Method and device for establishing secure communication between network devices
A technology for network equipment and secure communication, which is applied in the field of arrangement between network equipment and can solve problems such as confusion and complex distinction.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
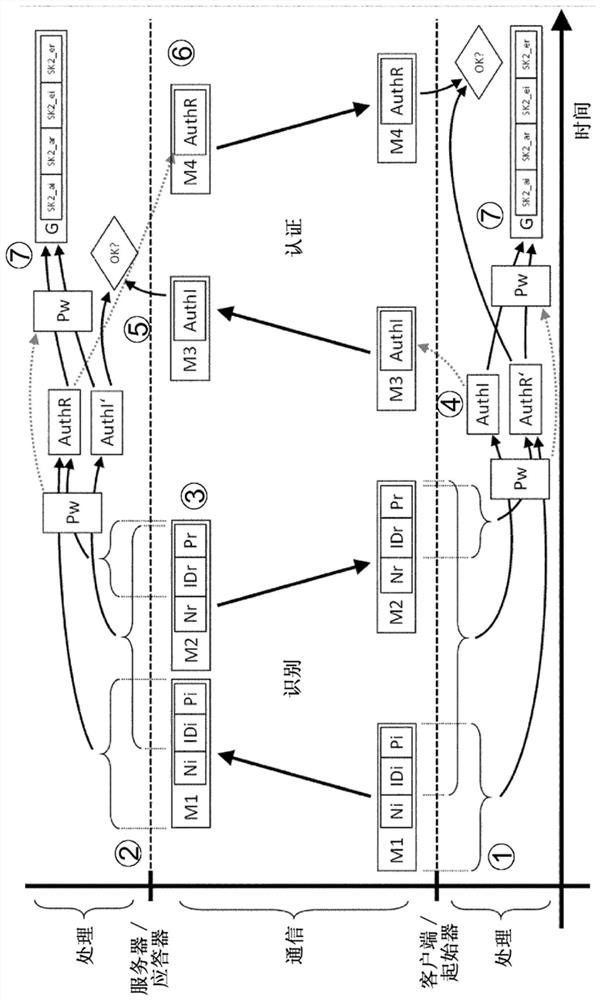
[0177] below in particular with reference to figure 1 , which shows a basic schematic diagram of a preferred procedure for establishing a secure communication within the scope of the present invention.
[0178] here, figure 1 shows in detail the communication network used in the figure 1 A first network device called a client or initiator in a figure 1 A preferred embodiment for setting up secure communication between second network devices referred to as servers or transponders in , wherein the communication network is not further shown here for the sake of clarity. as by figure 1 It can be seen that here, under the condition of using a symmetric encryption system or symmetric encryption technology, separate authentication / authentication is performed for the first and second network devices respectively, and the password G to be used as a shared key Pw for secure communication is generated It was previously performed in which, in a symmetric encryption system / symmetric en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com