Patents
Literature
61results about How to "Ensure correctness" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
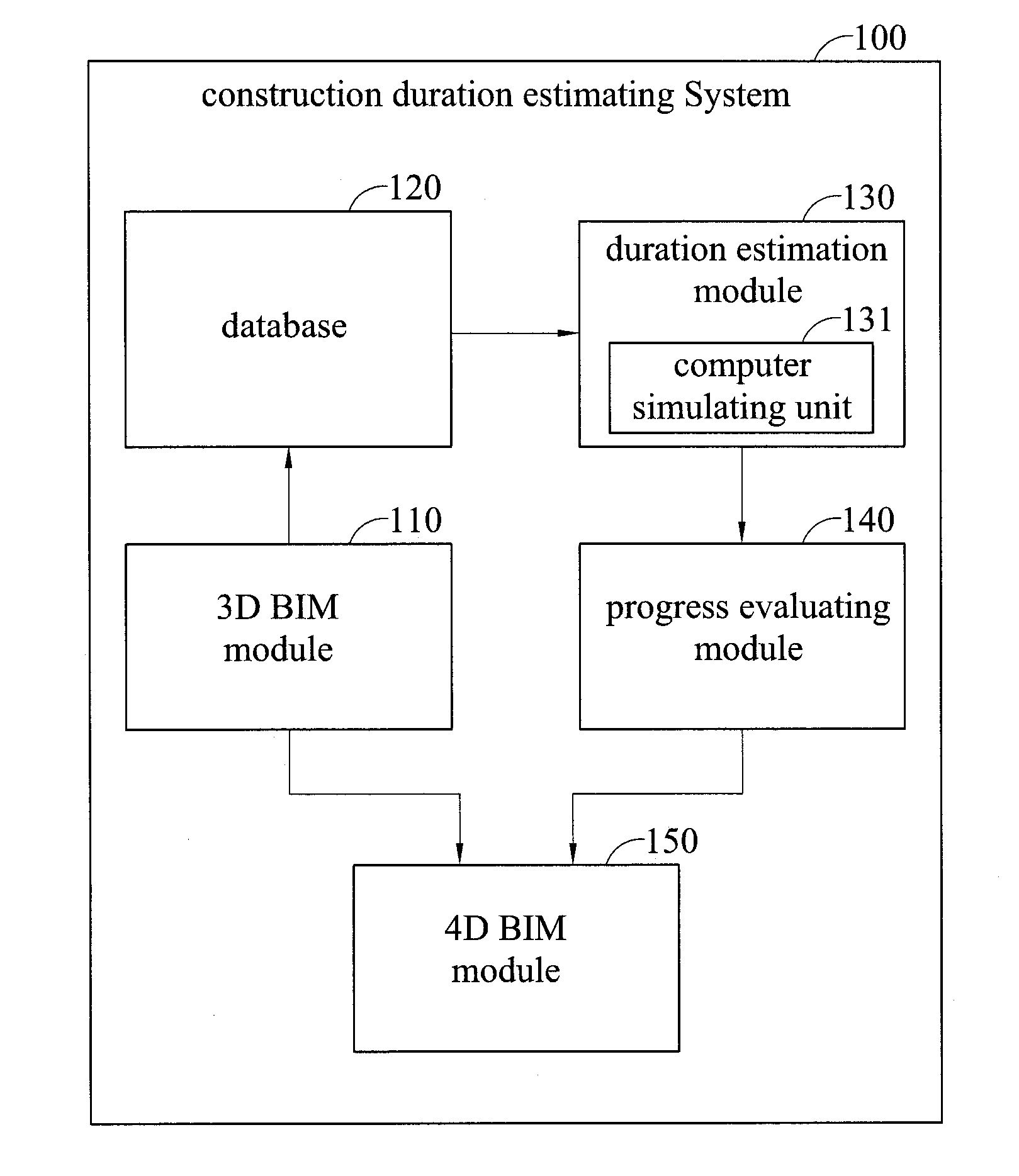
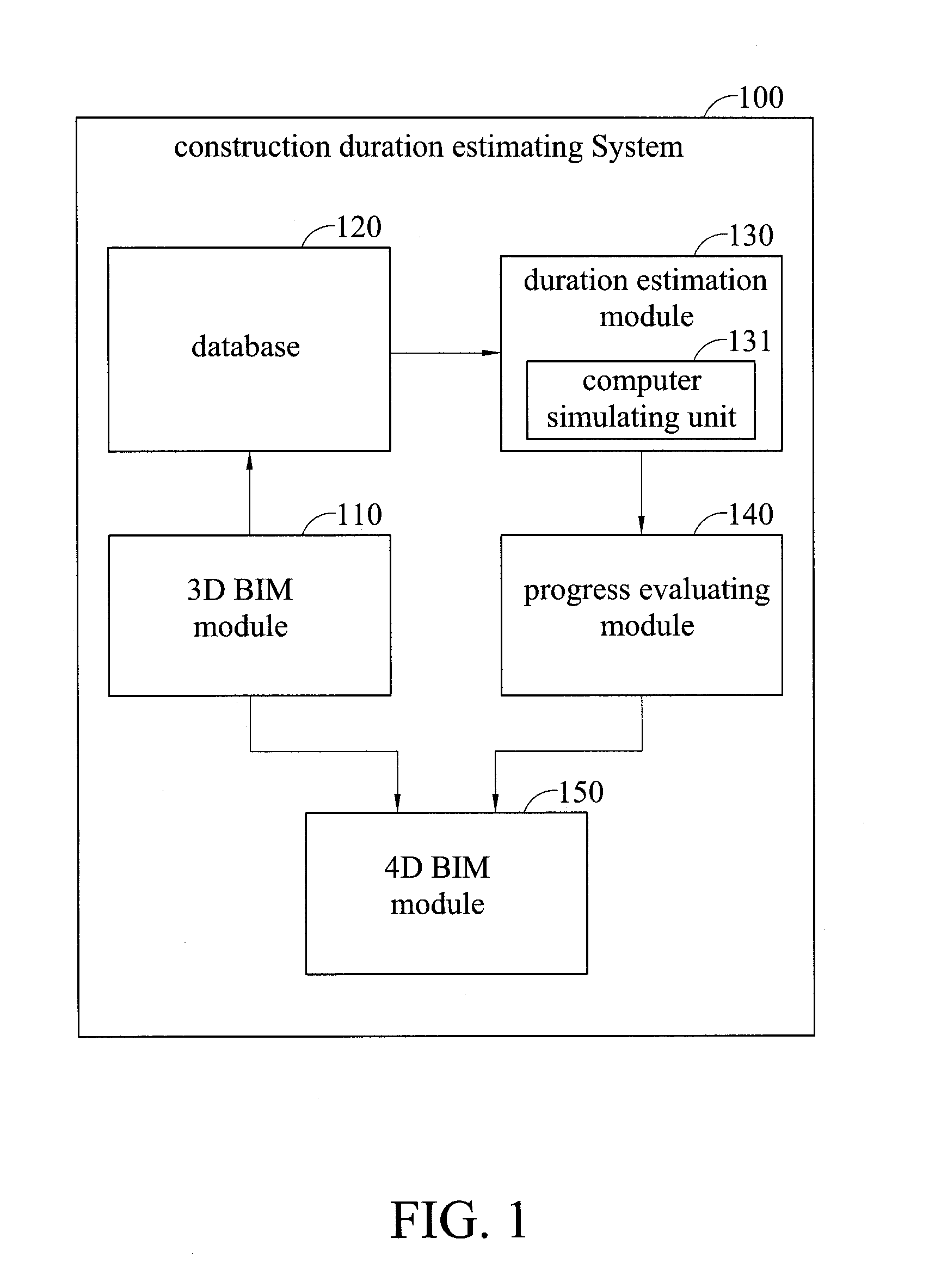
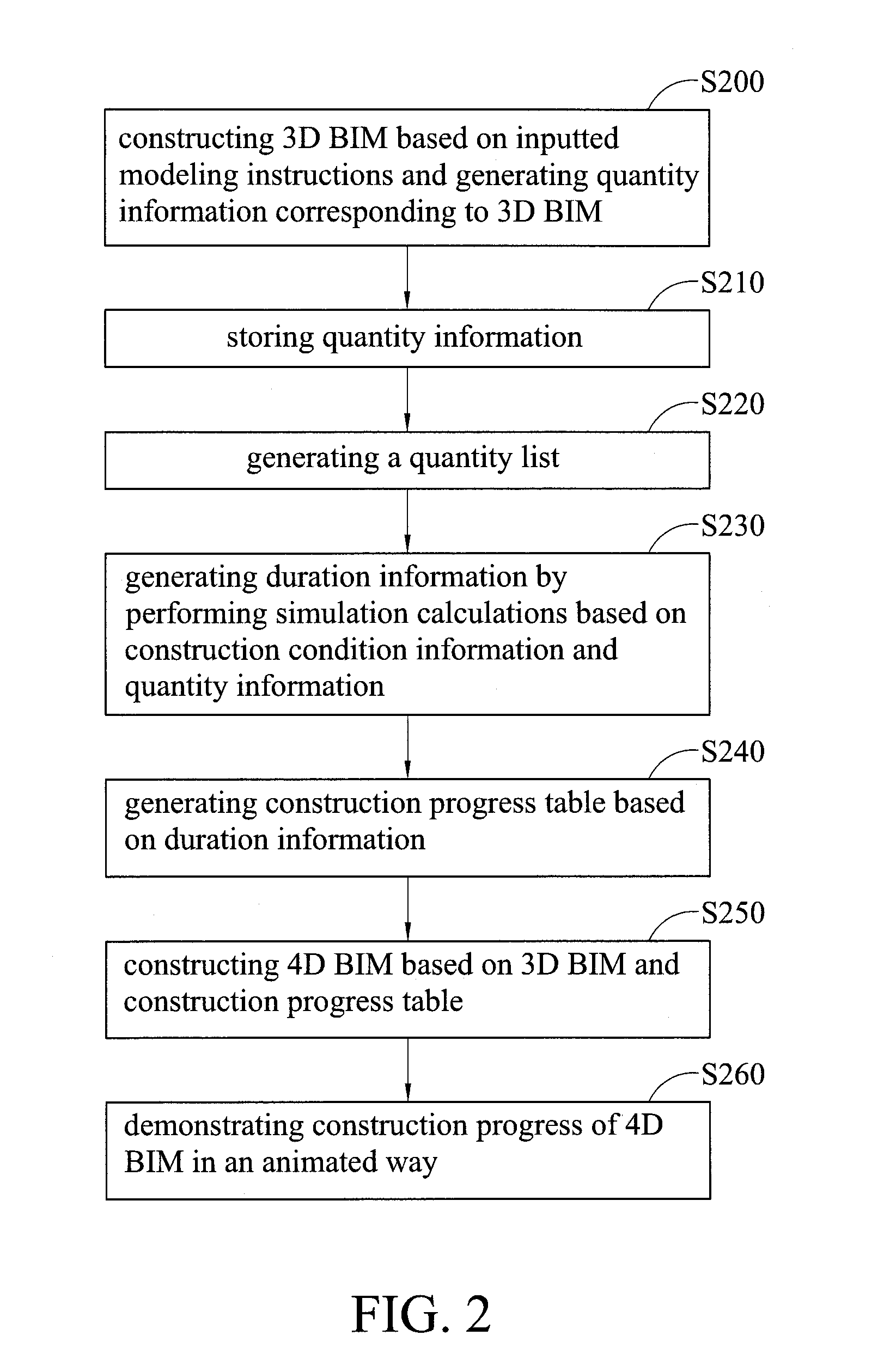
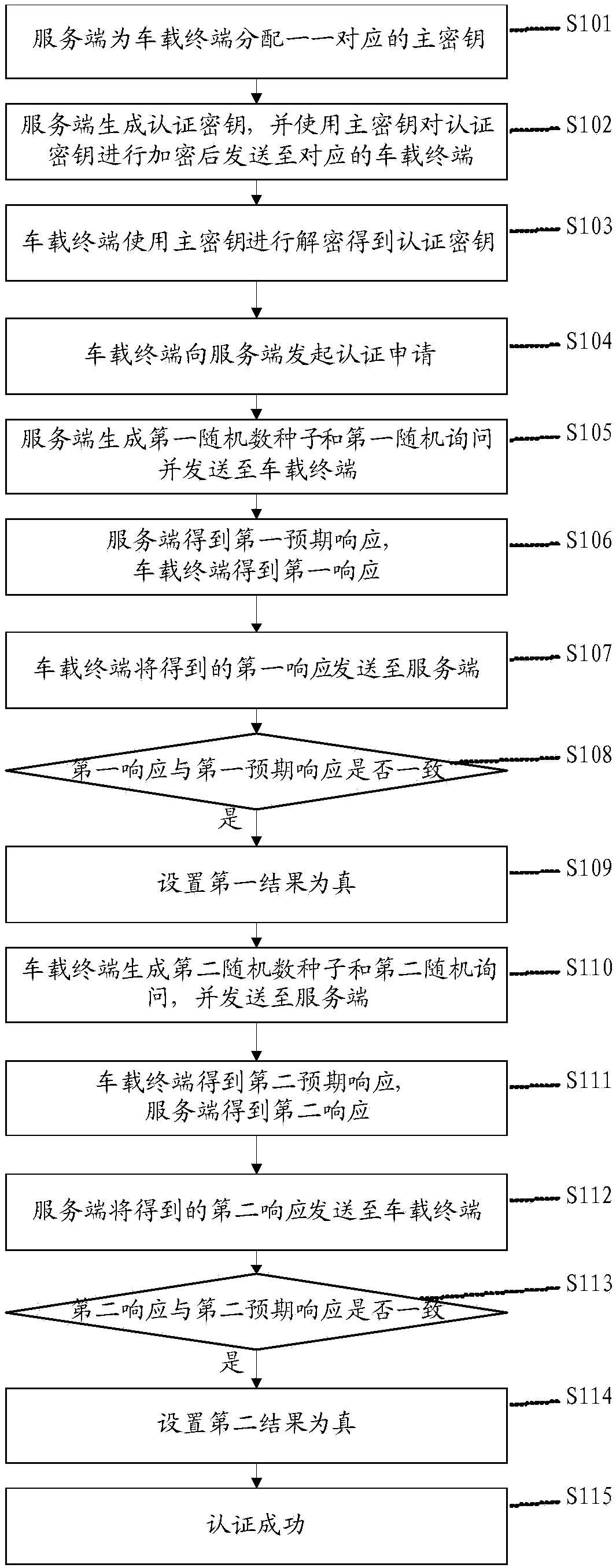
System and method for estimating construction duration
InactiveUS20130335413A1Ensure correctnessEnsure timelinessResources3D modellingAnimationProcess information
A system and method for estimating construction duration. The system includes a three-dimensional (3D) building information model (BIM) module, a duration estimation module, and a 4D BIM module. The 3D BIM module constructs a 3D BIM based on inputted modeling instructions and generates quantity information corresponding to the 3D BIM. The duration estimation module calculates duration information for construction work based on inputted construction condition information and the quantity information of the 3D BIM produced. The 4D BIM module constructs a 4D BIM based on the 3D BIM and the duration information. Thus, the present invention can automatically calculate the quantity of building materials, estimate the construction duration, establish a construction progress table, and demonstrate the construction progress of the 4D BIM in an animated way, replacing the traditional way of manually processing information for duration estimation.
