Detection method of abnormal data of embedded intelligent terminal, and embedded intelligent terminal
An abnormal data and intelligent terminal technology, applied in the field of network security, can solve the problems of low detection and detection efficiency of abnormal data, achieve the effect of improving the accuracy of abnormal data, improving the quality of clustering, and reducing the false positive rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
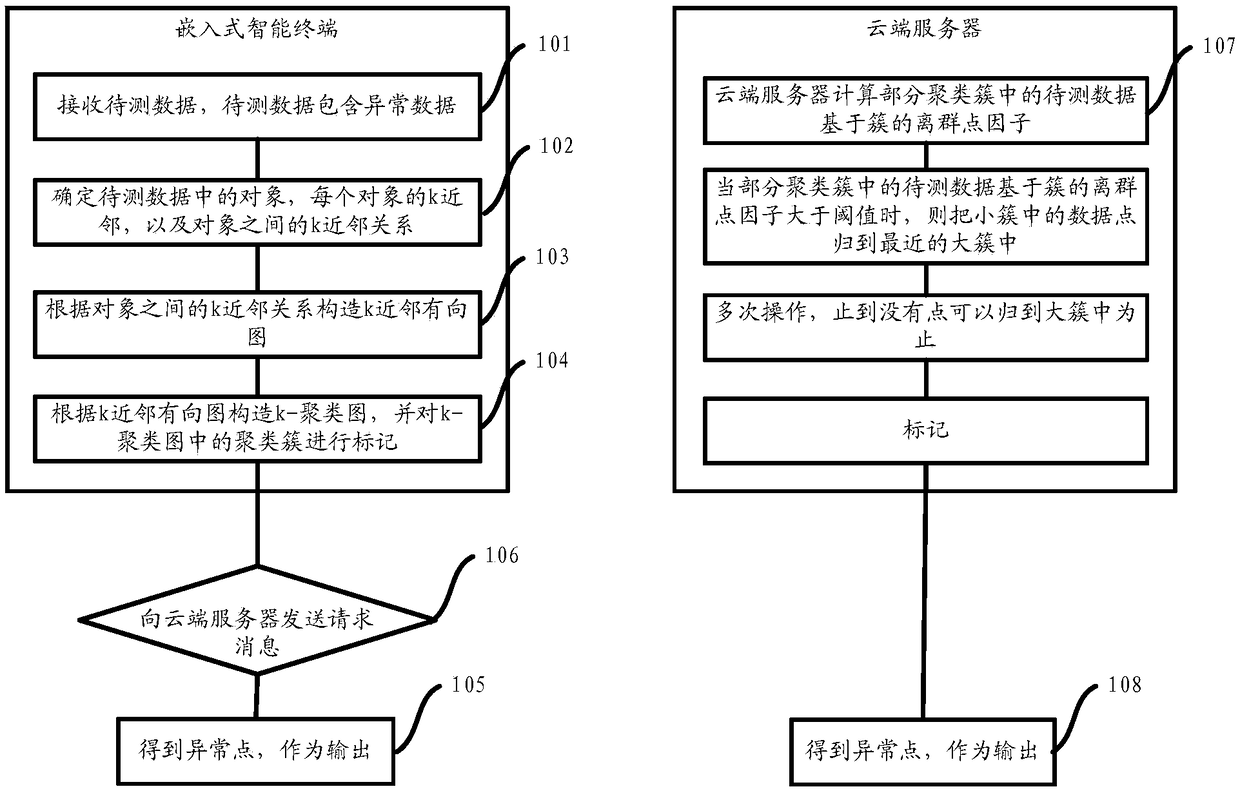
[0036] The embodiment of the present invention provides a method for detecting abnormal data of an embedded smart terminal and an embedded smart terminal, which can use the cloud-assisted method and use the graph clustering method to analyze the embedded smart terminal environment when the computing resources of the terminal device are limited. For small-scale abnormal data mining, the detection rate is high; the embedded smart terminal data has fewer attribute types, and the operating algorithm efficiency is higher. At the same time, the cloud collaboration method is used to assist the embedded smart terminal to perform secondary marking, which reduces the computing burden of the embedded smart terminal and improves the computing efficiency of the embedded smart terminal. In addition, the adoption of the technical solution of the present invention improves the problem that the traditional K-Means-based anomaly detection algorithm needs to preset the number of clusters, improve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com