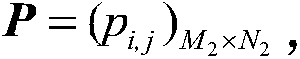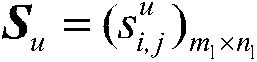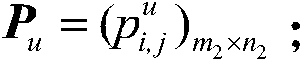Secret image camouflage recovery method by combining secret key and random orthogonal tensor basis
A key and secret image technology, which is applied in image data processing, graphics and image conversion, instruments, etc., can solve the problem that the mean block and the difference block do not satisfy the orthogonal relationship, cannot be restored, and cannot guarantee the accurate reconstruction and acquisition of secret image and audio High-precision secret image audio and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0120] The present invention is described in further detail below in conjunction with accompanying drawing:
[0121] The following takes JAVA jdk1.7.0_09 as an example implementation environment, and describes the implementation of the present invention in detail in conjunction with the accompanying drawings, wherein figure 1 is the embedded flowchart, figure 2 is the extraction flow chart.
[0122] Step 1: Pick a secret image such as image 3 As shown, it is an 8-bit grayscale image with a resolution of 512×512. Select a public image, such as Figure 4 As shown, it is an 8-bit grayscale image with a resolution of 512×512, that is, r=8; take m 1 = 4, n 1 = 4, m 2 = 4, n 2 = 4, that is, both the secret image and the public image are divided into 4×4 blocks, and the secret image and the public image can be divided into K=16384 small blocks in total, and the image small blocks corresponding to the secret image and the public image are respectively used as secret small bloc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com