Encryption and decryption method, equipment and computer storage medium
A technology of encryption, decryption, and encryption algorithm, which is applied in the field of information security, and can solve problems such as wifi spoofing, bandwidth occupation, and security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
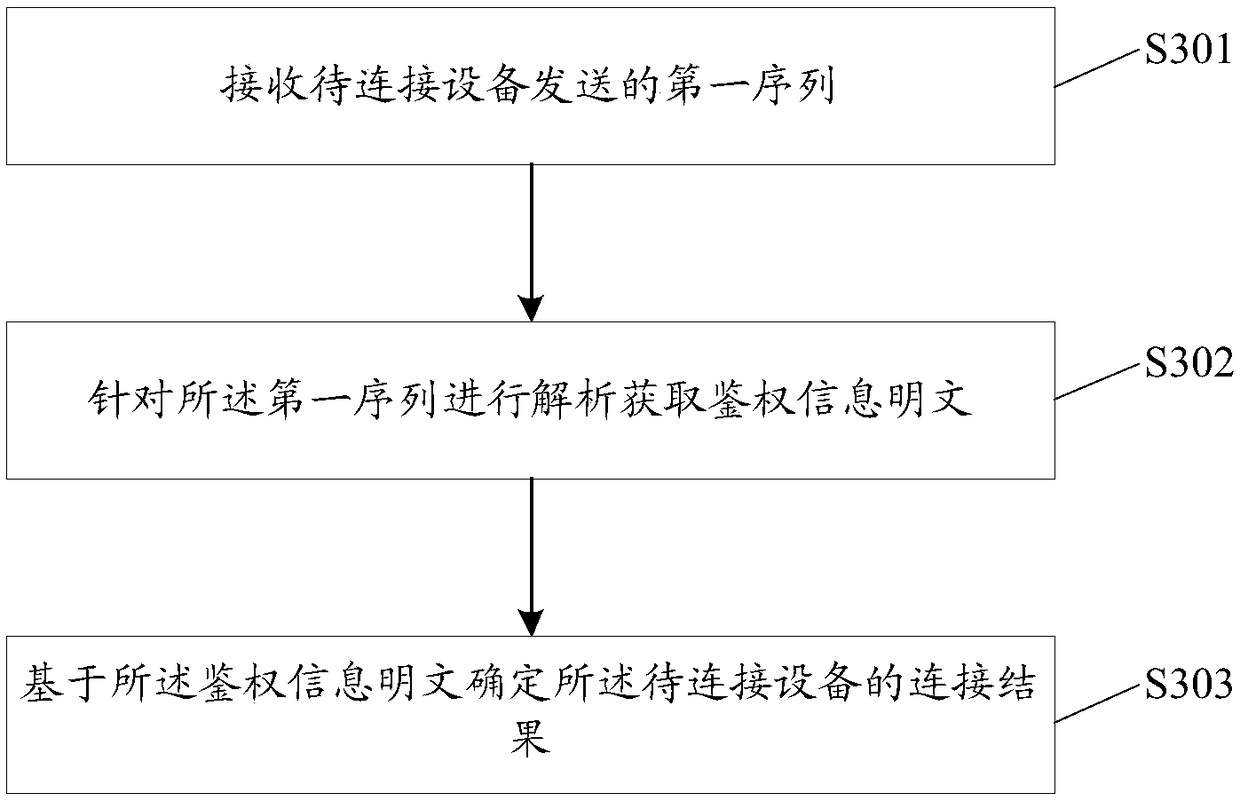
[0080] see image 3 , which shows an encryption and decryption method provided by an embodiment of the present invention, the method can be applied to routers, and the specific process of the method includes the following steps:
[0081] S301: Receive a first sequence sent by the device to be connected; wherein, the first sequence includes authentication information plaintext and parameter information of the device to be connected;
[0082] S302: Perform parsing on the first sequence to obtain authentication information plaintext;
[0083] S303: Determine a connection result of the device to be connected based on the authentication information in plain text.
[0084] In this embodiment of the present invention, the router parses the received first sequence containing the plaintext of the authentication information and the parameter information of the device to be connected to obtain the plaintext of the authentication information, and determines the plaintext of the device to...
Embodiment 2
[0108] Based on the same inventive concept of the foregoing embodiments, see Figure 4 , which shows an encryption and decryption method provided by an embodiment of the present invention, the method can be applied to the device to be connected, and the method can specifically include:
[0109] S401: Generate a first sequence based on the parameter information and authentication information of the device to be connected in plain text;
[0110] S402: Send the first sequence to the router; wherein the first sequence is used to parse and obtain the plaintext of the authentication information and determine a connection result of the device to be connected based on the plaintext of the authentication information.
[0111] In the embodiment of the present invention, the device to be connected generates the first sequence based on the plain text of the authentication information and the parameter information of the device to be connected, and sends it to the router for authentication...
Embodiment 3
[0123] Based on the same inventive concept of the foregoing embodiments, see Figure 5 , which shows an encryption and decryption method provided by an embodiment of the present invention. The method can be applied to a router and a device to be connected. In this embodiment, the device to be connected is preferably a terminal. The method can specifically include:
[0124] S501: The terminal sends a connection request to the router;
[0125] It can be understood that, in order to access the wifi network, the terminal needs to initiate a connection request.
[0126] S502: The router receives the connection request;
[0127] S503: The router sends indication information for indicating an encryption algorithm for the connection request;
[0128] It can be understood that, for the connection request sent by the terminal, the router determines the encryption algorithm in the local algorithm library according to the local policy. The local policy may be determined according to ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com