An auxiliary screening method and system for suspicious transaction cases
A transaction and case technology, applied in data processing applications, finance, instruments, etc., can solve problems such as high input costs of manpower and material resources, reduce input costs, and the influence of subjective factors of staff, and achieve strong objectivity, reduce input costs, The effect of high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
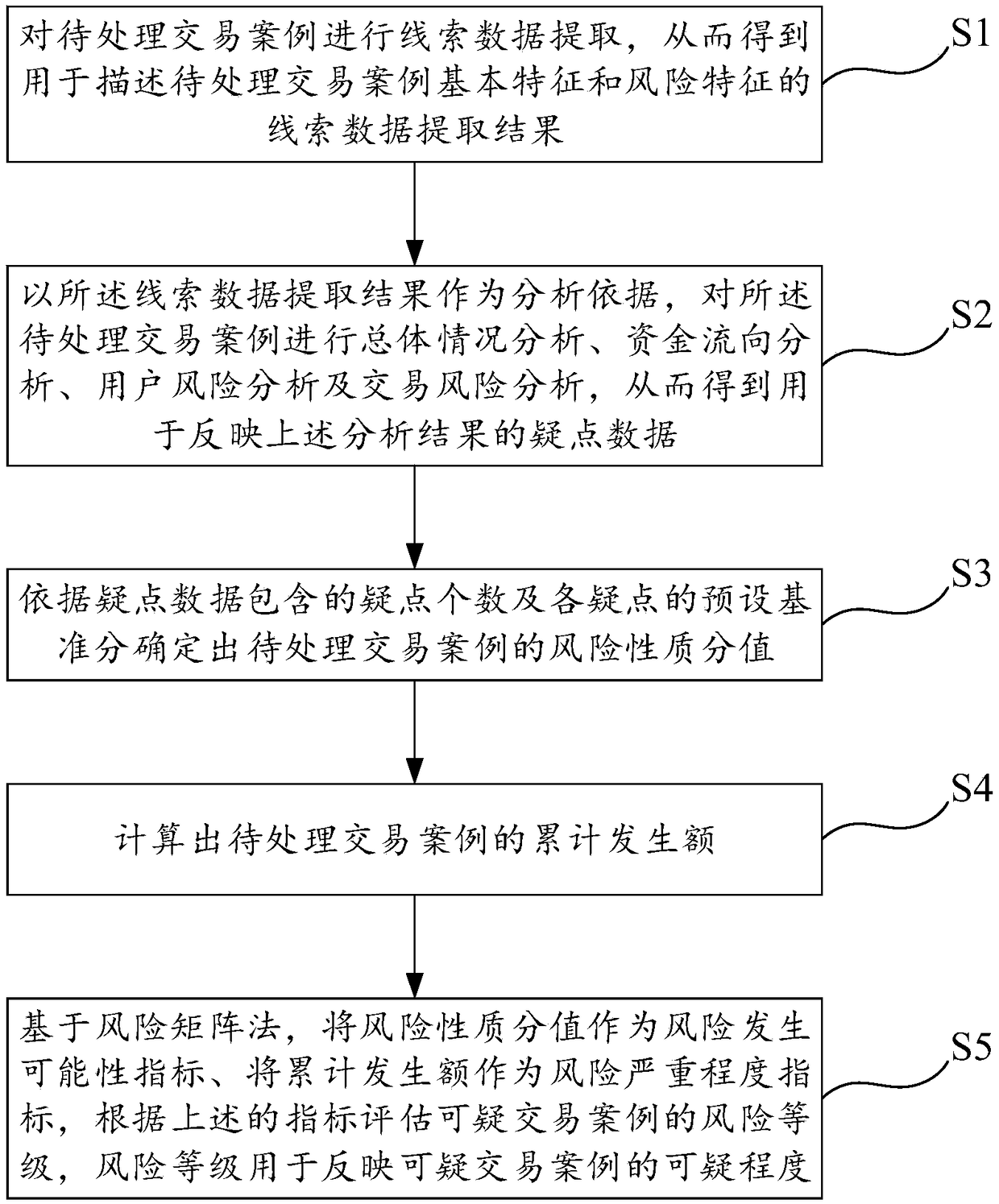
[0072] Such as figure 1 As shown, this embodiment discloses an auxiliary screening method for suspicious transaction cases, which objectively screens the suspicious degree of transaction cases, and provides corresponding suggestions based on the screening results. The auxiliary screening method includes the following steps.
