Base station, terminal access control device and method
A terminal access and control method technology, applied in the field of communications, can solve problems such as poor user experience, and achieve the effects of reducing processing load, improving accuracy, and improving path utilization.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
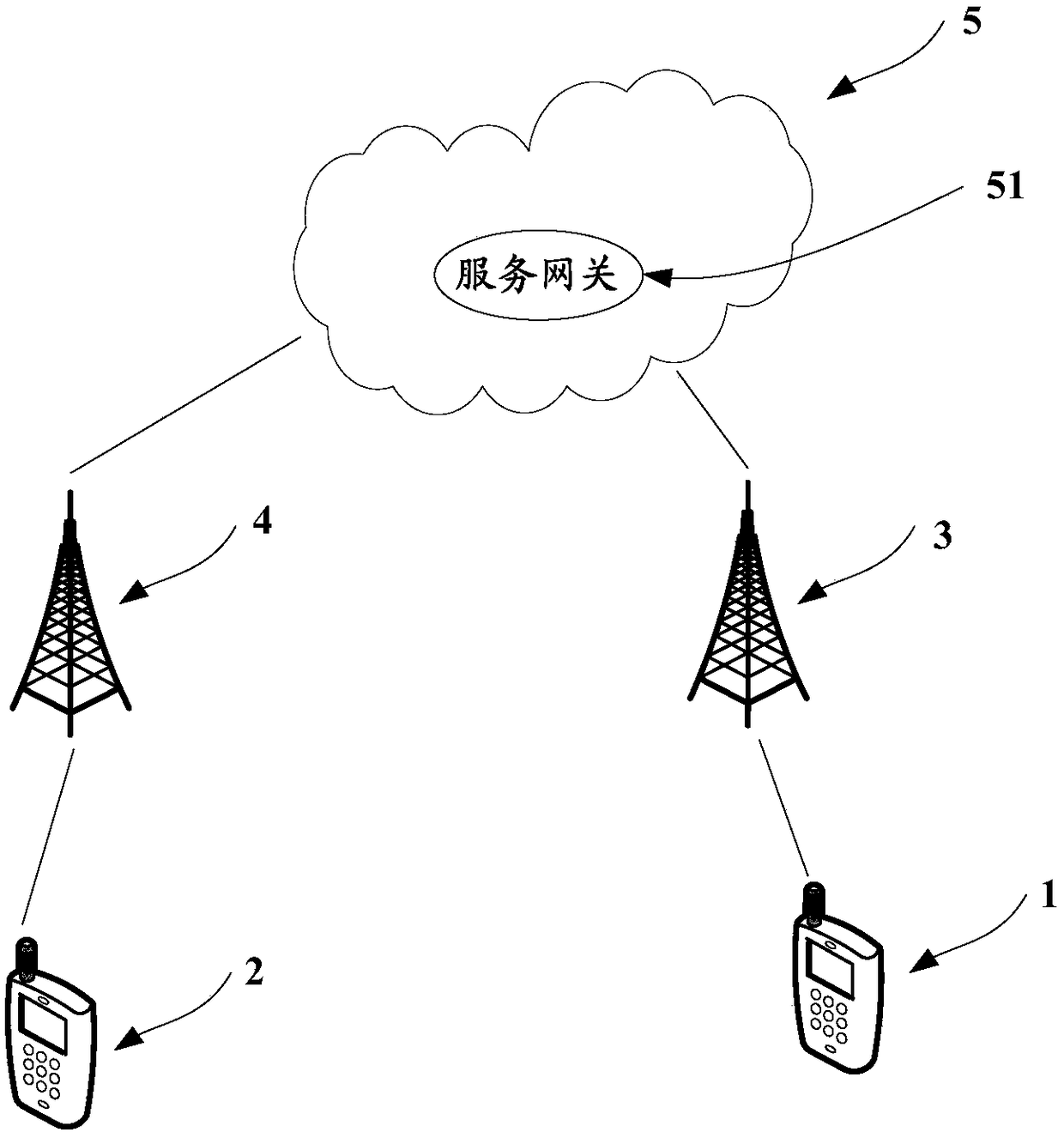
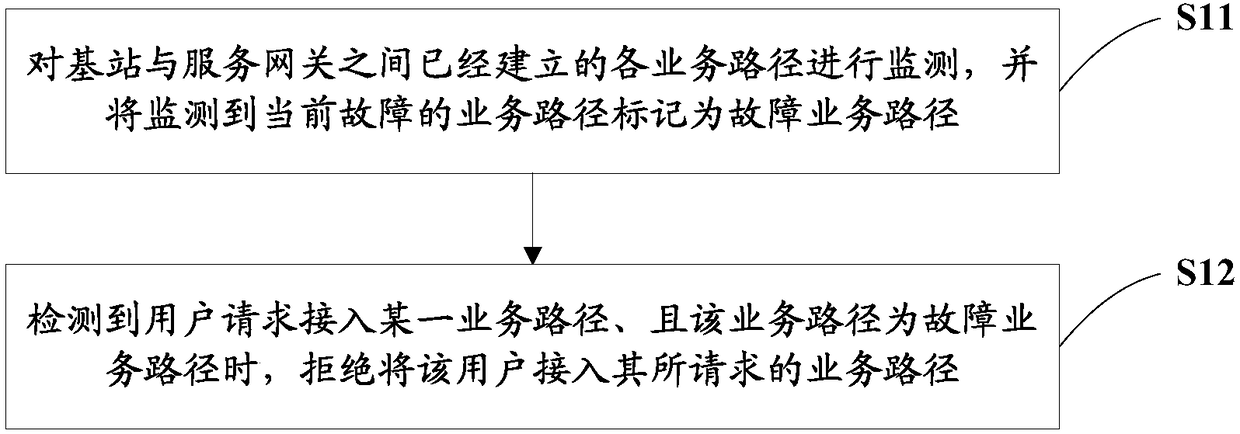
[0045]In order to avoid the failure of the service path requested by the terminal, the base station repeatedly creates the path, allows the terminal to access, releases the connected terminal, deletes the invalid access process of the path, improves the accuracy of terminal access, and reduces the processing load, the embodiment of the present invention provides a terminal access control method, please refer to figure 2 ,include:
[0046] S11: Monitor each service path that has been established between the base station and the serving gateway, and mark a currently faulty service path as a faulty service path.
