Application data obtaining method and device
A technology that applies data and acquisition methods, and is applied to electrical components, transmission systems, etc., to achieve the effect of ensuring safe transmission and improving the security level
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
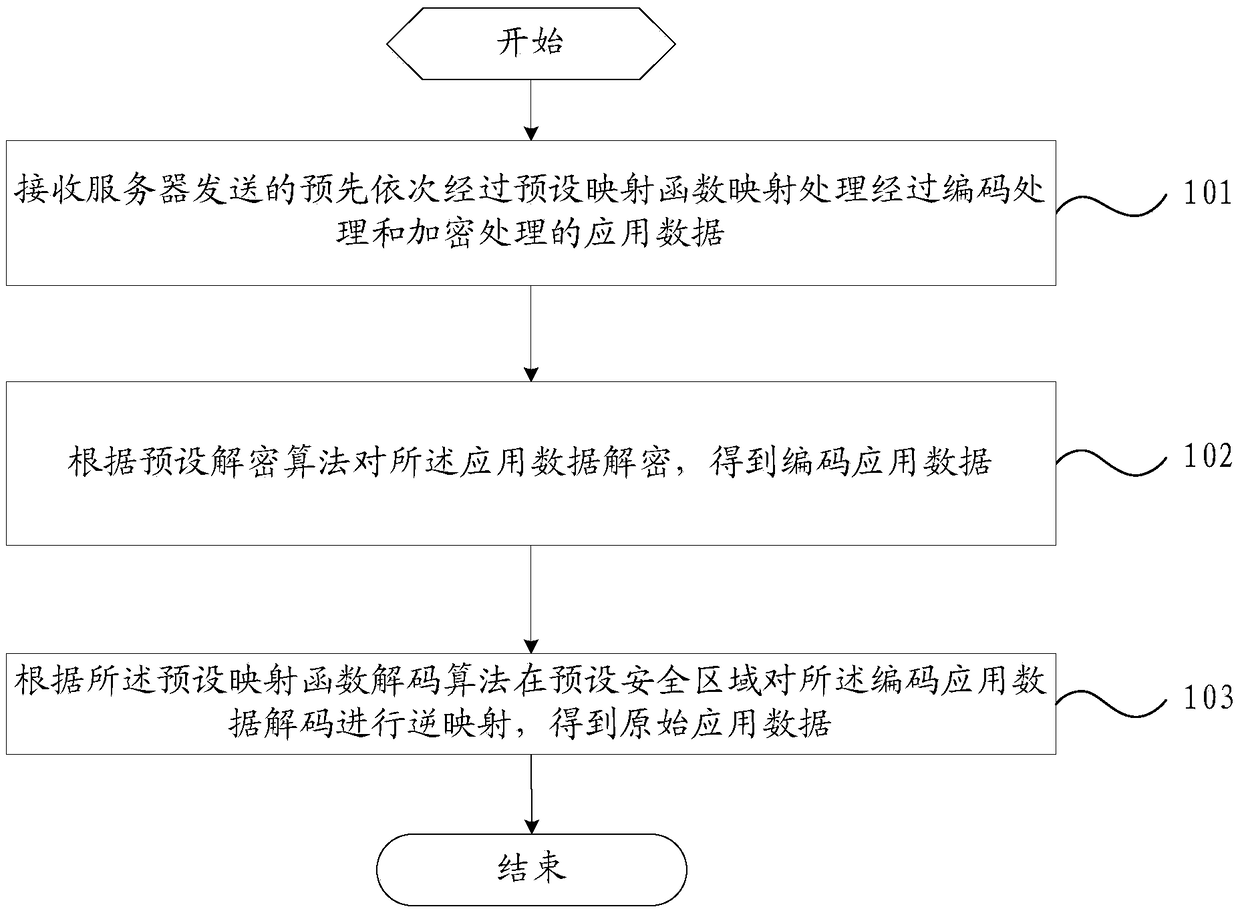
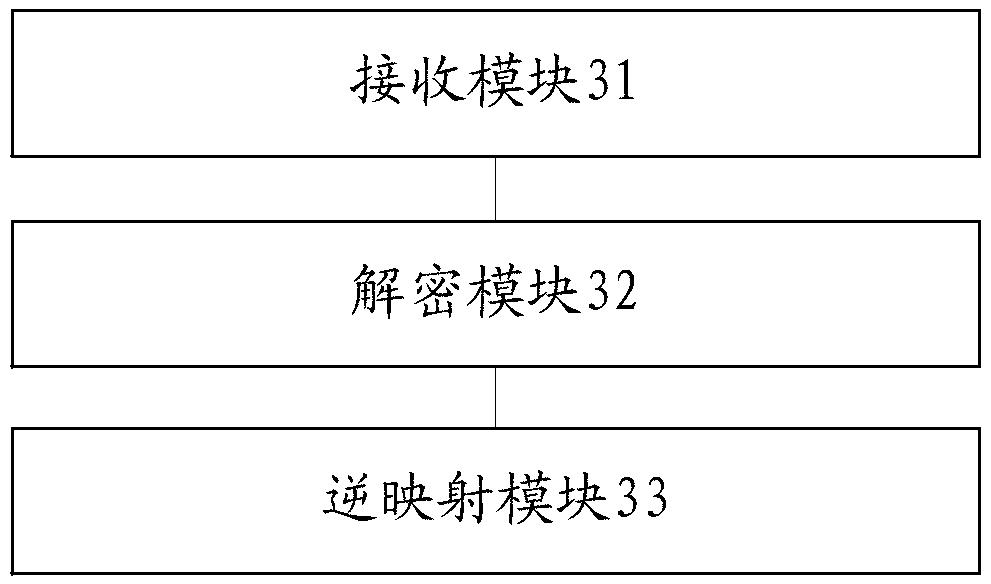
[0033] refer to figure 1 , which shows a flow chart of the steps of an embodiment of a method for obtaining application data according to the present invention, which may specifically include the following steps:
