Method, computer program and device for reducing an interference of temporary communication resources used for a wireless communication between a vehicle key and a vehicle
A technology of wireless communication and communication resources, applied in the field of reducing interference to time communication resources used for wireless communication between car keys and vehicles, computer programs and equipment, capable of solving problems such as high costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
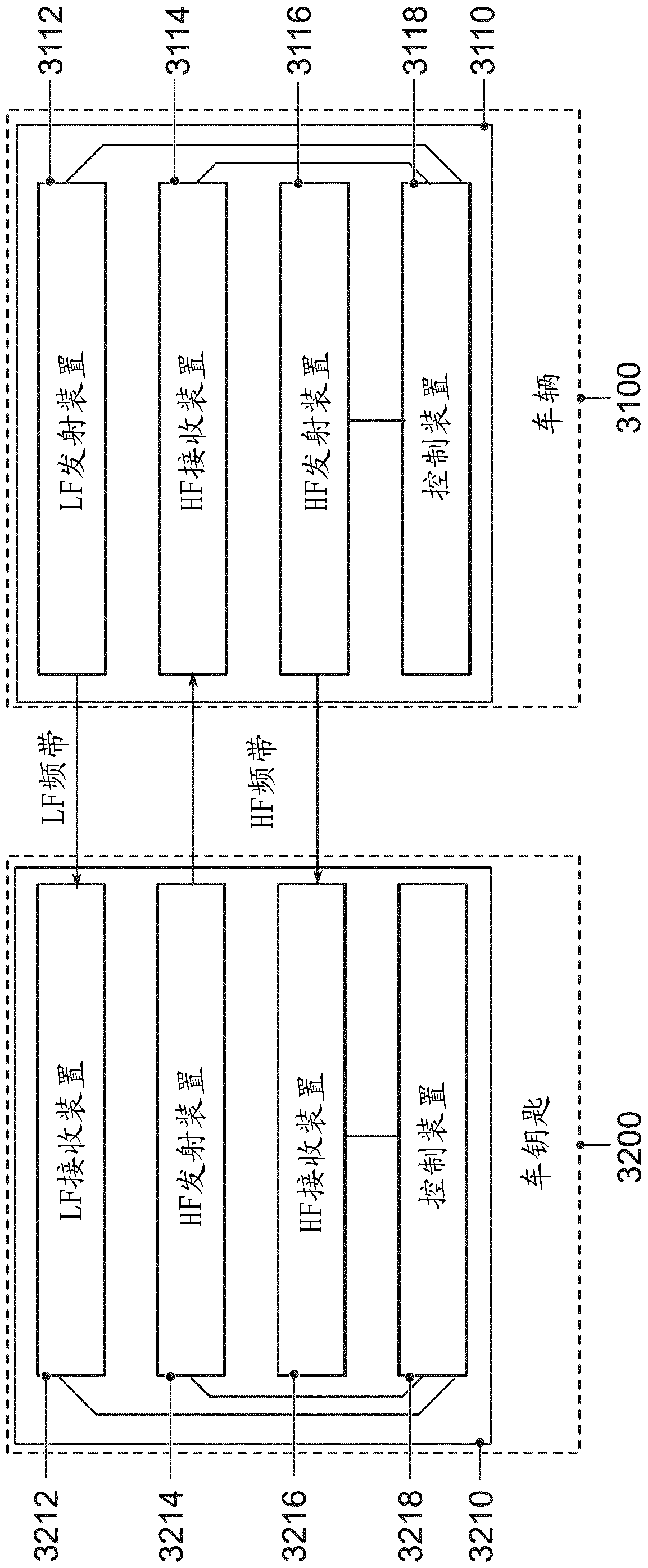
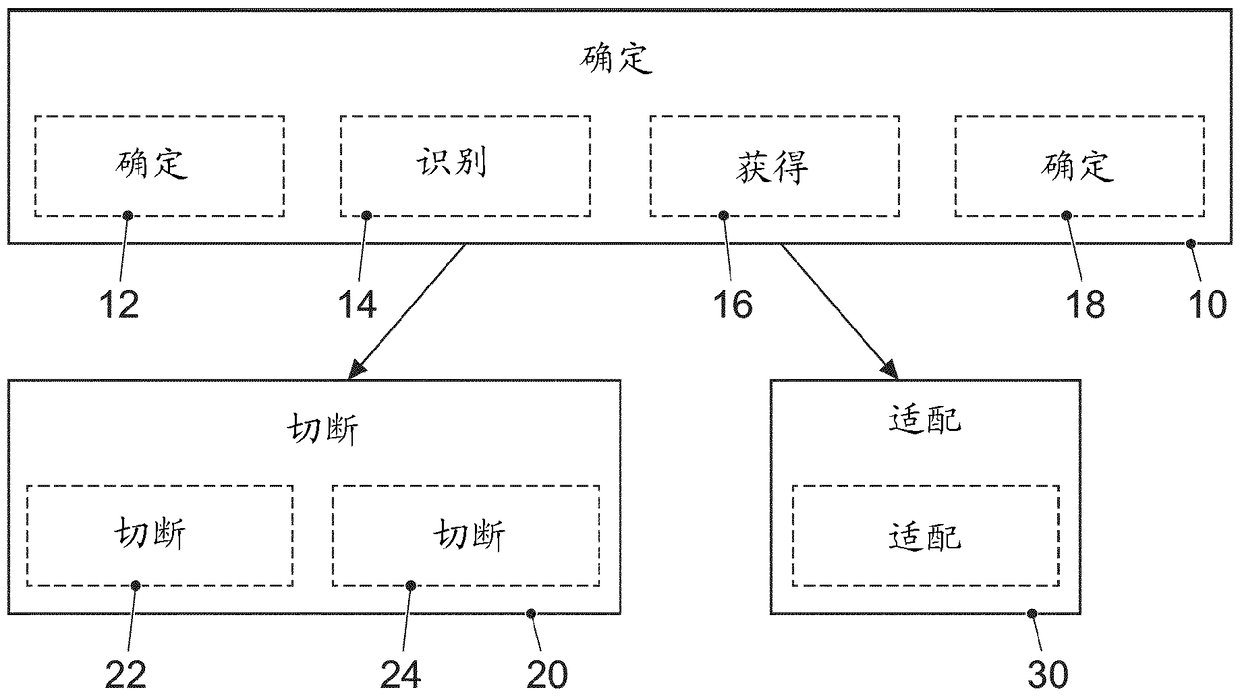
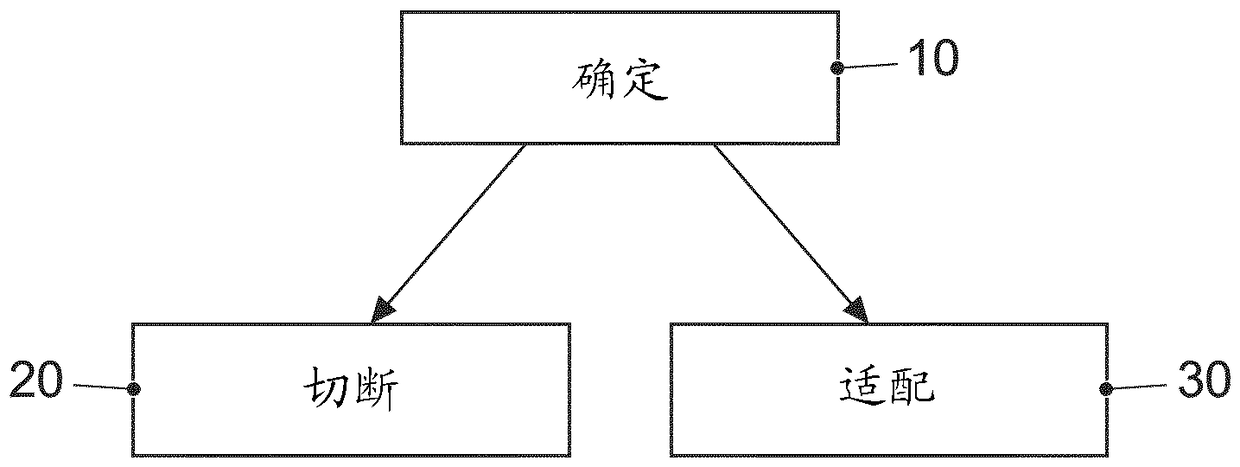
[0025] Different embodiments are now described in more detail with reference to the accompanying drawings in which some embodiments are shown. In the drawings, the thickness dimensions of lines, layers and / or regions may be shown exaggerated for clarity.
[0026] In the ensuing description of the accompanying drawings, which show only some exemplary embodiments, like reference numerals may designate like or similar components. Furthermore, general reference signs may be used for components and objects which appear several times in the exemplary embodiment or in the figures, but which are however commonly described with respect to one or more features. Components or objects described with the same or general reference numerals can relate to single, multiple or all features (such as the component or The size of the object) is implemented identically, but possibly also differently.
[0027] Although the embodiments may be modified and altered in various ways, the embodiments ar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com