Identity authentication method, electronic apparatus and computer readable storage medium
An identity authentication and ID card technology, applied in the fields of identity authentication methods, electronic devices and computer-readable storage media, to achieve the effect of improving accuracy and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
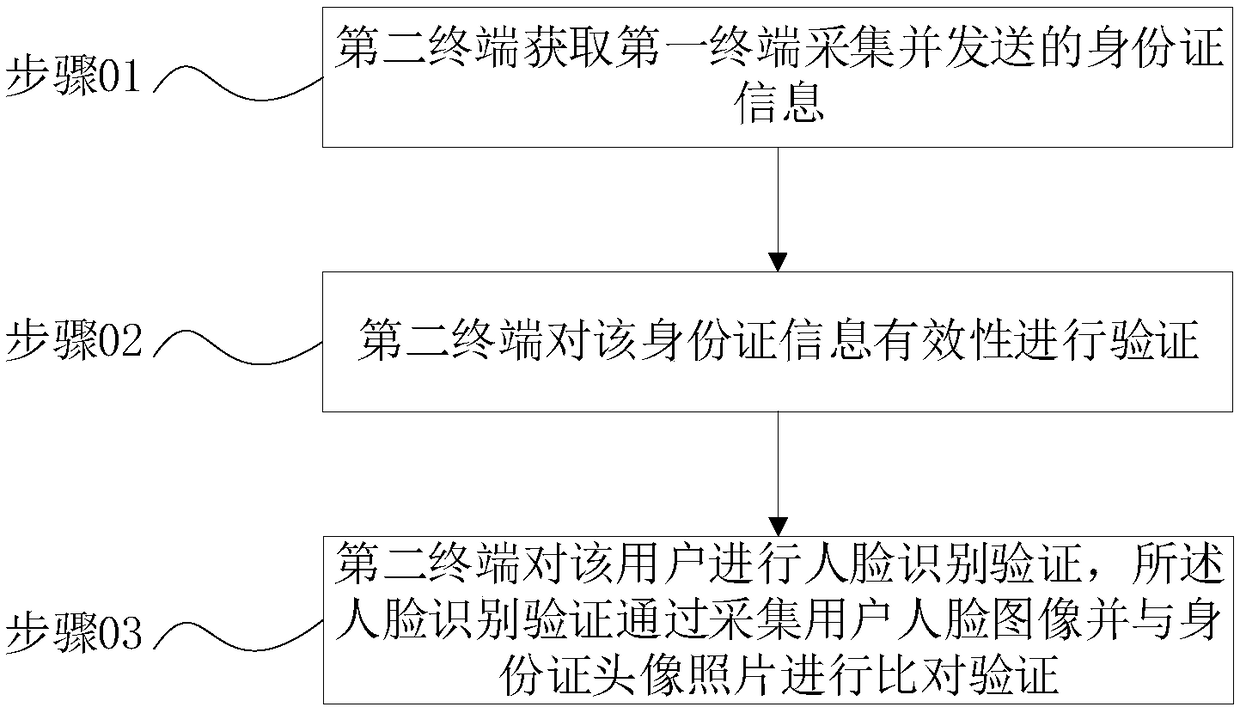
[0030] Refer to figure 1 , Shows an identity authentication method, including the following steps:
[0031] Step 01: The second terminal obtains ID card information collected and sent by the first terminal.
[0032] The user sends a service request to the second terminal through the first terminal. After receiving the request, the second terminal sends an identity verification instruction to the first terminal. After receiving the instruction, the first terminal turns on the ID card authenticator at the first terminal , And give the user text and voice operation instructions on the first terminal interface, including reminding the user to place the ID card in the designated area, and adjust the brightness of the client and other collection parameters, and the authenticator scans the ID card to extract the avatar on the ID card Photos, ID card number information, and de-texture the avatar photo, send the processed photo and ID card number information to the file server of the first ...
