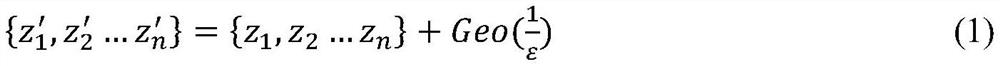A Frequent Itemset Mining Method Oriented to Differential Privacy Protection
A technology of frequent itemset mining and differential privacy, which is applied in the field of information security, can solve the problems of adding more noise, low data availability, and low availability of mining results, and achieves the effect of protecting personal privacy, simple method and easy operation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
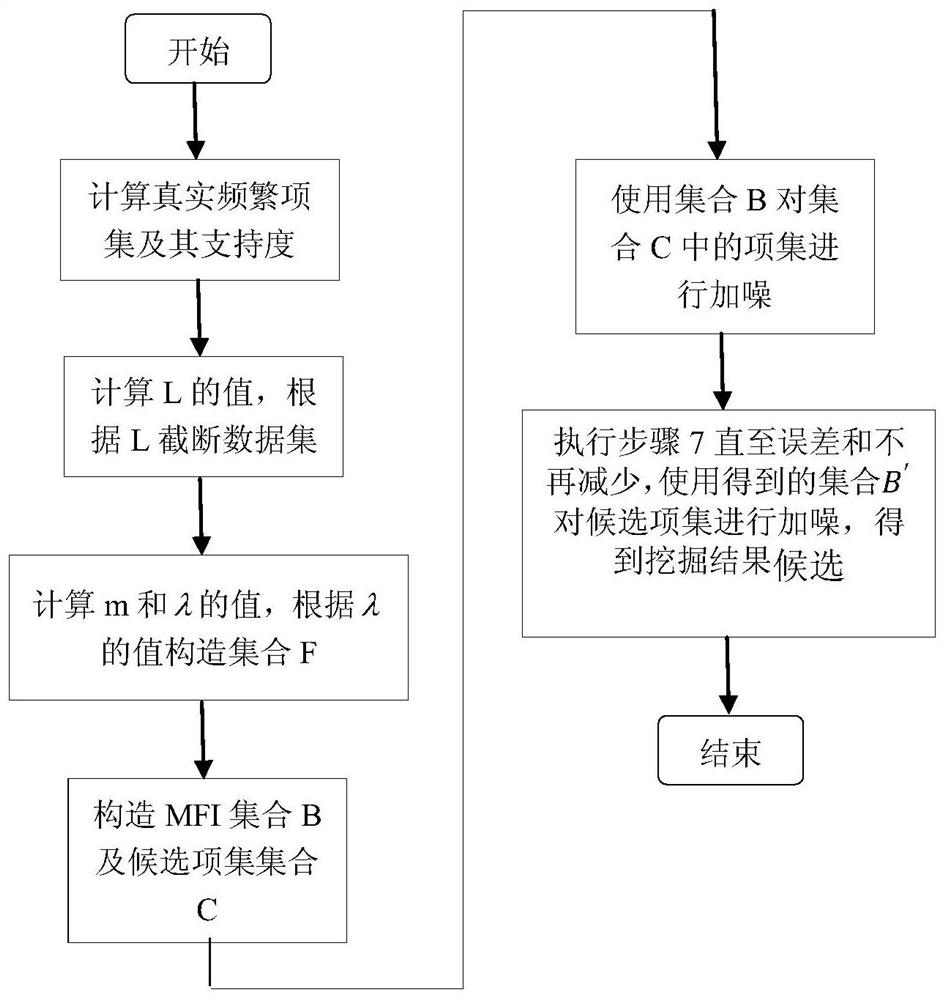
[0049] The implementation of the technical solution of the present invention will be described in further detail below in conjunction with the accompanying drawings. It should be understood that these examples are only used to illustrate the present invention and are not intended to limit the scope of the present invention. After reading the present invention, those skilled in the art will understand the present invention Modifications in various equivalent forms fall within the scope defined by the appended claims of the present application.
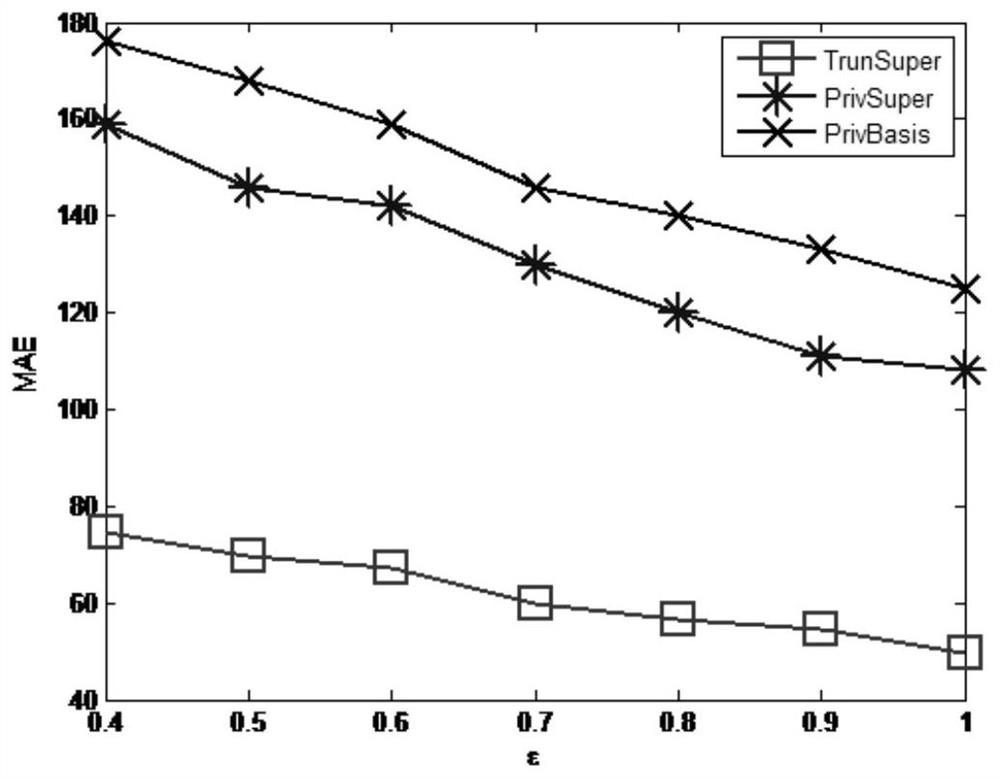
[0050] The method of the invention is simple and easy to operate, and it is theoretically proved that it satisfies the ε-differential privacy condition, and can effectively reduce the dimension of the data set, thereby reducing the noise that needs to be added, improving the usability of the result, and protecting privacy. The method is suitable for data publishing and privacy protection of datasets of different scales and dimensions.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com