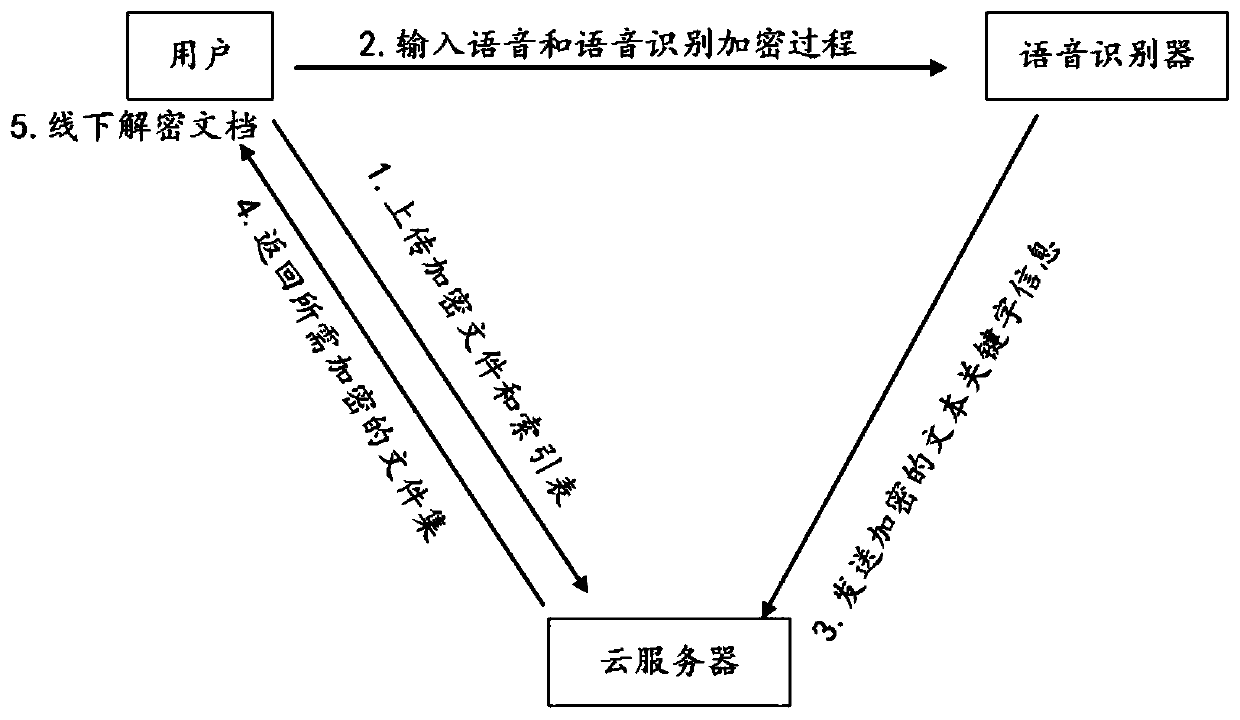
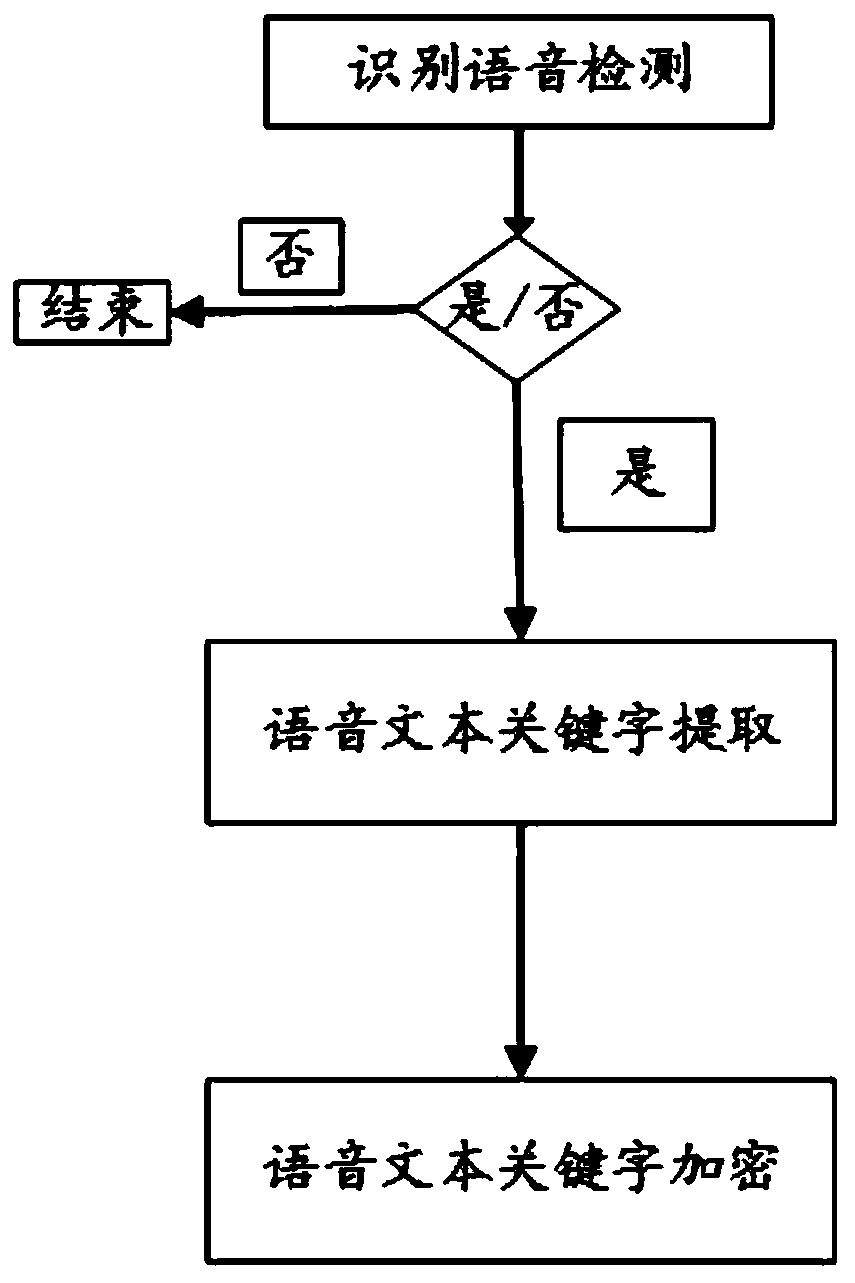
A cloud storage method supporting voice encrypted search
A voice encryption and cloud storage technology, which is applied in the field of cloud storage, can solve the problems of unresolved voice search encryption, users' cloud data privacy is easily threatened, and privacy issues are not considered.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0055] The symmetric encryption search algorithm that supports voice forms mainly consists of five steps:
[0056] In the first step, the user runs the key generation algorithm: the user first inputs a system security parameter k to generate n+2 k-bit keys Here n represents the total number of documents to be uploaded by the user.
[0057] In the second step, the user runs the encryption algorithm: first, the user will As the key of the symmetric encryption algorithm ε.Enc(·,·), pair D i Encrypt, and the encrypted result is written in C i means, where i=1,...,n.
[0058] Then, the user generates an index for these documents. Specifically, the user starts with document D 1 ,D 2 ,...,D n Extract the keyword w from 1 ,...,w m , and stored in the set W={w 1 ,...,w m}middle. Will K 1 , K 2 respectively as a pseudorandom function f 1 , f 2 The key of the user is each keyword w in the set W j Calculation: tr(w j ) = f 1 (K 1 ,w j ), Here j=1,...,m. Then, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com