Third party authorized login method and system
A login method and authorized technology, applied in the Internet field, can solve the problems of cumbersome operation process and reduce user experience, and achieve the effect of simplifying operation process and improving experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
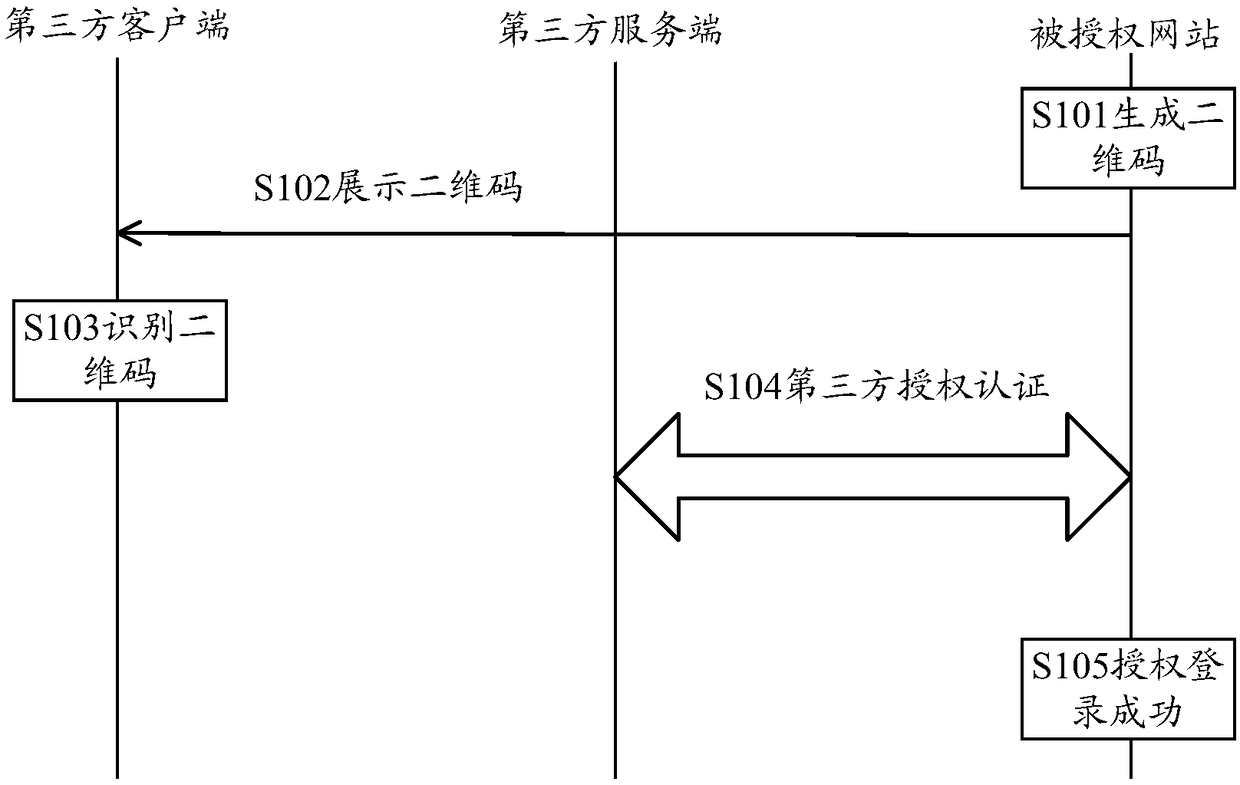
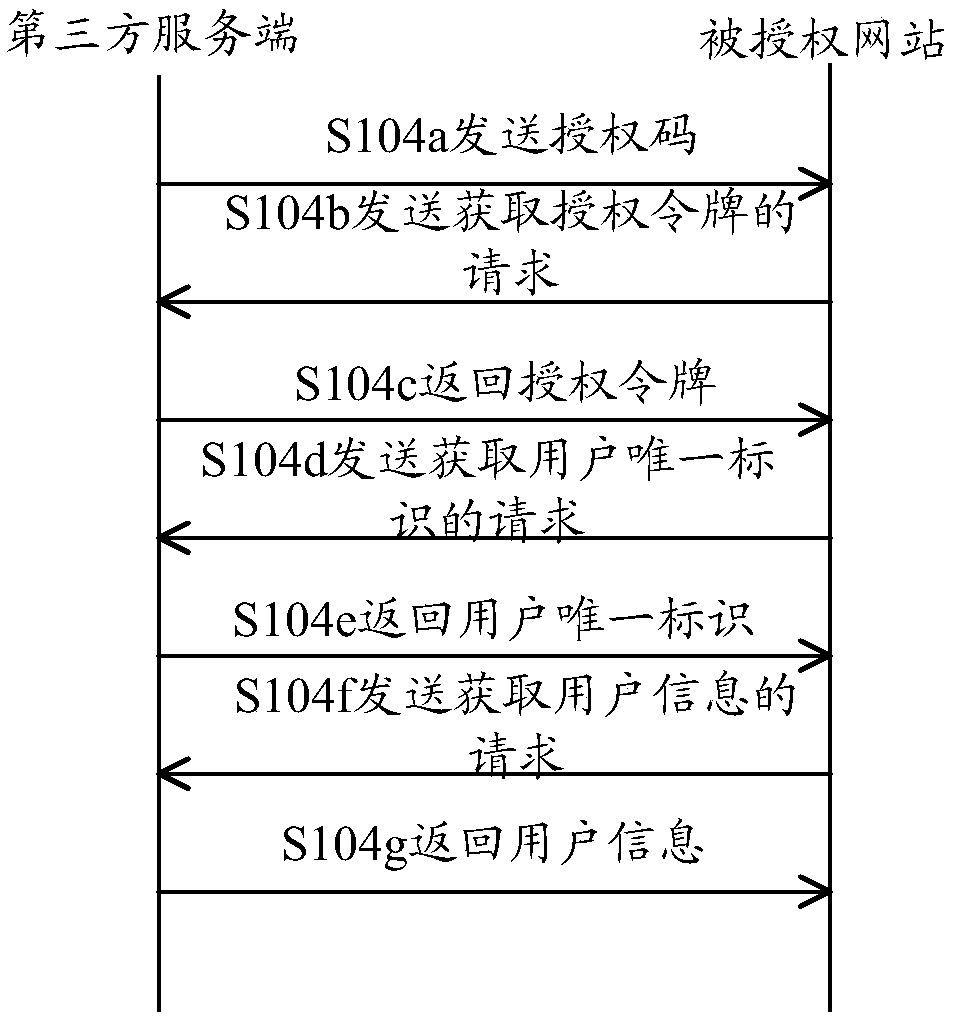
[0028] Because users often visit websites on PCs to check and download data, generally PCs are used as a tool for users’ daily office work, especially as public PCs, third-party account numbers and passwords are sensitive information of users themselves, and they will not be used on PCs for a long time. The third-party account is online, where the third-party account can be an Alipay account, QQ account, WeChat account, Weibo account, etc., and only when necessary will you log in to your own third-party account. Therefore, when a user needs to log in to access an authorized website, select a third-party account to log in, he needs to jump to the third-party website to log in with his third-party account and password to authorize, and then jump back to the authorized website. The authorized site shows that the user is logged in. For users, the operation process is cumbersome, which reduces the user experience.
[0029] In view of the above problems, the embodiments of this spe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com