Owner:NAT CHIAO TUNG UNIV
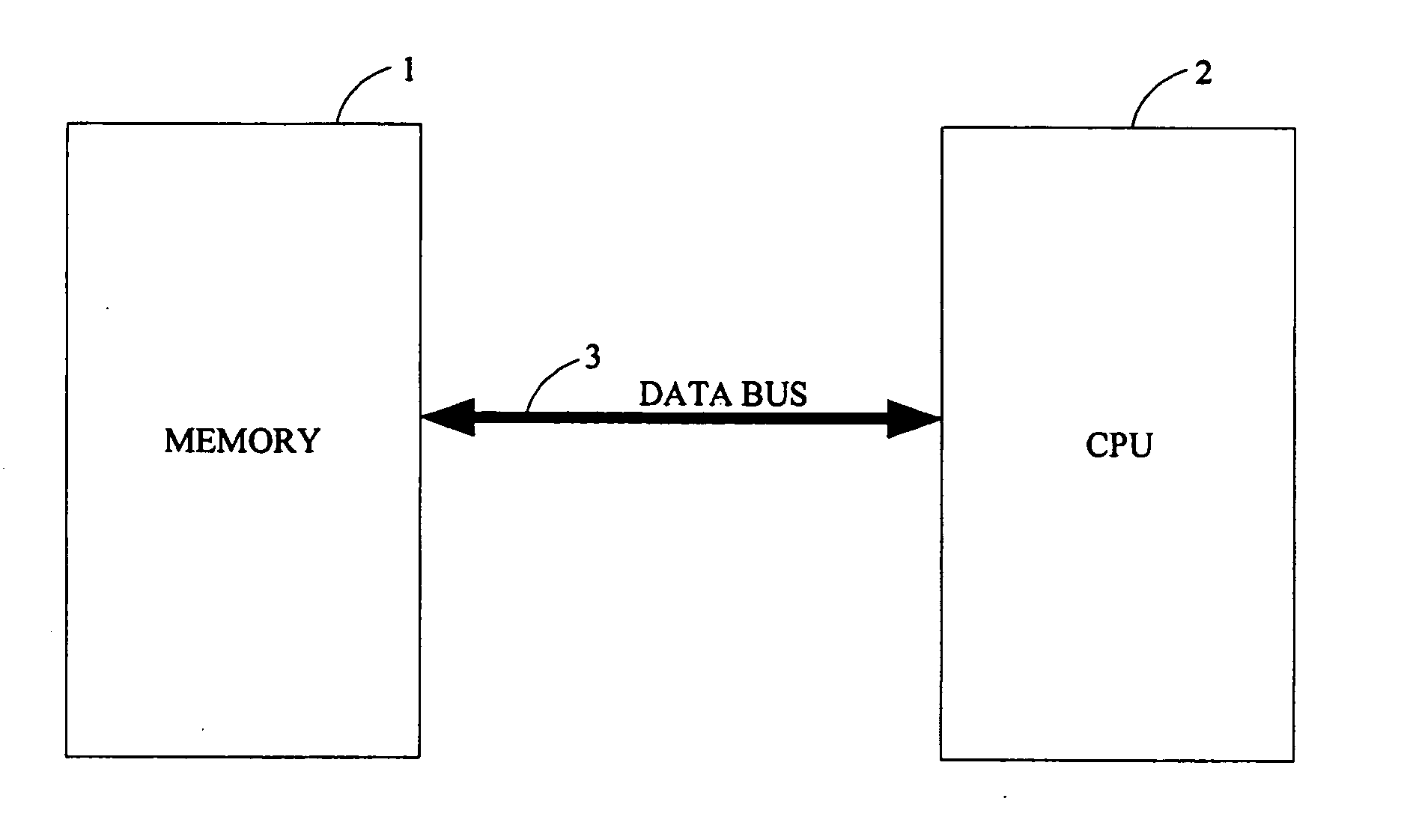
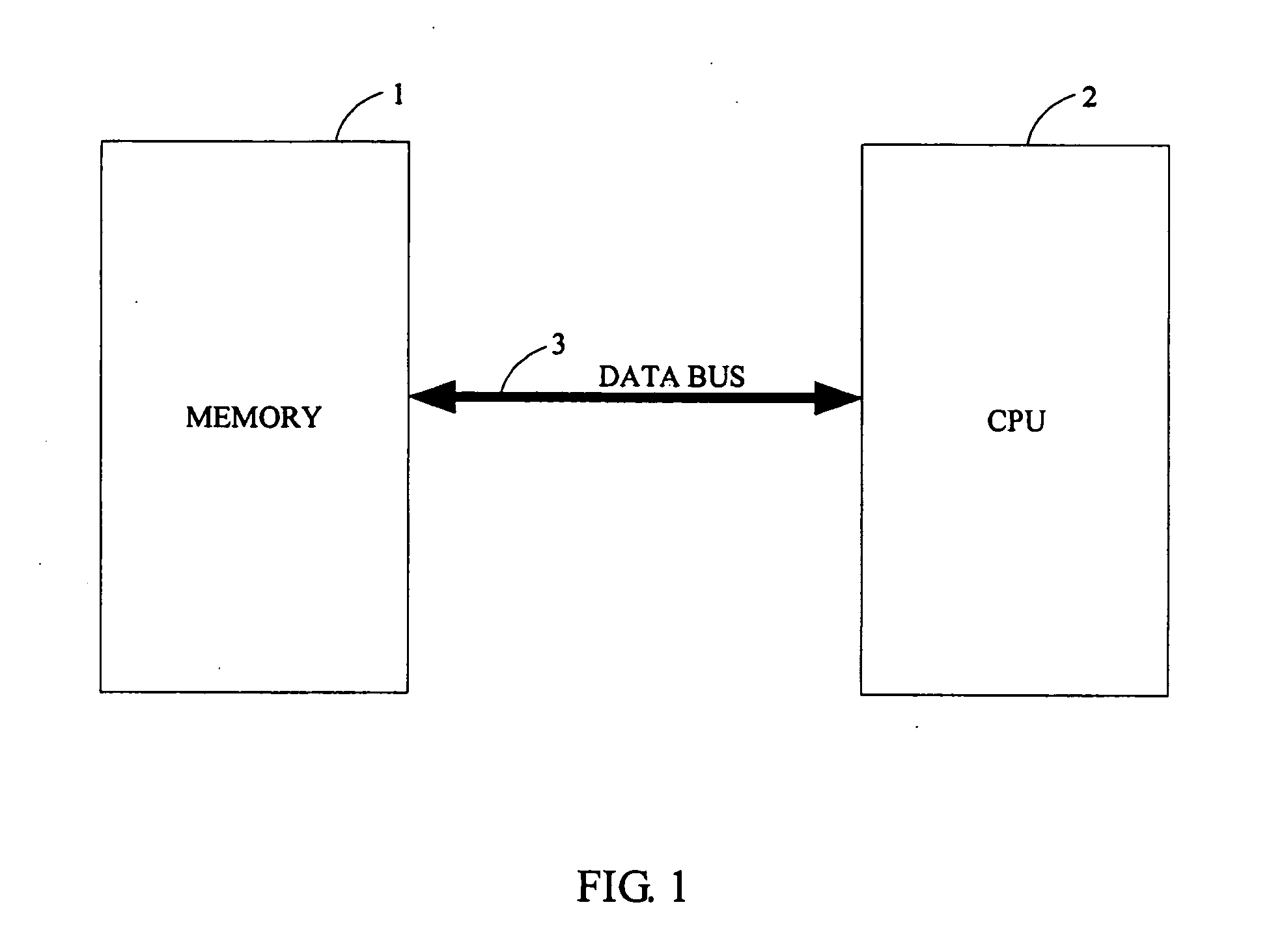
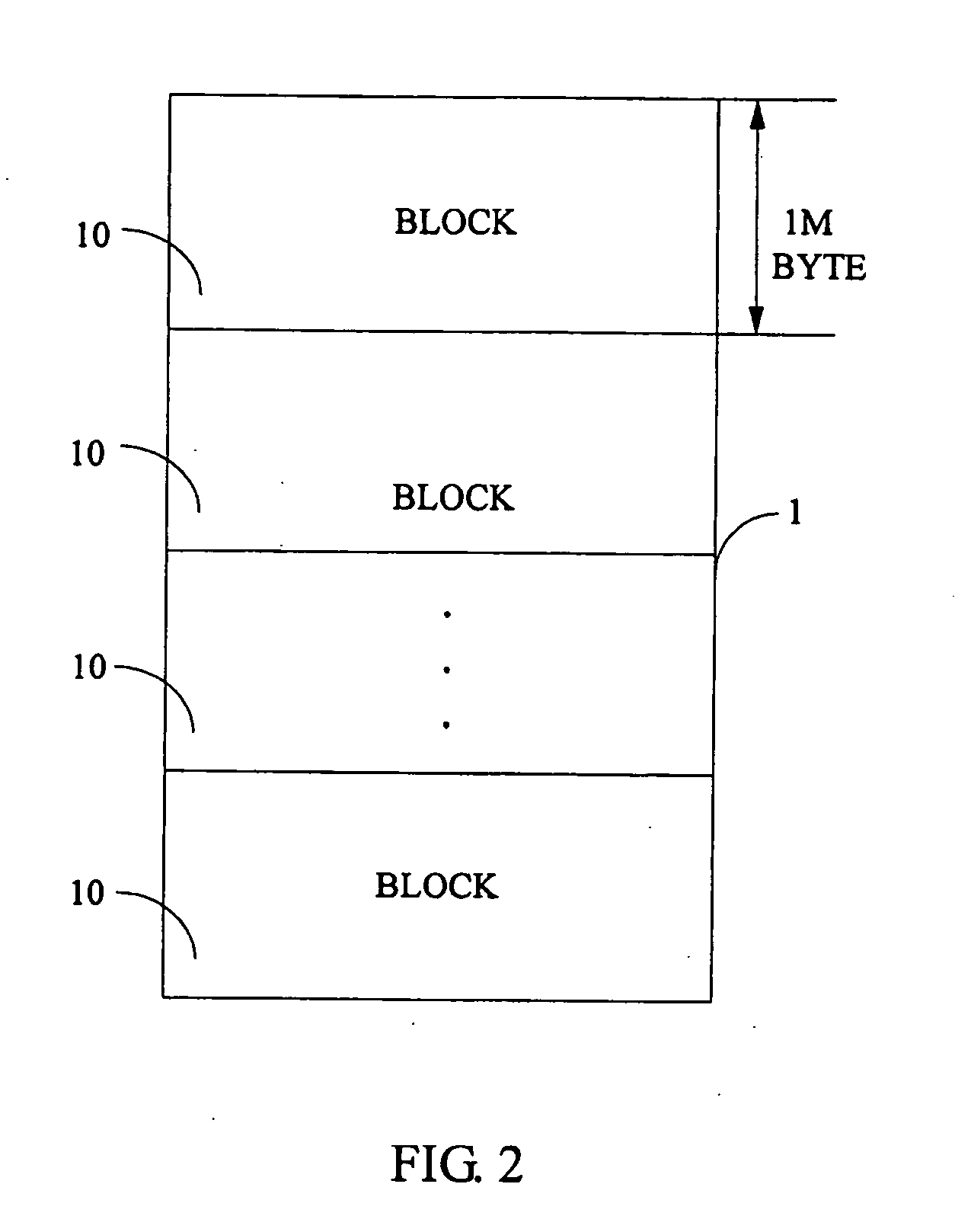
System and method for securely storing data in a memory
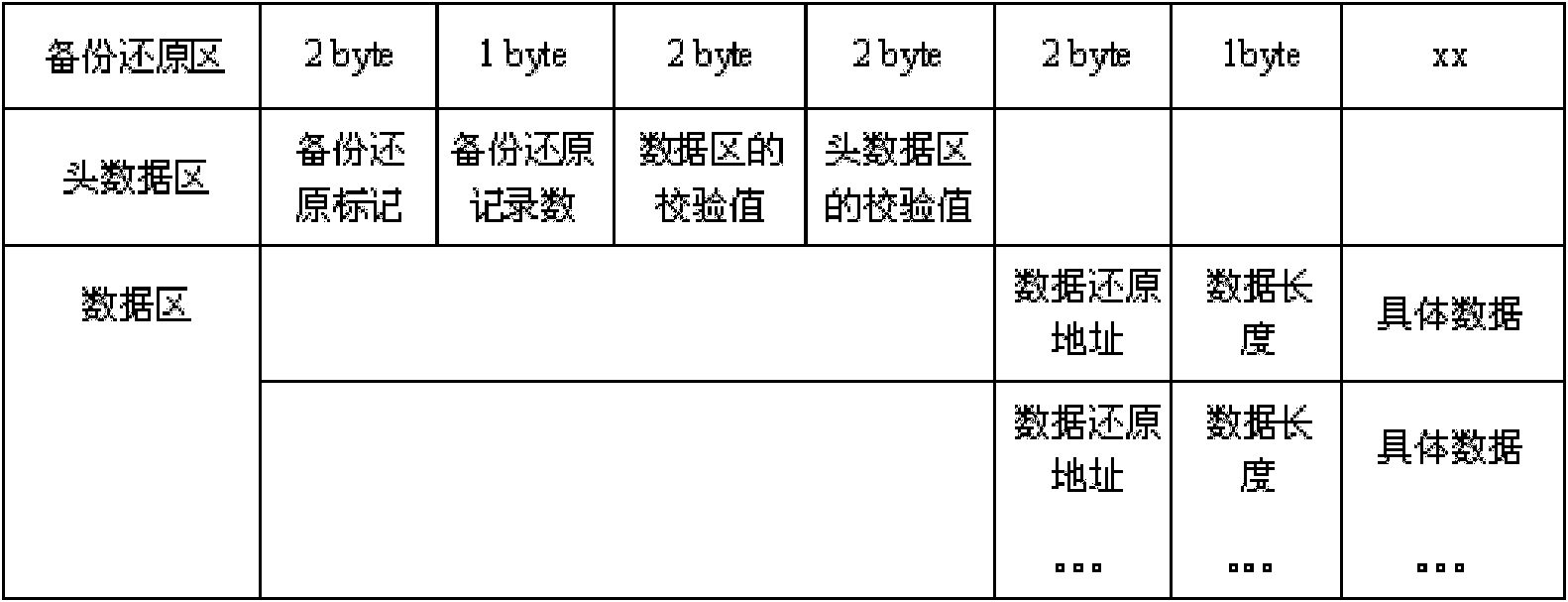
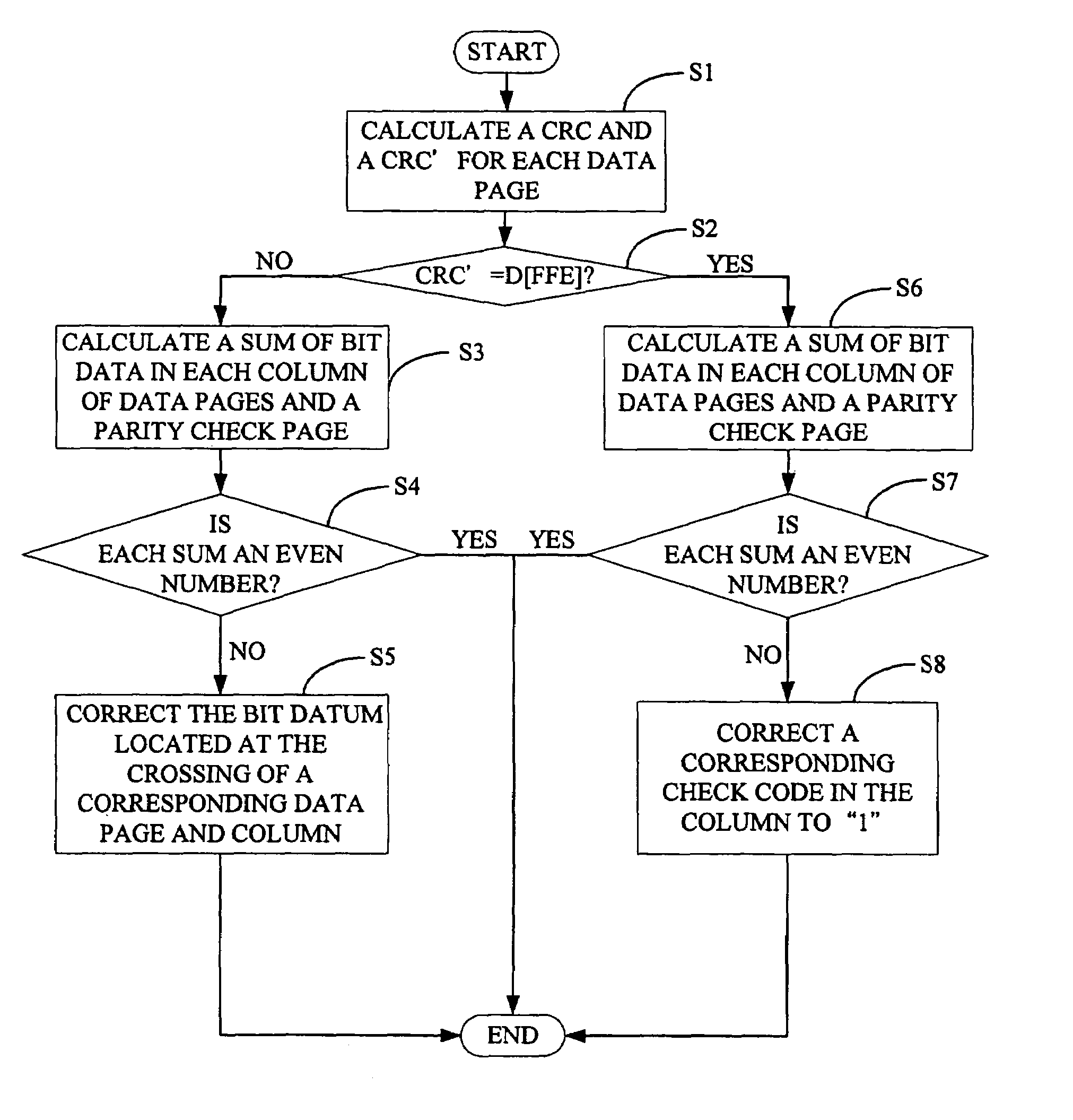
InactiveUS20050091569A1Ensure correctnessEnsure completenessCode conversionCoding detailsByte addressingTerm memory
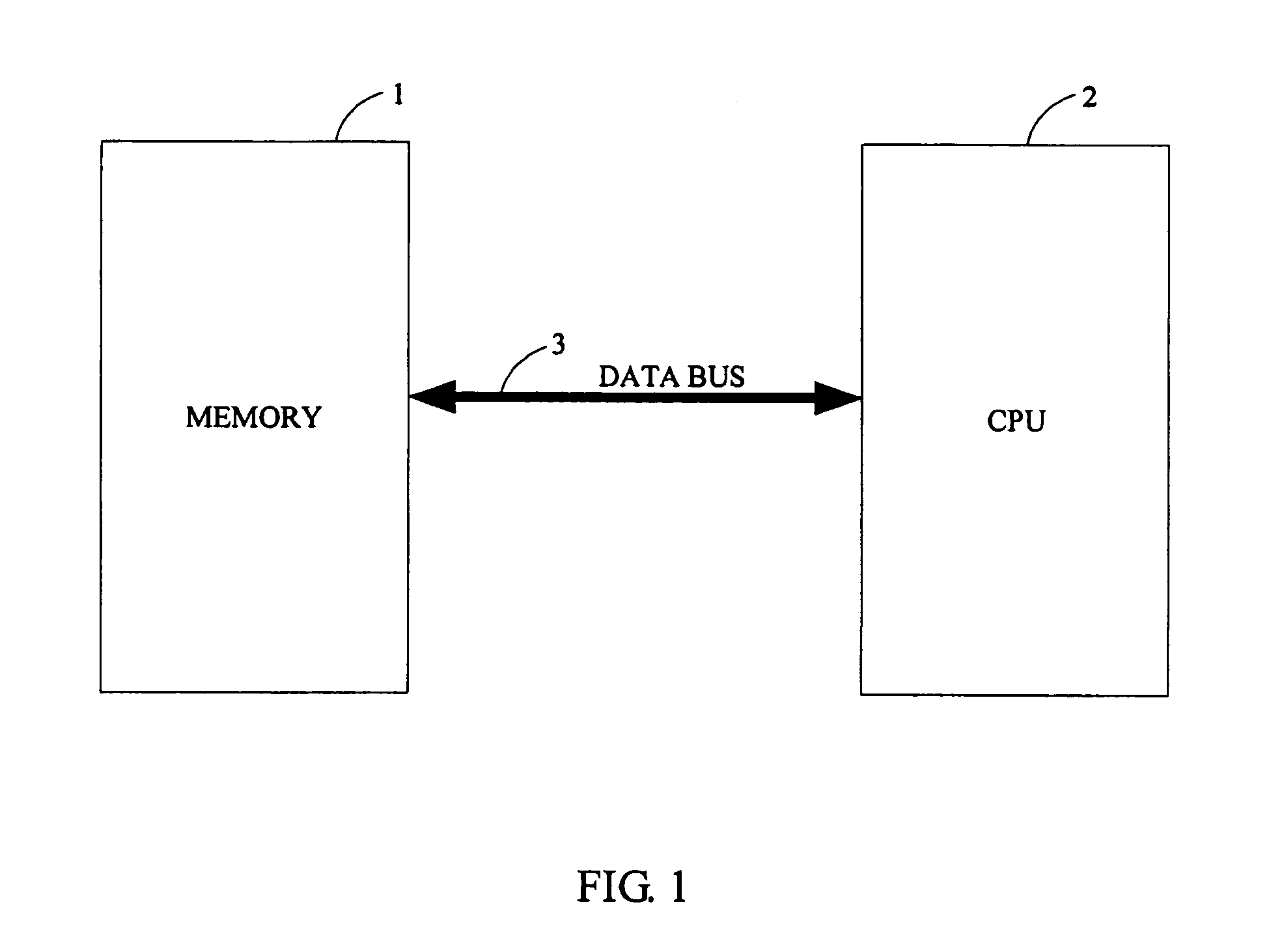
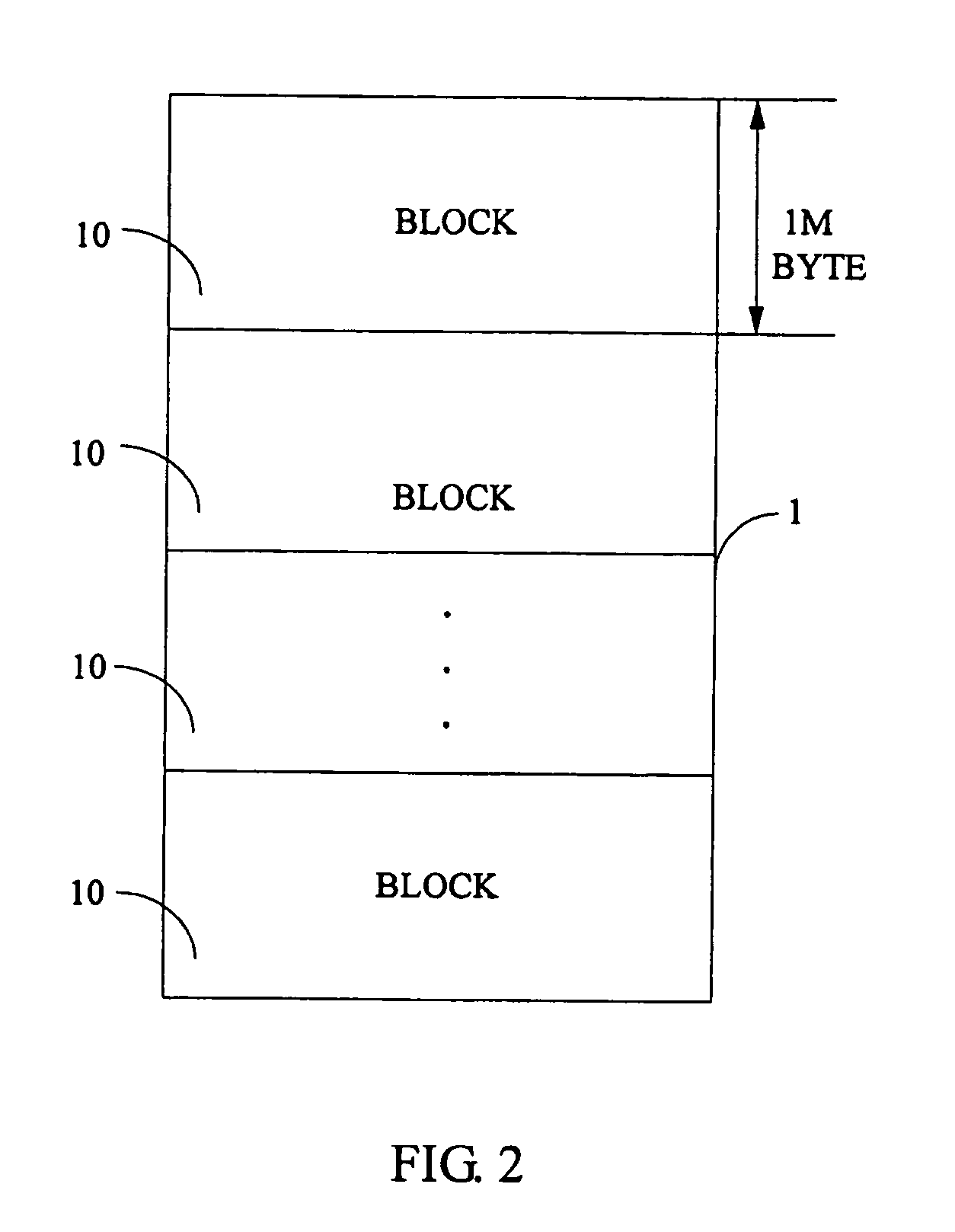
A system for securely storing data in a memory includes a memory (1) and a CPU (Central Processing Unit) (2). The memory is divided into a plurality of fixed-size blocks (10) for storing data. Each block includes a plurality of data pages (101), and a parity check page (102) storing check codes for checking and recovering byte data. Each data page includes a plurality of byte addresses for storing byte data including a CRC (Cyclic Redundancy Check), and a complement of the CRC in the hexadecimal system expressed as CRC′. The CPU is for calculating a CRC for each data page according to byte data of the data page, calculating a CRC′ based on the CRC of the data page, and for identifying and correcting any incorrect bit data. A related method is also disclosed.
Owner:CLOUD NETWORK TECH SINGAPORE PTE LTD
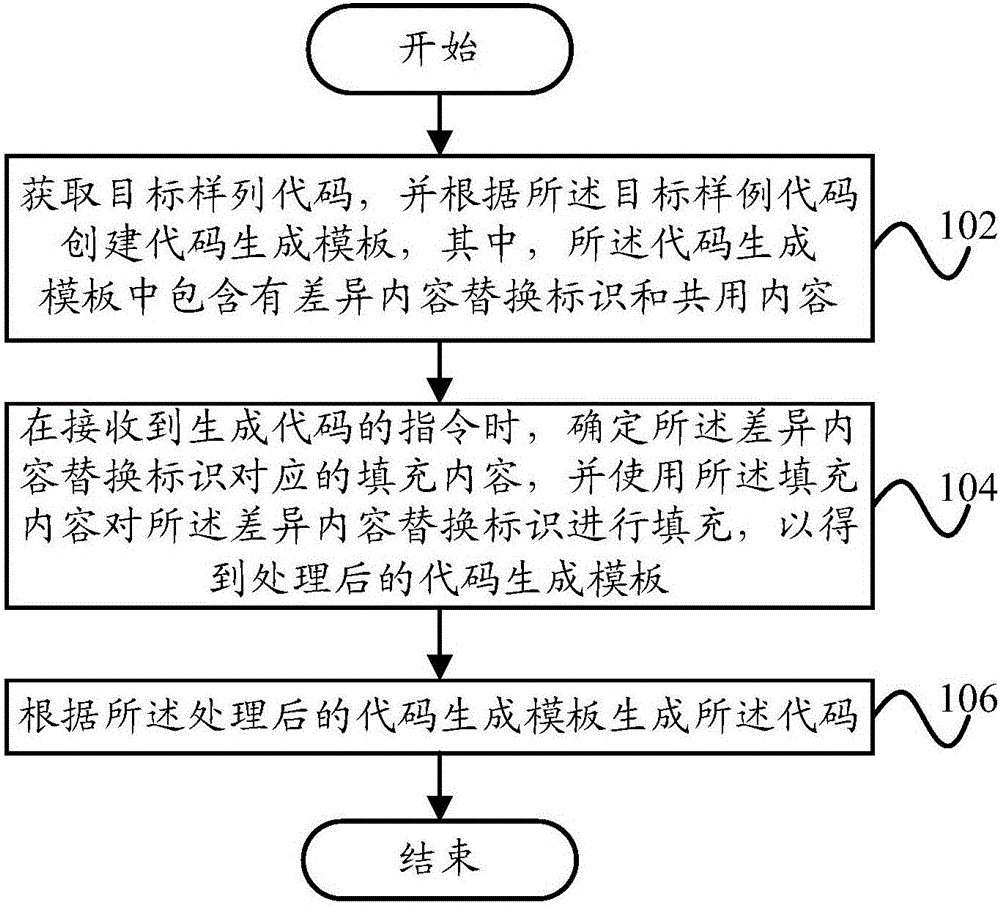
Code generation method and code generation system
ActiveCN106528165AImprove development efficiencyEnsure normativeIntelligent editorsSpecific program execution arrangementsProgramming languageItem generation
The invention provides a code generation method and a code generation system. The code generation method comprises obtaining a target sample code, and creating a code generation template in dependence on the target sample code, the code generation template including a different content replacing identification and a sharing content; determining the fill content corresponding to the different content replacing identification