Threshold recovery method and system for private key storage
A recovery method and private key technology, applied in the Internet field, can solve problems such as inconvenient use and limited performance of security chips, and achieve the effect of avoiding limited use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
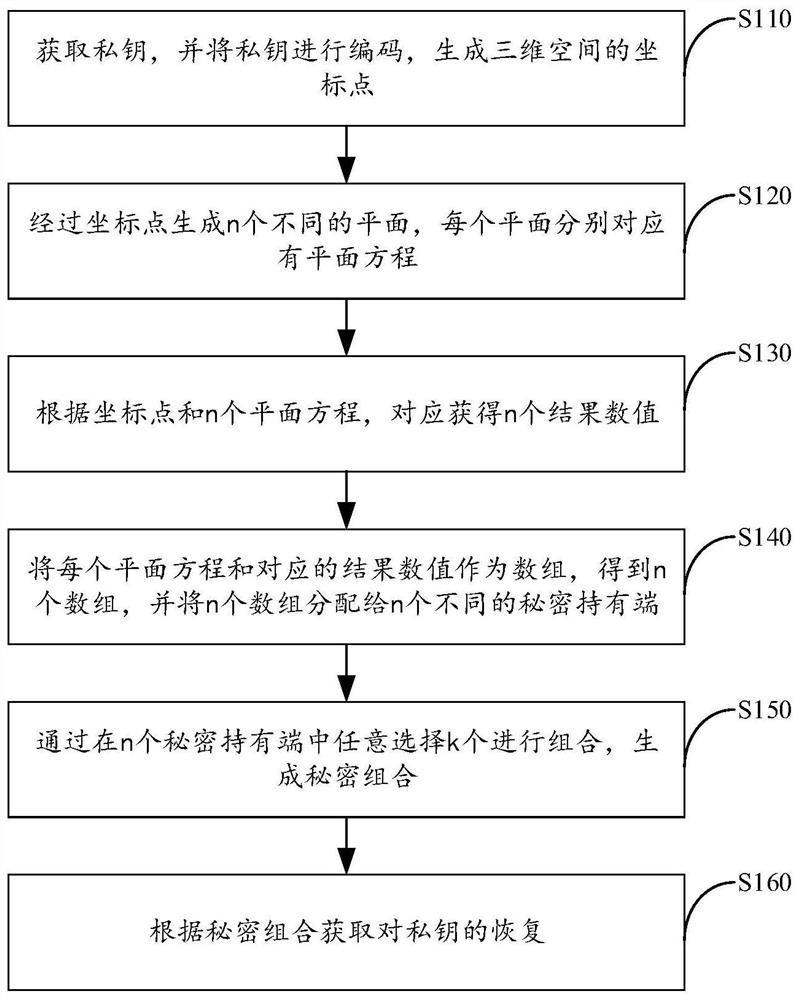
[0056] figure 1 It is a flow chart of the threshold recovery method for private key storage provided by Embodiment 1 of the present invention.
[0057] The general idea of the threshold recovery method for private key storage provided in this embodiment is based on the shamir(k, n) threshold secret sharing scheme, that is, any k of n individuals can provide keys to restore the entire encrypted content, and any k -1 person cannot restore the entire content, choose k and n to be odd numbers. In the embodiment, a total of k-1 partners and the cloud are selected as the secret holder to store the secret scheme. The secret scheme itself has nothing to do with the private key and can be encrypted by the public key of the secret holder to avoid the secret being collected publicly. The user himself stores a secret recipe in a flexible manner. According to the (k, n) threshold secret sharing scheme, the key can be recovered by collecting k secrets. However, as the partner of the se...
