A kernel-based method and system for detecting super-privilege behavior of an application program
A technology of super authority and application program, which is applied in the field of information security, can solve problems such as complex attack methods, large manpower consumption, and difficult judgment, and achieve the effects of obvious feature distinction, low false alarm rate, and high accuracy rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention more clear, the implementation manners of the present invention will be described in detail below in conjunction with the drawings and embodiments.
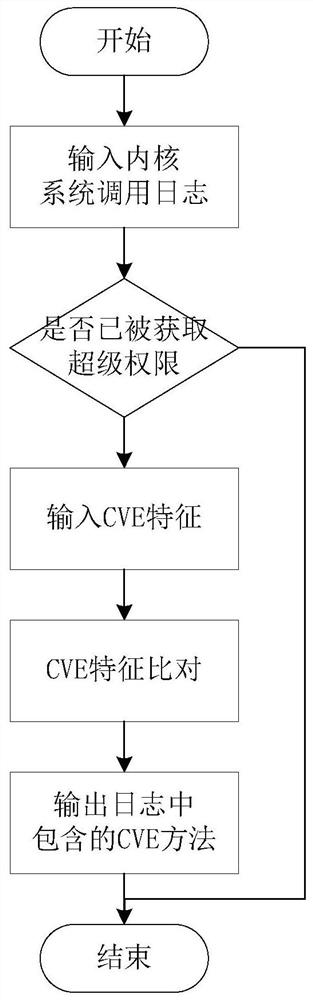
[0036] The core part of the system is mainly composed of two units, which are the judgment unit for obtaining super authority and the CVE detection unit. The input data of the system is the kernel log generated when the application under test installed on the Android system is running. It is worth noting that the kernel logs here are mainly the usage of system calls.
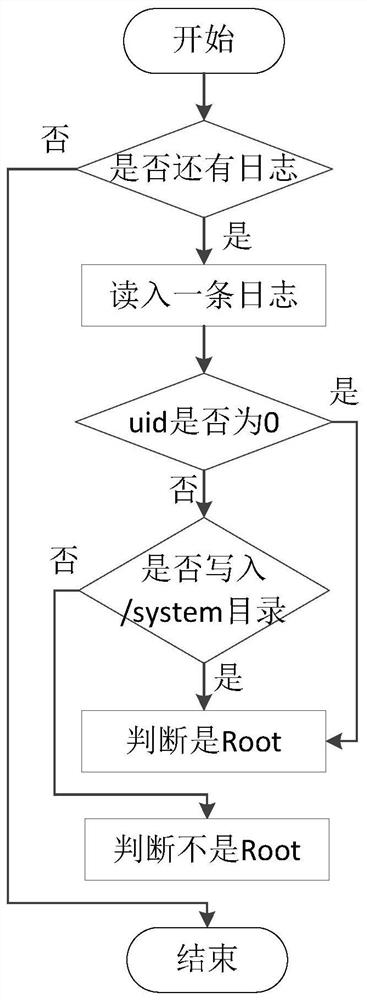
[0037] First, input the above data into the super authority judgment unit. This subsystem includes a UID detection module. By traversing the uid of the system call process in the traversal log, it is judged whether the system has obtained the super authority; the subsystem also includes the system directory The detection module is used as a supplemen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com