when a code generation instruction is received, and filling the different content replacing identification with the fill content in order to obtain a processed code generation template; and generating the code in dependence on the processed code generation template. According to technical scheme, the code can be generated based on the created code generation template, the code exploitation efficiency can be effectively improved, and the code normativity and correctness can be ensured.
Owner:ZICT TECH CO LTD
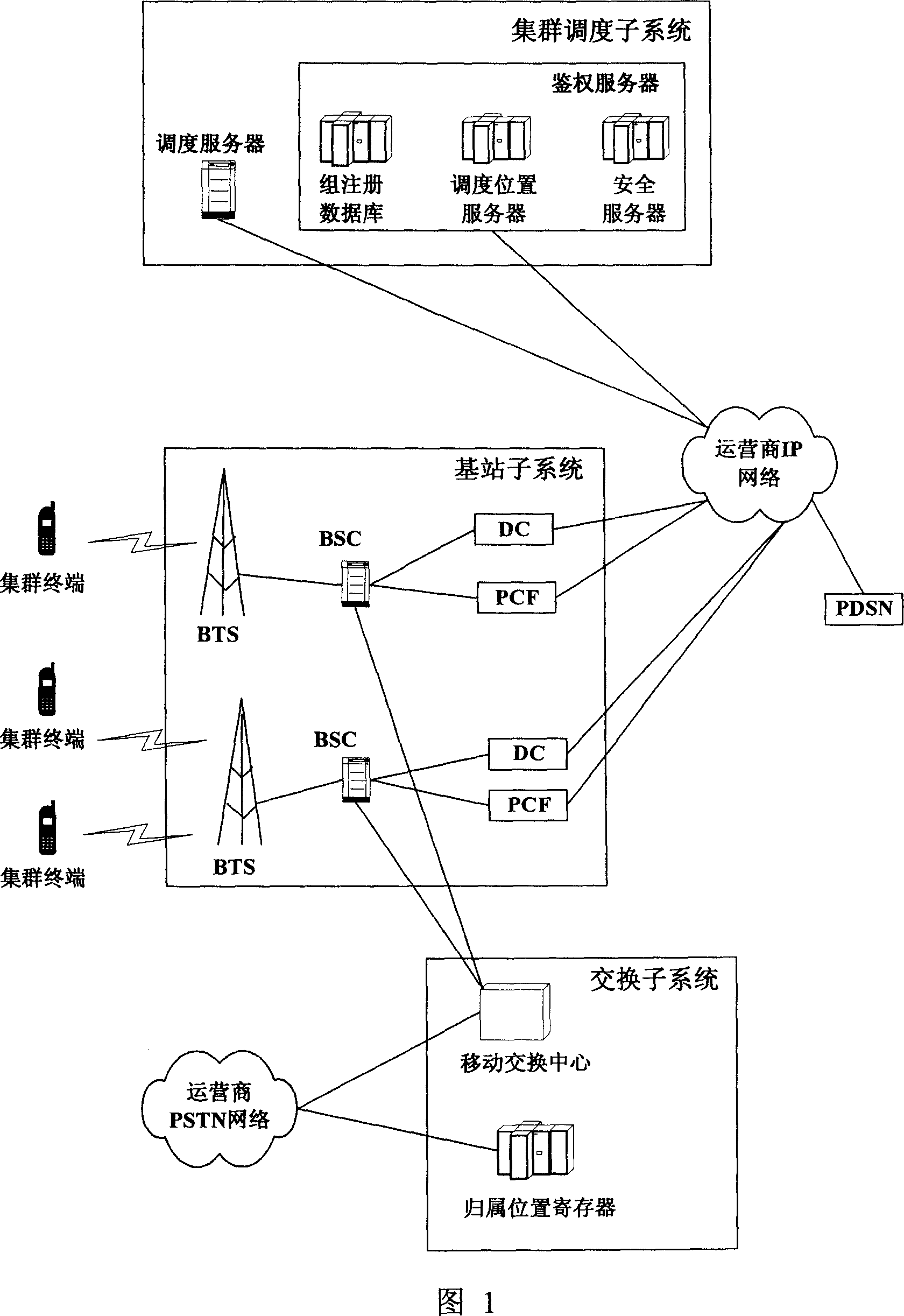
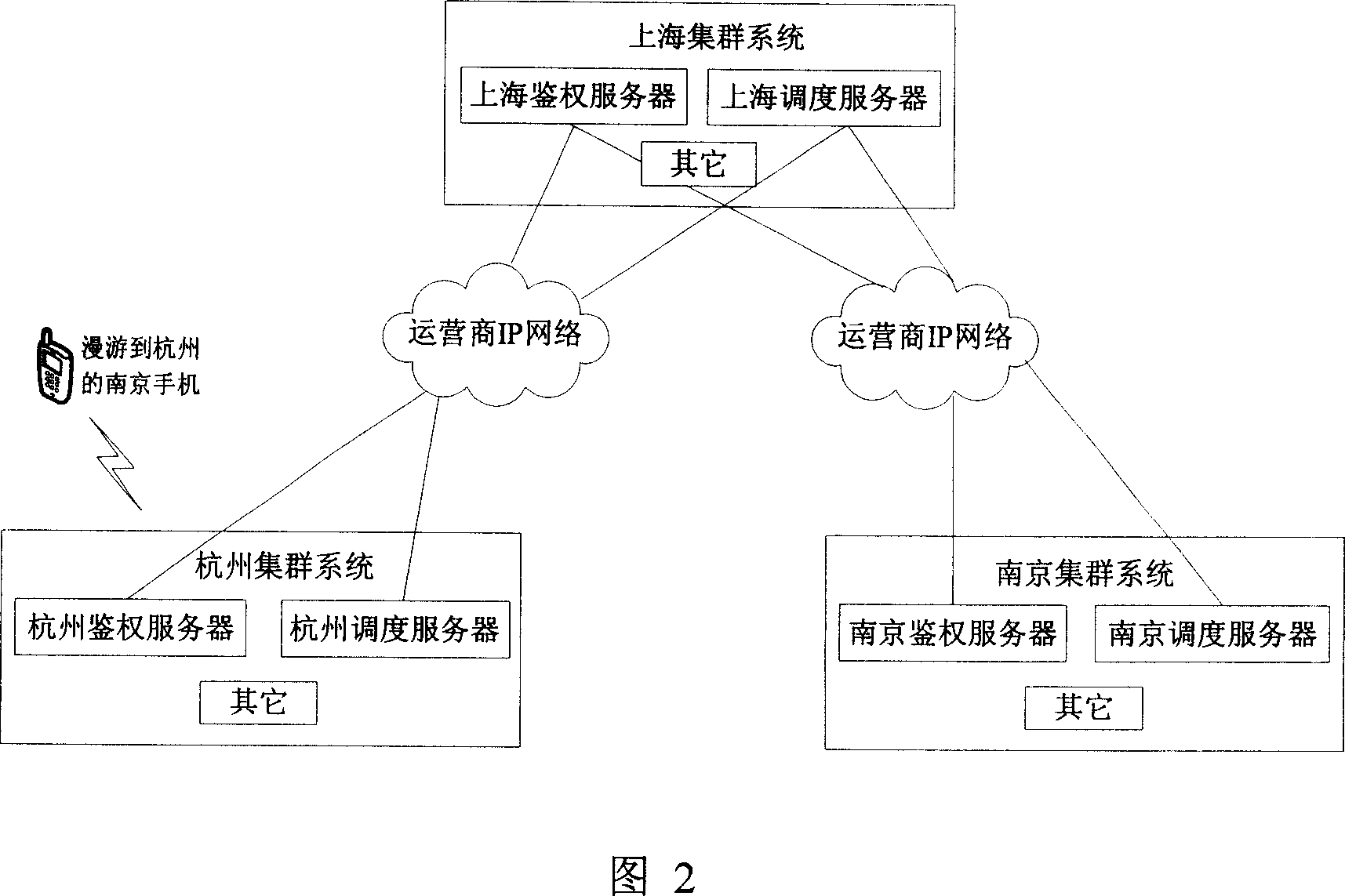
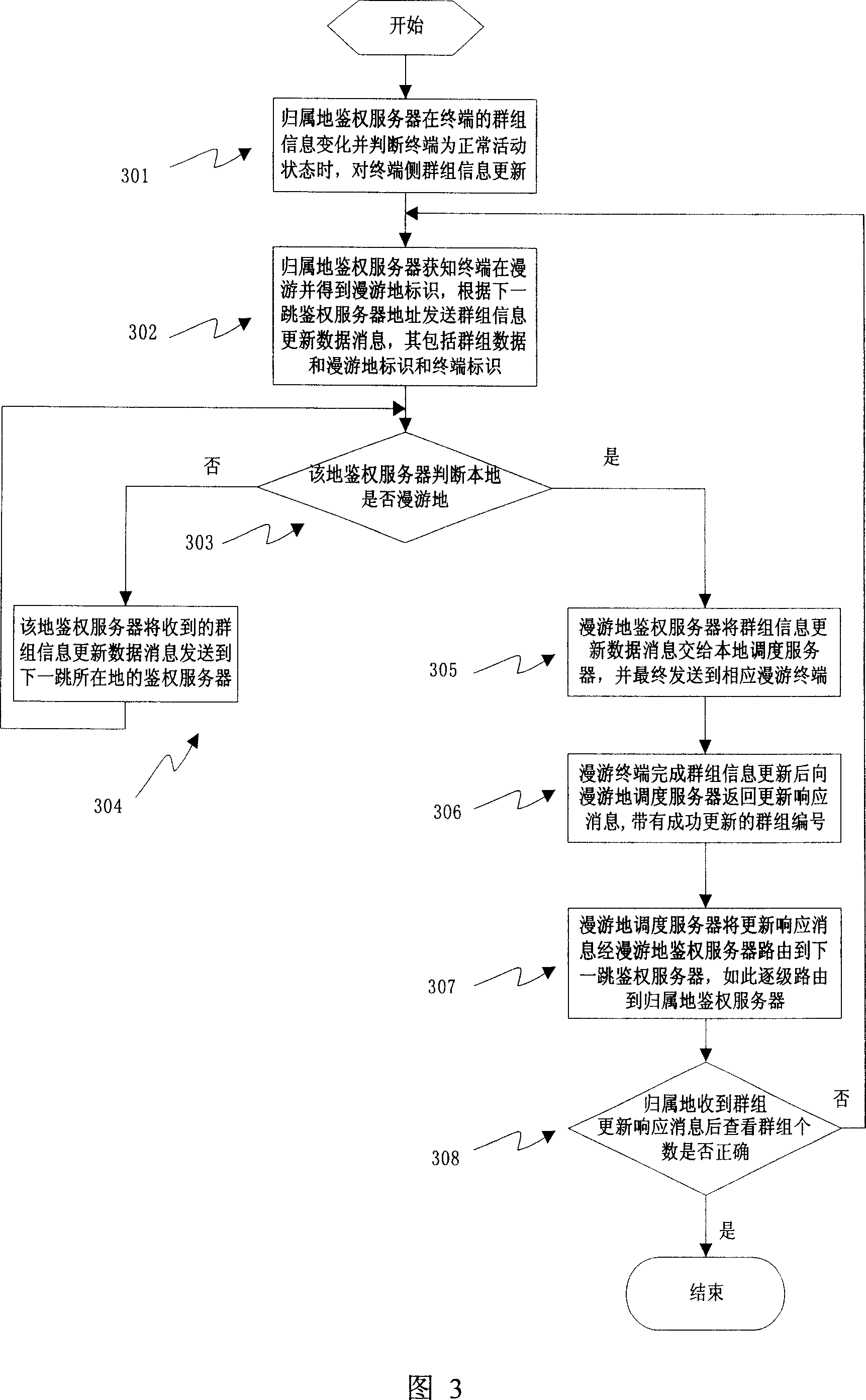
Method for realizing roaming terminal group information updating for cluster system
ActiveCN1937833AEnsure timelinessEnsure correctnessNetwork topologiesBroadcast service distributionTelecommunicationsInformation access
The invention discloses an information updating method of the roaming terminal group in cluster system. When the apanage authentication server judges that whether the group information of roaming terminal group has changed and it is in normal active state. It will generate one or many group information to update the data which includes the terminal mark and the new group information; the apanage authentication server gets the information of the terminal roaming position and the routing information access to authentication server of the roaming position to transfer the data message to the scheduling server of the roaming position through the authentication server of the roaming position, then it is transferred to the roaming terminal by the scheduling server of the roaming position; the roaming terminal updates the group information by using new group information. The group information updating in the invention can be launched by the roaming terminal or the authentication server and transmitted further. The terminal can reverse the response to insure the safety and betimes of the information.
