Data security protection method, network access equipment and terminal
A technology for network access equipment and data security, which is applied to data security protection methods, network access equipment and terminals, and data transmission fields, and can solve problems such as inability to perform AS layer security protection and insufficient guarantee of user data security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0067] This embodiment provides a data security protection method, which can be applied to a 5G IoT network. In the prior art, the 5GIoT network does not have an initial security activation process in the CP mode, that is, the AS layer security protection cannot be performed in the CP mode, resulting in that the security of user data transmission on the air interface in the 5GIoT network is not fully guaranteed. This embodiment proposes a technical solution to this problem.
[0068] The executor of this embodiment may be a network access device, which may be used to implement the data security protection method of this embodiment; in practice, the network access device may be, for example, an evolved base station (eNB), or a responsible A component, device, device or system performing a function similar to an eNB.
[0069] Based on the network access device, see image 3 , the data security protection method provided by the present embodiment includes the following steps:
...
Embodiment 2
[0089] This embodiment corresponds to Embodiment 1, and provides a data security protection method applied on the terminal side, including the following steps:
[0090] Step 1), the terminal sends an RRC connection request message to the network access device, and the RRC connection request message includes a security capability algorithm supported by the terminal;
[0091] Step 2), receiving the RRC connection establishment message sent by the network access device, the RRC connection establishment message includes the security capability algorithm supported by the network access device according to the network access device, and the terminal Supported security capability algorithms, determined target security capability algorithms;
[0092] Step 3), for the AS layer messages sent and received between the network access device and the terminal, use the security key of the terminal and the target security capability algorithm to perform data security protection.
[0093] In t...
Embodiment 3
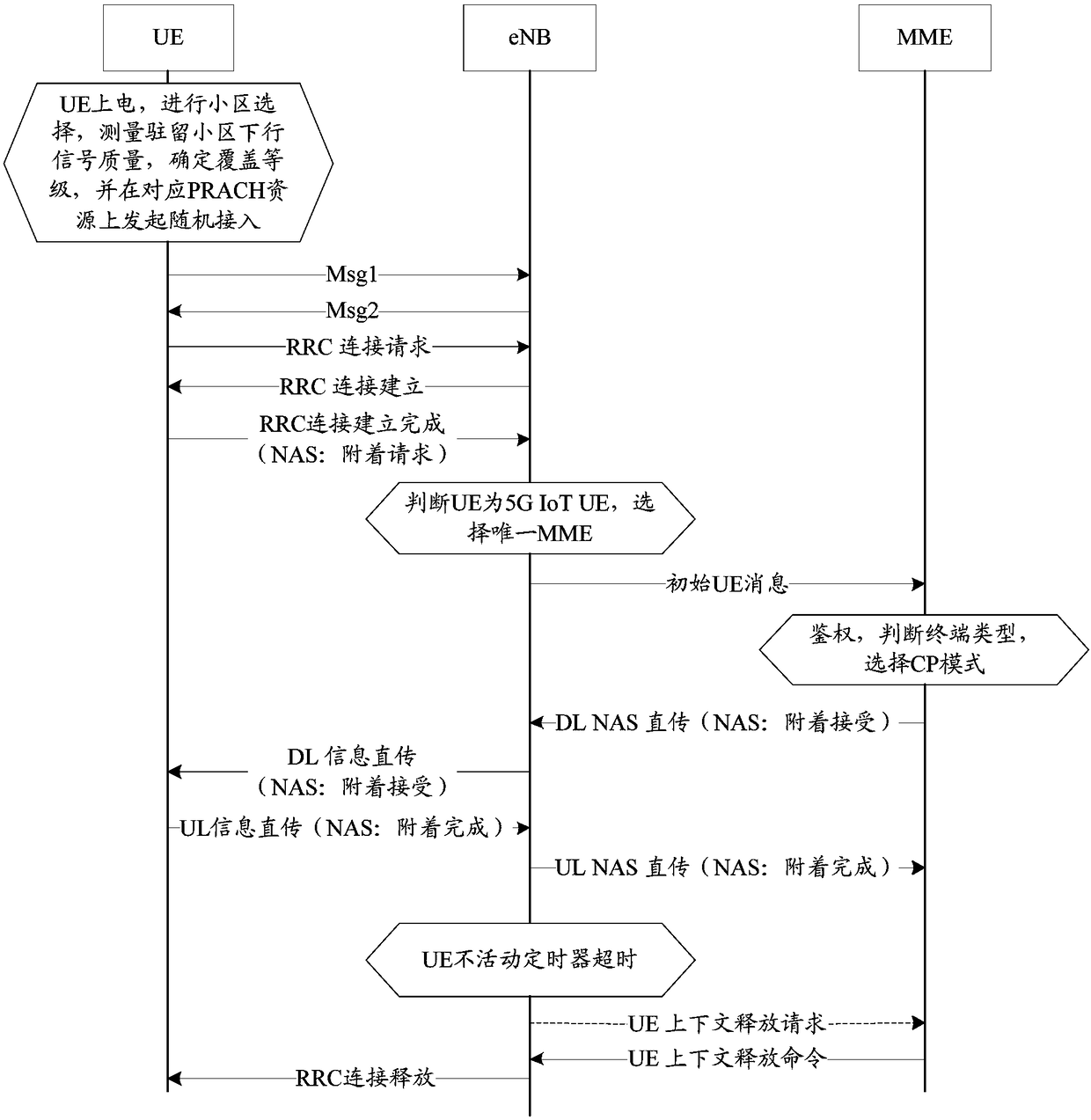
[0097] This embodiment is based on any one of the above-mentioned embodiments. In order to solve the problems existing in the prior art, this embodiment proposes a method for ensuring user data security in a 5G IoT network, that is, a solution for solving AS layer security problems of user data in CP mode. see Figure 4 , the method includes the following steps:
[0098] Step 401: When the terminal is initially powered on, select a cell on a designated frequency point, read the system information broadcast by the cell, and determine that the network is a 5G IoT network. The terminal determines the coverage level according to the quality of the downlink RSRP signal, and initiates random access on the corresponding Physical Random Access Channel (PRACH, Physical Random Access Channel) resource, including sending the random access preamble to the eNB and receiving the random access preamble sent by the eNB. Access response.
[0099] Step 402: The terminal sends a Msg3RRC Conne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com