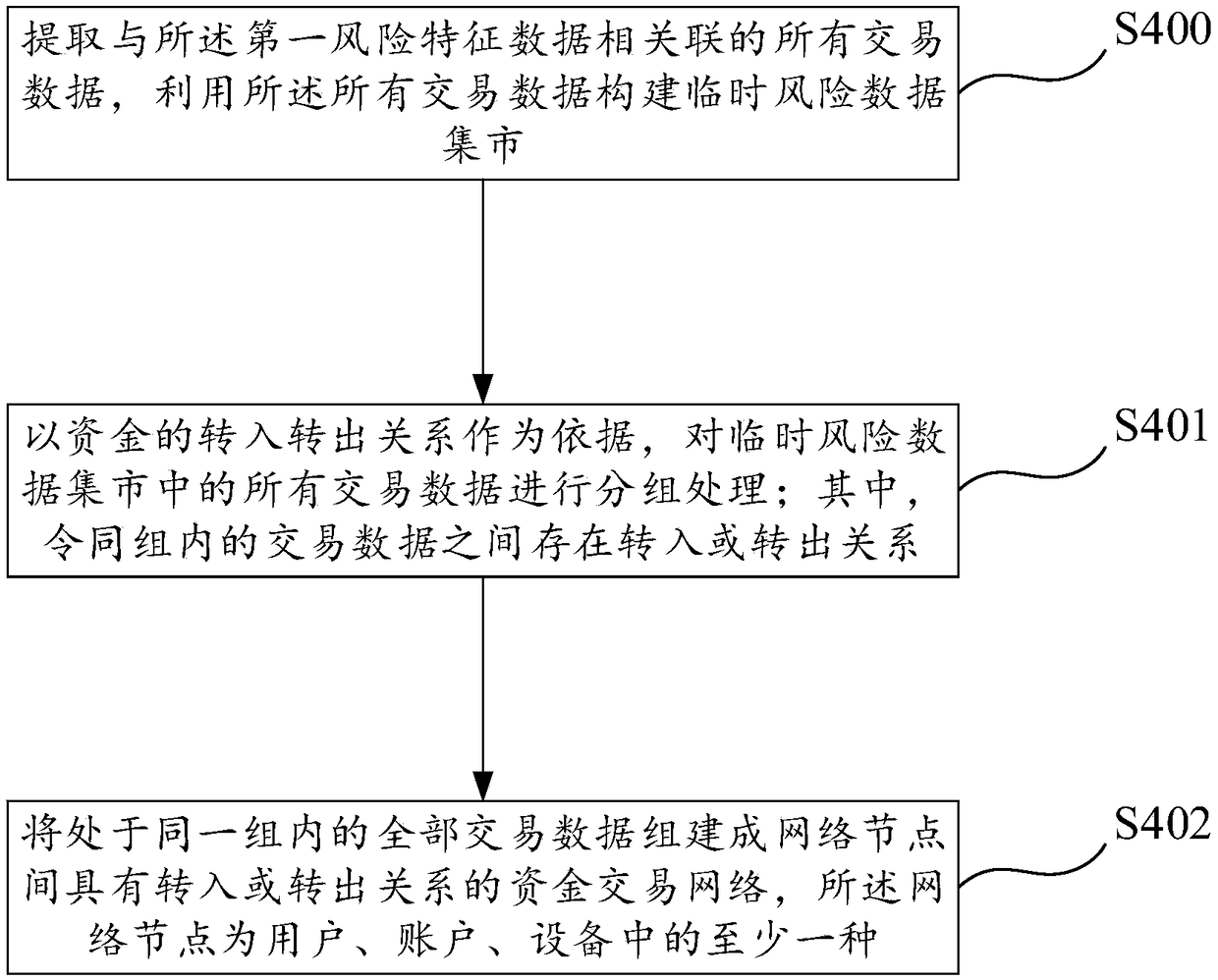
[0073] Step S1, information extraction of suspicious transaction cases: extract clue data from transaction cases to be processed, so as to obtain clue data extraction results for describing the basic characteristics and risk characteristics of transaction cases to be processed, and save the clue data extraction results; this embodiment Among them, the clue data extraction results include basic index data, transaction risk model, first risk characteristic data, transaction flow data and user information data, among which, transaction risk model and first risk characteristic data are used to describe the risk characteristics of pending transaction cases, Ba...