Owner:SHENZHEN ZTE TRUNKING TECH CORP
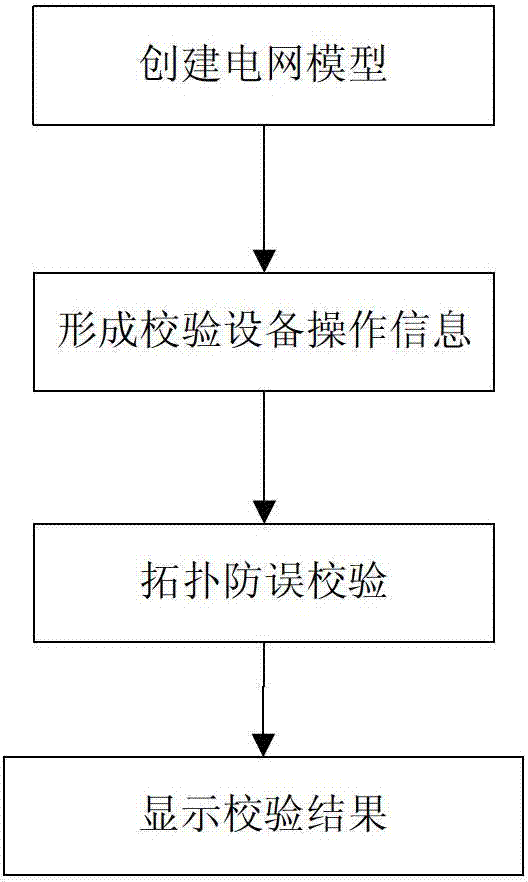
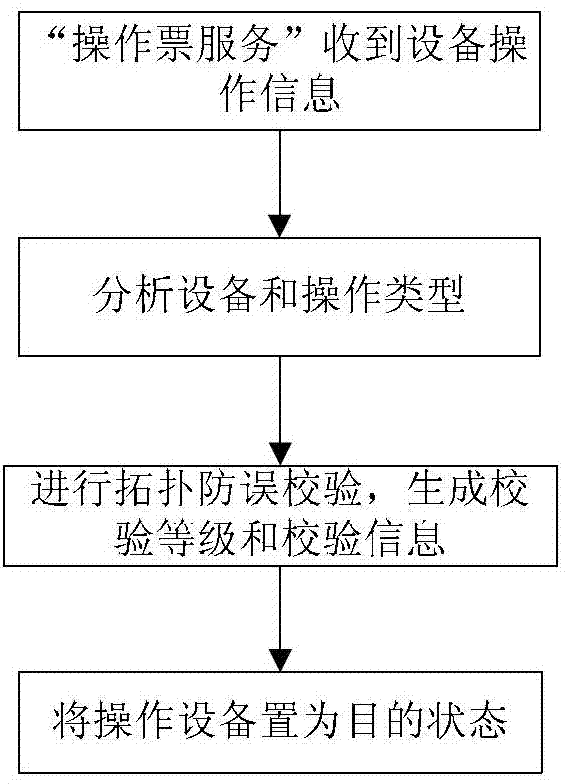
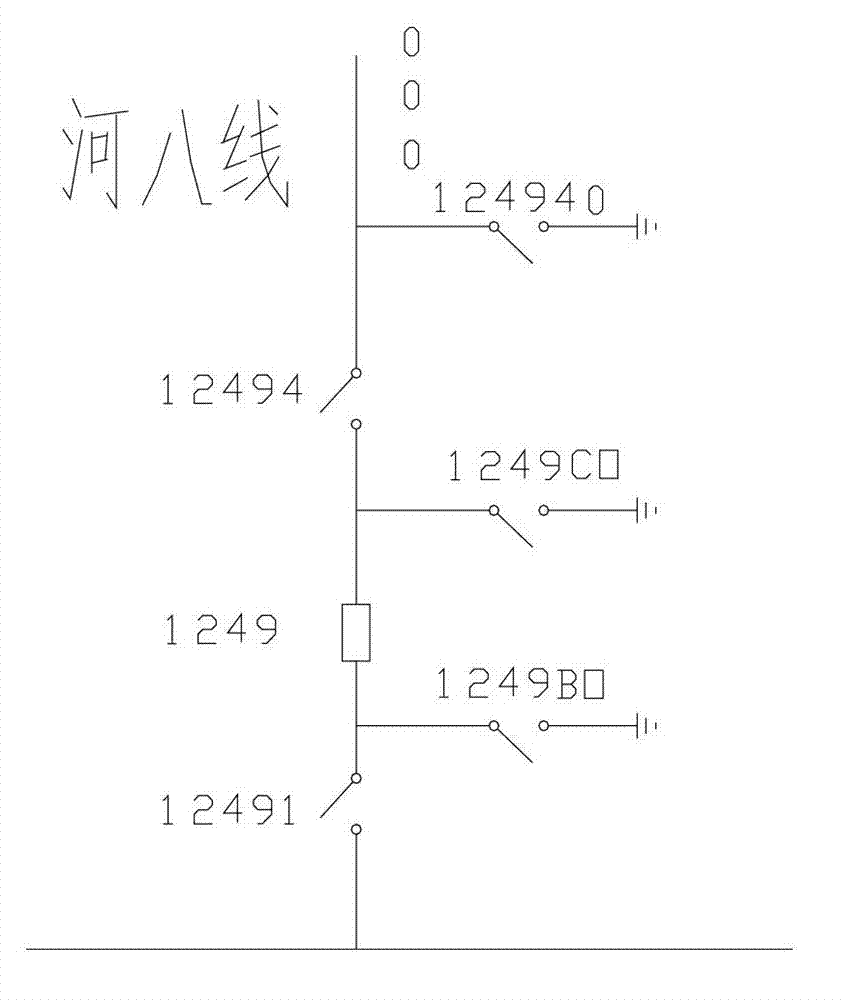
Topological anti-error check method of power dispatching master station type integrated intelligent anti-error system
The invention discloses a topological anti-error check method of a power dispatching master station type integrated intelligent anti-error system. The method comprises the following steps of: 1, creating a grid model; 2, forming check equipment operation information; 3, performing topological anti-error check; and 4, displaying check level and check information. The step of performing the topological anti-error check comprises the following sub-steps of: 3-1, after the master station type integrated intelligent anti-error system receives the equipment operation information, analyzing operation equipment and operation type, checking the current operation equipment, if the current operation equipment is not found, giving a prompt, and if the current operation equipment is found, executing the step 3-2; 3-2, performing the topological anti-error check on the current operation of the operation equipment according to a topological relation between the current grid operation mode and the equipment, and generating the check level and the check information; and 3-3, setting the state of the operation equipment as a destination state. By adoption of the method, the topological anti-error check is performed on the basis of the grid model, a graph and real-time operation mode data, and the accuracy and safety of dispatching operation are ensured.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID
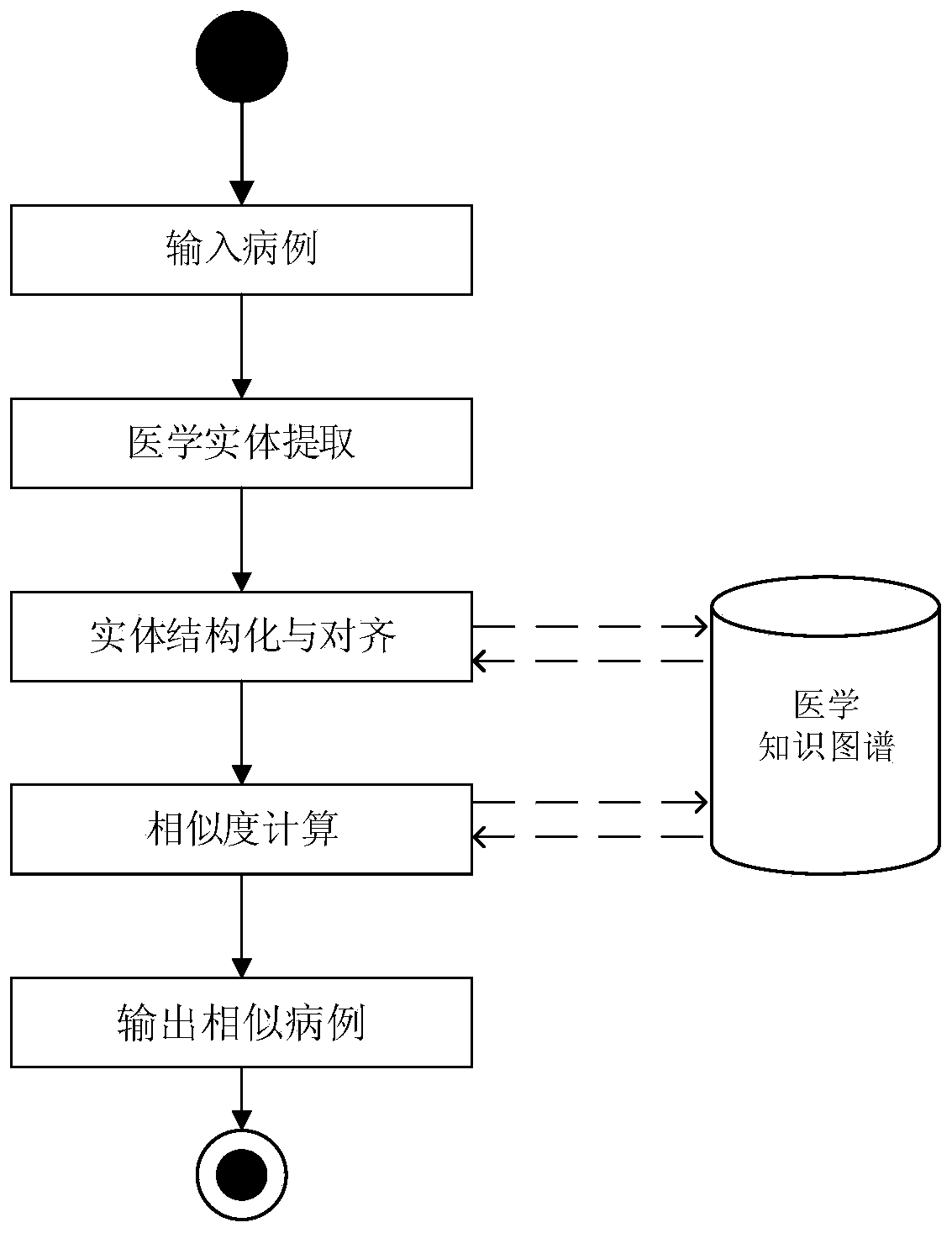
Semantic similar case retrieval method and device based on medical knowledge graph
ActiveCN111414393AEnsure correctnessEnsure normativeMedical data miningText database indexingMedical knowledgeSemantic network
The invention discloses a semantic similar case retrieval method and device based on a medical knowledge graph. The method comprises the steps of: obtaining electronic cases meeting case content specification requirements; performing structured processing on the electronic case text, and combining with a medical knowledge graph to obtain a structured electronic case with unified specification terms; calculating the similarity between the structured electronic case and a case in a library by combining the content matching degree and the scale similarity degree; and sorting and outputting the cases in the library according to the calculated similarity. According to the method, medical knowledge graph alignment is combined, and a semantic similarity calculation model is constructed accordingto the semantic network of the knowledge graph to calculate the similarity between the structured electronic case and the case in the library; and both the matching number and the matching metric value are considered, so that the similarity is defined as more matching and accurate matching, and the granularity requirement and accuracy of similar case matching are improved.
Owner:湖南科创信息技术股份有限公司
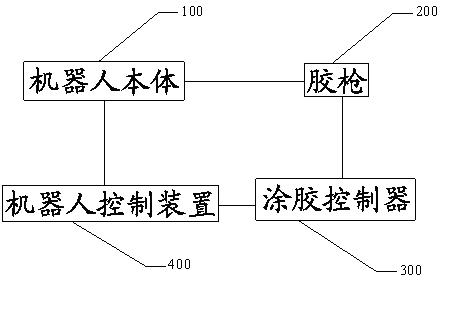
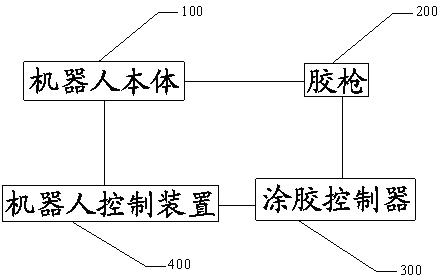
Gluing robot and gluing method thereof
InactiveCN102513268AEnsure correctnessEnsure accuracy andLiquid surface applicatorsSpraying apparatusControl systemRobot control
The invention discloses a gluing robot and a gluing method of the gluing robot. The gluing robot comprises a robot body, a glue gun, a gluing controller and a robot control device, wherein the robot control device is connected with the gluing controller and the robot body; and the glue gun is connected with the robot body and the gluing controller. Through the gluing robot and thegluing method, the gluing process can be completed automatically, and various modes of vehicles are glued at one station; and before gluing, the robot recognizes the modes of the vehicles to call the correct program initiatively to ensure the correctness and the accuracy of the robot gluing. Compared with the conventional gluing process, the automation of the gluing process is improved effectively, a hardware control system is simplified, the cost of the control system is lowered, and the flexibility of the control system is improved.
