access path prediction method
A technology of access paths and prediction methods, applied in special data processing applications, instruments, website content management, etc., can solve problems such as the exponential increase in the number of codes and the long length of binary position codes.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0044] Now do data preprocessing on a certain log file to get the user's access sequence set, as shown in the second column of Table 1, here specify the minimum support threshold λ=0.75, where a, b, c, d, e, f Represents the pages requested by the user, and the access sequence from left to right represents the sequence of pages requested by the user in chronological order.
[0045] Table 1 User Access Sequence Set with λ=0.75
[0046]
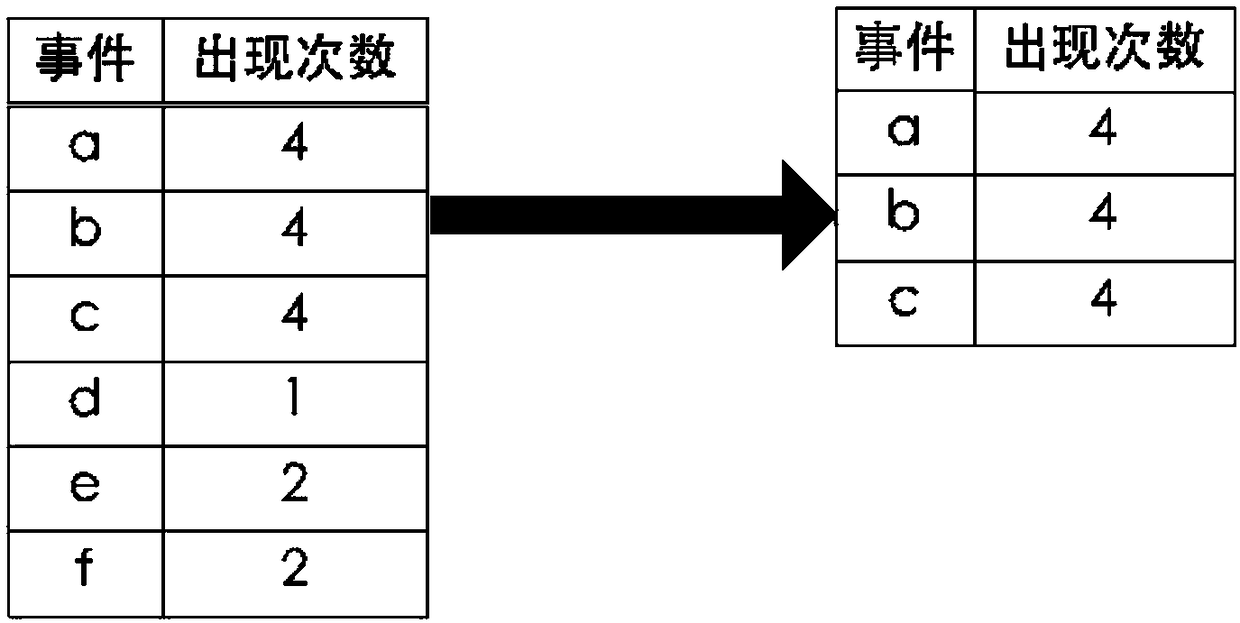
[0047] First, get the frequent access sequence set: scan the access sequence set, and count the number of occurrences of each access page in the access sequence set, such as image 3 shown on the left. Since the minimum support threshold λ=0.75, only when the number of times is greater than or equal to the minimum support threshold * the number of access sequence sets (4*0.75, that is, 3) can be regarded as frequent items (or frequent access pages), delete non- Frequent items, to obtain frequently accessed sequence sets, such as image 3 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com