Methods for monitoring approval operations, authorization operations, and form operations
A form and operation record technology, applied in instruments, electronic digital data processing, digital data protection, etc., can solve the problems of confusing, complex and time-consuming, and difficult operation of similar roles, so as to avoid leakage of confidential information, and operate easily and quickly. , the effect of reducing workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0065] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings, but the protection scope of the present invention is not limited to the following description.
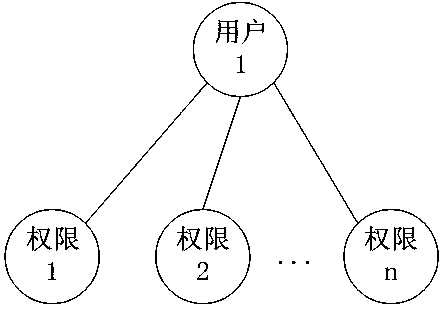
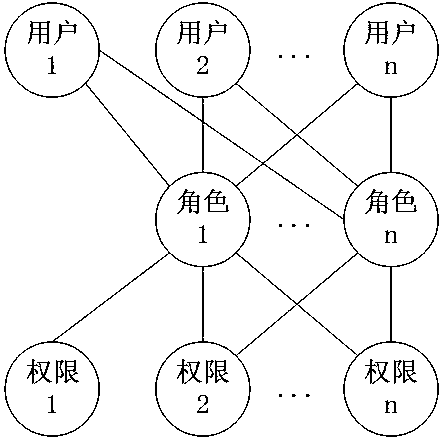
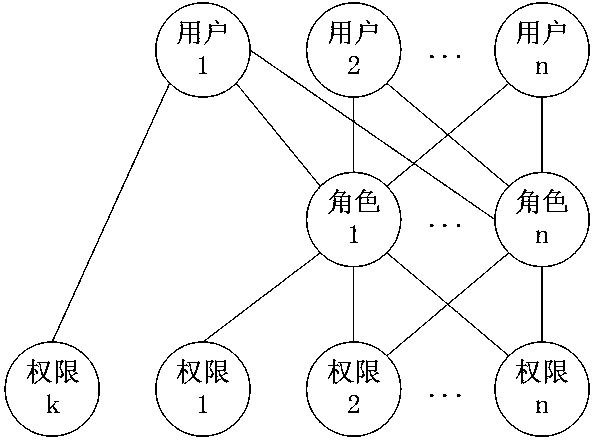
[0066] [Example 1] such as Figure 5 As shown, the method for supervising and approving operations includes the following steps: Create a role in the system, such as Figure 4 As shown, the role is an independent individual, not a group / class. At the same time, a role can only be associated with a unique user, and a user is associated with one or more roles; a user corresponds to an employee, and an employee corresponds to a user , employees determine (obtain) permissions through their corresponding user-associated roles (independent individual nature roles). Employees and users have a 1-to-1 relationship with each other and are bound for life. After a user corresponds to an employee, the user belongs to the employee and the user can no lo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com