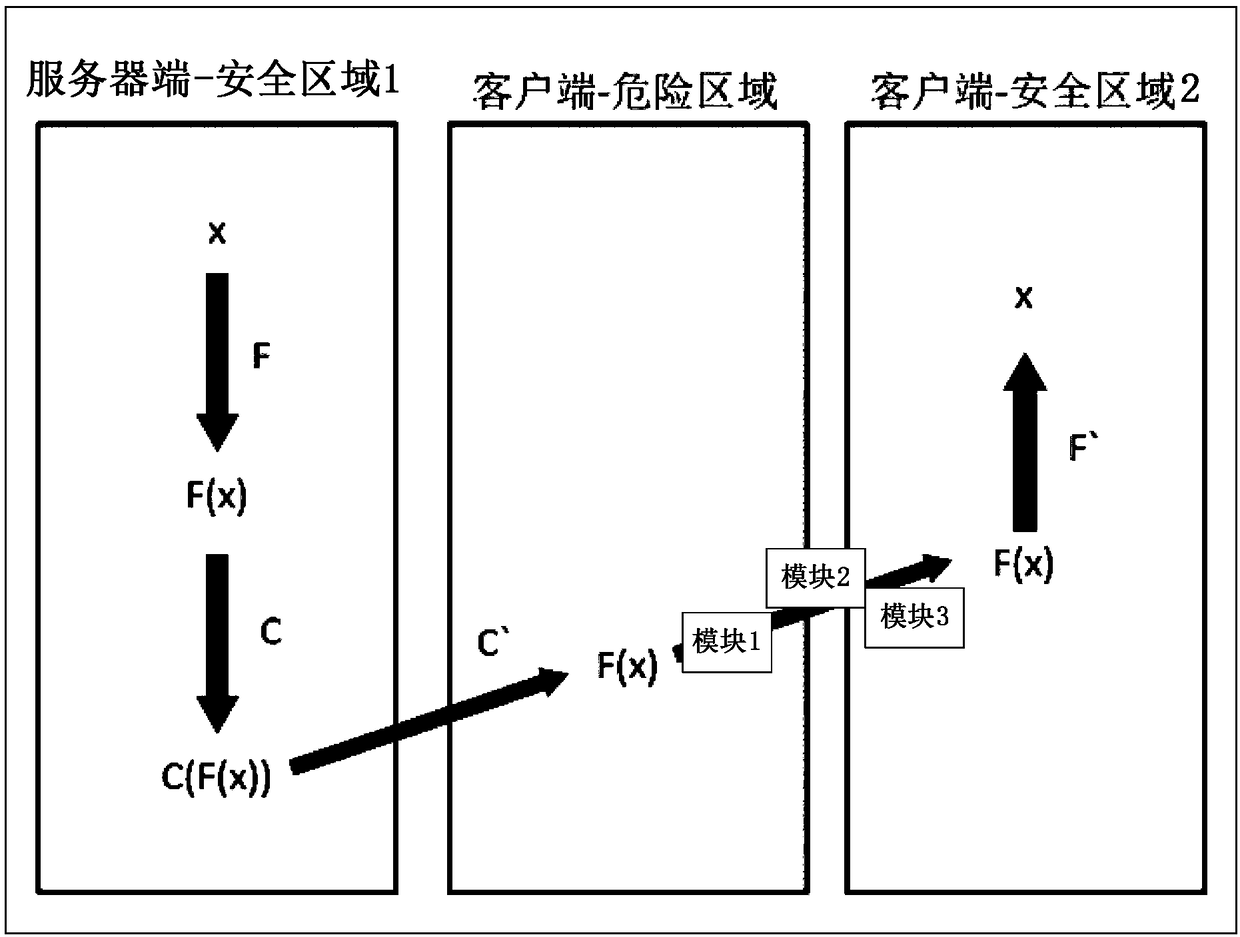
[0034] Step 101, receiving the application data sent by the server that has been mapped and encrypted by a preset mapping function in advance;
[0035] Wherein, the application data may be any type of application data issued by the server of the application program. For example, if the application program is video software, then the user can obtain the video data of a certain movie from the server side of the video software through video downloading. The video data here is an example of the above-mentioned application ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap