User mobile phone safety privacy protection method based on two-dimensional codes
A privacy protection and mobile phone security technology, applied in the field of private calls, can solve the problems of waste of communication service resources, secondary leakage, etc., and achieve the effect of reducing operating costs, avoiding secondary leakage, and enhancing privacy protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The specific implementation of the invention will be further described below in conjunction with the accompanying drawings.
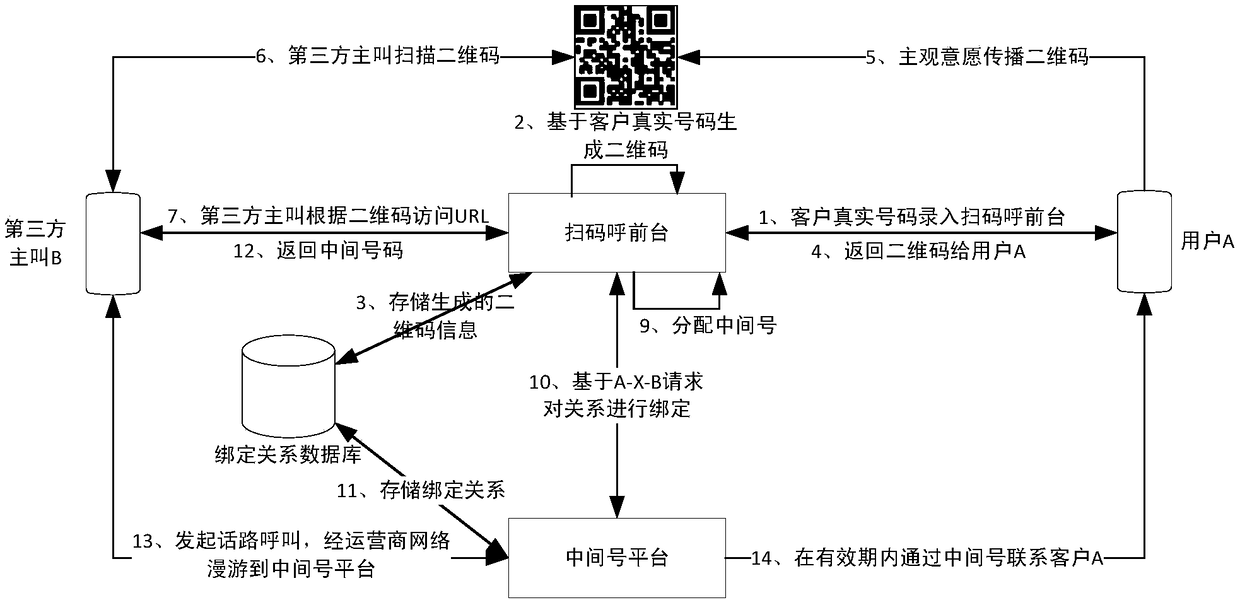
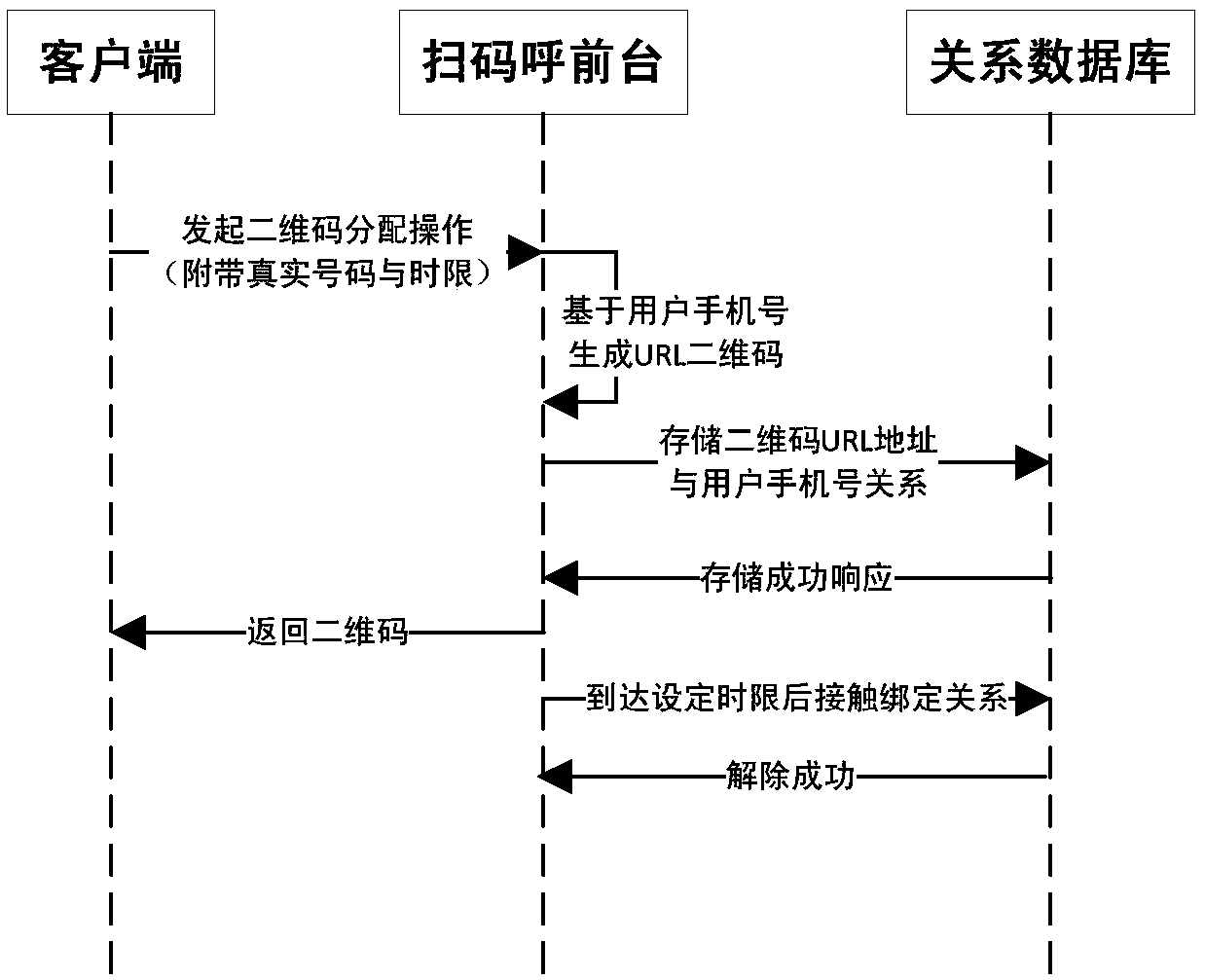
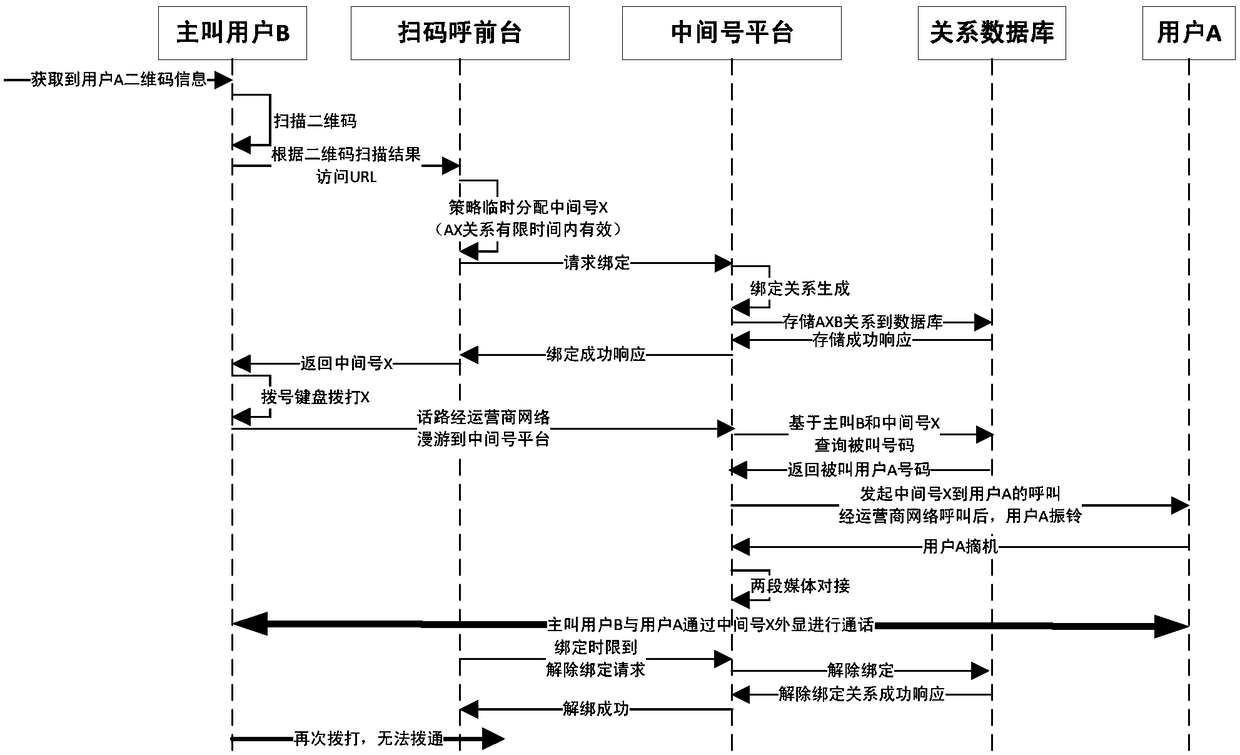
[0039] Such as figure 1 As shown, it is a functional schematic diagram of the system of the present invention, which includes a client, which is installed and installed in the user's mobile phone to scan the code to call the front desk, to respond to the request from the client, to generate a two-dimensional code, identify two-dimensional code information and complete the intermediate The code number is dynamically assigned; the mapping relationship between the QR code and the user's mobile phone number is generated. The intermediate number platform is linked with the code scanning front desk and the telecom core network, and is used to respond to the binding service request from the scanning code calling front desk; generate a code number binding relationship. The relational database is connected with the QR code scanning front desk and the int...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com