[0047] Monitoring the status of the service path that has been established can be realized specifically through the base station on the service path. The base station sends an Echo Request response request message to the service gateway on the service path, and responds to the request based on the Echo Response fed back by the service gateway Respond to the message to...
Embodiment 2
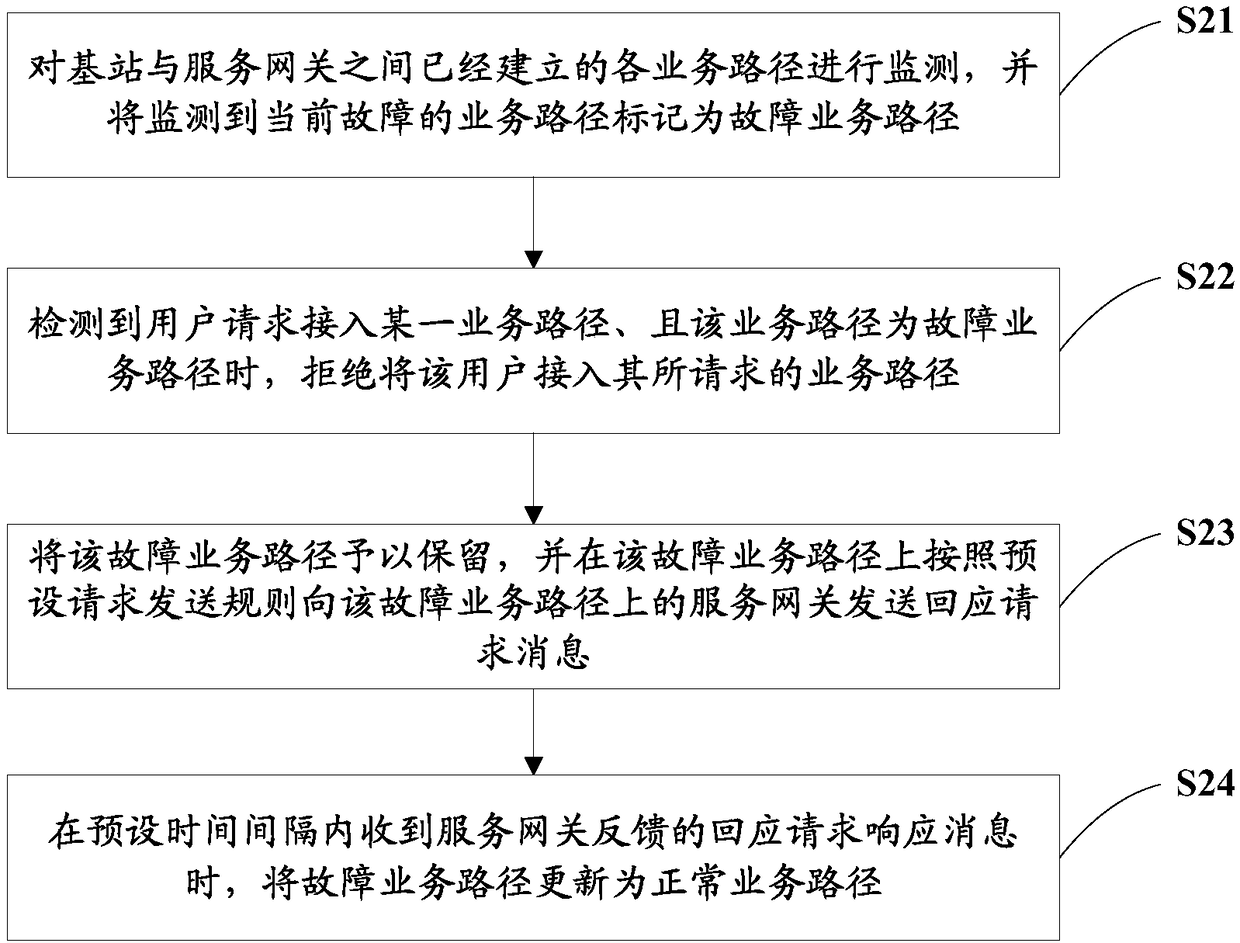
[0074] On the basis of Embodiment 1, this embodiment of the present invention provides a terminal access control method. Please refer to image 3 , including the following steps:
[0075] S21: Monitor each service path that has been established between the base station and the serving gateway, and mark a currently faulty service path as a faulty service path.
[0076] S22: When it is detected that the user requests to access a certain service path, and the service path is a faulty service path, refuse the user to access the requested service path.
[0077] The above steps S21 and S22 are the same as the steps S11 and S12 in the first embodiment, and will not be repeated here. In order to better use the present invention, further, the terminal access control method provided in this embodiment further includes the following steps:
[0078] S23: Reserve the faulty service path, and send a response request message to the service gateway on the faulty service path according to a ...
Embodiment 3
[0101] An embodiment of the present invention provides a device for controlling terminal access, which is used to implement the method for controlling terminal access described in Embodiment 1 and / or Embodiment 2 above. Please refer to Figure 6 , the terminal access control device 6 includes:
[0102] The fault monitoring module 61 is configured to monitor each service path established between the base station and the serving gateway, and mark the service path that is currently faulty during monitoring as a faulty service path. Specifically, the fault monitoring module 61 can monitor the state of the service path by sending an Echo Request response request message to the service gateway on the service path. For example, when the fault monitoring module 61 sends an Echo Request message to the service gateway on the service path After the Request responds to the request message, if an Echo Response response message fed back by the service gateway is received within a preset tim...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com