Owner:CHANGCHUN DAZHENG AUTOMATIC EQUIP
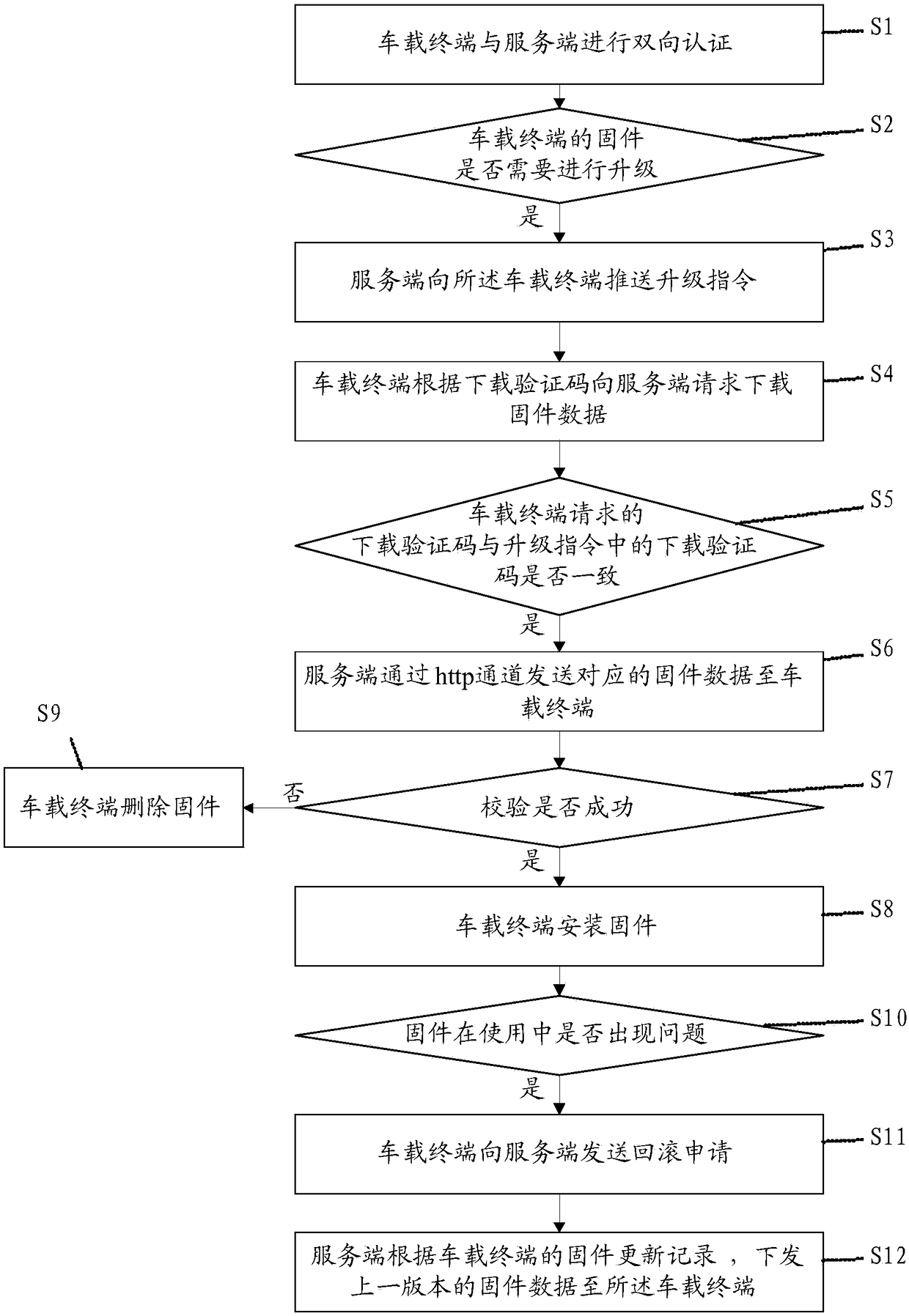
Air upgrade method of vehicle firmware, and computer readable storage medium
ActiveCN109413009AEnsure safetyEnsure correctnessTransmissionSoftware deploymentFirmware versionComputer terminal
The invention discloses an air upgrade method of vehicle firmware, and a computer readable storage medium. The method comprises the following steps that a vehicle-mounted terminal performs two-way authentication with a server; after the authentication is successful, the server judges whether the firmware of the vehicle-mounted terminal needs to be upgraded or not according to a firmware version number; if yes, the server pushes an upgrade instruction to the vehicle-mounted terminal; the vehicle-mounted terminal requests the server to download firmware data according to a downloading verification code; if a downloading verification code requested by the vehicle-mounted terminal is consistent with the downloading verification code in the upgrade instruction pushed by the server to the vehicle-mounted terminal, the server sends the corresponding firmware data to the vehicle-mounted terminal through an https channel; after the vehicle-mounted terminal downloads the firmware, and verifies the downloaded firmware according to the firmware size and a firmware MD5 verification code; if the verification is successful, the vehicle-mounted terminal installs the firmware; and if the verification fails, the vehicle-mounted terminal deletes the firmware. By the adoption of the air upgrade method disclosed by the invention, the upgrade efficiency of the vehicle firmware can be improved, and meanwhile the security of the firmware data is ensured.
Owner:XIAMEN YAXON NETWORKS CO LTD
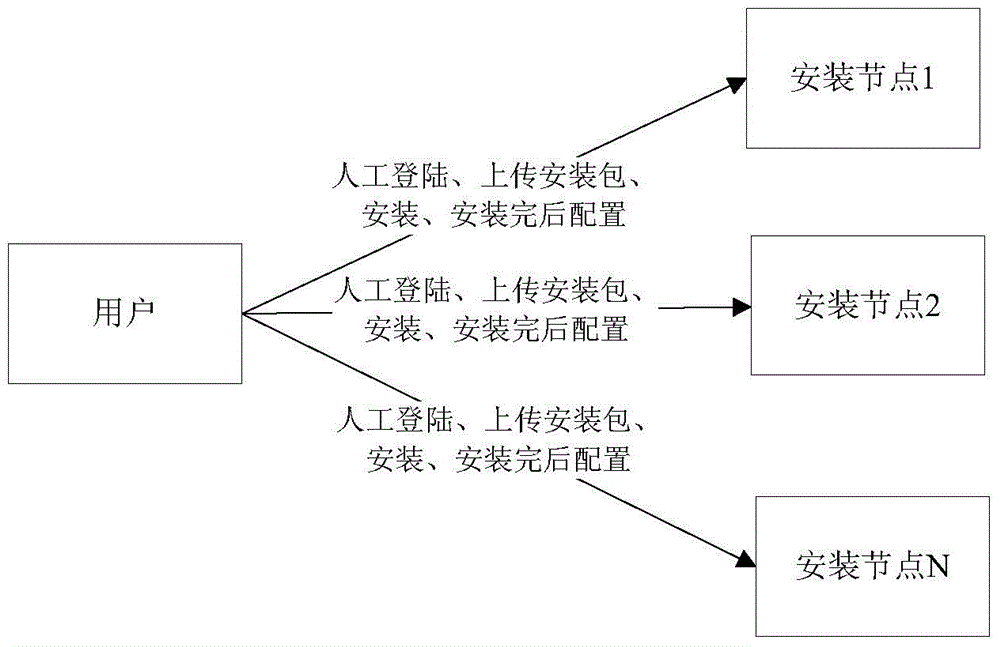
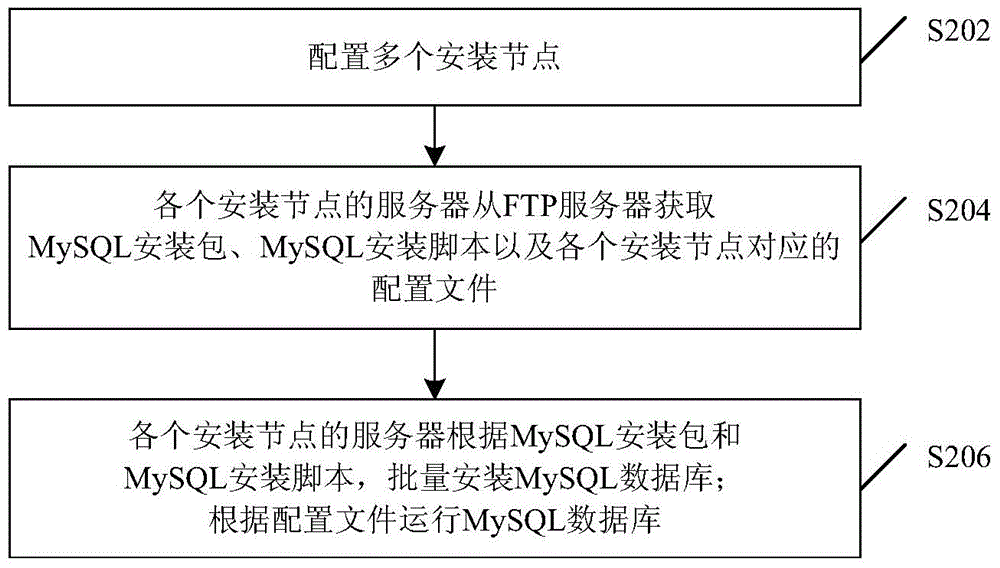
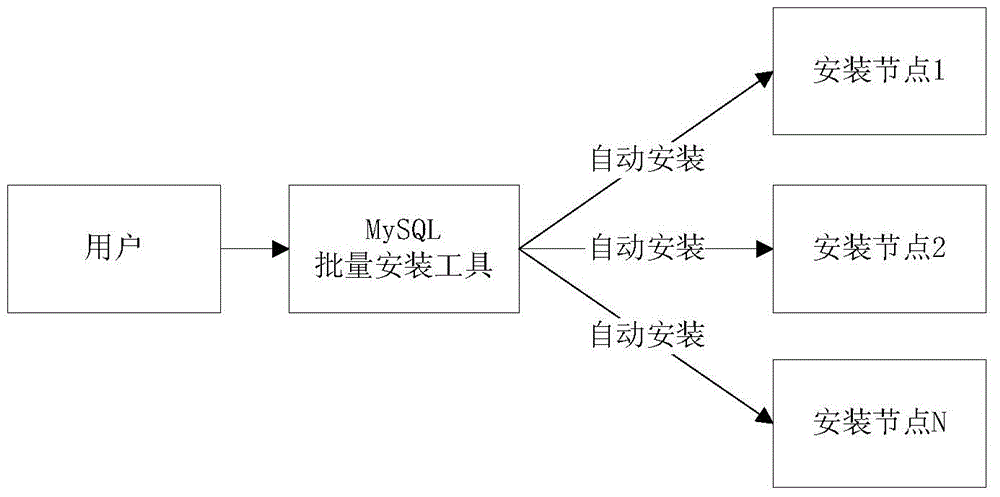
Method and device for installing MySQL database
InactiveCN105224348ASolve excessive energy consumptionResolution timeProgram loading/initiatingQuery languageOperating system
The invention discloses a method and device for installing a MySQL (Structured Query Language) database. The method comprises the following steps: a plurality of installation nodes are configured; a server on each installation node obtains a MySQL installation package, a MySQL installation script and a configuration file corresponding to each installation node from a reservation server, and the MySQL database is subjected to batch installation; the server on each installation node carries out the batch installation on the MySQL database according to the MySQL installation package and the MySQL installation script; and according to the configuration file, the MySQL database runs. The quick batch installation of the MySQL database is realized, the problem in the relevant prior that an installation method of the MySQL database consumes excessive vigor and time is solved, the complicated degree and the complexity of the large-scale installation of MySQL are lowered, installation time is greatly shortened, misoperation possibility is greatly lowered, and installation success rate and correctness can be guaranteed.
Owner:ZTE CORP
Power failure protection method for intelligent IC (integrated circuit) card data
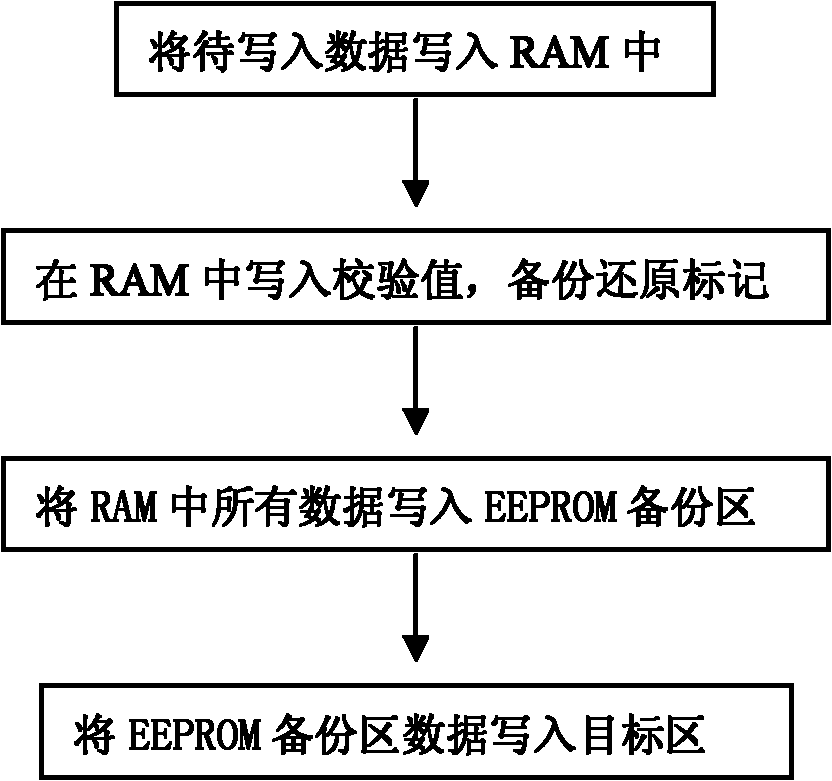
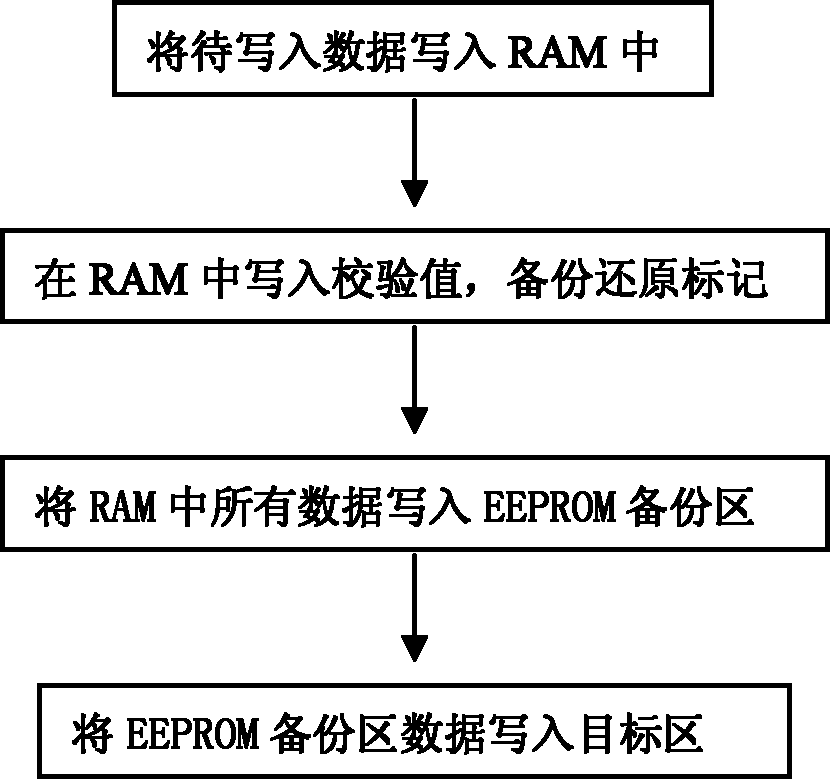
InactiveCN102609332AEnsure correctnessEnsure integrityRecord carriers used with machinesRedundant operation error correctionElectricityProgrammable read-only memory
The invention discloses a power failure protection method for intelligent IC (integrated circuit) card data. When an IC card is applied, data in the card are frequently modified, and if power fails after the data are erased in the process of modification, data to be written are not normally written while the original data are erased, and important data are lost. When the data in the card are modified, information to be written is firstly backed up to an RAM (random access memory), backup checking information is then computed, a backup and restore mark is set in a restore state, the information is written into the RAM together, all data are organized in the RAM and then written into an EEPROM (electrically erasable programmable read-only memory) backup area, the data are restored, effective data are written into a target data area, and then the backup and restore mark in the backup area is modified into a backup state. Data backup time is shortened by the aid of rapid access features of the RAM, the data are organized in the RAM and then written into the EEPROM backup area once, the frequency of writing the data into an EEPROM is effectively decreased, and the service life of the IC card is prolonged.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
System and method for securely storing data in a memory
InactiveUS7213191B2Ensure correctnessEnsure completenessCode conversionError correction/detection by combining multiple code structuresByte addressingByte
A system for securely storing data in a memory includes a memory (1) and a CPU (Central Processing Unit) (2). The memory is divided into a plurality of fixed-size blocks (10) for storing data. Each block includes a plurality of data pages (101), and a parity check page (102) storing check codes for checking and recovering byte data. Each data page includes a plurality of byte addresses for storing byte data including a CRC (Cyclic Redundancy Check), and a complement of the CRC in the hexadecimal system expressed as CRC′. The CPU is for calculating a CRC for each data page according to byte data of the data page, calculating a CRC′ based on the CRC of the data page, and for identifying and correcting any incorrect bit data. A related method is also disclosed.
