A large-scale Android malware automatic detection system and method
An automatic detection and malware technology, applied in the direction of platform integrity maintenance, etc., can solve the problems of identifying malware, improving the overall learning accuracy rate that cannot be coordinated, and Android security software cannot be granted the highest authority of the system, so as to achieve accurate identification Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
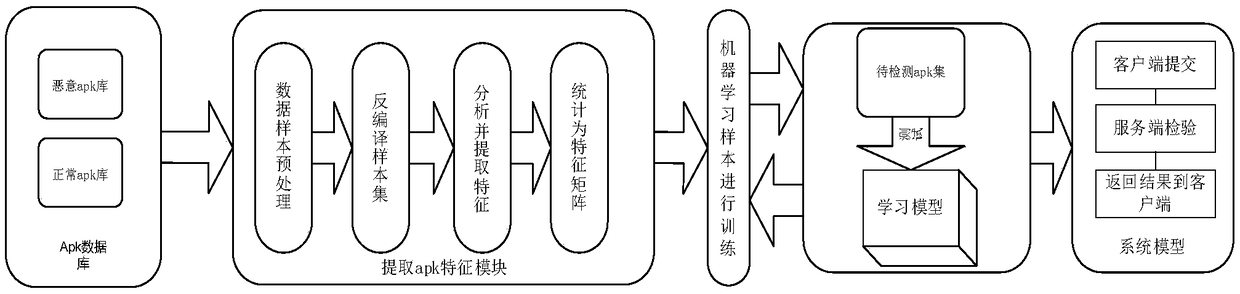
[0039] The solution of the present invention is realized through the following scheme: the user submits the Android executable file to be detected locally, and the server is responsible for analyzing the submitted sample, and then detects on the model that the system has learned, obtains the