Embodiment 2
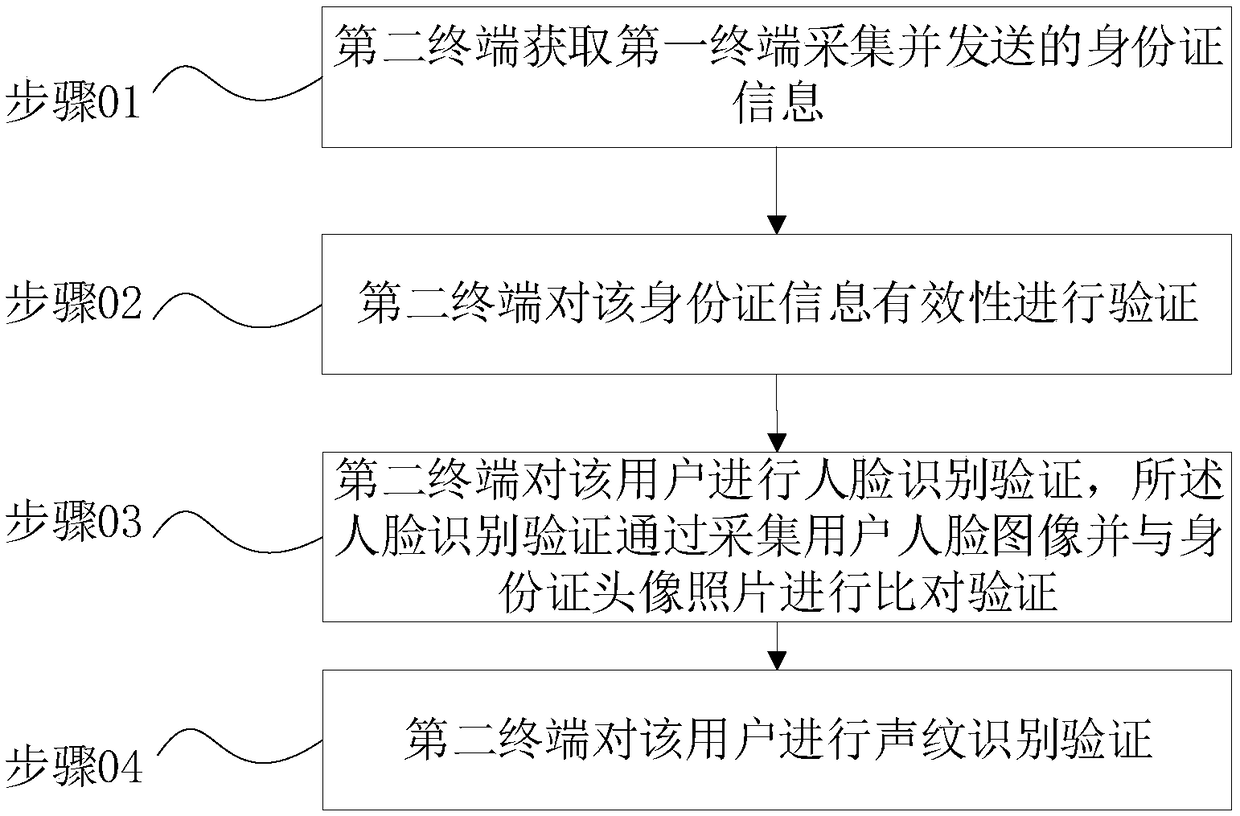
[0044] Refer to figure 2 , Shows an identity authentication method, including the following steps:
[0045] Step 01: The second terminal obtains ID card information collected and sent by the first terminal.
[0046] The user sends a service request to the second terminal through the first terminal. After receiving the request, the second terminal sends an identity verification instruction to the first terminal. After receiving the instruction, the first terminal turns on the ID card authenticator at the first terminal , And give the user text and voice operation instructions on the first terminal interface, including reminding the user to place the ID card in the designated area, and adjust the brightness of the client and other collection parameters, and the authenticator scans the ID card to extract the avatar on the ID card Photos, ID card number information, and de-texture the avatar photo, send the processed photo and ID card number information to the file server of the first...