Owner:CLOUD NETWORK TECH SINGAPORE PTE LTD
Method for processing sample data based on waveform fitting and secondary sampling
ActiveCN101635446AProtect normal executionOvercoming protectiveEmergency protective arrangements for automatic disconnectionInformation technology support systemElectricityTransformer
The invention discloses a method for processing sample data based on waveform fitting and secondary sampling. The method comprises the following steps: 1) determining the number of sample points which fulfill loss permission under a certain calculation accuracy condition according to the sample frequency of MU and the number of sample data points of transmission of each frame in a digital transformer station; 2) establishing a status word for data of each sample point in a primary buffer zone and a protective buffer zone, setting a 'valid' mark when the corresponding sample data is a real virtual value, and setting an 'invalid' mark when the value is invalid; 3) monitoring the communication condition of a device in real time, marking the state of the corresponding sample data into 'invalid' if a condition of frame drop / frame error happens; and 4) constructing an electricity fit waveform by cubic spline functions based on the primary sample data, and carrying out secondary sampling on the electricity fit waveform based on frequency tracking. The method solves the problem of insufficient capability of data processing of a protective device under a high speed sampling condition by using the method of waveform fitting based on the cubic spline functions and secondary sampling.
Owner:NARI TECH CO LTD +1
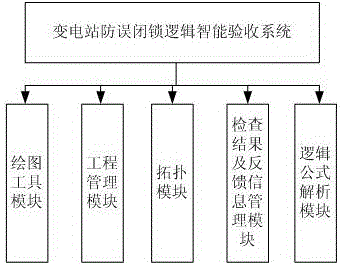
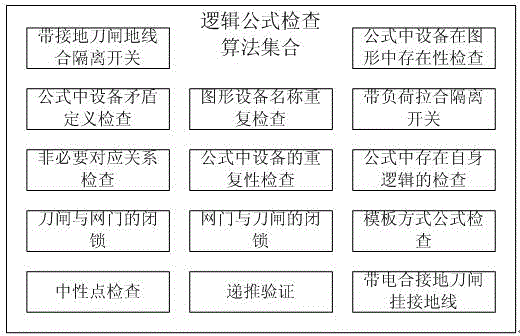
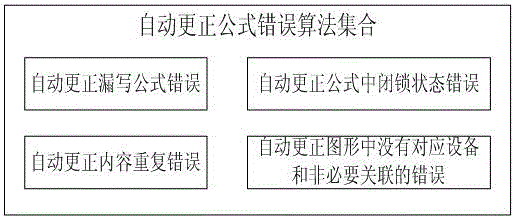
Intelligent check and acceptance system of substation anti-misoperation locking logic
ActiveCN106383958ASolve the efficiency of manual inspectionResolve accuracyData processing applicationsDesign optimisation/simulationMicrocomputerProgramming language
The invention discloses an intelligent check and acceptance system of substation anti-misoperation locking logic. The system comprises an engineering management module used for performing comprehensive management on engineering information, a drawing tool module used for performing conversion, drawing and repair processing on a graph, a topology module used for performing a graph topology search based on graph information and automatically generating anti-misoperation logic according to a topology rule language, a logic formula analysis module used for analyzing a topology language and logic languages of different anti-misoperation system manufacturers, and a check result and feedback information management module used for checking a substation microcomputer anti-misoperation system logic formula according to the anti-misoperation logic generated by topology analysis. Therefore, the technical effects of capability of automatically performing check and acceptance, and relatively high efficiency and accuracy are achieved.
Owner:国网四川省电力公司天府新区供电公司 +1
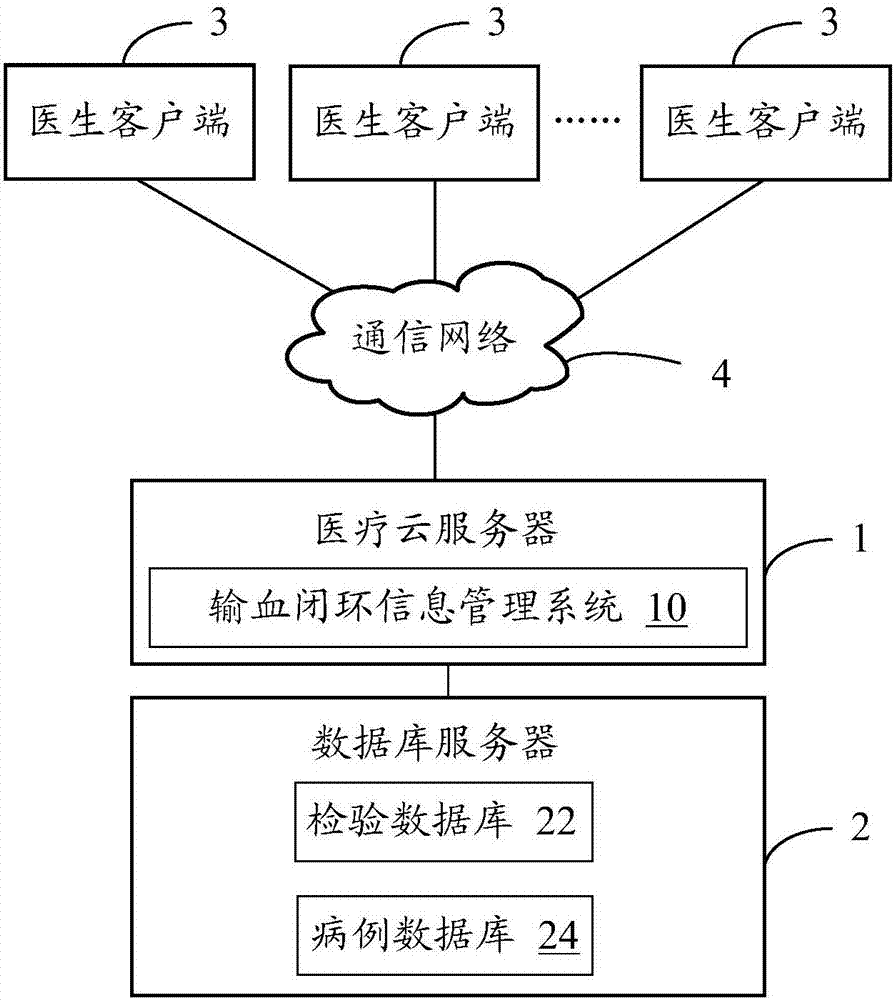
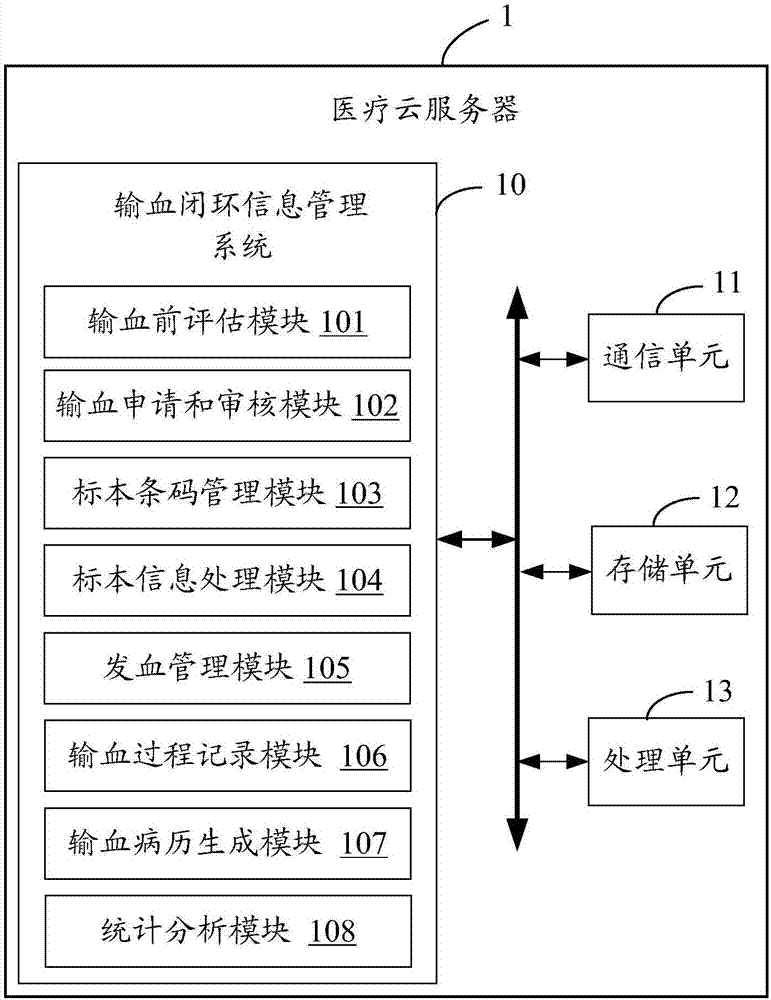
Transfusion closed loop control information management system with statistics and analysis function
InactiveCN107480433AGuaranteed reasonablenessEnsure consistencyInformaticsSpecial data processing applicationsInformation processingMedical record
The invention provides a transfusion closed loop control information management system with a statistics and analysis function. The system comprises a pre-transfusion evaluation module, a transfusion application and check module, a specimen bar code management module, a specimen information processing module, a blood delivering management module, a transfusion process recording module, a transfusion medical history generation module and a statistic analysis module. According to the embodiment, the complete flow informatization management from evaluation of application of blood for clinical use, transfusion application and check, specimen management, transfusion process recording to electronic medical history generation can be achieved; meanwhile, by conducting statistics and analysis on the historical blood using conditions, the blood for clinical use is effectively monitored, the blood utilization rate is increased, and the medical accidents due to man-made causes in the blood using process are reduced.
Owner:ANYCHECK INFORMATION TECH
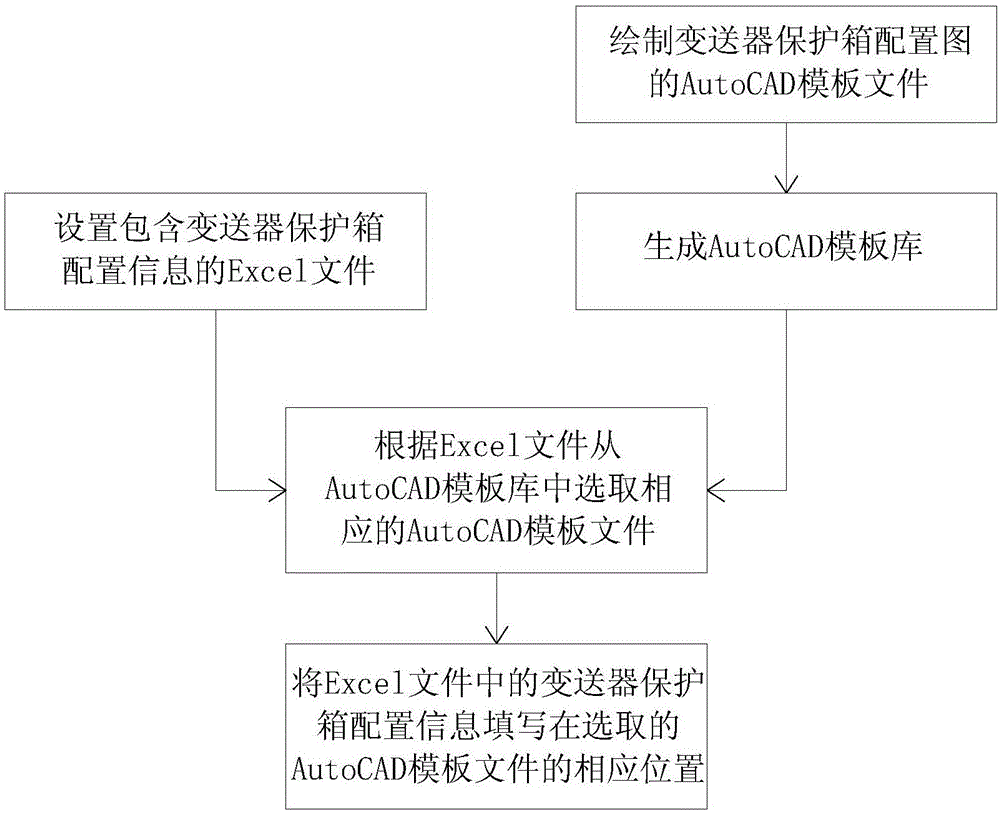
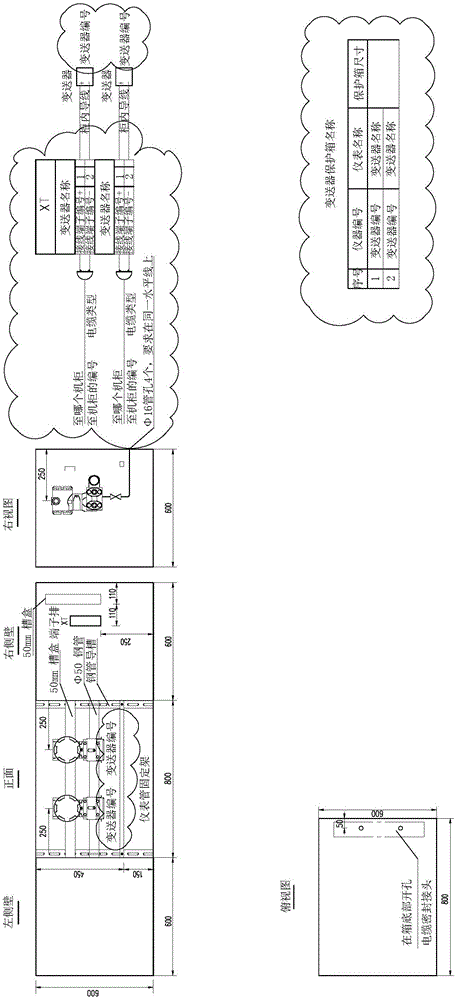
Method for automatically batch generating configuration diagrams of transmitter protection box
ActiveCN105045948AEnsure correctnessEnsure consistencySpecial data processing applicationsConfiguration interactionTemplate library
The present invention discloses a method for automatically batch generating configuration diagrams of a transmitter protection box. The method comprises the following steps of: S1, setting an Excel file comprising configuration information of the transmitter protection box; S2, drawing AutoCAD template files of the configuration diagrams of the transmitter protection box, and generating an AutoCAD template library; S3, selecting a corresponding AutoCAD template file from the AutoCAD template library according to the Excel file; and S4, filling a corresponding position of the selected AutoCAD template file with the configuration information of the transmitter protection box in the Excel file. The method provided by the present invention can save time of drawing batches of configuration diagrams of the transmitter protection box and improve the drawing accuracy.
Owner:CHINA HUADIAN ENG
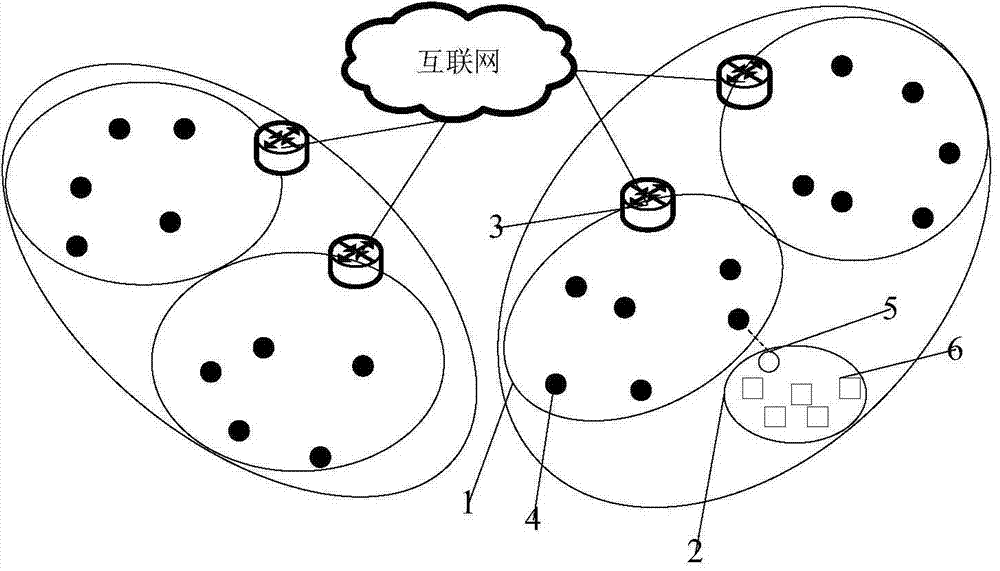
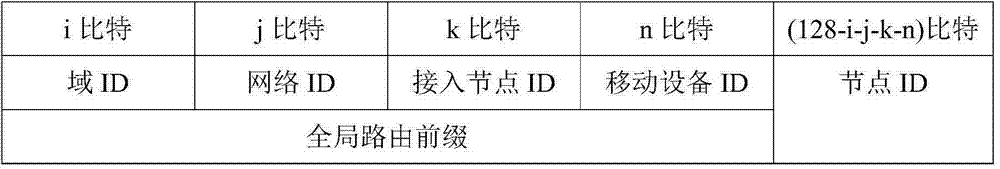
Realization method for wireless network communication based on positioning
The invention provides a realization method for wireless network communication based on positioning. A wireless network is composed of a routing backbone network and a user mobile network, wherein the routing backbone network is composed of an accessing router and more than one accessing node; the user mobile network is composed of mobile equipment and more than one sensor node; each sensor node is communicated with other mobile equipment or the sensor node through the mobile equipment; one user mobile network is used as a whole body to move; one set of the mobile equipment is connected with one accessing node and the accessing node is named as a connected accessing node of the mobile equipment; the mobile equipment is communicated with the other user mobile network through the connected accessing node and the routing backbone network of the connected accessing node; and in a node moving process, a care-of address does not need to be configured and hometown agencies do not need to be accessed, so that the communication performance is greatly improved.
