Malicious code detection system
A malicious code detection and malicious code technology, which is applied in the fields of instruments, electronic digital data processing, platform integrity maintenance, etc. Detection accuracy, wide application range, and automatic update effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] In order to make the objects and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the examples. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
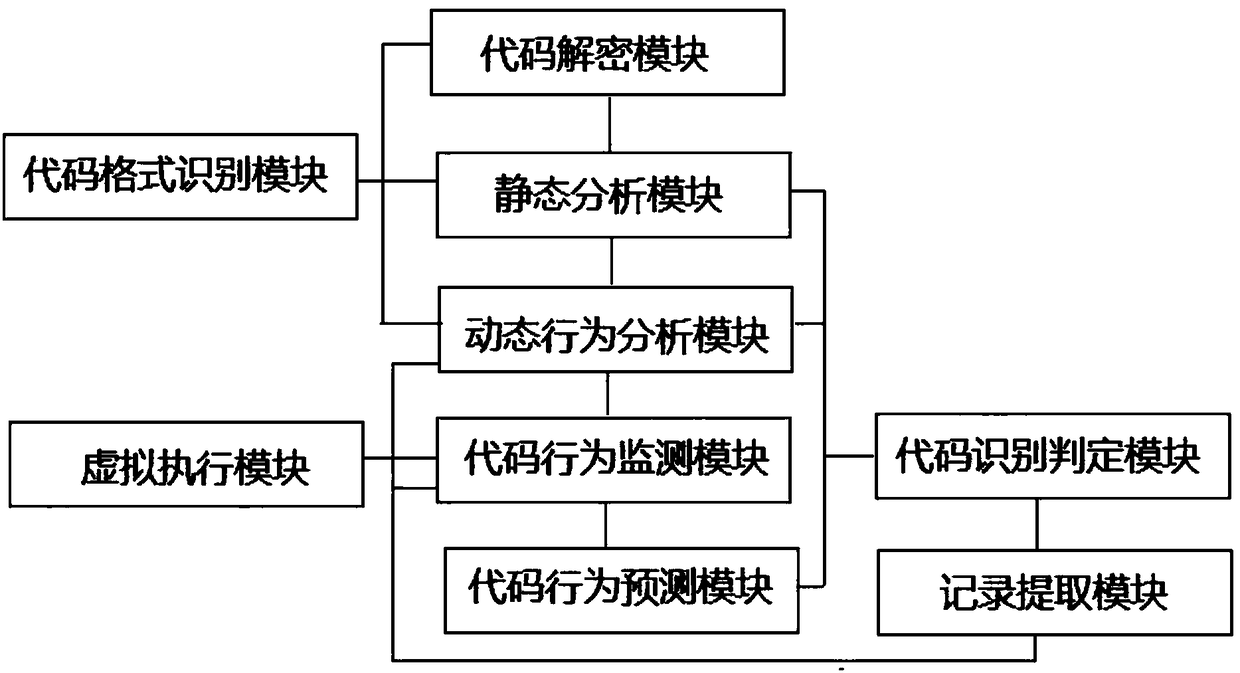
[0029] like figure 1 As shown, the embodiment of the present invention provides a malicious code detection system, including:
[0030] The code format recognition module is used to identify and analyze the code format to be detected;
[0031] The code decryption module is used to open and close according to the recognition results of the code format recognition module. Once the recognized code data has garbled characters or other encryption behaviors, the code decryption module is started to decrypt the code; after the decryption is completed, static , Dynamic behavior analysis;
[0032] The static analysis module is used to obtain the API fu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com