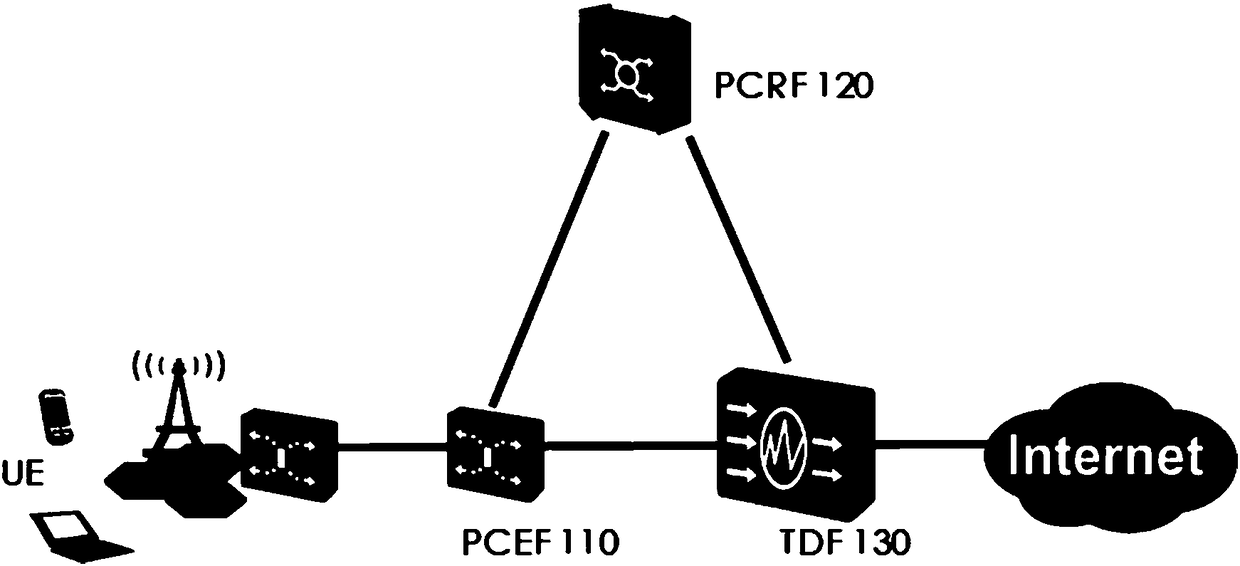
Method, device and system for realizing user equipment authentication
A user equipment and authentication technology, applied in the field of communication, can solve the problem of large average delay of UE access to the network, and achieve the effect of reducing the average delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach A
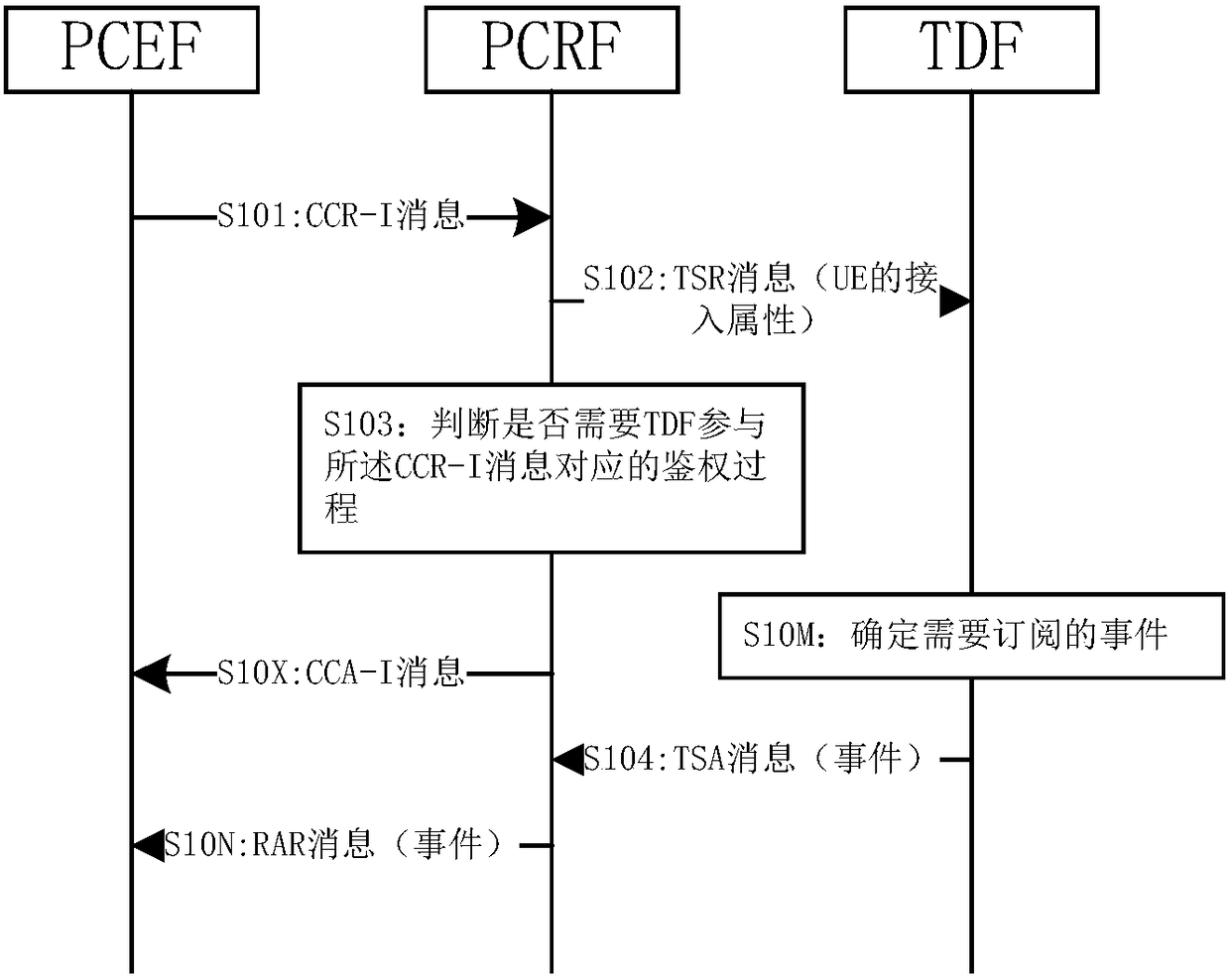
[0124] The TDF pre-configures event subscription rules, and the event subscription rules may be configured based on the UE's access attributes, for example: a UE whose access point name (APN, Access Point Name) is "iptv.net" subscribes to the RAT -Type-Change event.