Owner:苏州拉曼莱特科技有限公司
Bidirectional blockchain
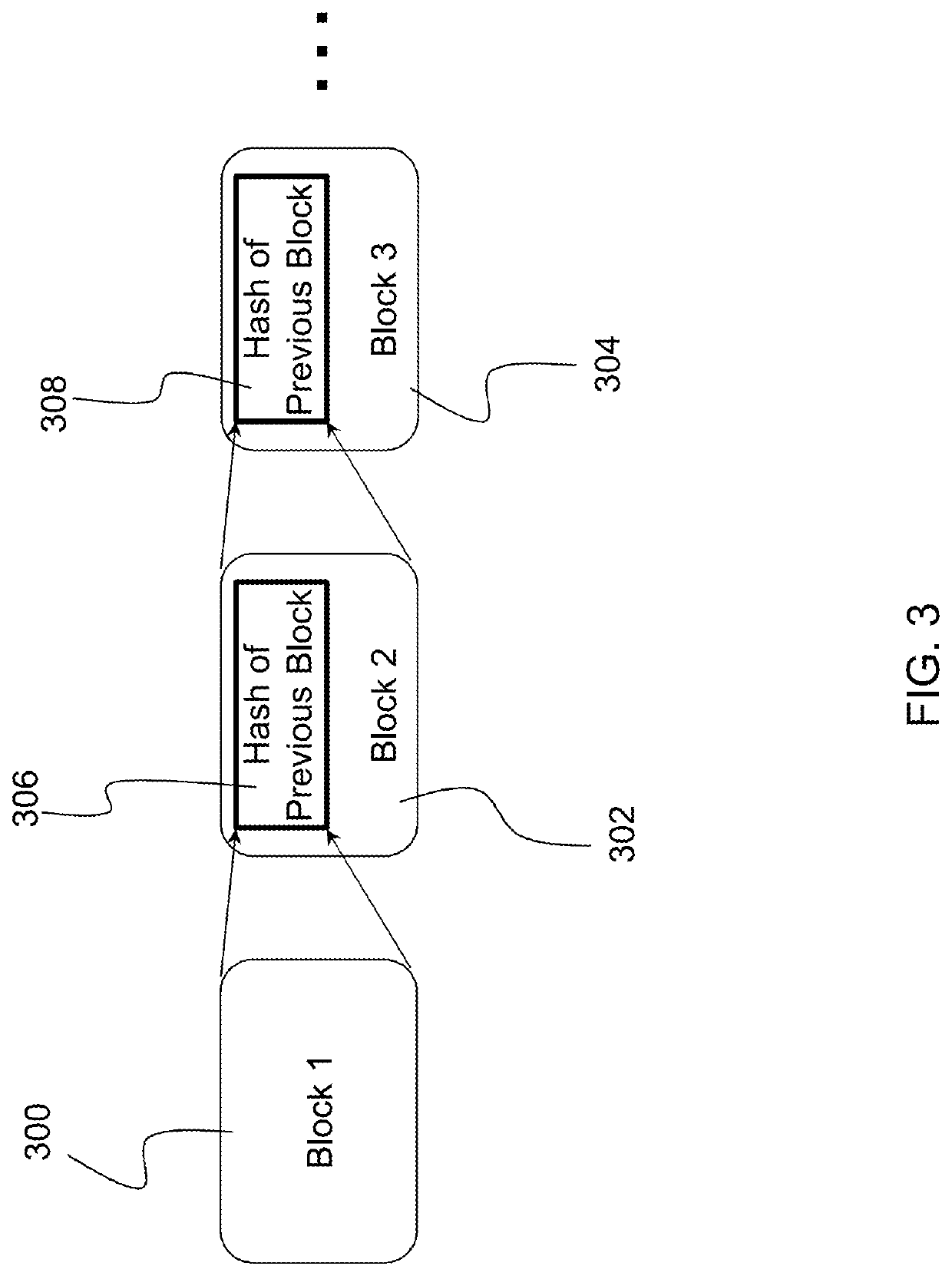
ActiveUS20200036530A1Improving data authenticationData augmentationPublic key for secure communicationUser identity/authority verificationEngineeringData element
Described is a system for improving data authentication using blockchain technology and multi-party computation (MPC). The system ensures authenticity of distributed data sent from one or more servers to the distributed clients. The system initializes MPC protocols to ensure secrecy of keys used to sign a new data element. Blockchain technology is utilized to ensure correctness and integrity of the new data element. A bidirectional blockchain is used such that a forward blockchain stores the new data element to be received by the distributed clients, and a reverse blockchain stores a public key used by the distributed clients to verify authenticity of the new data element stored in the forward blockchain. Signing of the new data element with the public key causes a previous public key to expire.
Owner:HRL LAB
Arc light monitoring and protecting system
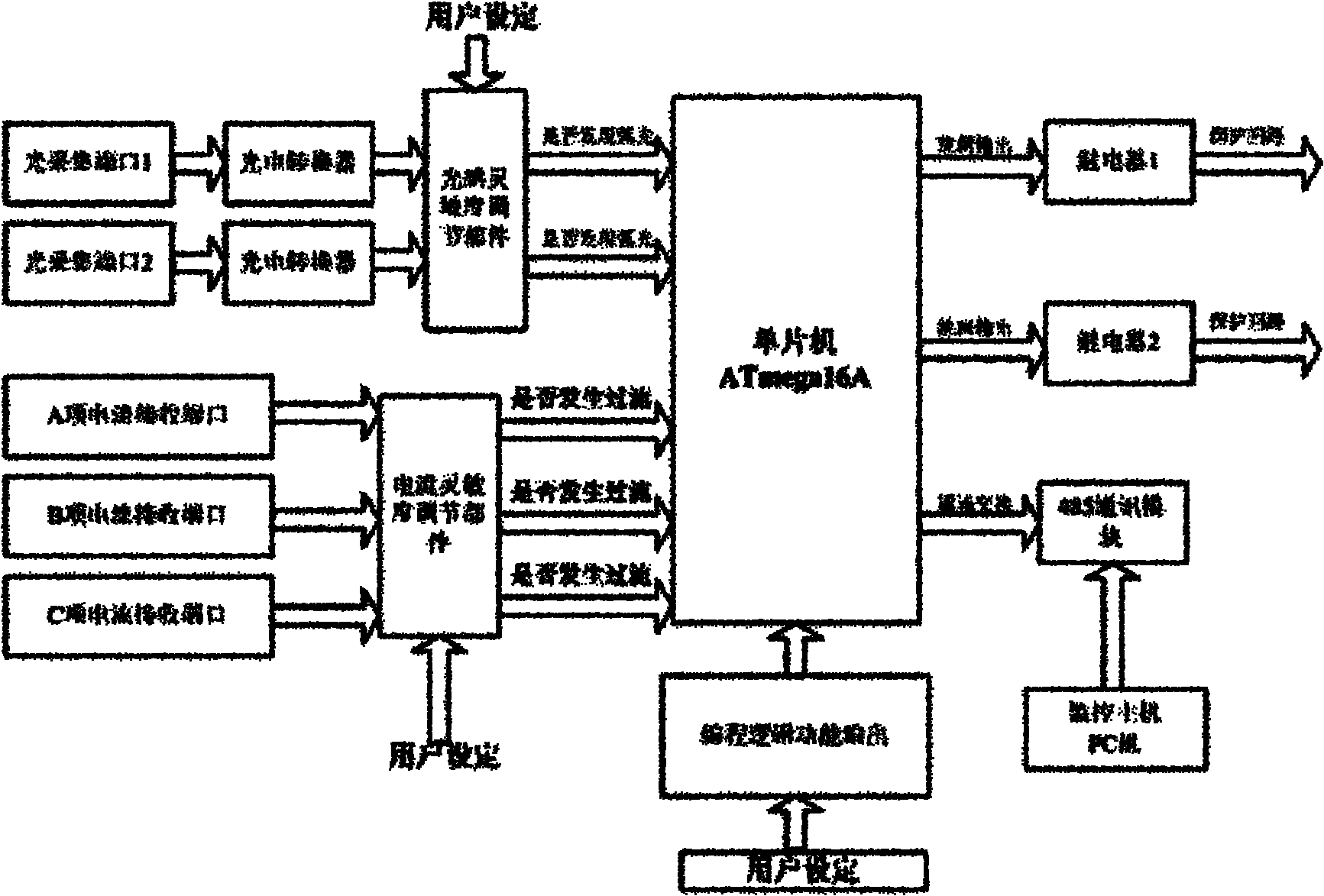
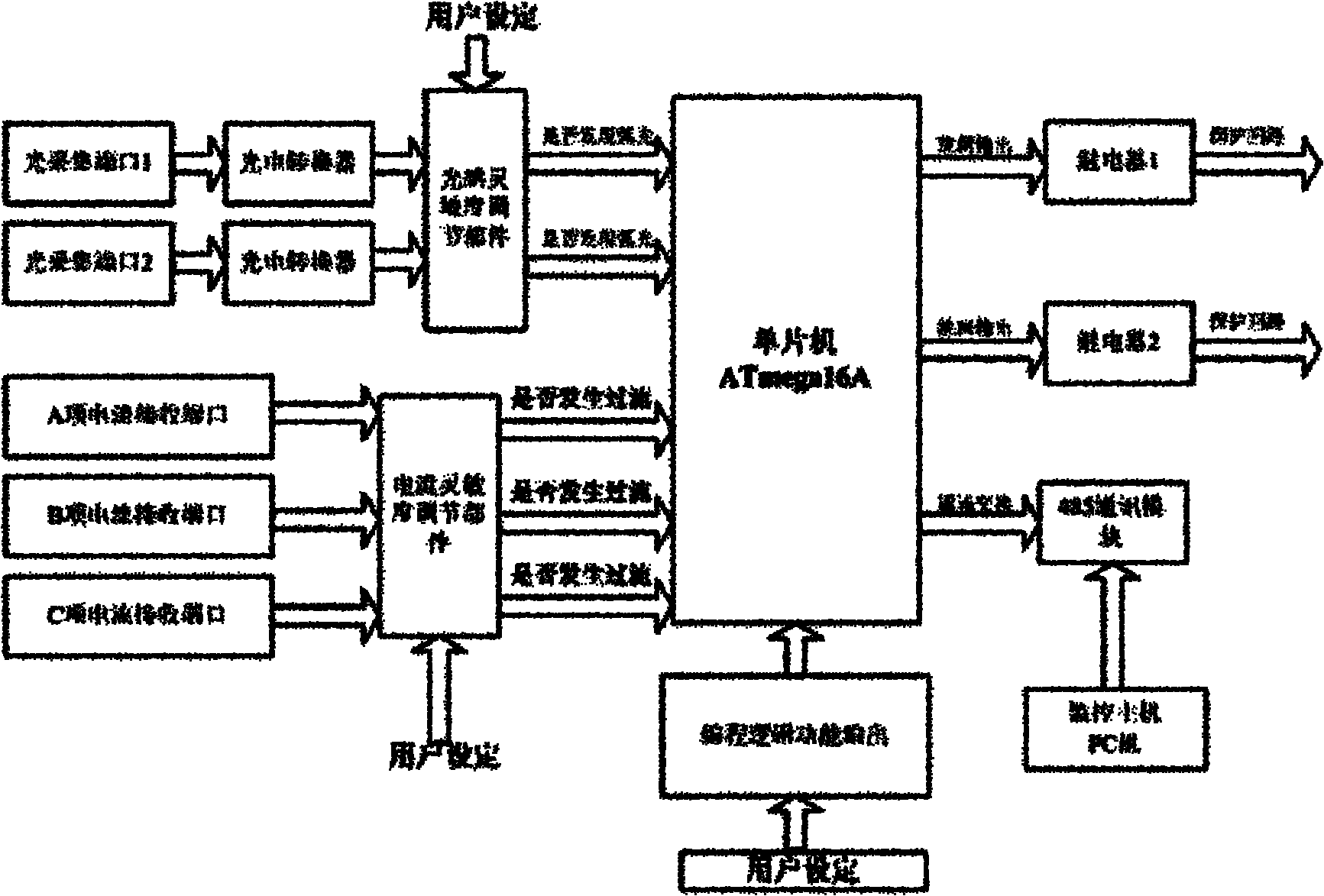
InactiveCN102025131AEnsure speedEnsure correctnessEmergency protective circuit arrangementsMicrocontrollerWide area
The invention discloses an arc light monitoring and protecting system, wherein two light collecting ports are connected with a photoelectric converter, the photoelectric converter is connected with a light sensitivity regulating part, the input is connected into a single-chip microcomputer ATmega16A, A, B and C current receiving ports are connected with a current sensitivity regulating part, the current sensitivity regulating part is connected with the single-chip microcomputer ATmega16A, the programmable logic function is inputted into the single-chip microcomputer ATmega16A, the output of the single-chip microcomputer ATmega16A is divided into two lines which are respectively connected with a relay, the output is connected into a protection loop, the single-chip microcomputer ATmega16A is connected with a 485 communication module, and the 485 communication module is connected into a power integrated automation system or a monitoring host after conversion. By utilizing the arc light monitoring and protecting system, the fast protection problem when arc light is generated due to short-circuit of a branch circuit of a feeder cabinet can be thoroughly solved, the short-circuit fault of the feed branch circuit of a substation can be avoided, the problem of wide-area burning of the substation can be avoided, and the speed at a trip outlet of the relay is controlled within 10 milliseconds.
Owner:TONGCHUAN POWER SUPPLY BUREAU +2
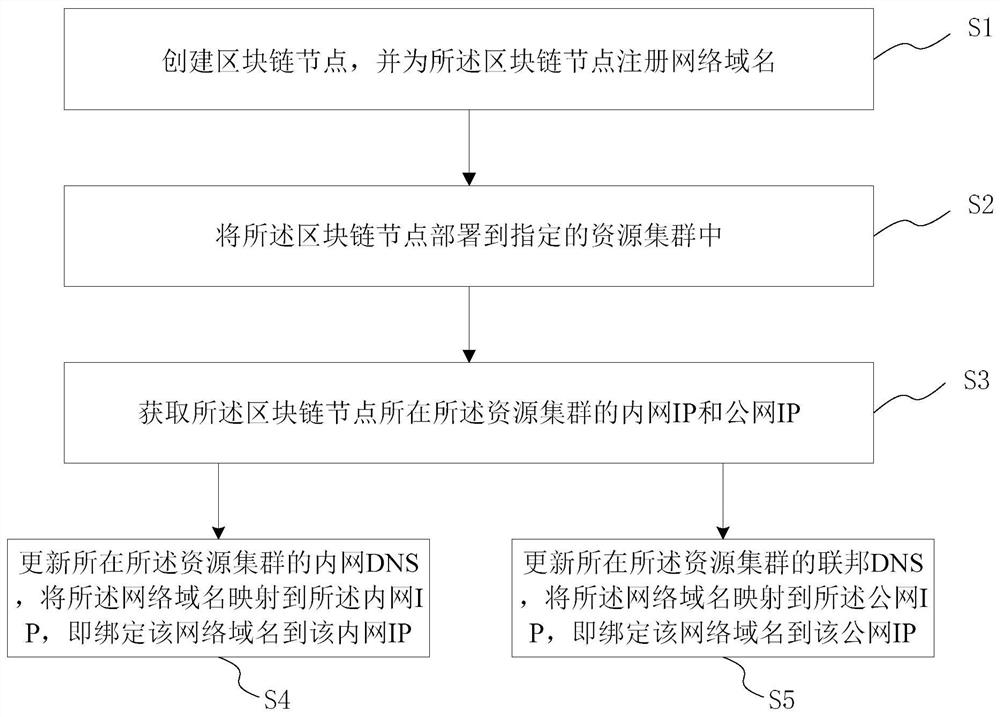
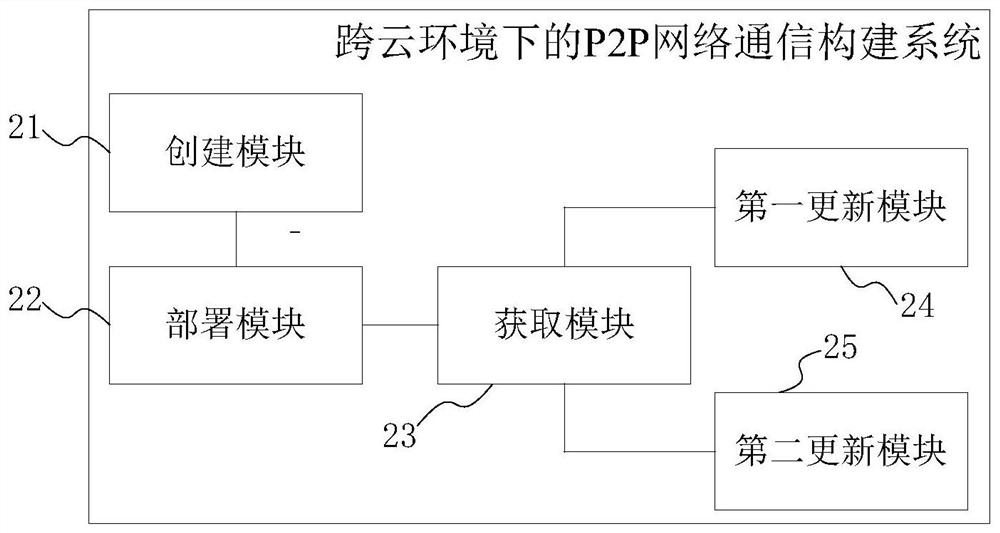
P2P network communication construction method and system in cross-cloud environment, medium and terminal
PendingCN111970337AEnsure efficiencyEnsure correctnessSecuring communicationDomain nameInternet traffic
The invention provides a P2P network communication construction method and system in a cross-cloud environment, a medium and a terminal. The method comprises the following steps: creating a blockchainnode, and registering a network domain name for the blockchain node; deploying the blockchain node into a specified resource cluster; obtaining an intranet IP and a public network IP of the resourcecluster where the blockchain node is located; updating an intranet DNS of the resource cluster, and mapping the network domain name to an intranet IP; updating the federation DNS of the resource cluster, and mapping the network domain name to the public network IP. According to the invention, an internal and external network IP heterogeneous environment is faced, a unified access mode can be formed, analyzing can be acheived as required according to a priority sequence from a bottom layer to an upper layer; P2P communication is performed by the network in a layer where a result can be analyzed, whether intranet communication or public network communication can be automatically selected according to the environment where the target node is located is achieved, it is ensured that network traffic can be sent in a reasonable link, and communication efficiency and correctness are ensured.
