Air upgrade method of vehicle firmware, and computer readable storage medium
An air upgrade and firmware technology, applied in software deployment, electrical components, transmission systems, etc., can solve problems such as loss of brand value, high cost, low efficiency, etc., to ensure security, ensure correctness and integrity, and improve upgrades efficiency effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
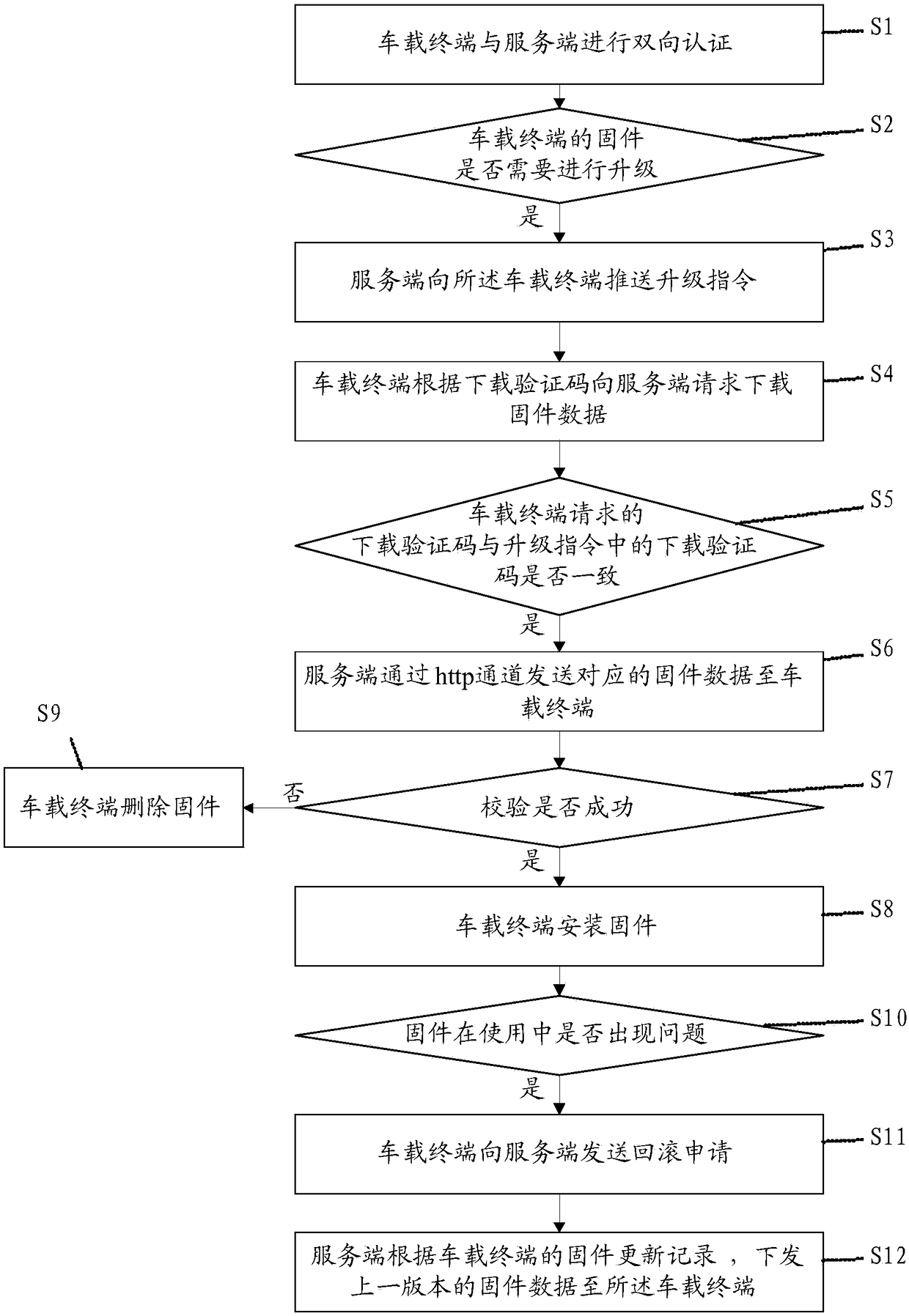
[0095] Please refer to figure 2 , Embodiment 1 of the present invention is: a method for over-the-air upgrading of vehicle firmware, comprising the following steps:
[0096] S1: The in-vehicle terminal and the server perform two-way authentication; if the authentication is successful, step S2 is performed. That is, the vehicle terminal and the server implement two-way air interface authentication and log in to the server.
[0097] S2: The server determines whether the firmware of the vehicle-mounted terminal needs to be upgraded according to the firmware version number, that is, the server determines whether the vehicle-mounted terminal has upgradeable firmware by comparing whether the current version number of the vehicle-mounted terminal firmware is consistent with the latest version number, and if so, Then step S3 is executed.
