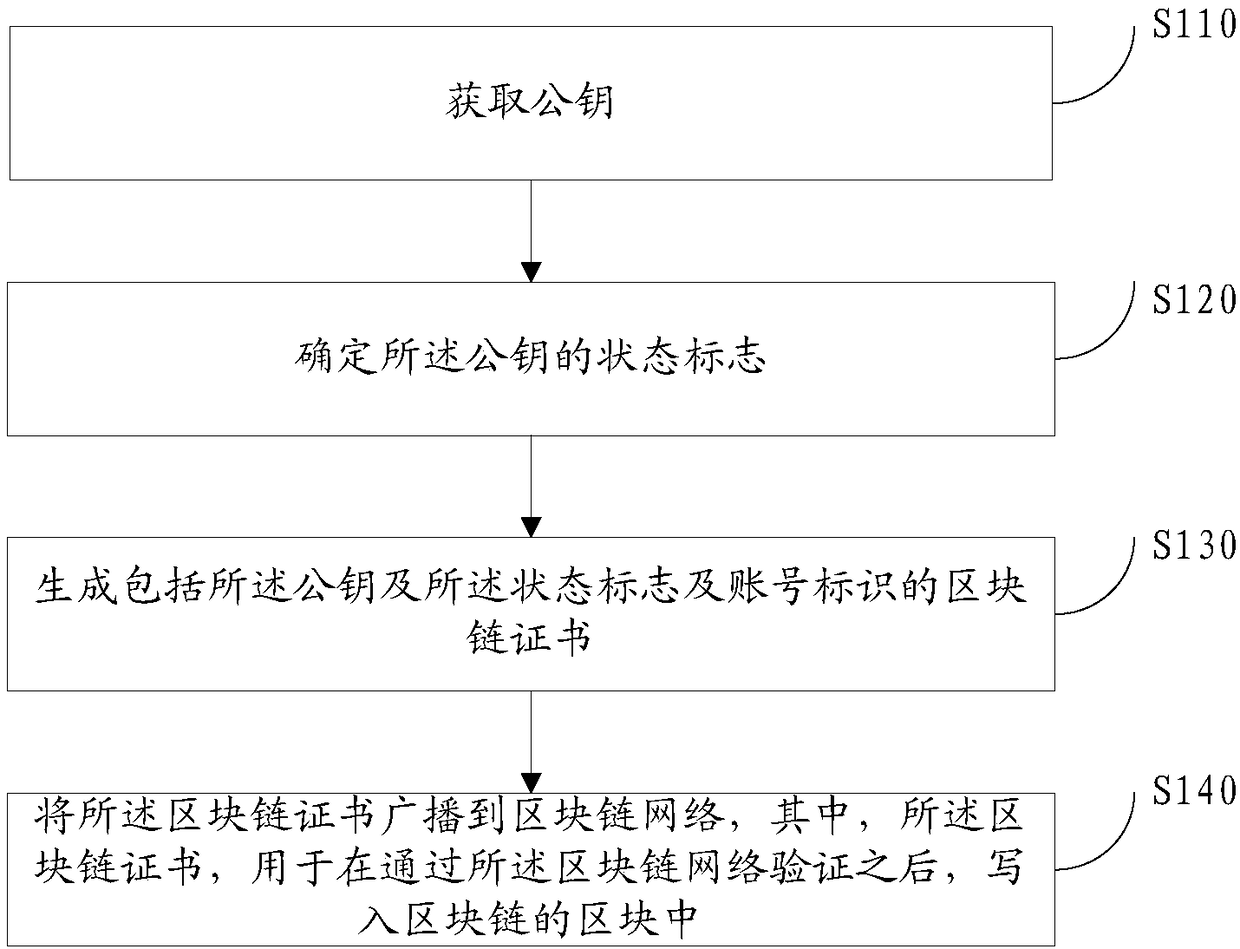
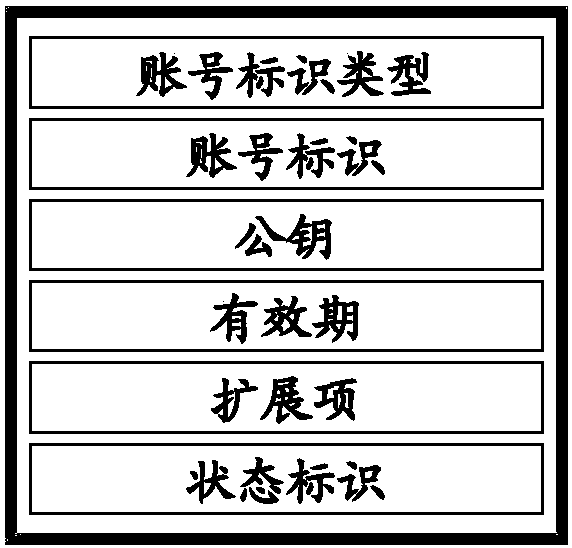
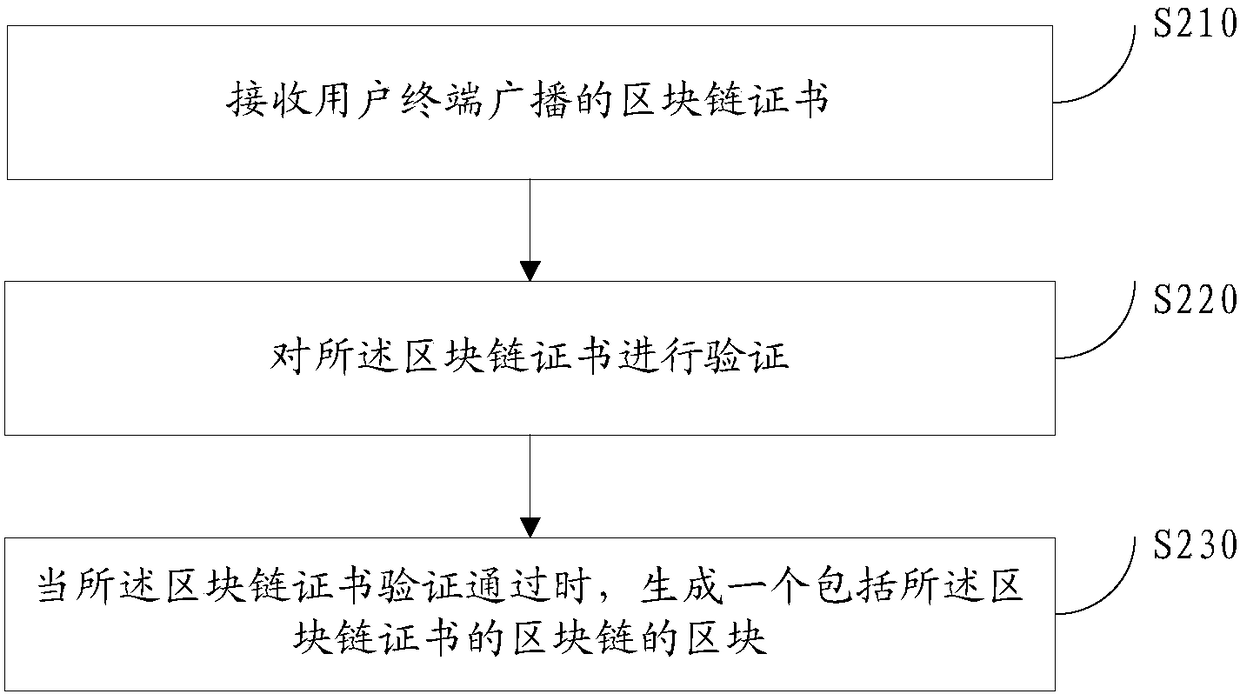
Public key processing method and device for public key infrastructure
A technology of public key infrastructure and processing method, which is applied in the field of public key processing method and device of public key infrastructure, can solve the problems of complex legality verification algorithm, limited digital certificate, complicated operation, etc., and achieve simplified acquisition of public key process, high security, effect of reducing failure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0194] Such as Image 6 As shown, this example provides a blockchain certificate application and issuance method, including:
[0195] The user terminal sends an application request carrying a blockchain certificate to the blockchain network;
[0196] The network nodes of the blockchain network perform identity verification. After the verification is passed, a new block is generated based on the consensus mechanism of the blockchain, and the newly generated block is connected to the generated blockchain to increase the block the length of the chain. The identity verification here is a kind of verification of the blockchain certificate or corresponding request in the foregoing embodiments.
[0197] The following details the various operations of the above-mentioned user terminal and blockchain network:
[0198] 1: The user terminal generates a blockchain certificate and marks the status of the blockchain certificate as valid. The user terminal processes the information of th...
example 2
[0208] Such as Figure 7As shown, this example provides a blockchain certificate revocation method, including:
[0209] 1: The user terminal sends a revocation request to the blockchain network, and the revocation request carries the blockchain certificate that needs to be revoked.
[0210] 2: After the network node of the blockchain network receives the revocation request, it verifies the user address to determine whether it meets the consensus mechanism generated by the blockchain. in the blockchain. The user address verification here is a kind of verification of the blockchain certificate or corresponding request in the foregoing embodiments.
[0211] The following is a detailed introduction to each operation of blockchain certificate revocation, and the specific steps are as follows:
[0212] The user terminal copies the blockchain certificate that needs to be revoked, and changes the status of the certificate to invalid. The user terminal treats the certificate inform...
example 3
[0216] Such as Figure 8 As shown, this example provides a query method for blockchain certificates, including:
[0217] 1: The user terminal sends a query request to the blockchain network, and the query request carries the user identification to be queried, such as a user name or a user serial number.
[0218] 2: After the network node of the blockchain network receives the query request, it uses the user ID as the query index to query the blockchain, and returns the public key in the valid blockchain certificate to the user terminal.
[0219] Specific steps are as follows:
[0220] To obtain someone else's blockchain certificate, the user terminal needs to use the user name on the blockchain certificate to initiate a query on the local blockchain or the remote blockchain. For efficiency, the search query starts from the latest block conduct;
[0221] If the user name to be queried is not retrieved on the blockchain, the query is terminated and an error message (the certi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com