Embodiment 2
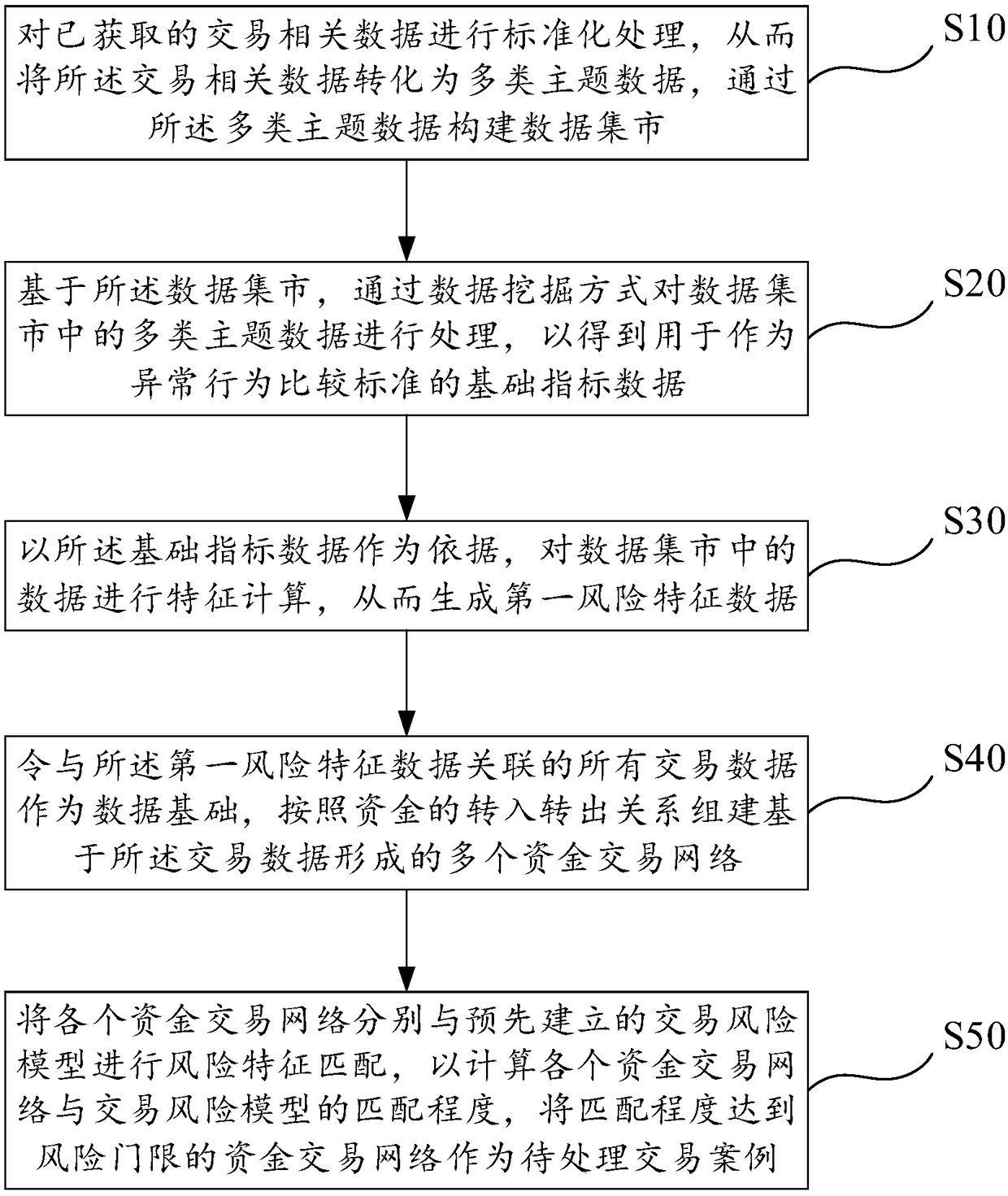
[0108] This embodiment is based on the same inventive concept as Embodiment 1, and proposes an auxiliary screening system for a suspicious transaction case that implements the auxiliary screening method in Embodiment 1, such as Figure 6 As shown, the auxiliary screening system includes a data mart construction module, a basic index mining module, a risk feature generation module, a transaction network construction module and a transaction case generation module, a clue data extraction module, a transaction case analysis module, a risk nature determination module, and a cumulative A balance calculation module and a suspicious degree determination module.
[0109] The data mart building module is used to standardize the acquired transaction-related data, so as to convert the transaction-related data into multi-category subject data, and to construct a data mart through multi-category subject data.
[0110] The basic index mining module is used to process multiple types of subje...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com