Method and device of identifying target terminal
A technology for target terminals and users, applied in character and pattern recognition, instruments, computing, etc., can solve problems such as sparse user data, inability to add new user clusters, and impact on the accuracy of user clusters, to ensure diversity and solve problems. Effects of cold starts and data sparsity issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
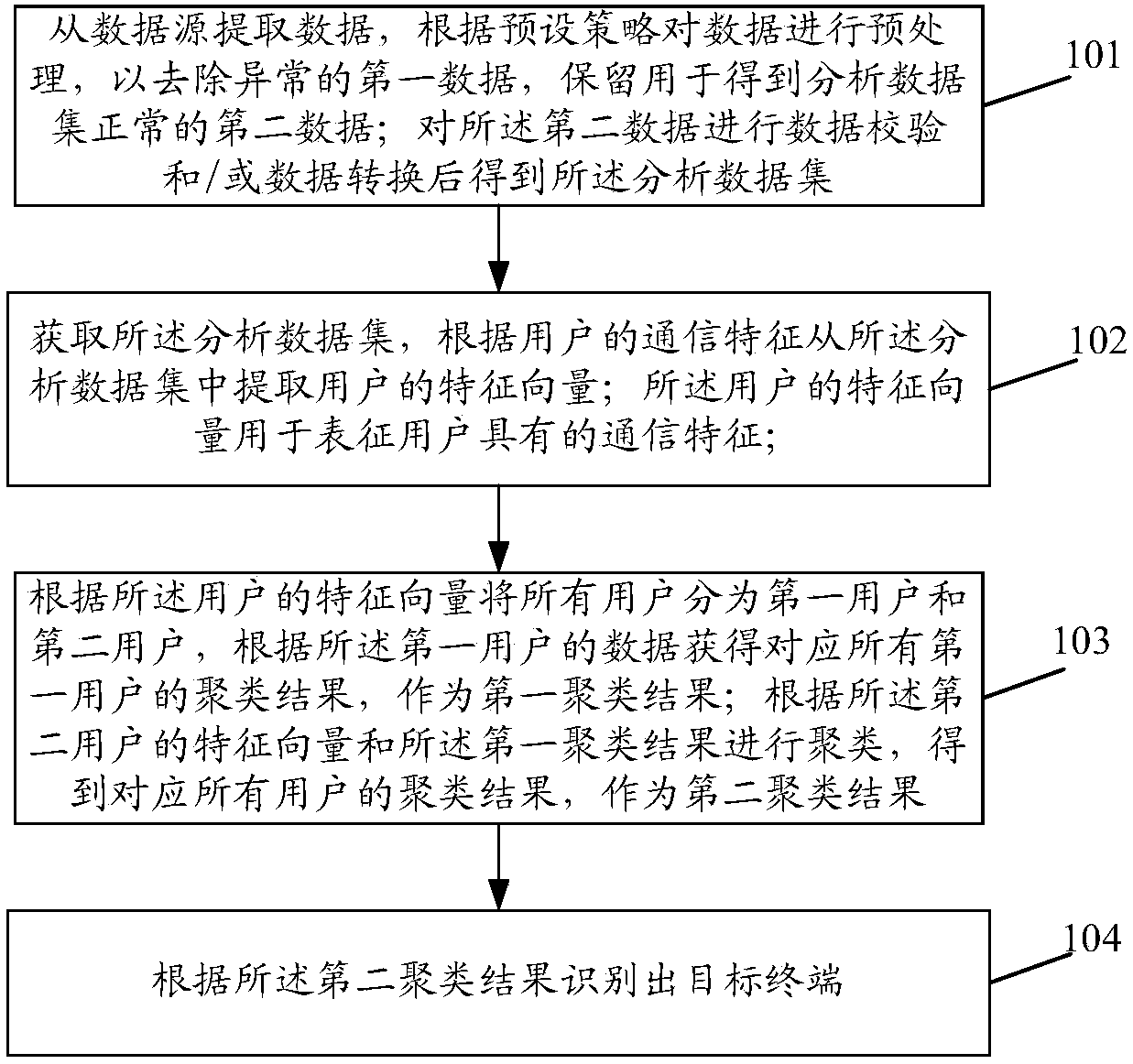
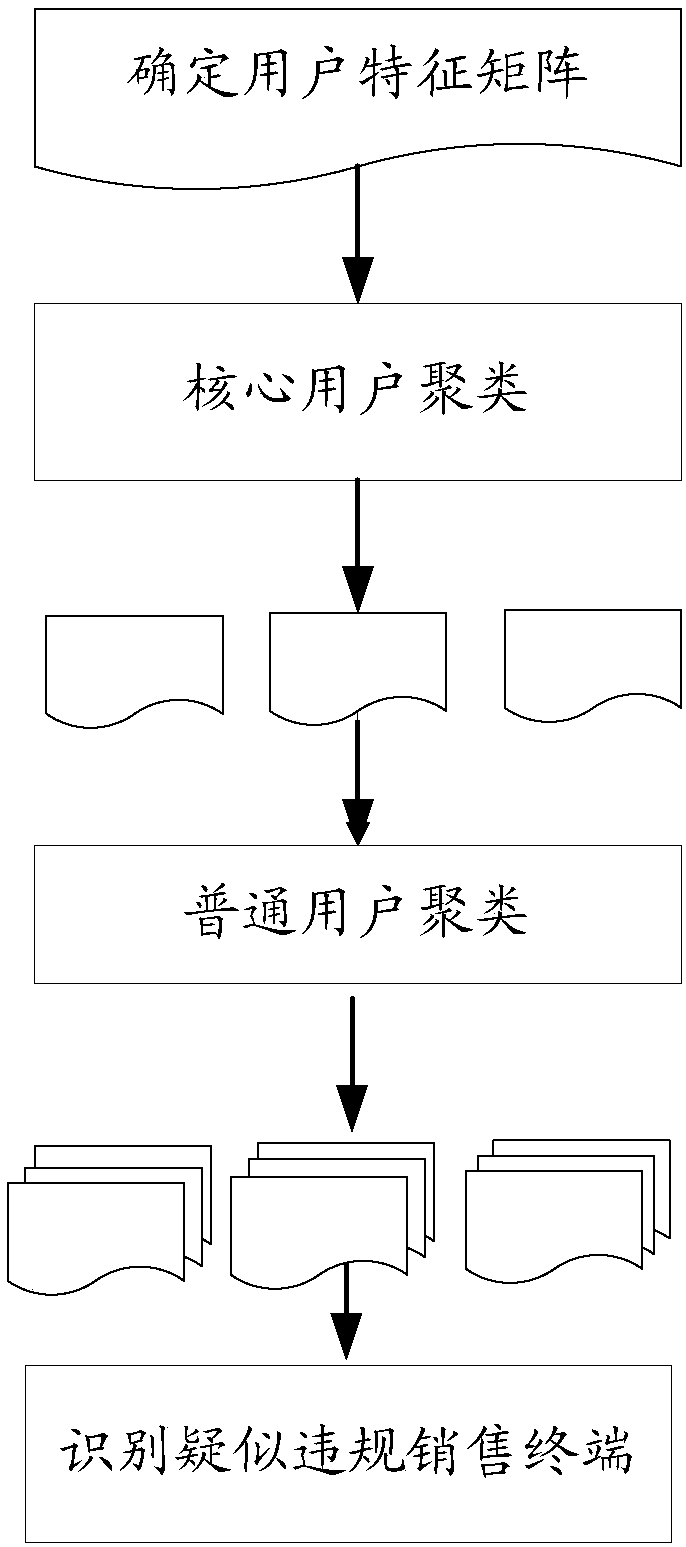
[0052] In the embodiment of the present invention, the data is extracted from the data source, and the data is preprocessed according to the preset strategy to remove the abnormal first data and retain the normal second data for obtaining the analysis data set; The analysis data set is obtained after data verification and / or data conversion; the analysis data set is obtained, and the user's feature vector is extracted from the analysis data set according to the user's communication characteristics; the user's feature vector is used to represent the user Have communication characteristics; divide all users into first users and second users according to the feature vectors of the users, and obtain clustering results corresponding to all first users according to the data of the first users as the first clustering results ; Perform clustering according to the feature vector of the second user and the first clustering result to obtain a clustering result corresponding to all users a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com