Support steganographic methods based on attribute information extraction
A technology of attribute information and attributes, applied in the field of image information hiding, can solve the problems of insecure and inconvenient secure communication, and achieve high imperceptibility, good detection effect, and high concealment effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
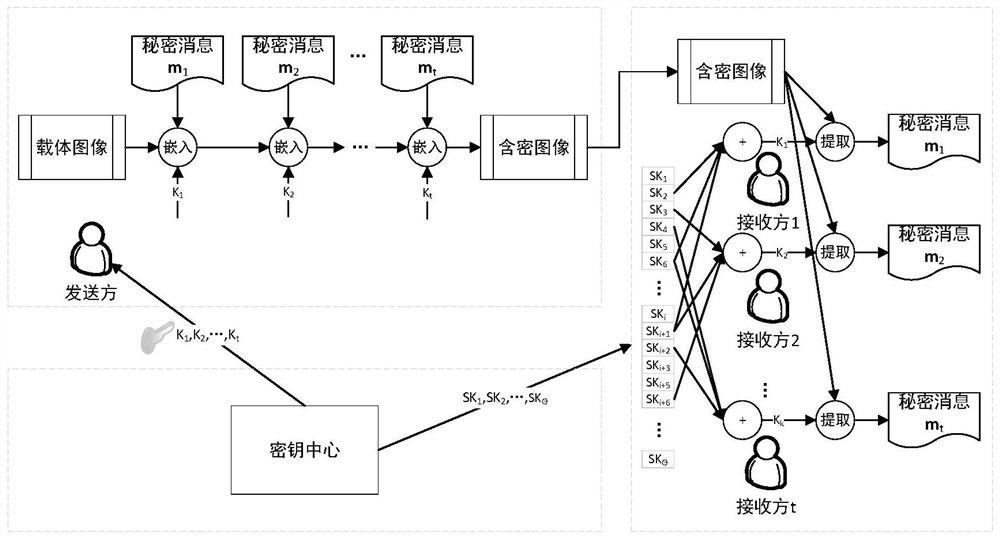
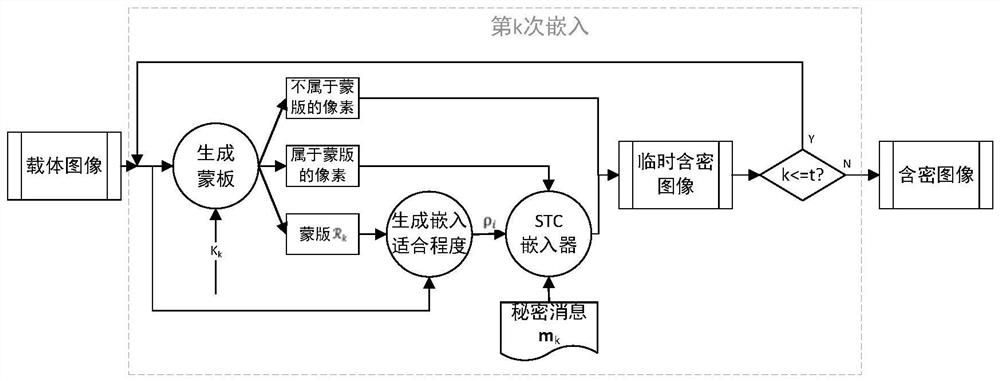
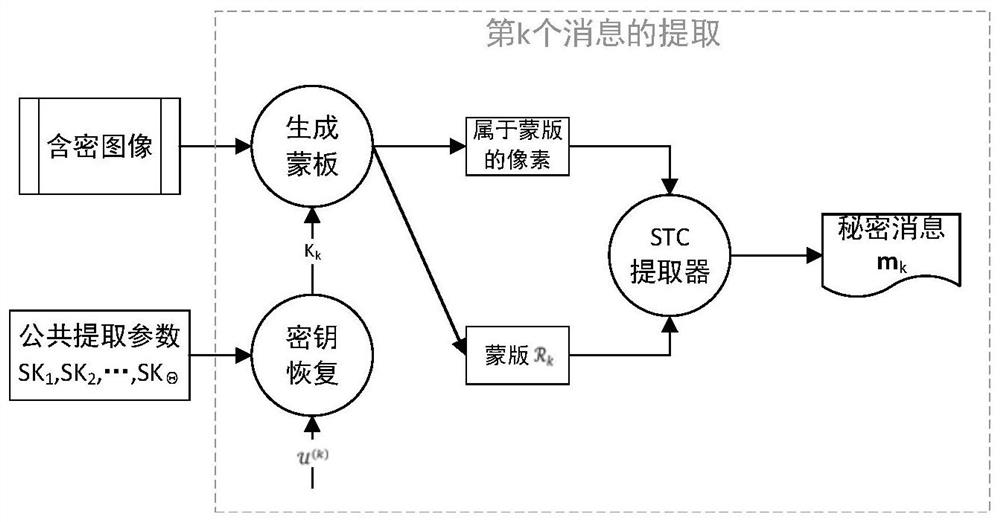
[0030] The present invention combines secret sharing and steganographic scheme design technology based on adaptive steganographic coding (STC), to hide a plurality of private information with different attributes at one time. In order to hide multiple private messages, the present invention uses secret sharing to generate a message embedding position mask for them based on a key assigned to each message. According to this mask and the embedding perturbation measure based on the image content, we judge the suitable embedding degree of each pixel, and use the embedding technology of STC to complete the embedding of the secret message. Receivers can and can only locate the mask of the corresponding message according to their identity attributes, and then use the extraction technology of STC to extract the message. If the recipient does not have the identity attribute, then they cannot be located, or even know that other secret messages exist.
[0031] That is to say, the present...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com