A device and a method for security lateral comparative analysis of Internet-of-Things
A comparative analysis, Internet of Things technology, applied in the direction of computer security devices, instruments, platform integrity maintenance, etc., can solve problems such as inability to accurately and effectively capture risk activities, low efficiency, lack of security modules, etc., to achieve rapid and efficient risk. Effects of Perception Methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be described in further detail below in conjunction with the examples, but the protection scope of the present invention is not limited thereto.
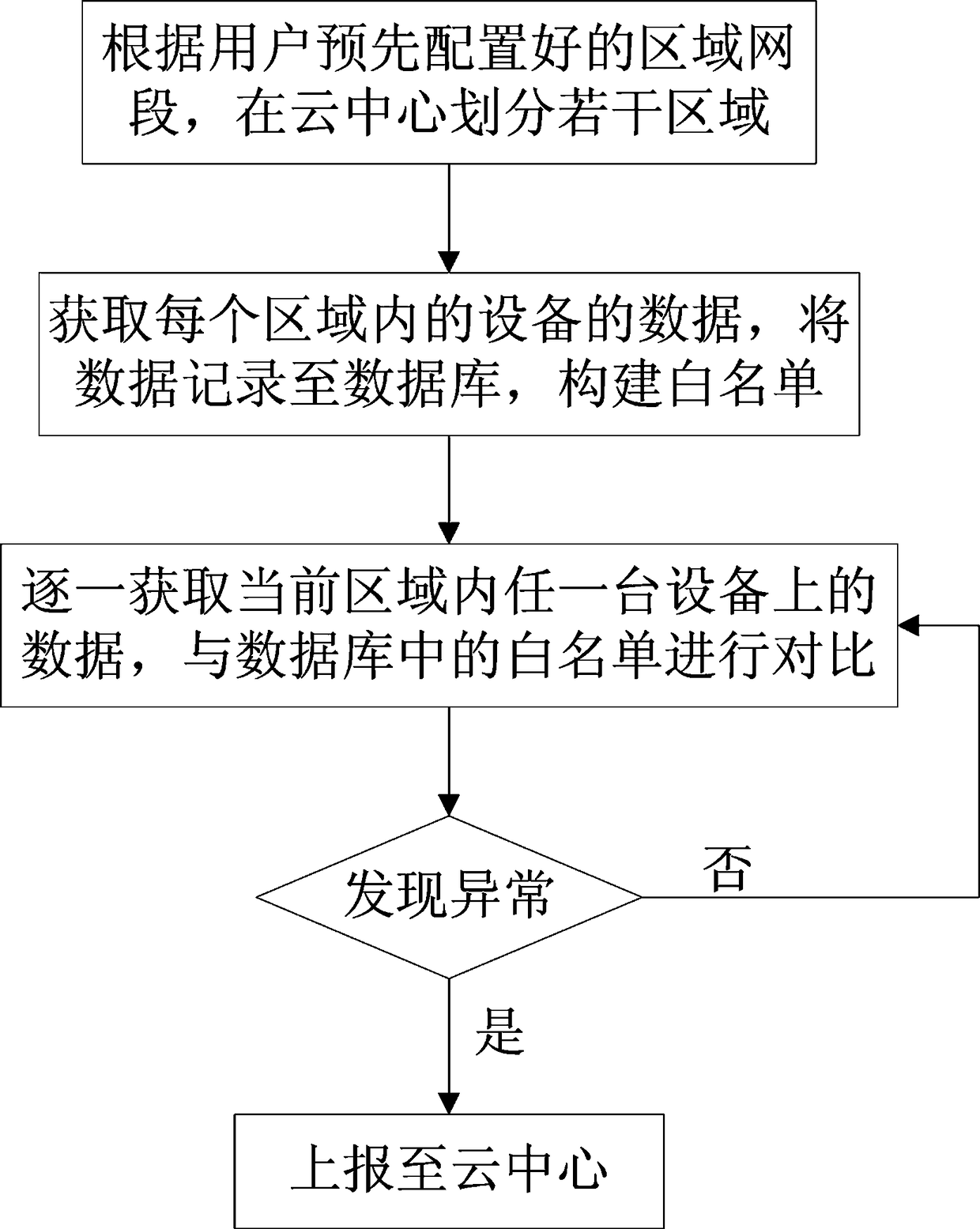
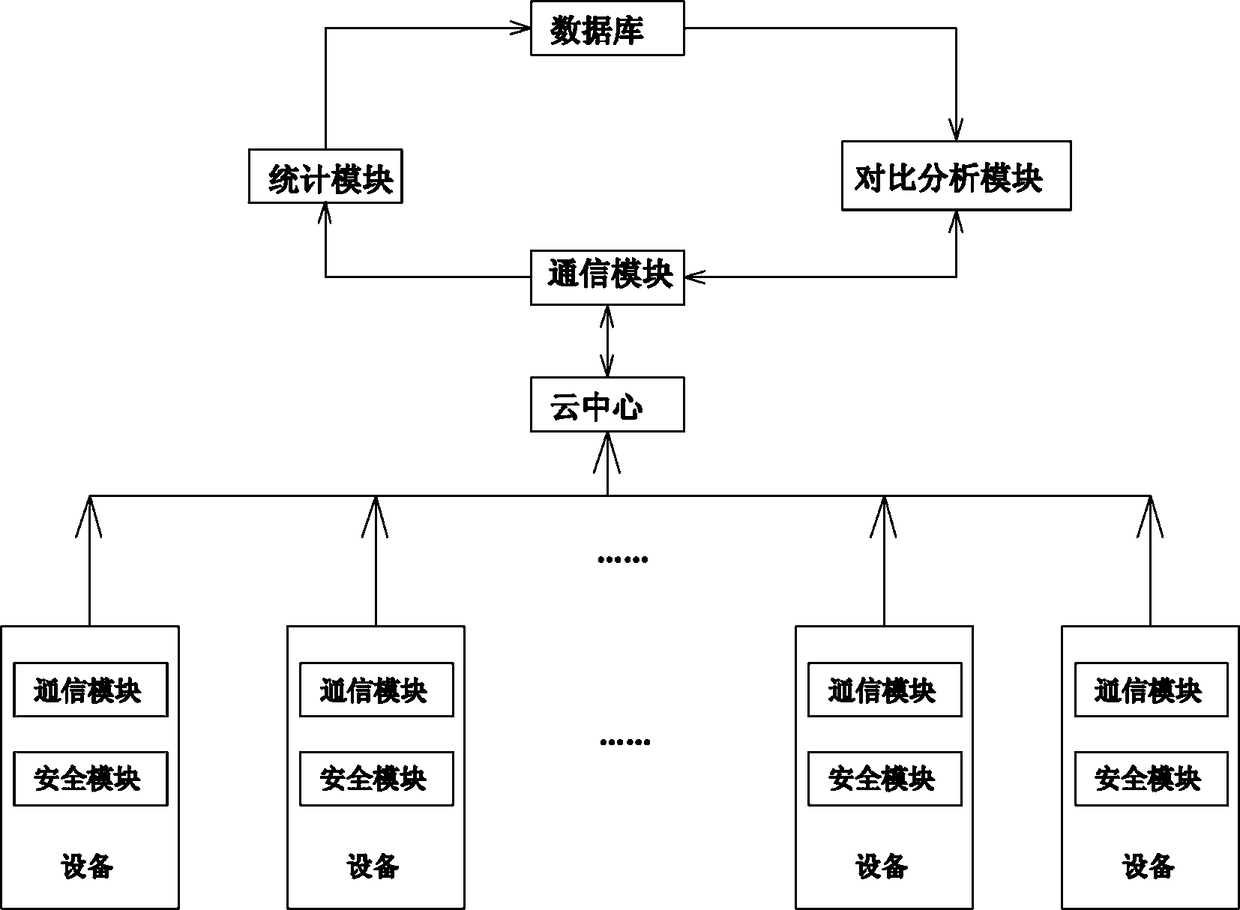
[0029] The present invention relates to a method for comparing and analyzing the security of the Internet of Things horizontally. The Internet of Things includes a cloud center and a device communicatively connected with the cloud center. The method includes the following steps.
[0030] Step 1: Divide several areas in the cloud center according to the area network segment pre-configured by the user.
[0031] In the step 1, the several areas divided in the cloud center may include several large block areas, and any one of the large block areas includes several small block areas.
[0032] In the present invention, the division of regions mainly depends on the regional asset network segment configured in advance by the user. For example, the user configures the regional asset IP network segment of Han...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com