Integrated detection method of edge side cloned node based on counterpropagation neural network
A back-propagation and neural network technology, applied in the field of edge-side clone node integration detection, can solve the problems of increasing network transmission load, clone detection delay, and increasing central network computing load.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0090] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings, but the protection scope of the present invention is not limited to the following description.
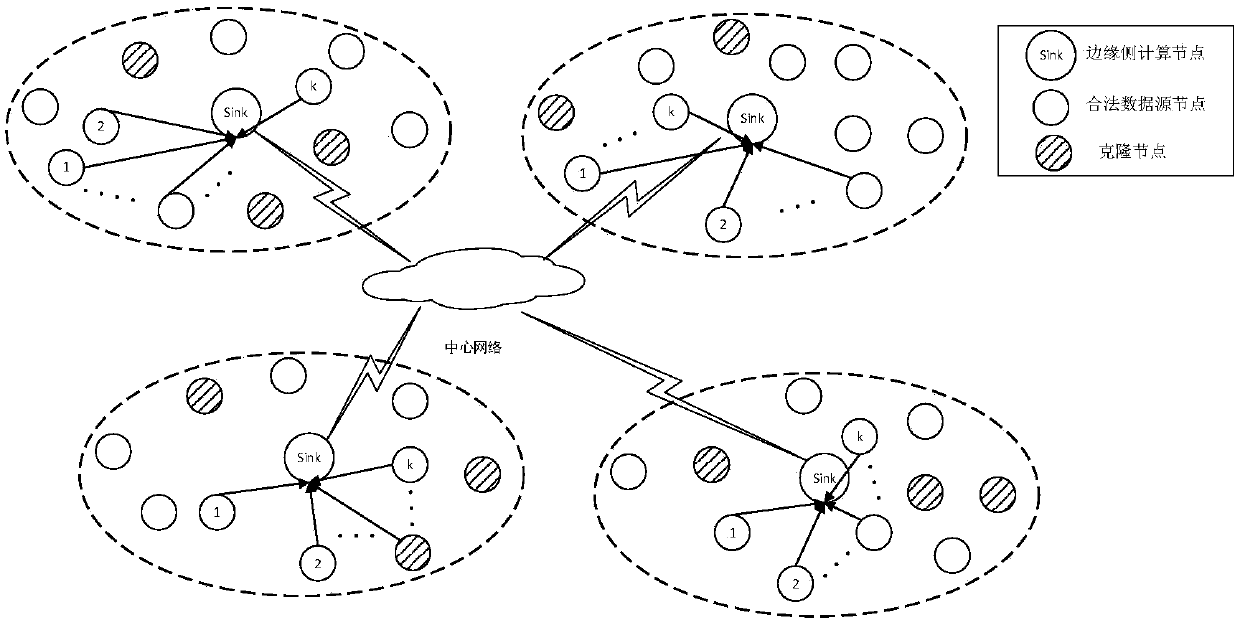
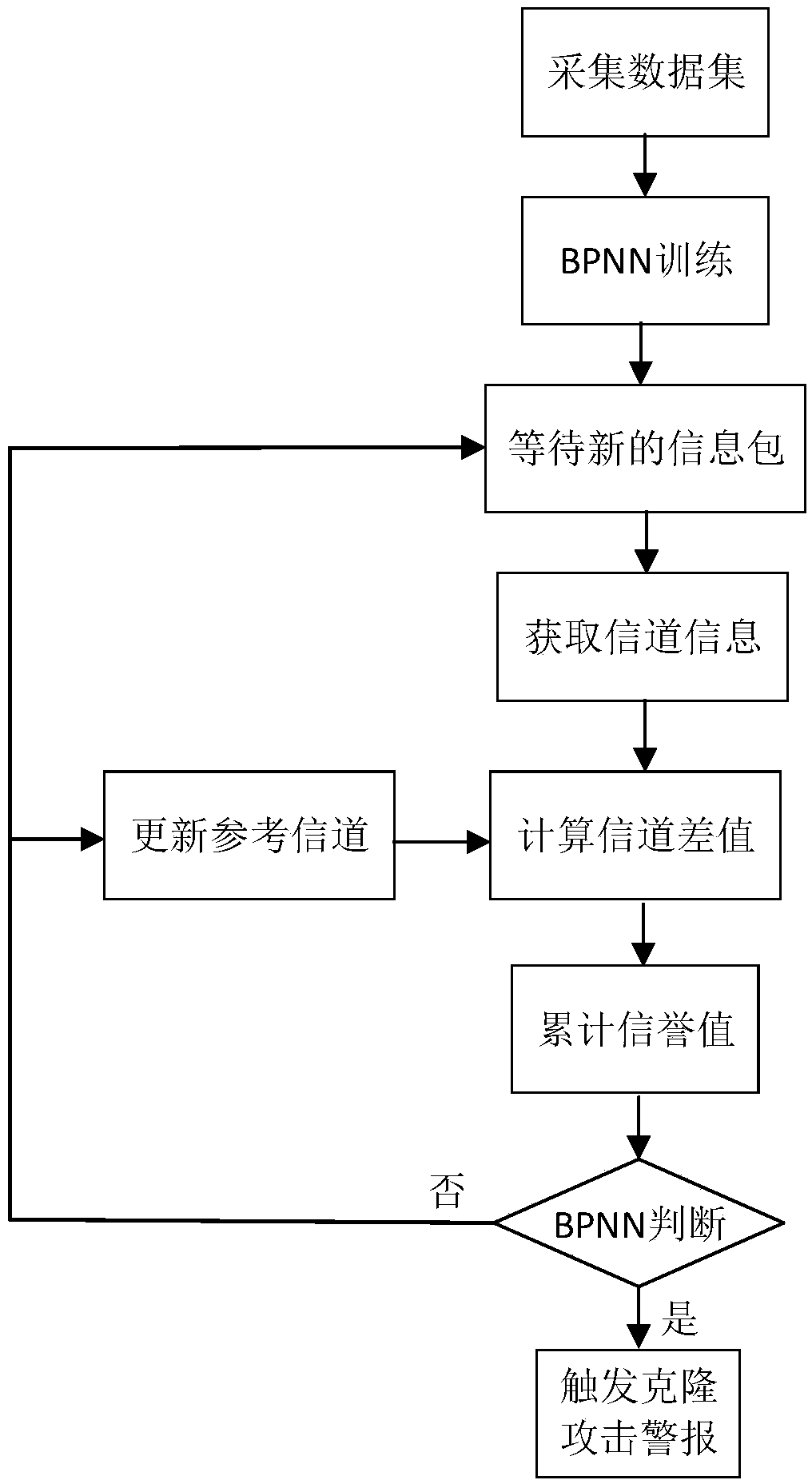
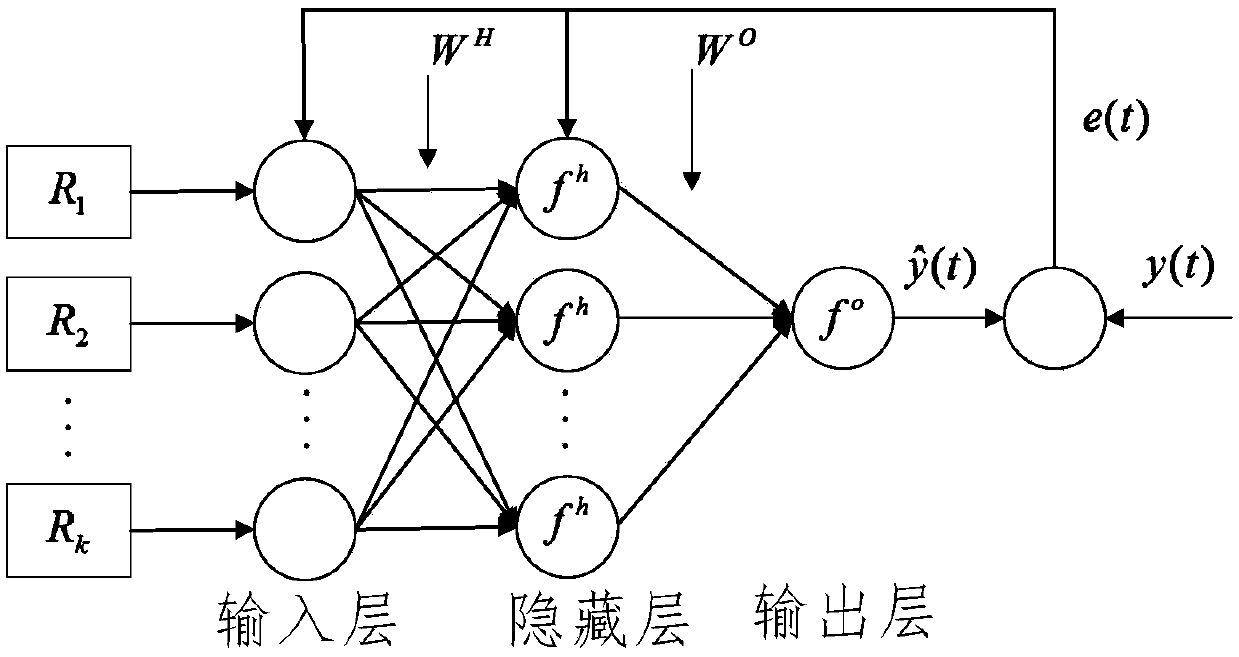
[0091] Such as figure 1 As shown, the present invention is implemented in a network of terminals, nodes, and edge-side computing nodes with legitimate data sources. Clone node attack means that the attacker captures a legitimate data source node and obtains legal information such as its identity ID and key, and clones multiple clone nodes with the same ID at different physical locations in the network, thereby attacking the network. Way. The characteristic of the clone node is that the data sources with the same identity ID are located in different physical locations. The clone detection of the present invention is implemented on the computing nodes at the edge side, and clone attack detection is performed on the data source nodes. In th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com