Mobile terminal authentication method and system
A mobile terminal and authentication technology, applied in the field of information security, can solve the problems of easy cracking of the login interface, weak confidentiality, high cost, etc., and achieve the effect of complete protection, no cost, and stable performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
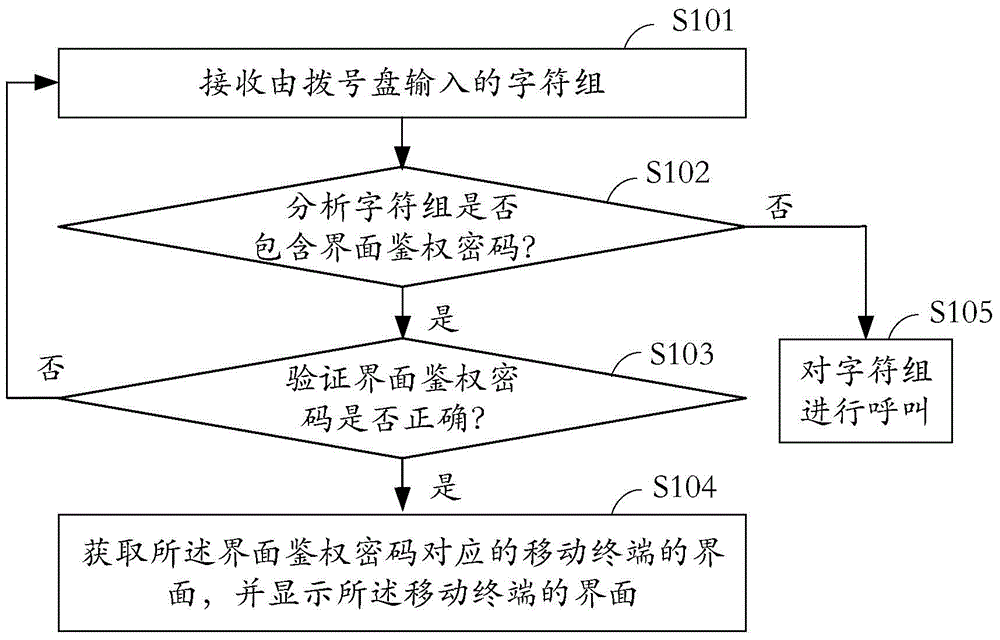
[0027] see figure 1 , which is a schematic flowchart of an authentication method for a mobile terminal. The authentication method shown is mainly applied to mobile phones, and can also be applied to other smart terminals with a dial-up function, such as smart glasses, smart watches, etc., which are not listed here.
[0028] The authentication method includes the following steps:
[0029] In step S101, a character group input by a dial pad is received.
[0030] It can be understood that, the interface of the dial pad is usually set with a total of 12 characters from 0 to 9, * and # to choose from. The dial includes: a push-button dial, a dial displayed on a touch screen, and a projection dial.
[0031] In step S102, it is analyzed whether the character group contains an interface authentication password. Wherein, if the character group includes the interface authentication password, execute step S103; if the character group does not include the interface authentication pass...
Embodiment 2
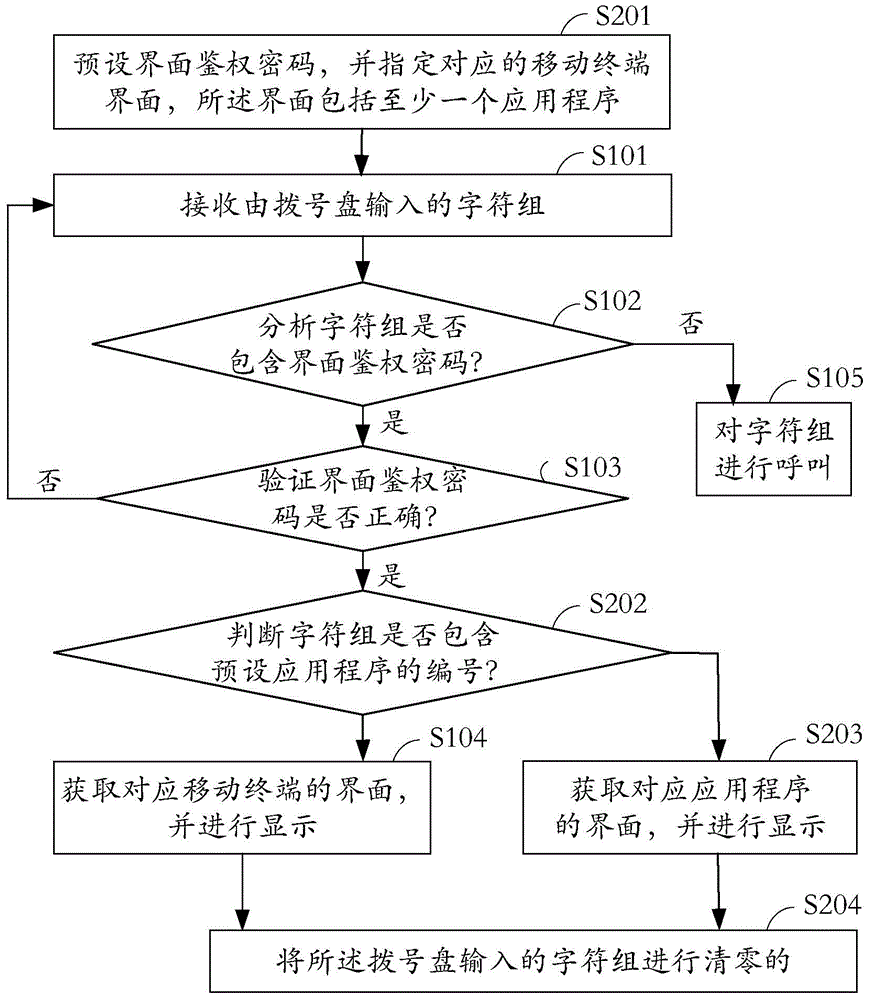
[0049] see figure 2 , which is a schematic flowchart of an authentication method for a mobile terminal. The authentication method shown is mainly applied to mobile phones, and can also be applied to other smart terminals with a dial-up function, such as smart glasses, smart watches, etc., which are not listed here.
