Method, device, and system for controlling device access authority
A technology of access control and device access, applied in transmission systems, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
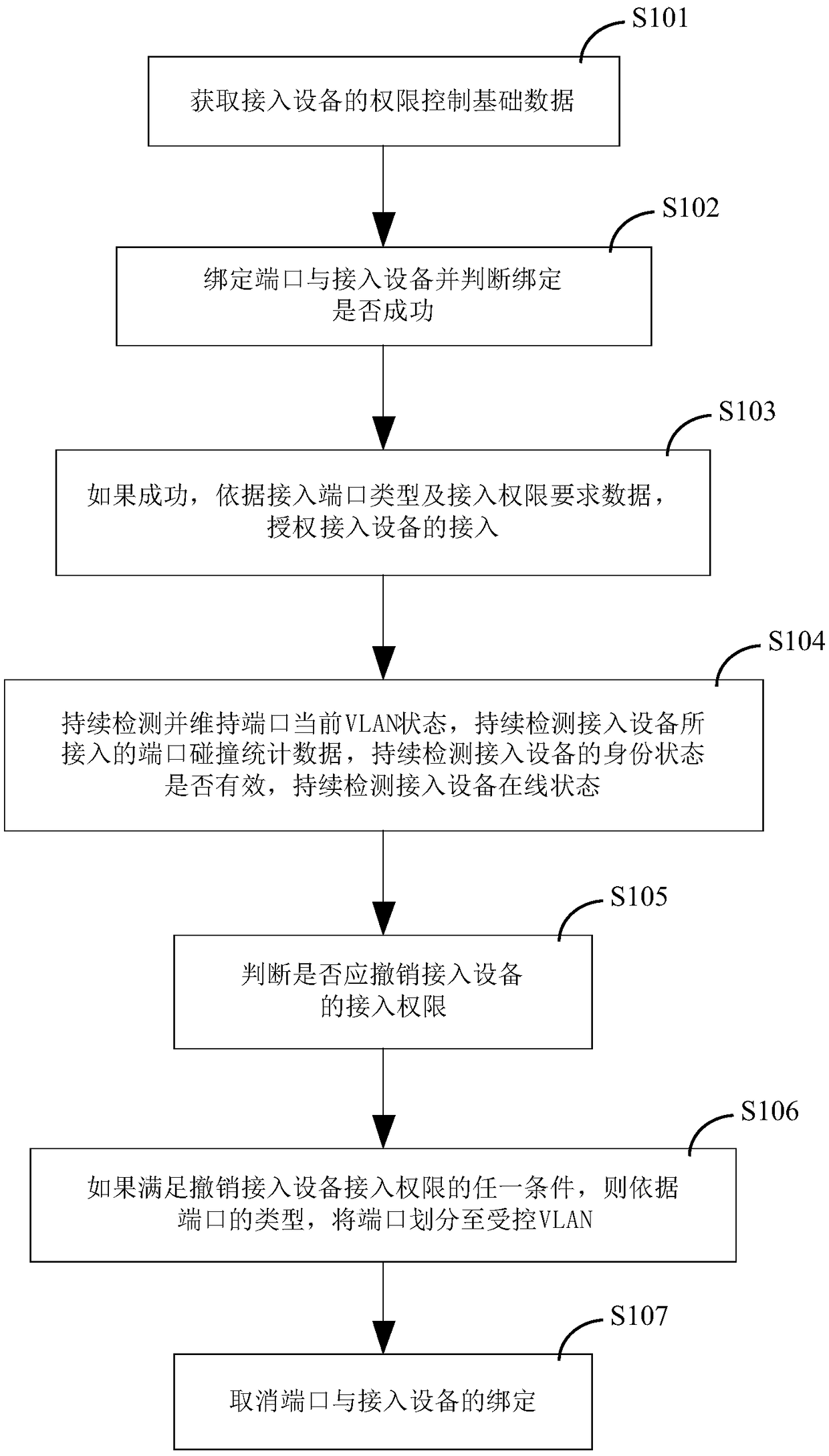
[0239] as attached figure 1 As shown, an embodiment of a device access authority control method, which is used to control the authority of access device 30, specifically includes the following steps:
[0240] S101) Obtain the basic authority control data of the access device 30, the basic authority control data of the access device 30 at least includes access authority requirement data, the identification and type of the port 101 accessed by the access device 30;
[0241] S102) Bind the port 101 and the access device 30 and determine whether the binding is successful;
[0242] S103) If the binding is successful, authorize the access of the access device 30 according to the type of the accessed port 101 and the access authority requirement data;
[0243] S104) continuously detect and maintain the current VLAN state of the port 101, continuously detect the collision statistics of the port 101, continuously detect whether the identity status of the access device 30 is valid, and...