Embodiment 2
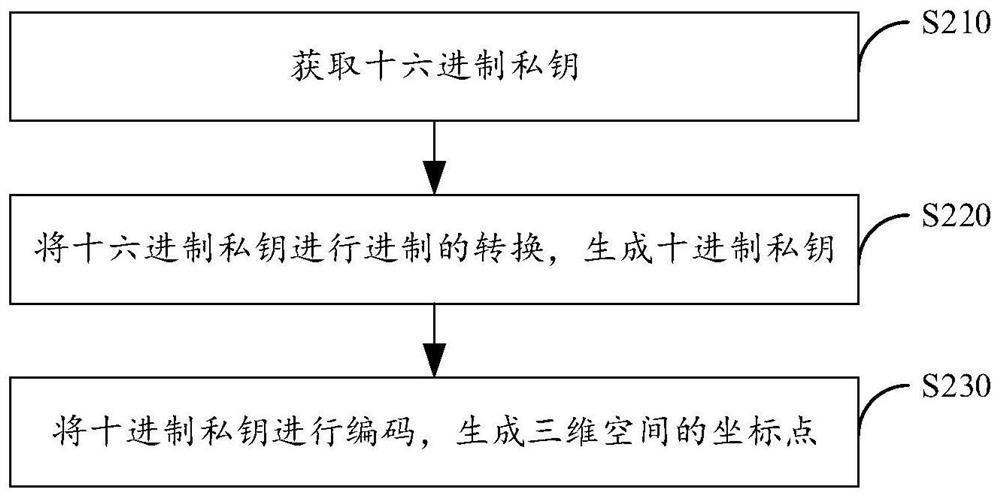
[0072] figure 2 It is a flow chart of the private key encoding method provided by Embodiment 2 of the present invention.
[0073] This embodiment describes each step of the threshold recovery method for private key storage provided in the above embodiments by using examples.
[0074] In step S110 of the threshold recovery method for private key storage, refer to figure 2 , the process of encoding the private key includes:
[0075] Step S210, obtaining a hexadecimal private key;
[0076] Step S220, converting the hexadecimal private key to a decimal system to generate a decimal private key;
[0077] Step S230, encoding the decimal private key to generate coordinate points in three-dimensional space.
[0078] Specifically, take the hexadecimal private key as an example:
[0079] A90C28B2861B5D47F339599753A2387A86A79DBC88E7AAF0808D02B29C23F0BB;先把十六进制私钥转化为十进制形式:1223397671331149484138190714211802661074685763175964491678362870066873941035952;再把十进制形式的私钥编码成三维空间的坐标点:(12233976713...
Embodiment 3
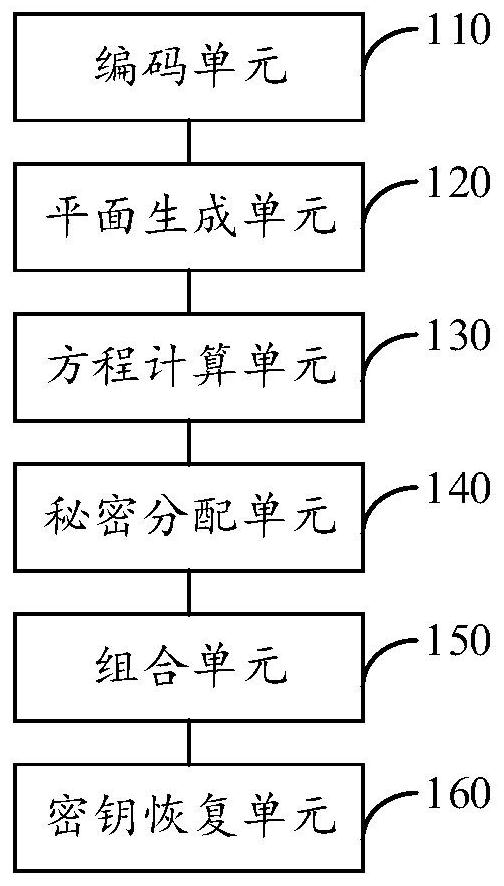
[0089] image 3 It is a schematic diagram of a threshold recovery system for private key storage provided by Embodiment 3 of the present invention.
[0090] The embodiment of the present invention also provides a threshold recovery system for private key storage, which is used to implement the above threshold recovery method for private key storage. refer to image 3 , the threshold recovery system for private key storage includes the following units:
[0091] Encoding unit 110, configured to obtain the private key, and encode the private key to generate coordinate points in three-dimensional space;
[0092] A plane generation unit 120, configured to generate n different planes through the coordinate points, each plane corresponding to a plane equation;
[0093] An equation calculation unit 130, configured to obtain n result values correspondingly according to the coordinate points and n plane equations;
[0094] A secret distribution unit 140, configured to use each pla...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com