Key configuration method, device and system
A configuration method and key technology, applied in the field of communication, can solve the problems that the negotiation mechanism of LTE cannot be directly applied to 5G communication, does not support business-based security policy negotiation, and does not support differentiated security protection, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
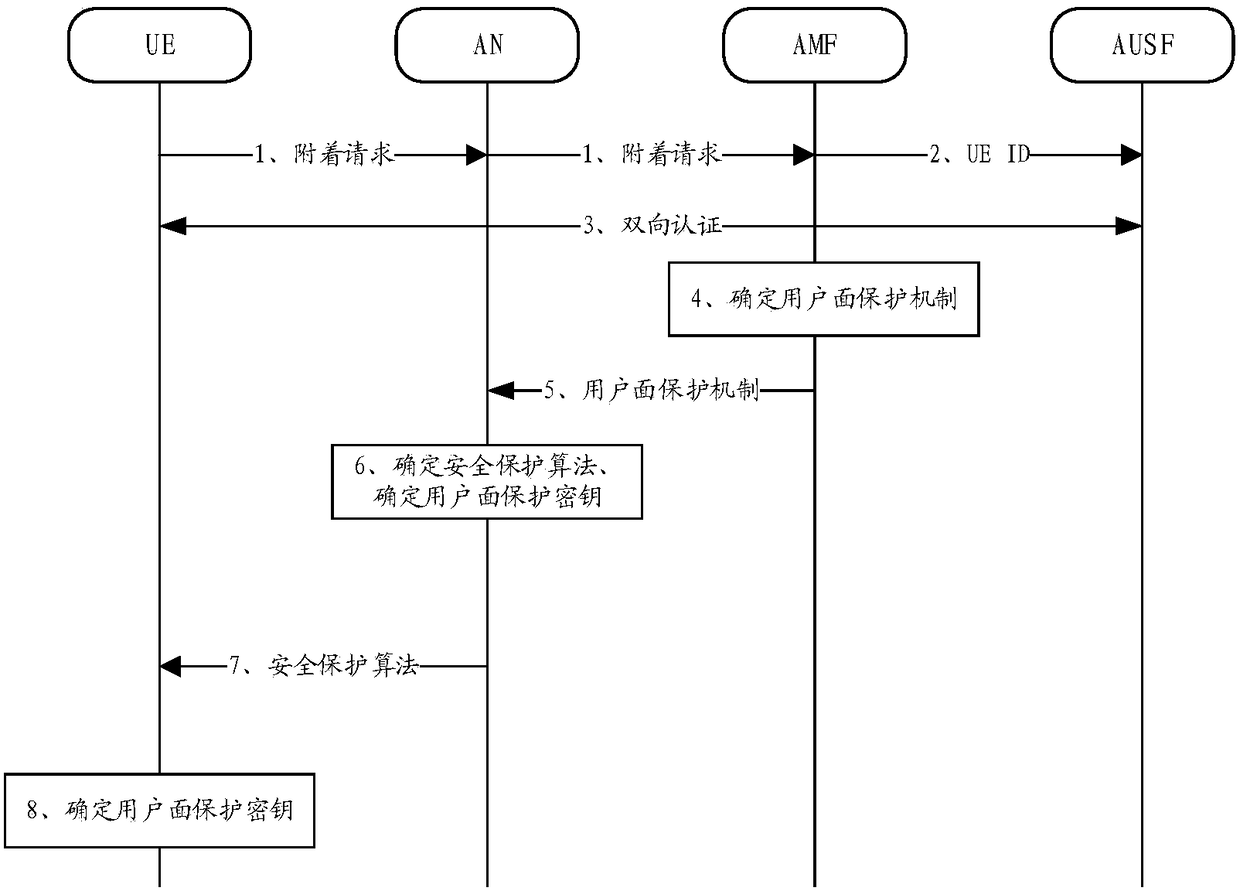
[0274] Possibility 1: If the AMF does not need indicator information in the process of determining the user plane protection mechanism, the UE may not send the indicator to the network side (or the indicator may not be included in the attachment request).
[0275] Possibility 2: This embodiment does not limit the sequence of the above process steps. For example, AMF can determine the user plane protection mechanism before the two-way authentication (that is, step 4 can be placed before step 3).
[0276] It should also be noted that the above image 3 The embodiment is only an example and should not be regarded as a limitation to the present invention.
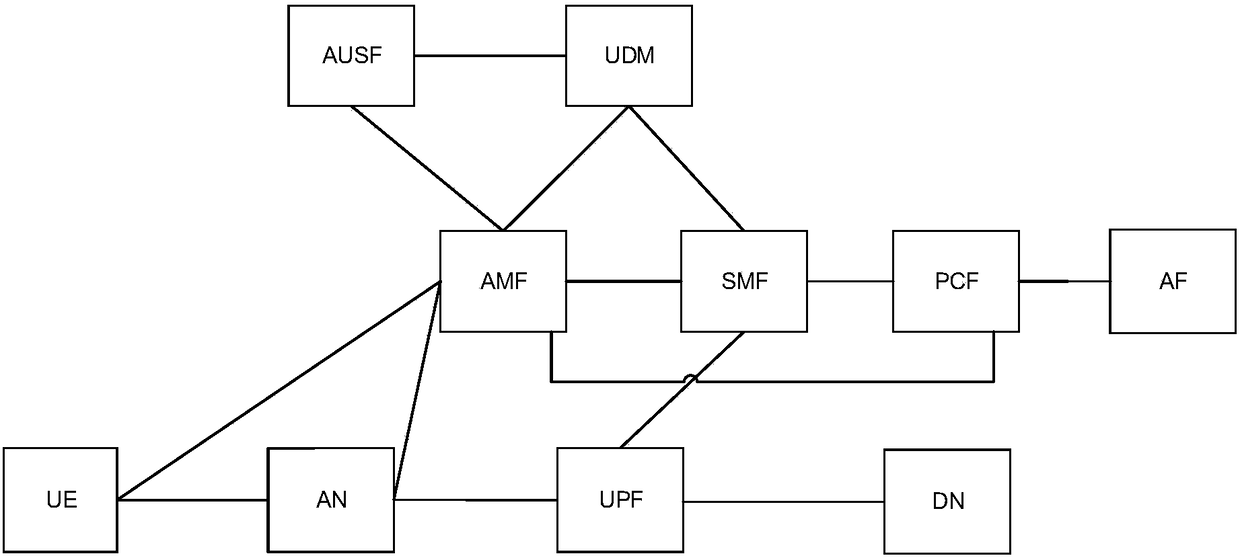
[0277] It can be seen that the implementation of the embodiments of the present invention can realize the communication architecture based on the future 5G. In the process of attaching to the network, the UE-AN completes the policy negotiation, and the AMF is used according to the security requirements of the user equipment side (inclu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com