Message reliability evaluation method for aggregation of two trust evaluations in car networking
A vehicle networking and reliability technology, applied in the field of vehicle networking security, can solve problems such as actual performance limitations, ignoring trust, and ignoring data-oriented trust, and achieves the effects of fast evaluation speed, high dynamic characteristics, and accurate evaluation results.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
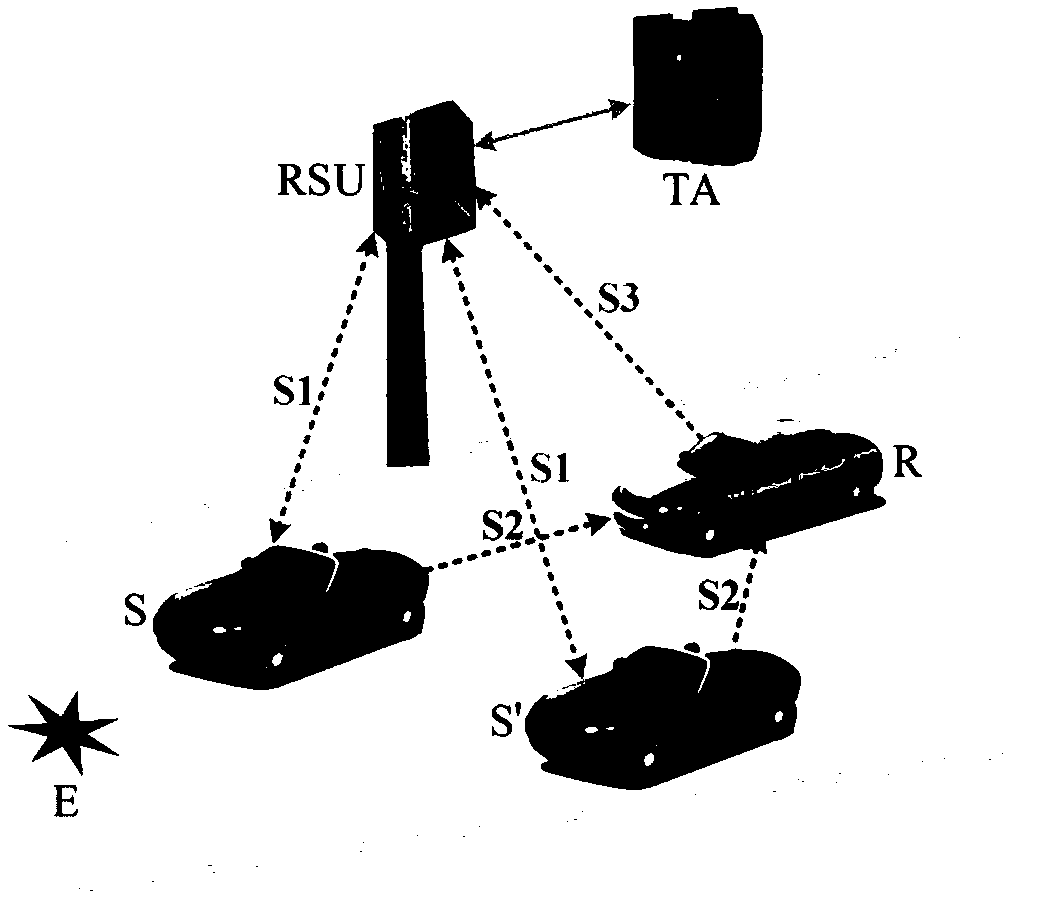
[0061] Attached below figure 1 And attached figure 2 The technical solution described in the present invention is described in detail.
[0062] The technical solution described in the invention mainly includes three elements, namely, a trust center (Trust Authority, TA), a road-side unit (Road-Side Unit, RSU) and a vehicle (ie, a node, Node), wherein the vehicle and the road-side unit pass through other The vehicle's relay communicates wirelessly, while the roadside unit and the trust center use wired communication.
[0063] The trust center is responsible for maintaining the trust information of nodes, and updating the trust value of each node at intervals of Δt.
[0064] Taking the calculation of the trust value TV(S) of node S as an example, the trust center first selects the latest at most n pieces of trust feedback ( That is, TF(A,S), TF(B,S), TF(C,S), etc.), and add the corresponding feeder to the feeder set FS(S) of node S, that is, FS(S)={A ,B,C,...}.
[0065] Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com