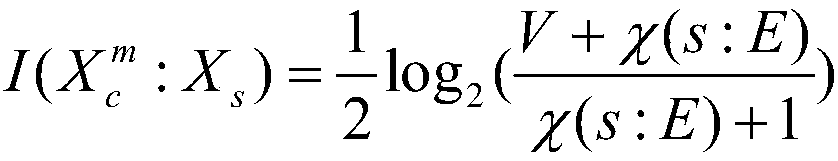Fingerprint authentication method based on continuous variable quantum key distribution
A technology of quantum key distribution and fingerprint authentication, which is applied in the field of fingerprint authentication based on continuous variable quantum key distribution, can solve problems such as the application research of non-continuous variable quantum key distribution, and achieve the effect of ensuring security and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
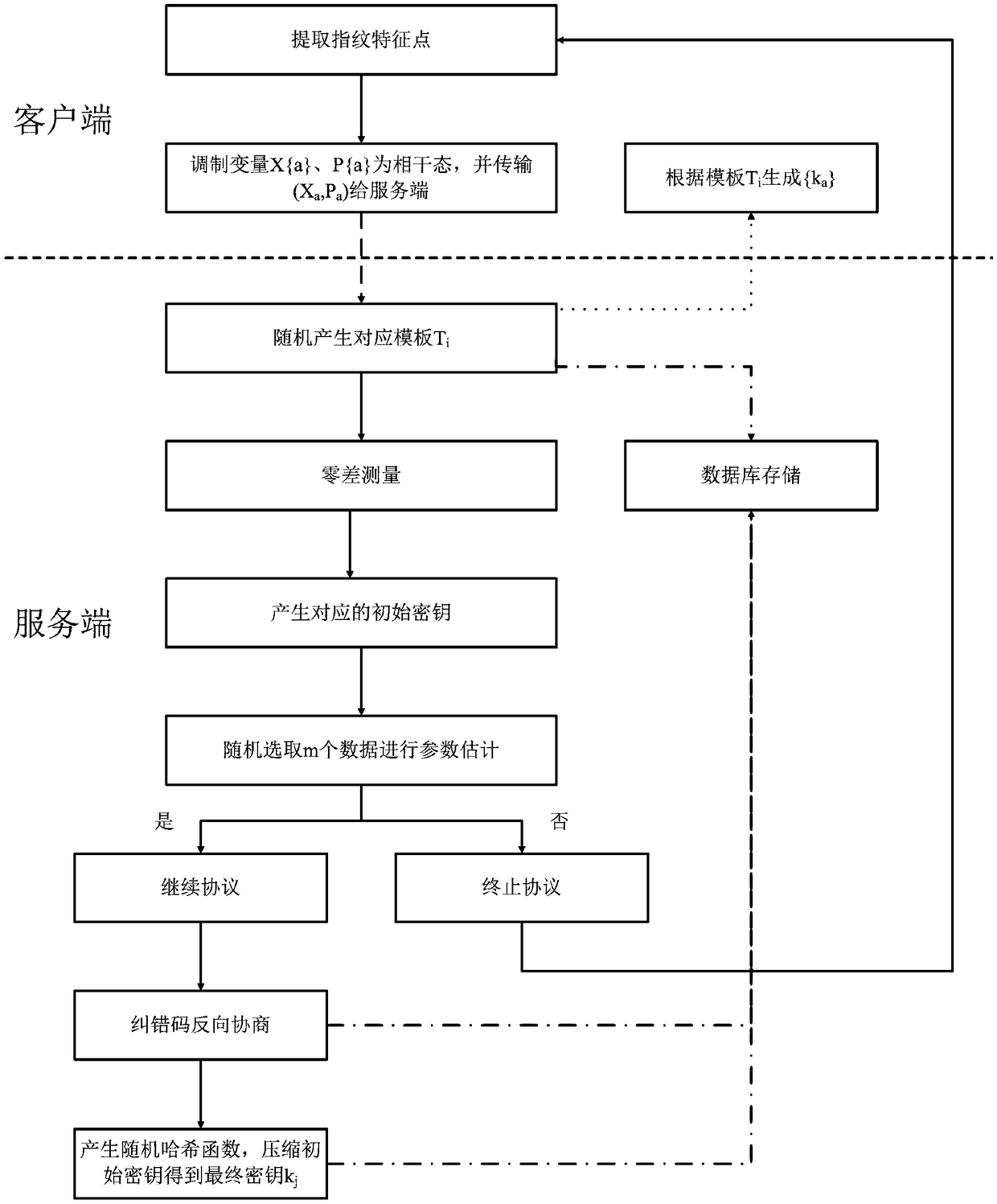
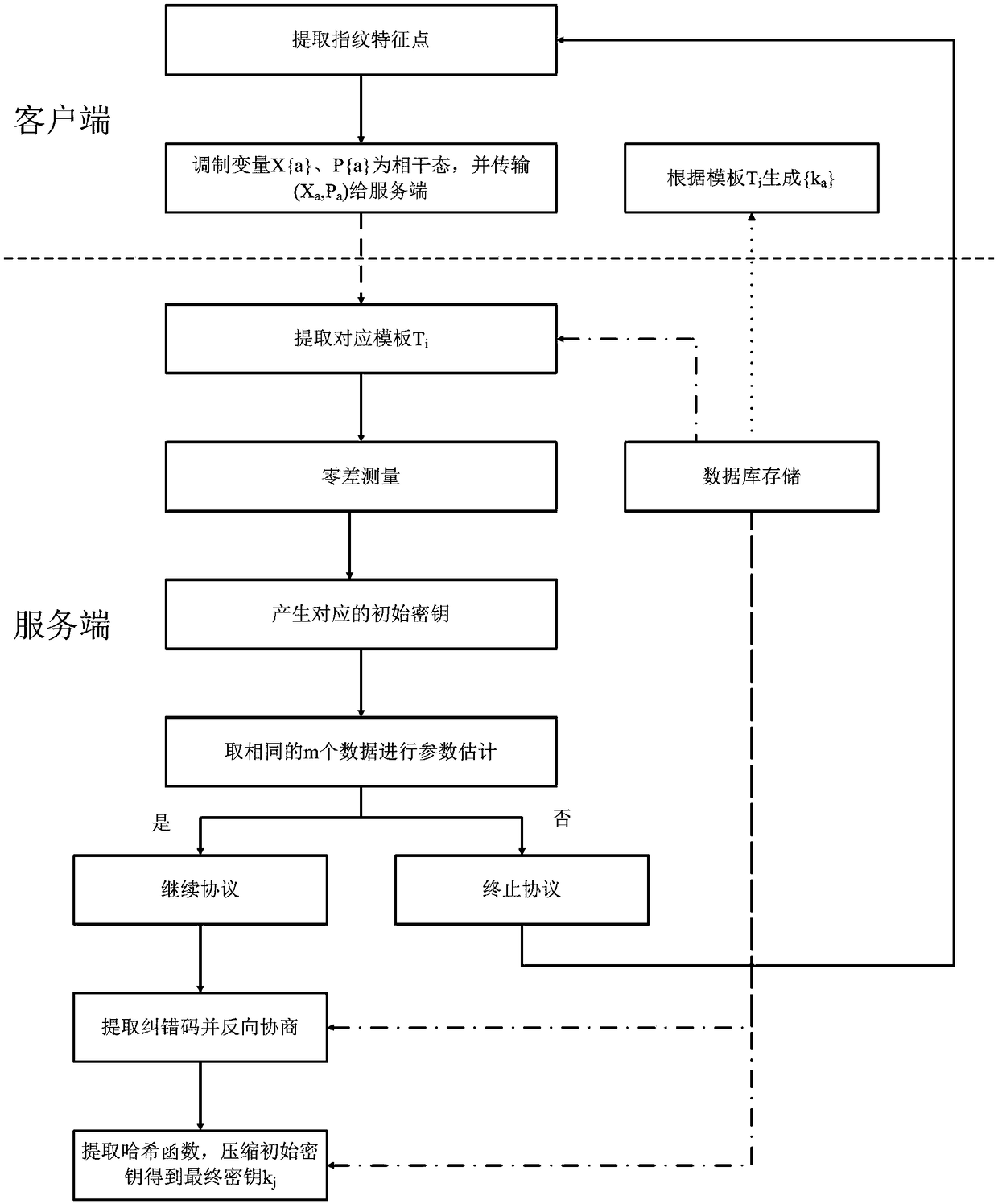
[0041] The fingerprint authentication method based on continuous variable quantum key distribution provided by the present invention realizes the working principle of the scheme based on continuous variable quantum key distribution; the method of the present invention is mainly divided into two stages, the first stage is user fingerprint identity In the registration stage, the second stage is the user fingerprint identification stage. Because the method of the present invention does not directly transmit the user's fingerprint identity information, but modulates the fingerprint feature points into coherent state variables, generates an initial key through a correspondingly generated revocable template, and then passes through a series of post-processing processes (including parameter estimation, The process of reverse error correction negotiation and key strengthening) finally obtains the encryption key, so that the whole system has better security and privacy.
[0042] Such a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com