Embodiment 2
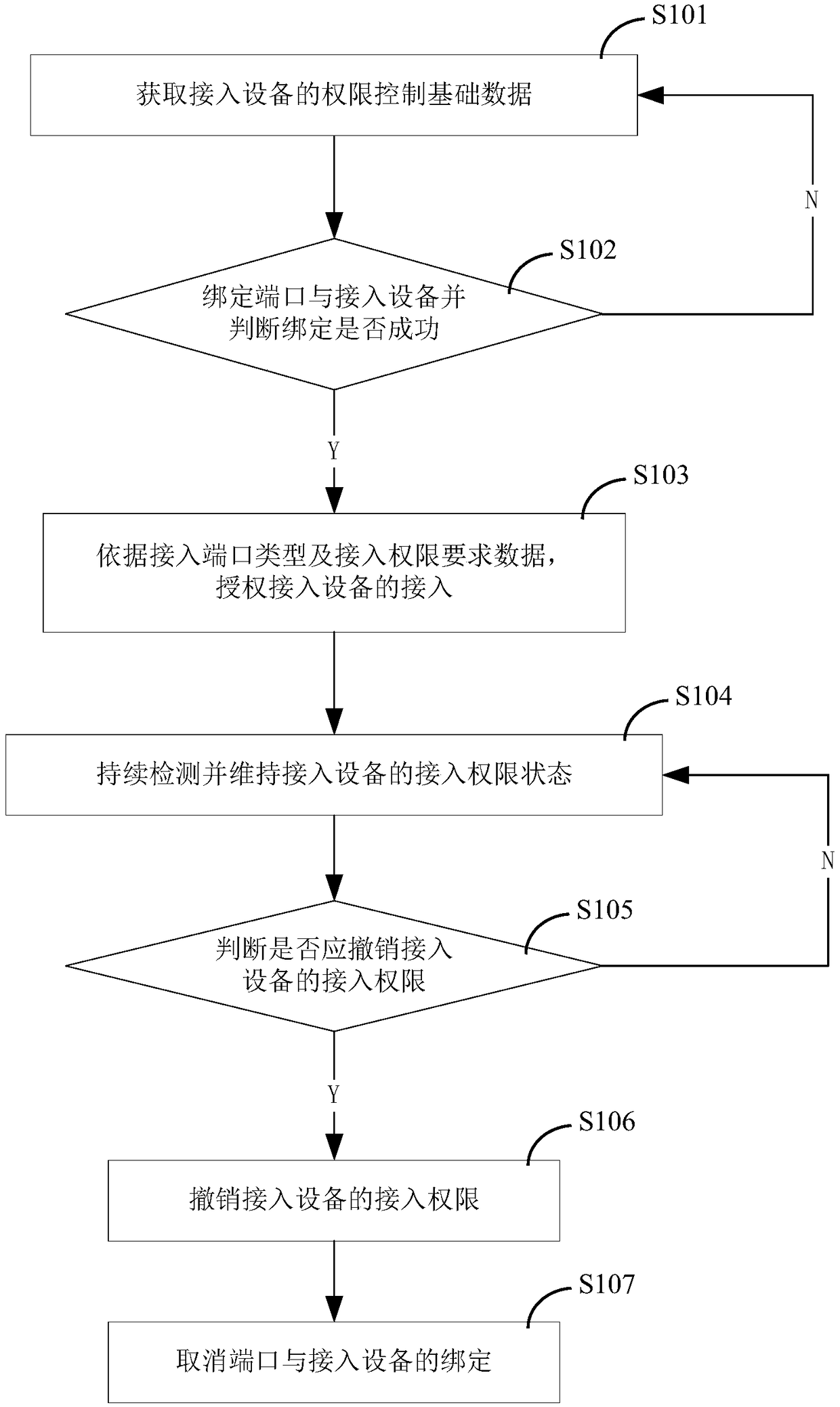
[0292] as attached figure 2 As shown, another embodiment of the device access authority control method is used to control the authority of the access device 30, which is characterized in that it specifically includes the following steps:
[0293] S101) Acquiring basic authority control data of the access device 30;
[0294] Obtain the identity authentication information of the access device 30 connected to the controlled port;
[0295] According to the identity authentication information of the access device 30, the identity authentication key and authentication rules of the access device 30 are obtained directly or indirectly locally or remotely, and the identity of the access device 30 is successfully authenticated.
[0296] S102) Bind the port 101 and the access device 30 and determine whether the binding is successful;
[0297] The technical solution for binding the port 101 and the access device 30 includes but is not limited to binding the port 101 and the access devi...