result, and returns Analyze the results to the user, and automatically classify whether the submitted software collection is malicious software.
[0040] 1. the realization process of the present invention is:
[0041] (1) Collect security software and malware libraries. Malware obtains a fixed number of samples from Google play, together with known malware data sets, to form the initial sample set of the scheme.
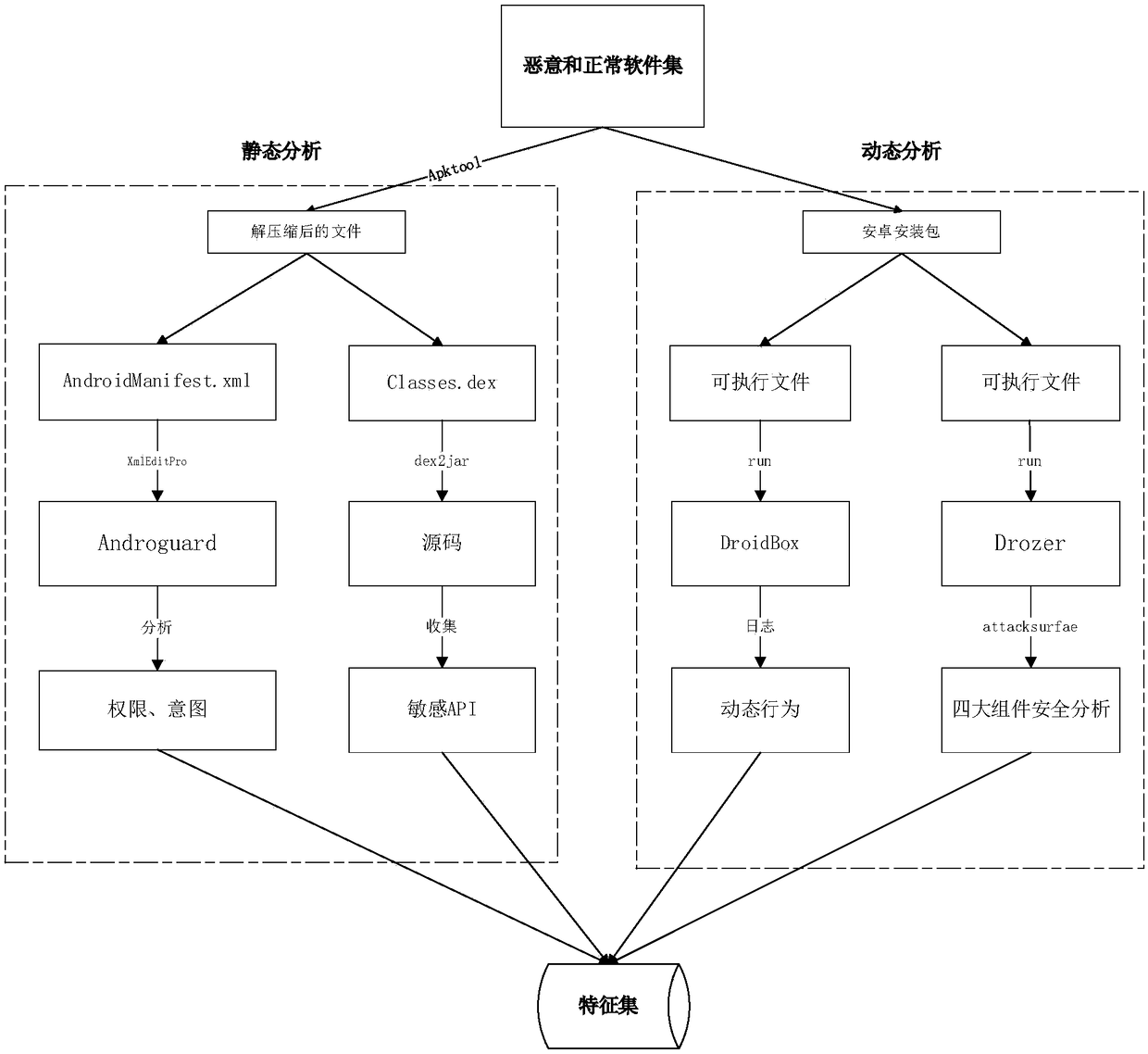
[0042] (2) Use software analysis tools such as Androguard and Droidbox to collect the characteristics of each software from dynamic and static perspectives to form a table of Android software characteristics.
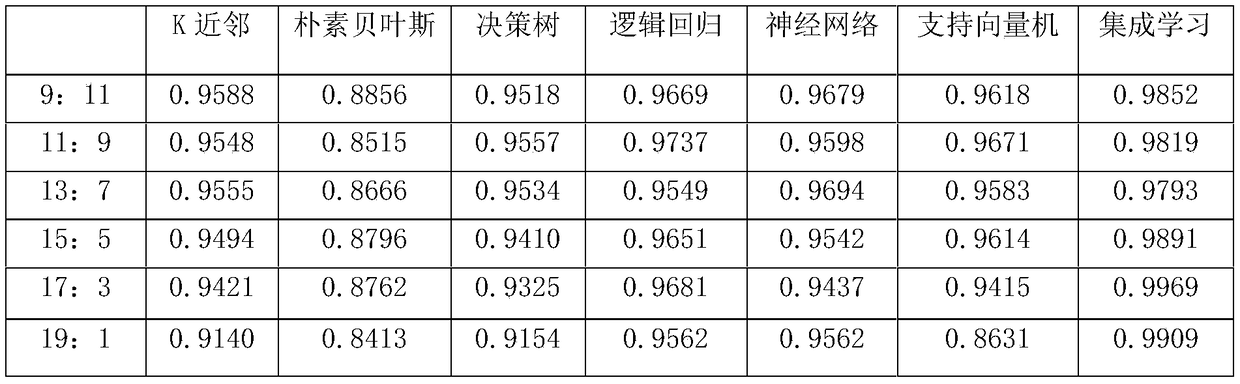
[0043] (3) Process the receipt of the form, specify a threshold, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com