Method for securely exchanging link discovery information
A technology for discovering grouping and executing methods, applied in the field of data security, can solve the problems of deceiving receiving end nodes, applications not operating normally, deceiving network construction, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
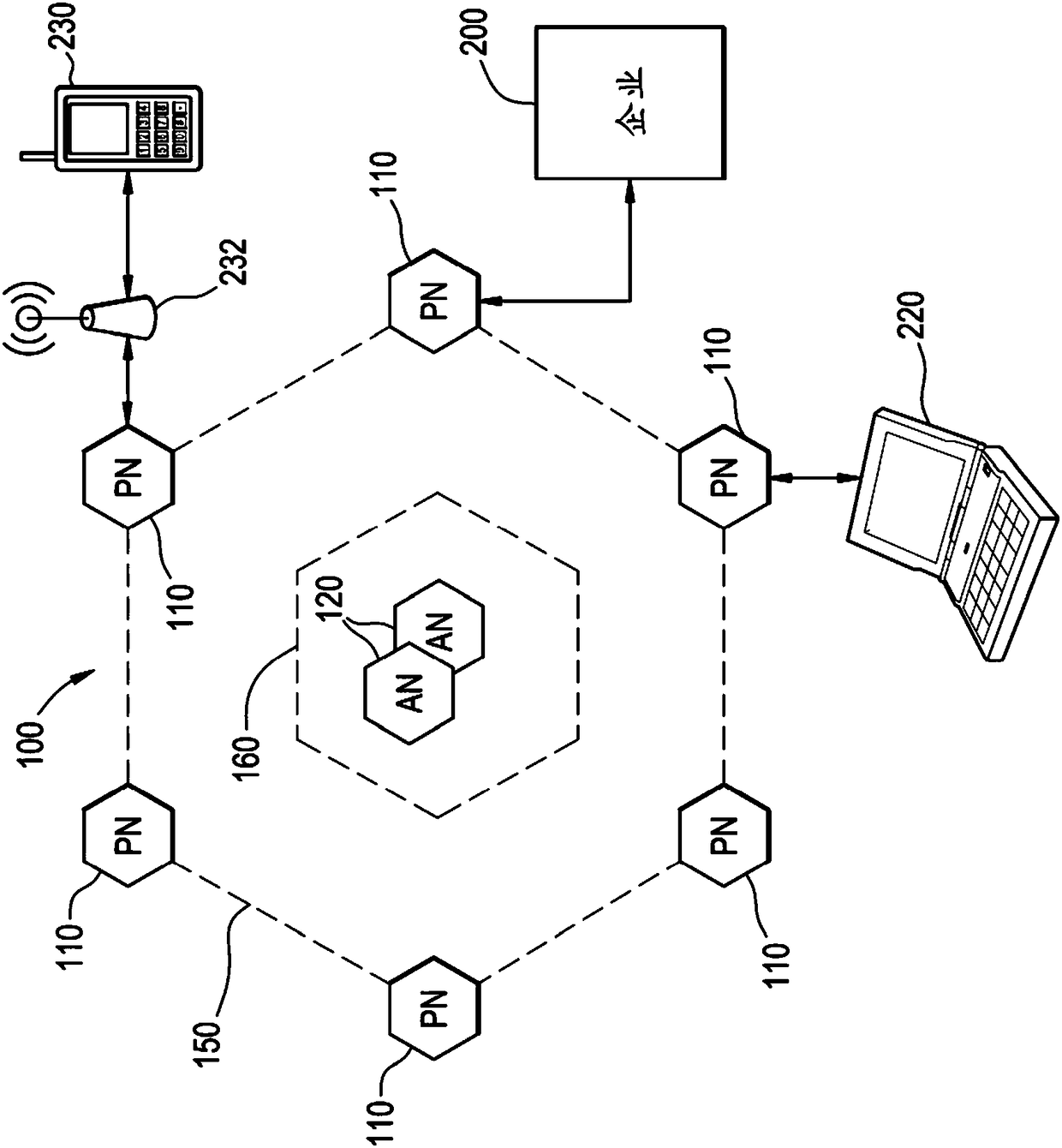
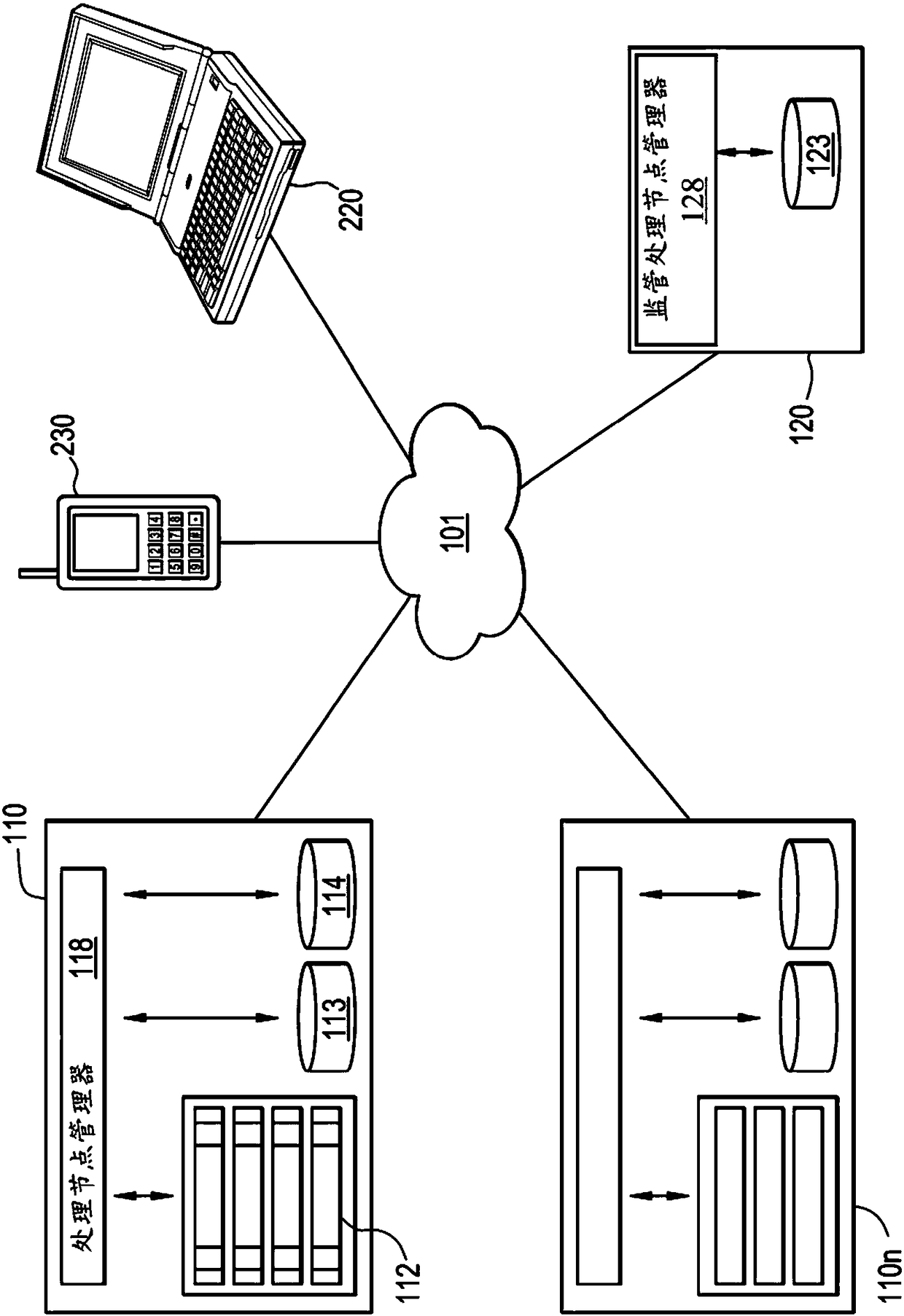
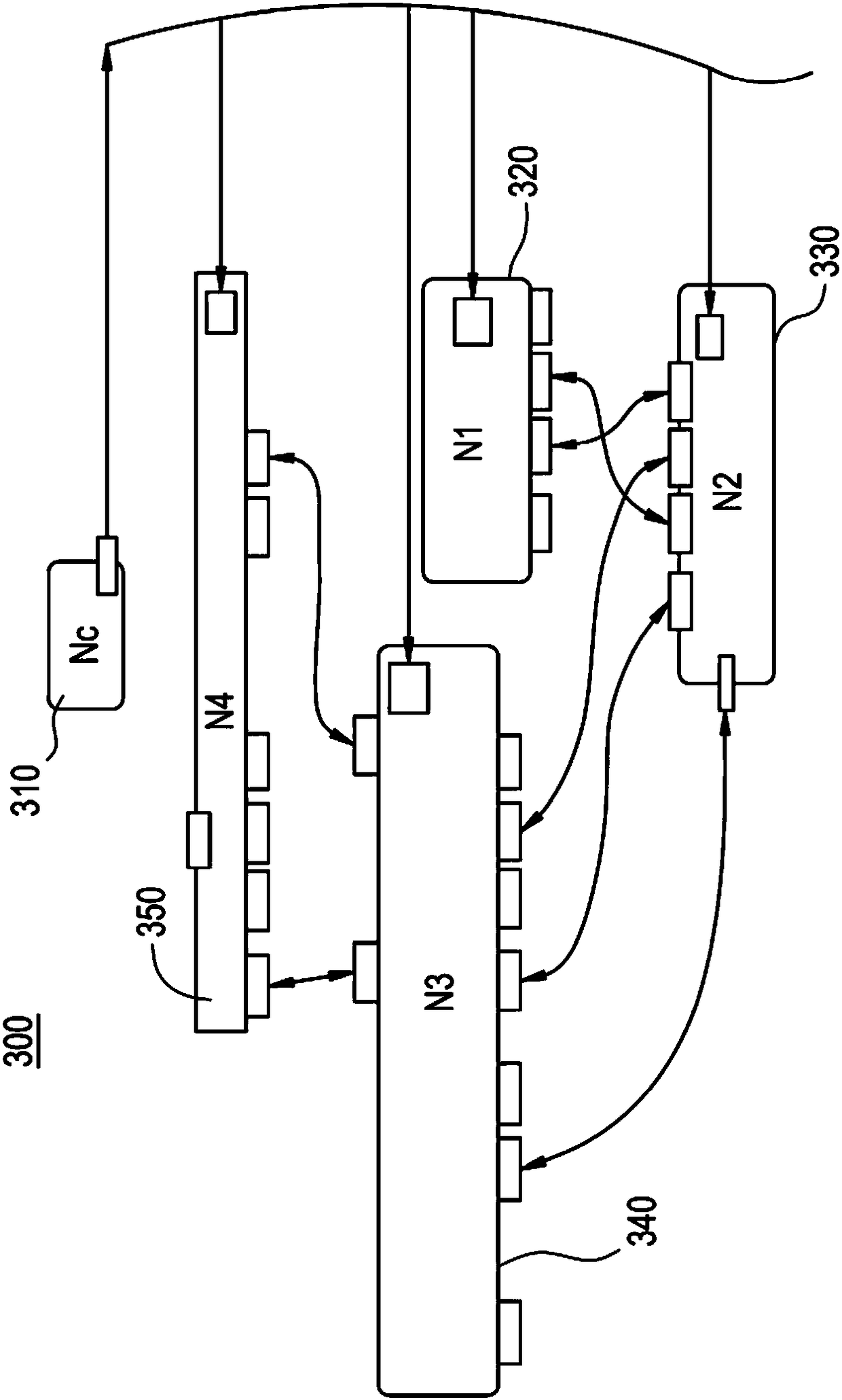
[0057] The present invention is described with reference to the drawings, wherein like reference numerals designate similar or identical elements throughout. The above-mentioned drawings are not drawn in actual scale, and are only provided to illustrate the present invention. Some aspects of the invention are described below as references to illustrate exemplary applications. It is meant that numerous specific details, relationships and methods are set forth in order to provide a full understanding of the invention. However, one having ordinary knowledge in the relevant art will recognize that the present invention can be practiced without one or more of the specific details or otherwise. In other instances, well-known structures or operations are not listed in detail to avoid obscuring the invention. The invention is not limited by the illustrated acts or sequence of events, as some acts may occur in a different order or concurrently with other acts or events. Furthermore,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com