Embodiment 3
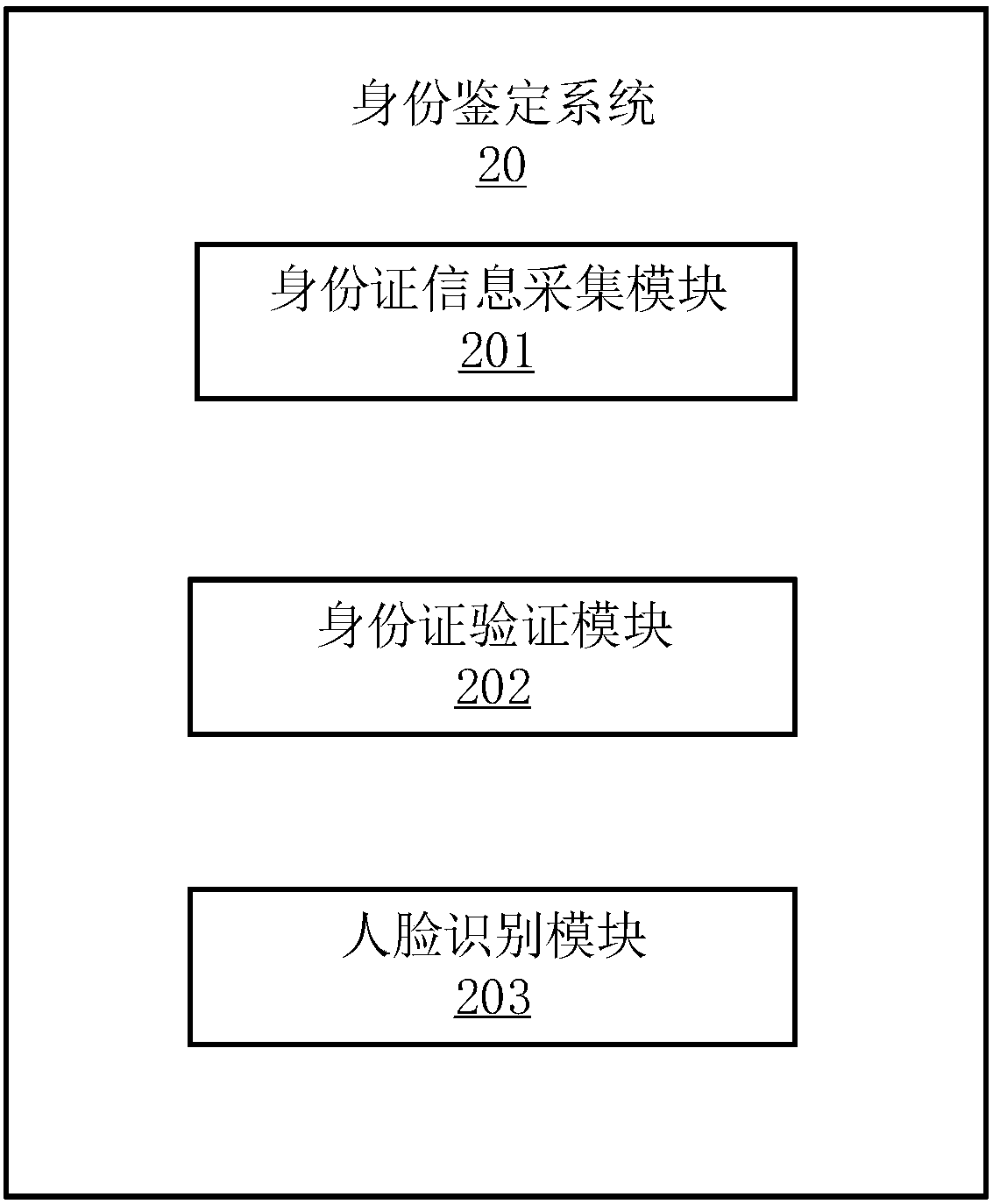
[0060] Refer to Figure 3-6 , Shows an identity authentication system 20. In this embodiment, the identity authentication system 20 is divided into one or more program modules, one or more program modules are stored in a storage medium, and are composed of one or more The processor executes to complete the present invention. The program module referred to in the present invention refers to a series of computer program instruction segments that can complete specific functions, and is more suitable for describing the execution process of the identity authentication system 20 in the storage medium than the program itself. The following description will specifically introduce each program module of this embodiment Function:
[0061] The ID card information collection module 201 is used to collect ID card information of the user, including ID card avatar photos and ID card numbers, and de-netize the avatar photos.
[0062] The ID card verification module 202 is used to verify the vali...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com