[0050] Understandably, figure 2 Yes figure 1 Flow optimization of the authentication method shown. Among them, in order to reflect the figure 1 Zhongyuan steps with figure 2 The difference between the optimization steps in , the original step starts with S10, and the optimization step starts with S20. The following steps are performed in the order in which they appear, unless otherwise indicated.
[0051] In step S201, an interface authentication password is preset, and a mobile terminal interface corresponding to the interface authentication password is specified, and the interface includes at least one application program.
[0052] It can be understood...
Embodiment 3
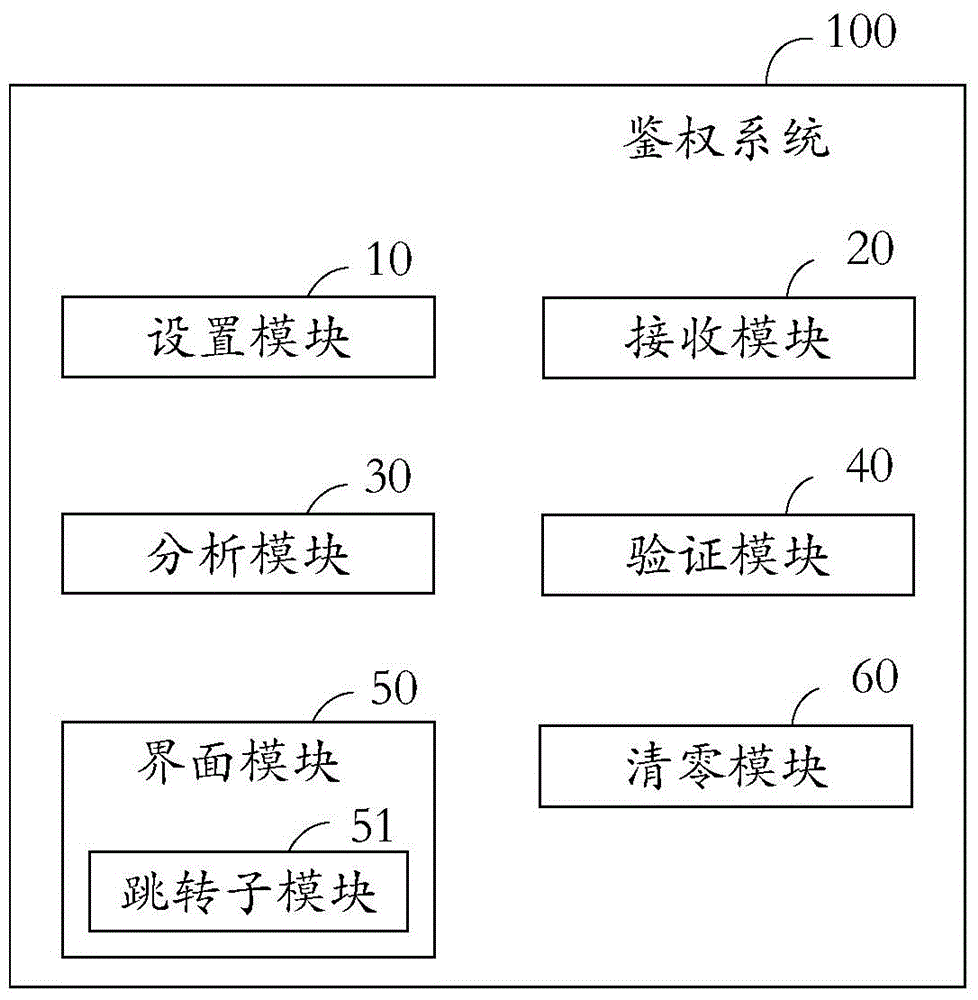
[0074] see image 3 , shows the block diagram of the authentication system. The authentication system 100 includes: a setting module 10 , a receiving module 20 , an analysis module 30 , a verification module 40 , an interface module 50 , and a reset module 60 .
[0075] Specifically, the setting module 10 is configured to preset an interface authentication password, and designate a mobile terminal interface corresponding to the interface authentication password, and the interface includes at least one application program.
[0076] It can be understood that each interface authentication password corresponds to an interface of a mobile terminal, and there are multiple application programs in different interfaces. The number of the application program is defined by the user, for example, the number of the railway ticket booking program is 12306 or 003.
[0077] Wherein, the interface authentication password includes at least one preset character, wherein the preset character ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com