Relationship chain creation method, device, server, terminal, storage medium
A relationship chain and terminal technology, applied in the computer field, can solve problems such as incomplete relationship chain and difficult to eradicate viruses, and achieve the effect of improving protection ability and complete protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
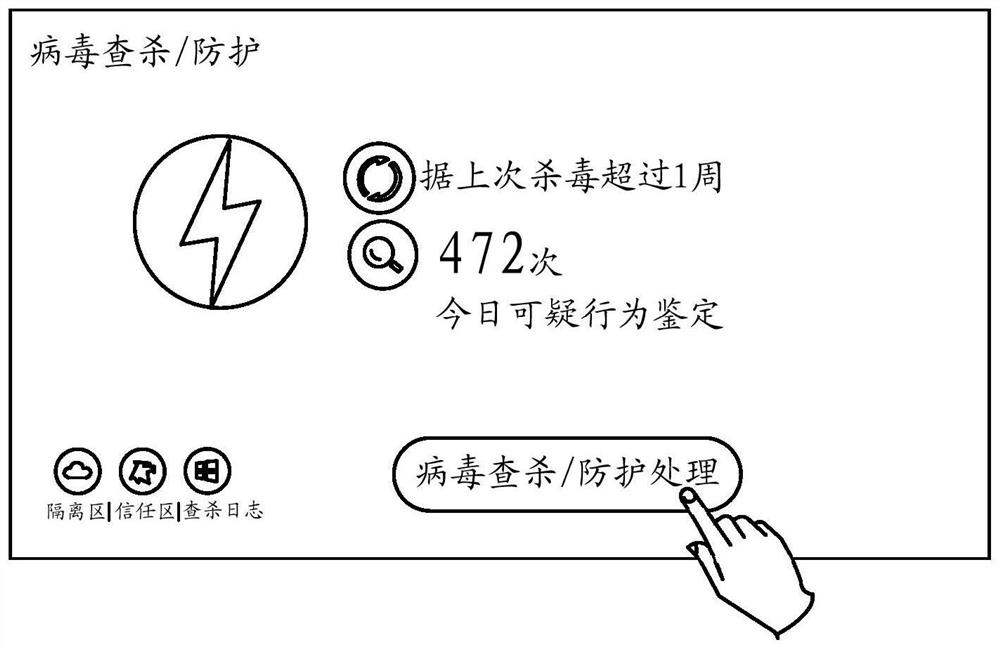
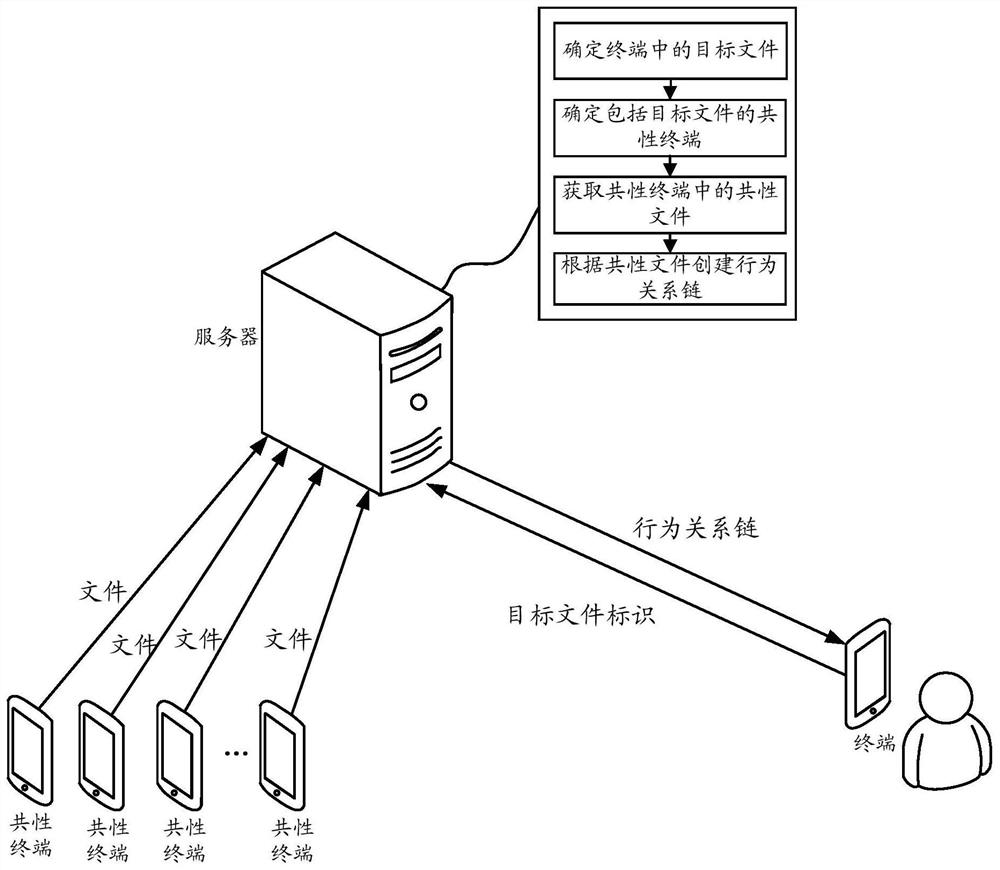
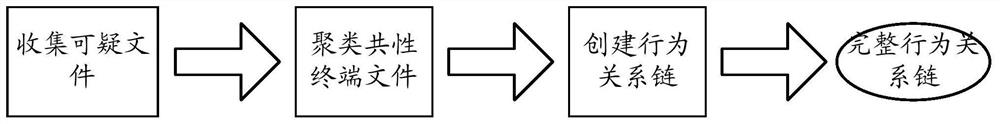
[0053] In the embodiment of the present invention, the terminal may provide a user interface, and provide a virus killing / protection processing button in the user interface. Such as figure 1As shown in , the user can click this button to instruct the terminal to perform virus scanning / protection processing. When the terminal detects that the user clicks the button, it can perform file detection on the files in the terminal. If a suspicious file is found, the suspicious file will be used as the starting file for behavior relationship chain detection, so as to perform behavior relationship chain detection. In an embodiment, the suspicious file here may refer to a file detected by the terminal with specified file behavior data, and the specified file behavior data is used to record the specified behavior of the suspicious file, and the specified behavior may be: encrypting other files behavior, behavior that destroys other files, and so on. For example, if a file encrypts other...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com