[0098] S3: The server pushes an upgrade instruction to the vehicle terminal, where the upgrade instruction includes the firmware name, version n...
Embodiment 2
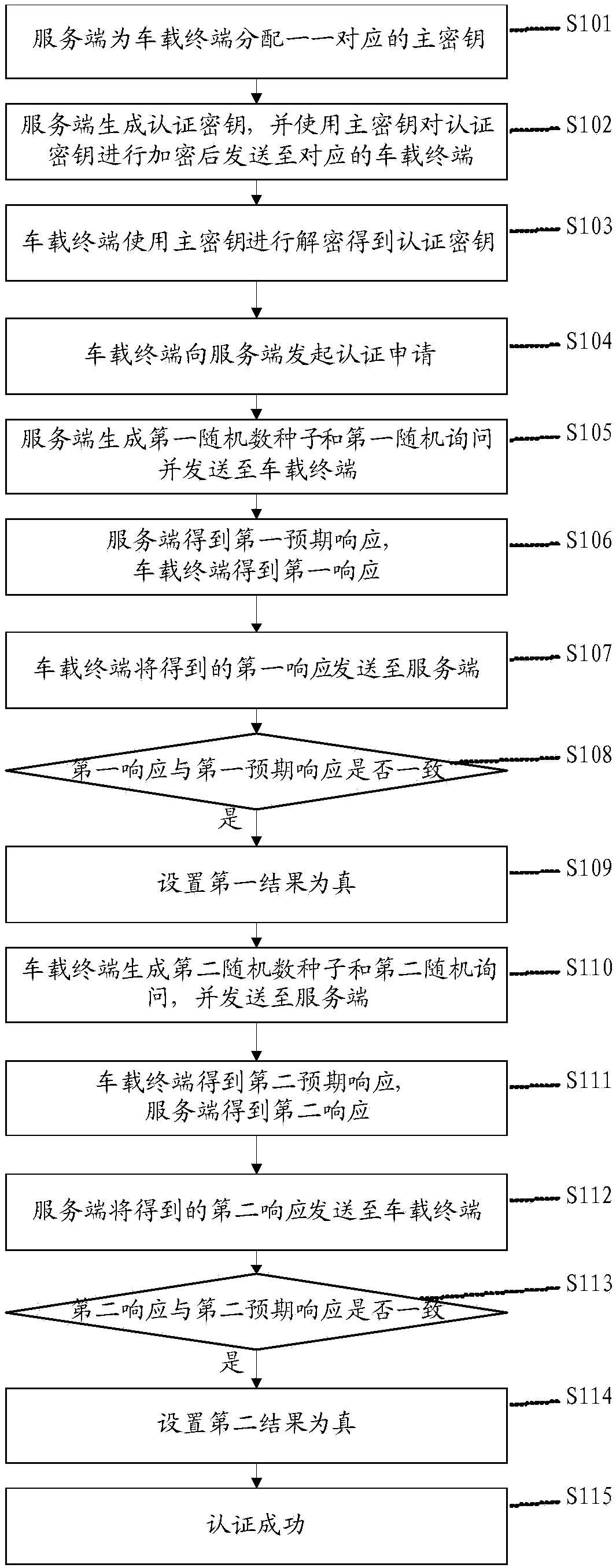
[0110] Please refer to image 3 , this embodiment is a further expansion of step S1 in the first embodiment, including the following steps:
[0111] S101: The server assigns a one-to-one corresponding master key MK to each vehicle-mounted terminal, and the master keys MK of each vehicle-mounted terminal are independent of each other. The master key MK is used to complete the encryption and decryption of the authentication key AK distributed in the air; further, the master key MK can be manually injected into the security entity through the loading device.
[0112] S102: The server generates the authentication key AK, encrypts the authentication key AK with the master key MK, and sends it to the corresponding vehicle terminal; that is, after the vehicle terminal is successfully registered, the server generates the authentication key AK, and uses the The master key MK corresponding to the in-vehicle terminal is encrypted and sent to the in-vehicle terminal.
[0113] S103: The ...
Embodiment 3
[0129] This embodiment is a computer-readable storage medium corresponding to the above-mentioned embodiment, and a computer program is stored thereon, and the program implements the following steps when executed by a processor:
[0130] Two-way authentication between the vehicle terminal and the server;
[0131] If the authentication is successful, the server determines whether the firmware of the vehicle terminal needs to be upgraded according to the firmware version number;
[0132] If so, the server pushes an upgrade instruction to the vehicle terminal, and the upgrade instruction includes the firmware name, version number, firmware size, firmware MD5 verification code and download verification code;
[0133] After receiving the upgrade instruction, the vehicle-mounted terminal requests the server to download firmware data according to the download verification code;
[0134] If the download verification code requested by the in-vehicle terminal is consistent with the dow...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com