Embodiment 3
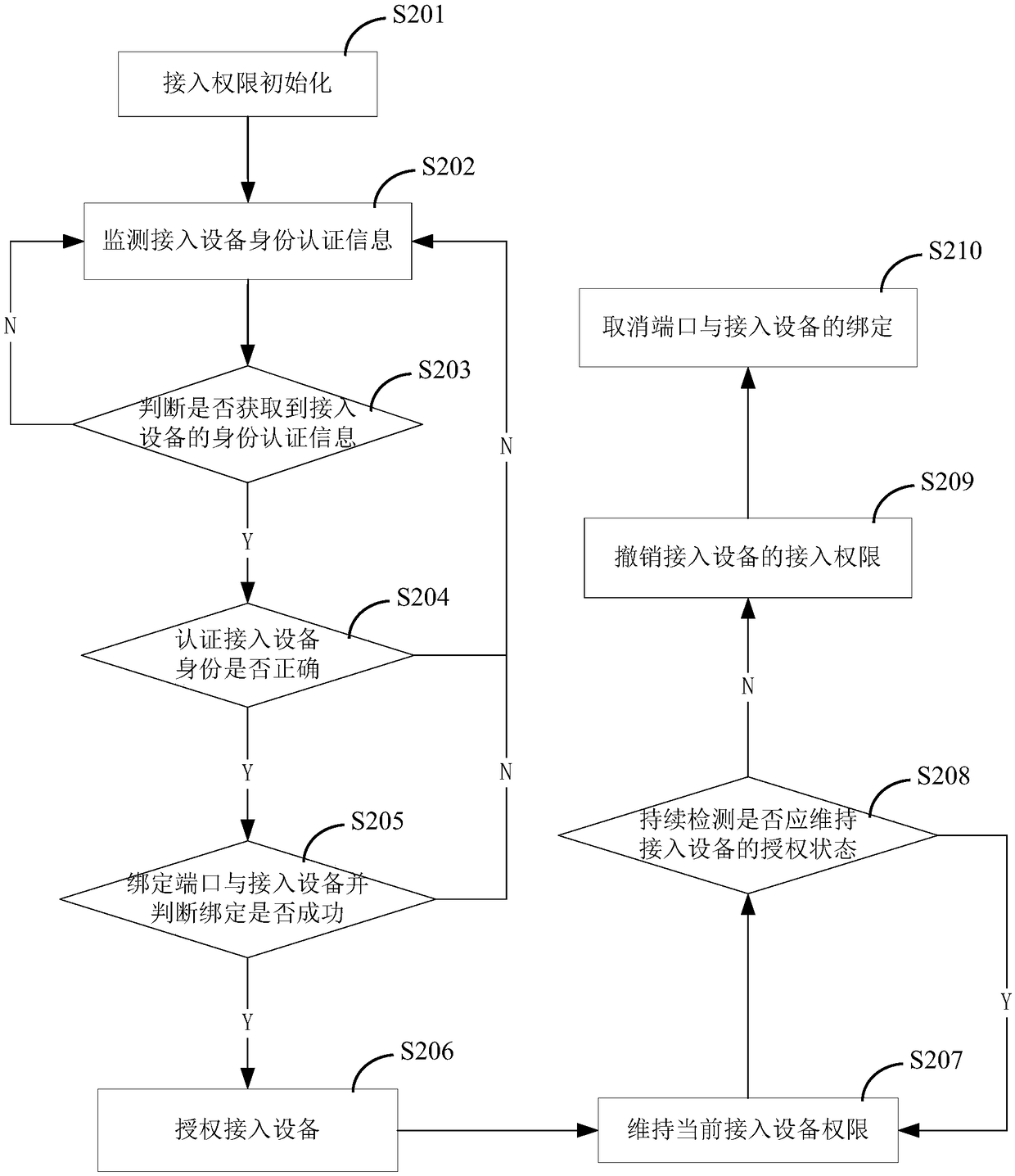
[0324] as attached image 3 As shown, another embodiment of a device access authority control method is used to control the authority of the access device 30, which is characterized in that it specifically includes the following steps:
[0325] S201) access authority initialization;
[0326] According to the design data requirements, create all VLANs, and divide all VLANs into controlled VLANs and normal VLANs. The device requesting cross-VLAN communication in a way prohibits the cross-VLAN communication between the controlled VLAN and the normal VLAN; its effect is to cut off the communication channel between the terminal equipment 30 in the controlled VLAN and the terminal equipment 32 in the normal VLAN, preventing unauthorized The access device 30 in the authorized controlled VLAN communicates with the terminal device 32 in the normal VLAN through cross-VLAN technology, cancels the permission of the non-default authorized fixed terminal device to access the normal VLAN, c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com