Linux operation log audit system and method
A journal, topic technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be further described below through a preferred embodiment, but the present invention is not limited to the scope of the described embodiment.
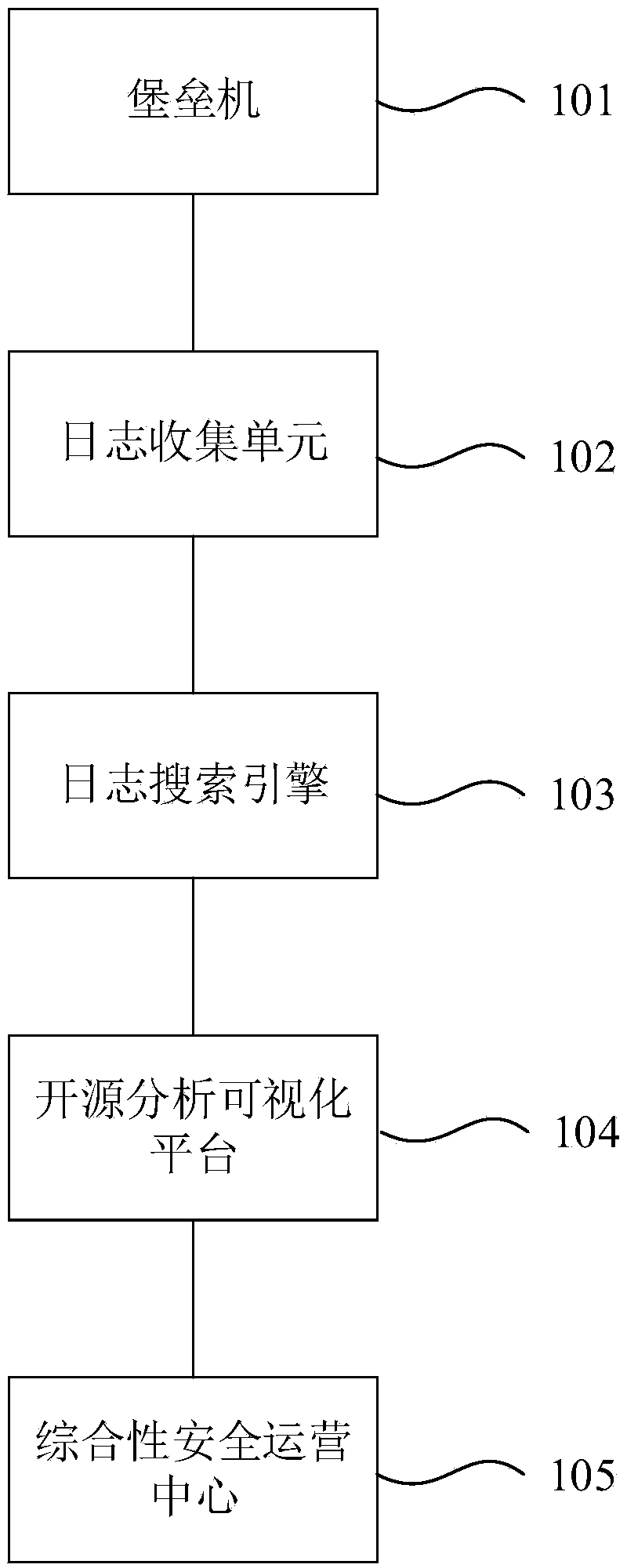
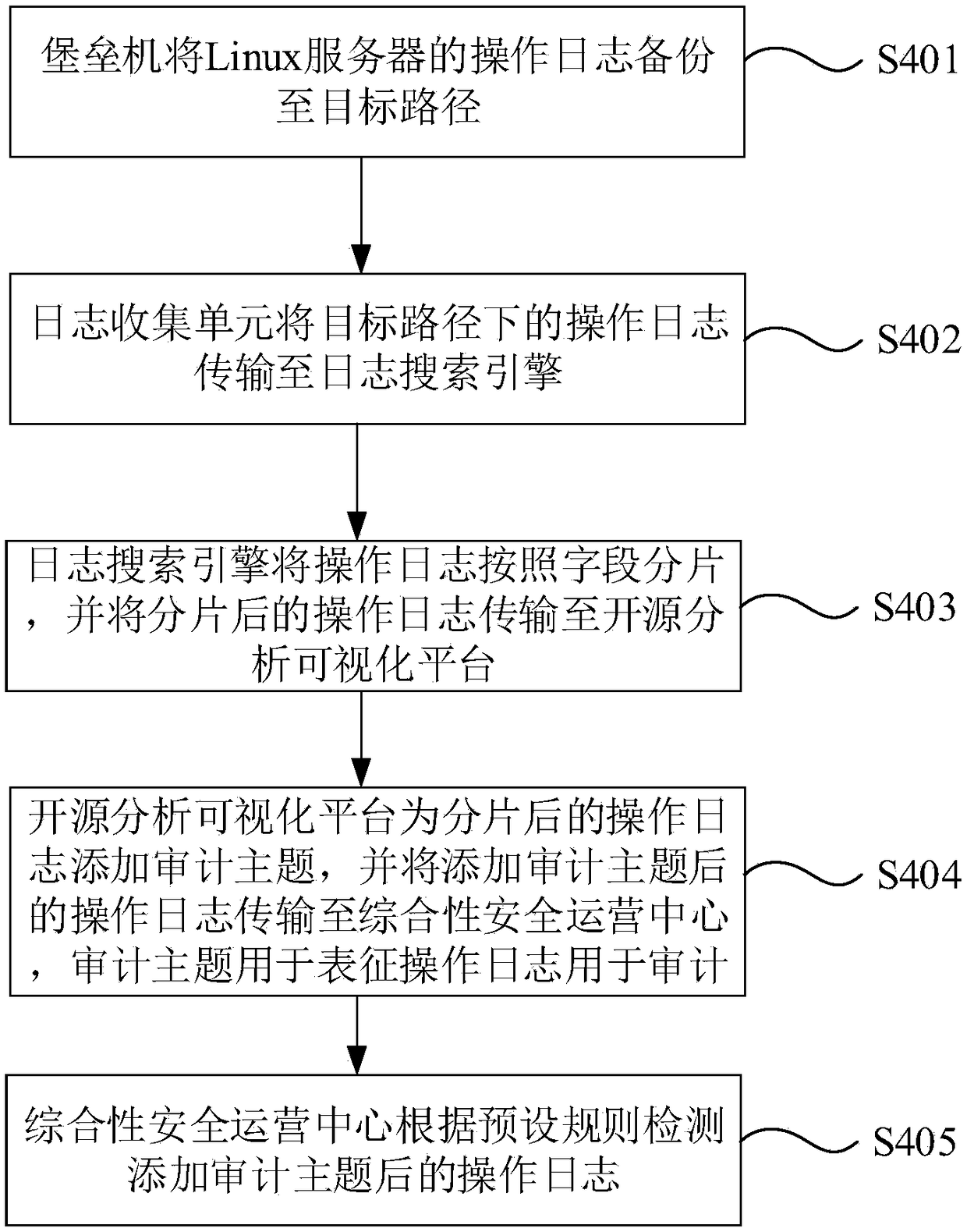
[0037] This embodiment provides a kind of audit system of Linux operation log, refer to figure 1 , the audit system of the Linux operation log includes a bastion host 101, a log search engine 103, a log collection unit 102, an open source analysis and visualization platform 104, and a comprehensive security operation center 105; the bastion host 101 is used to back up the operation log of the Linux server to the target path; the log collection unit 102 is used to transmit the operation log under the target path to the log search engine 103; the log search engine 103 is used to fragment the operation log according to fields, and transmit the fragmented operation log to the open source analysis and visualization platform 104; the open source analysis and visualization platform 104 is used to add an audit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com