[0125] Such as Figure 3a Shown:
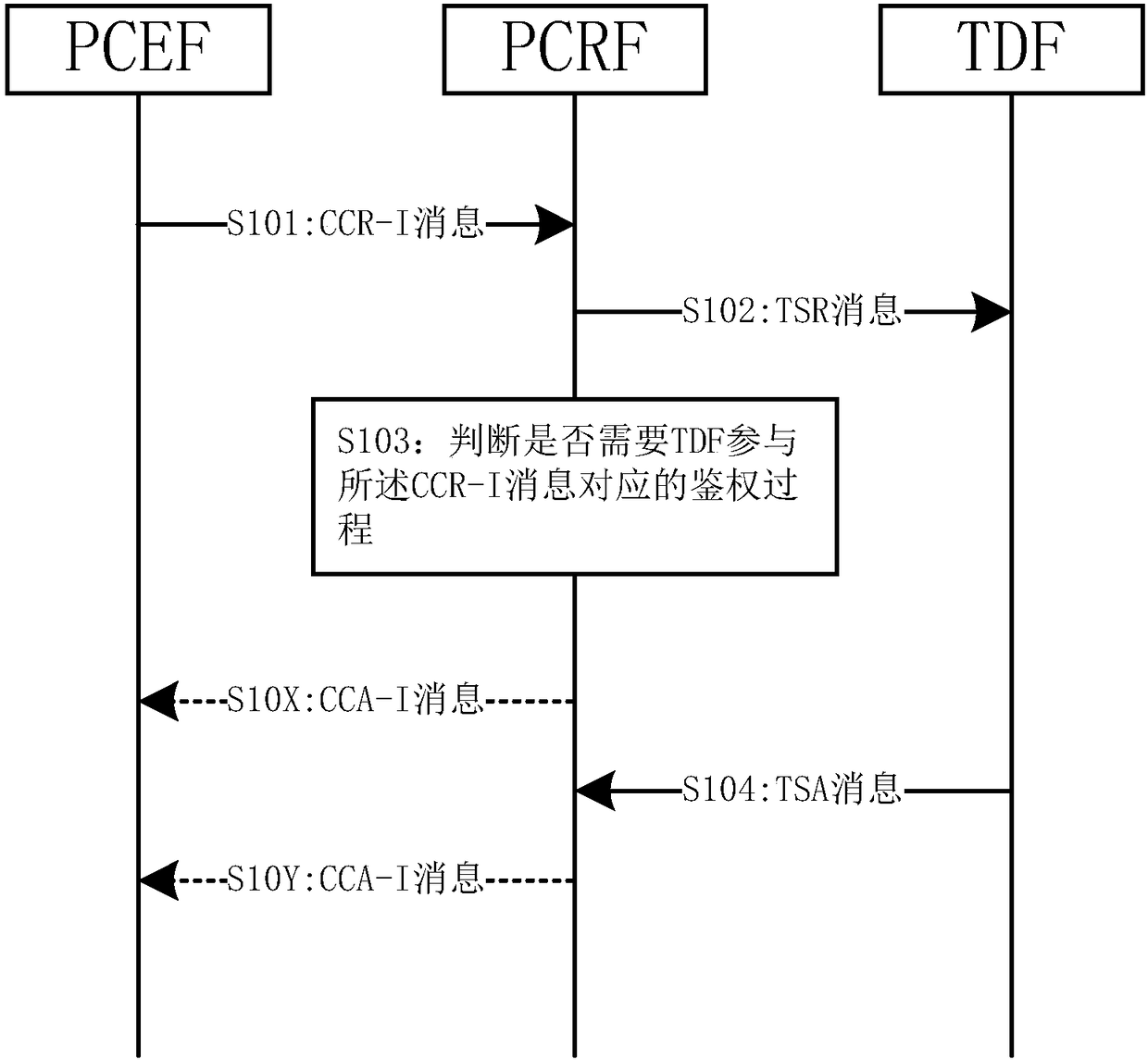
[0126] The TSR message in step S102 of the method 100 provided by Embodiment 1 of the present invention also includes the access attribute of the UE, and the access attribute of the UE included in the TSR message is the same as the CCR- The access attribute of the UE included in the I message will not be described again.
[0127] The method 100 provided in Embodiment 1 of the present invention may further include steps S10M and S10N after S102.
[0128] Step S10M: After receiving the TSR message in step S102, the TDF determines the event that needs to be subscribed according to the access attribute of the UE and the event subscription rule, for example: RAT-Type-Change event,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com