Owner:TIANYI ELECTRONICS COMMERCE
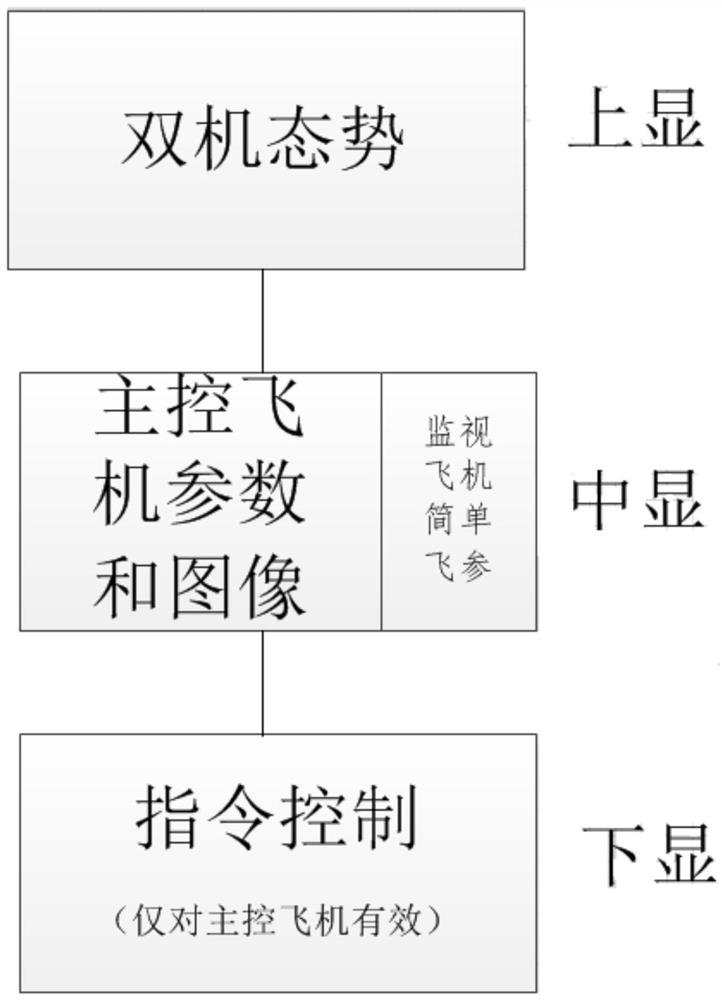
One-station-control double-machine display control method for unmanned aerial vehicle
ActiveCN112214030ARich display and control informationIntuitive display and control informationAlarmsTotal factory controlInformation controlCommand and control
The invention belongs to the field of unmanned aerial vehicle command and control, and particularly relates to a one-station-control double-machine display control method for an unmanned aerial vehicle. Two groups of flight monitoring seats and two groups of task monitoring seats are arranged. One group of flight monitoring seats and one group of task monitoring seats form a unit, and complete full-task command and control of one unmanned aerial vehicle respectively; and the two units cooperate together to complete full-task command and control of the two unmanned aerial vehicles. Each monitoring seat displays the dual-aircraft situation, the head-up display center area displays the parameters and images of the main control aircraft, the edge area displays the selected flight parameters ofthe other monitored aircraft, and the control instruction is only effective to the main control aircraft and supports the display and control of one station and two aircrafts. The situation information of the two aircrafts is presented differently; the parameters are matched with the visual scene, so that richer and more visual display and control information is provided for an operator; correctness and reliability of uplink remote control are ensured through cooperation of the control right and the machine number, and the display control of one-station-control double-machine is realized.
Owner:CHENGDU AIRCRAFT DESIGN INST OF AVIATION IND CORP OF CHINA
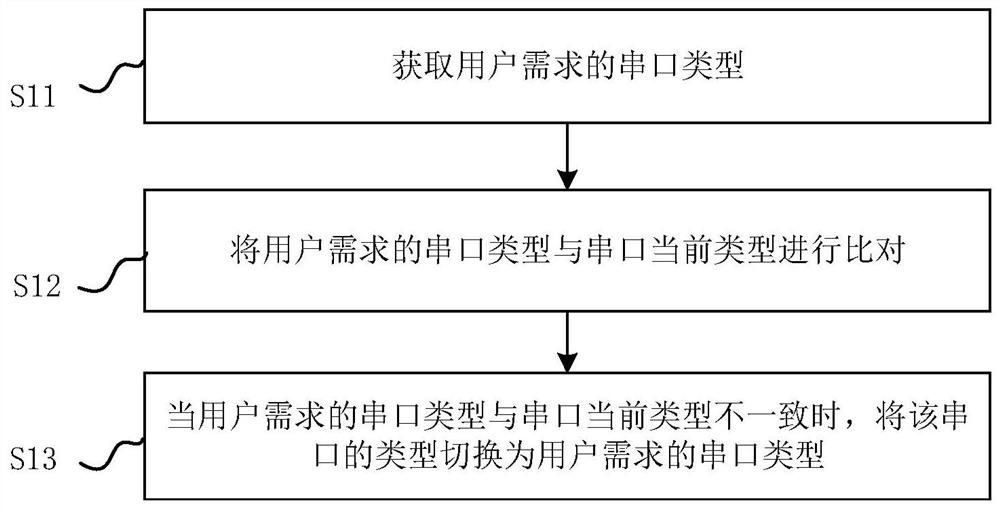
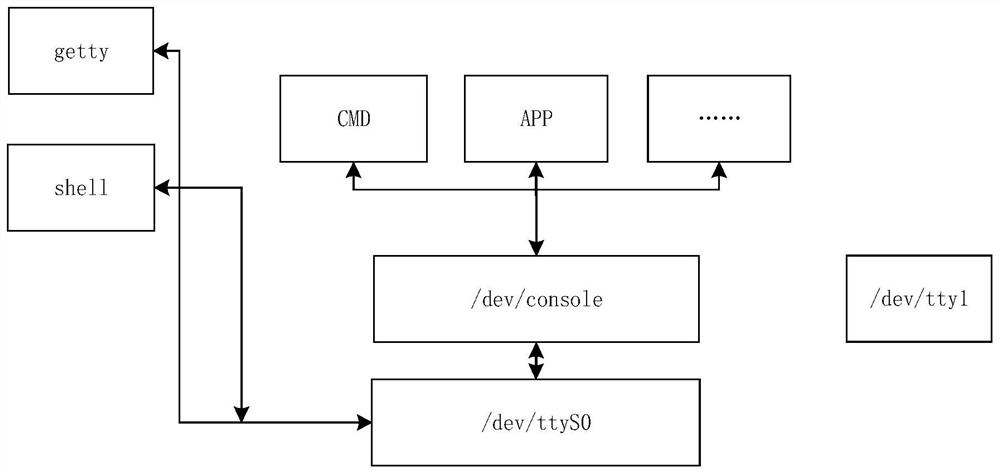
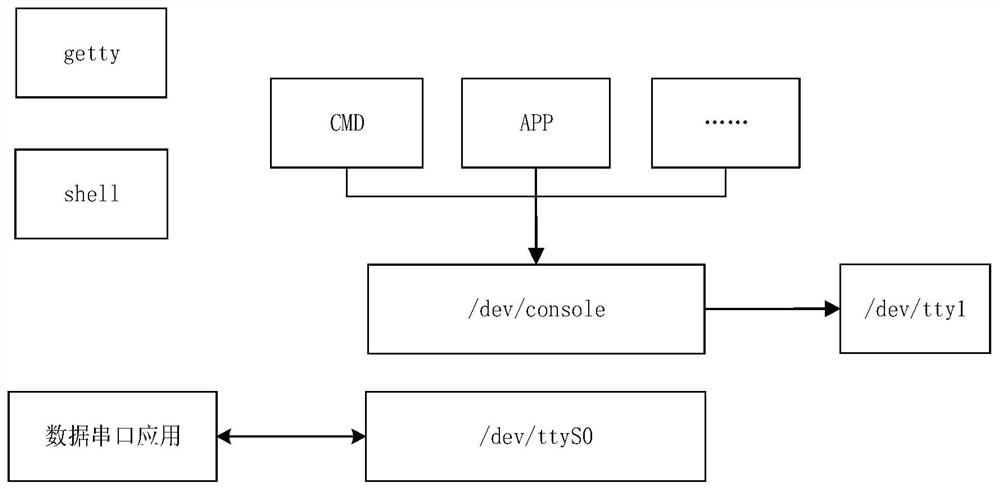
Debugging serial port and data serial port multiplexing method and device and controller
PendingCN112256513AEnsure integrityEnsure correctnessFaulty hardware testing methodsMultiplexingComputer architecture
The invention relates to a debugging serial port and data serial port multiplexing method and device and a controller. The debugging serial port and data serial port multiplexing method comprises thefollowing steps: acquiring a serial port type required by a user; comparing the serial port type required by the user with the current type of the serial port; and when the serial port type required by the user is inconsistent with the current type of the serial port, switching the type of the serial port into the serial port type required by the user. According to the invention, under the condition of serial port resource shortage in an embedded system, data serial port and debugging serial port function multiplexing can be realized on one hardware serial port device, i.e., the serial port can be seamlessly switched between the data serial port function and the debugging serial port function simply and quickly; and according to the method, the integrity and correctness of the data on theserial port can be ensured in the switching process of the data serial port function and the debugging serial port function.
Owner:成都菁蓉联创科技有限公司
Bluetooth based name card transmission method
InactiveCN103354497AAvoid wastingAvoid pollutionUser identity/authority verificationNear-field systems using receiversComputer hardwareBusiness card
The invention provides a Bluetooth based name card transmission method. The method comprises the steps of setting a Bluetooth name card format of a handheld device, encrypting the a Bluetooth name card, and delivering information to an object user, and carrying out decryption when the object user captures the information, thereby receiving original information of the Bluetooth name card sent by a sending party. The Bluetooth based name card transmission method provided by the invention avoids waste of resources and environmental pollution caused in the mass production process of traditional physical name cards, provides convenience for people to delivery electronic name cards, is simple to operate, and can ensure the accuracy and the safety of the content of electronic name cards.
Owner:HUAQIAO UNIVERSITY
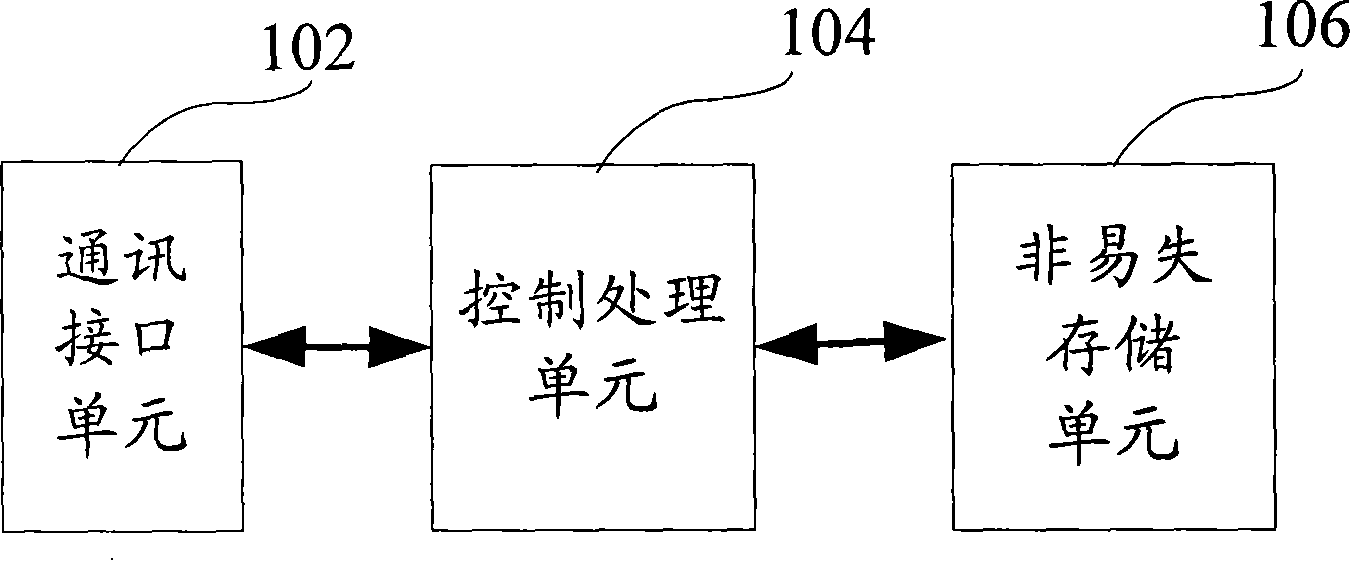
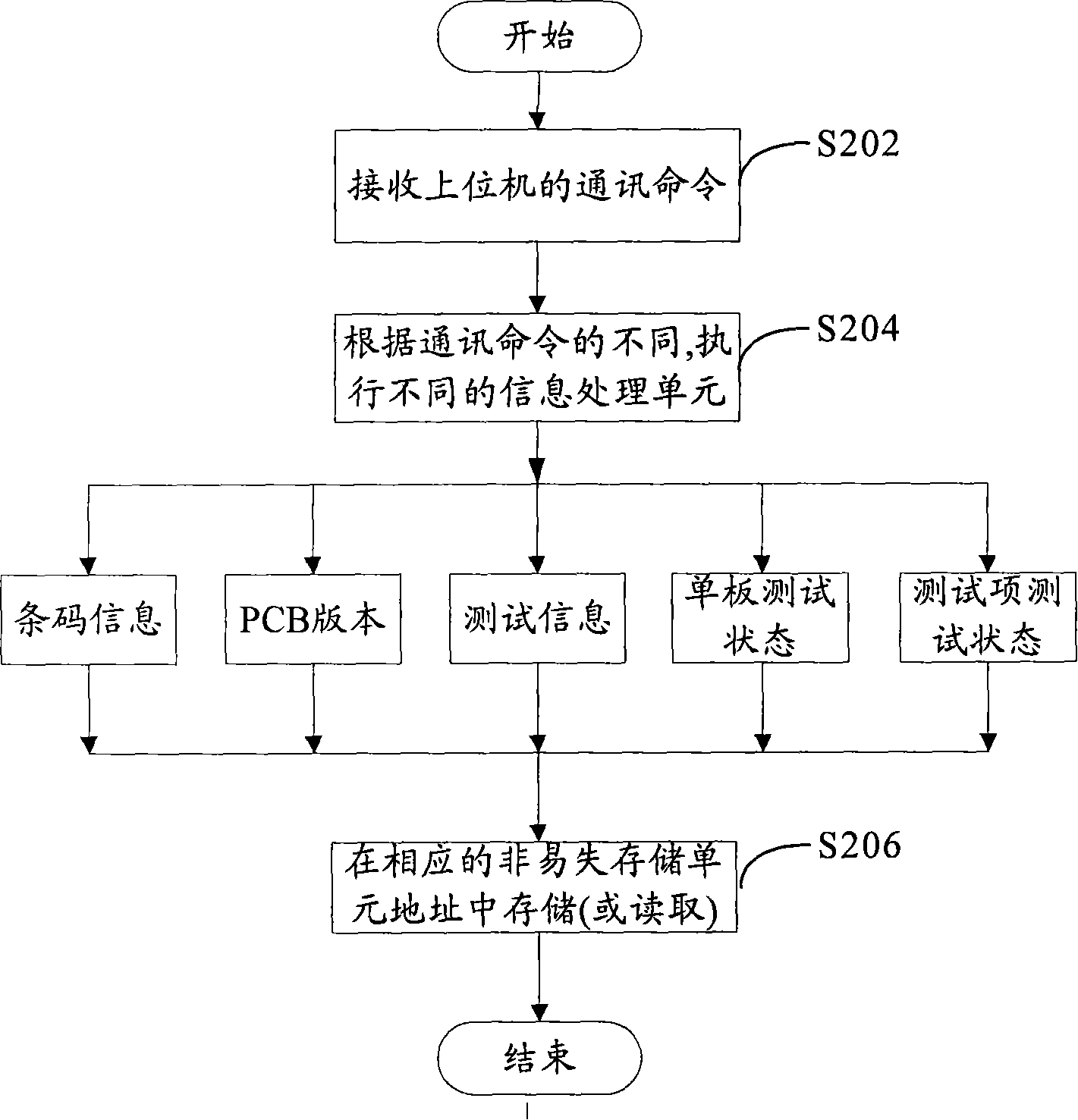
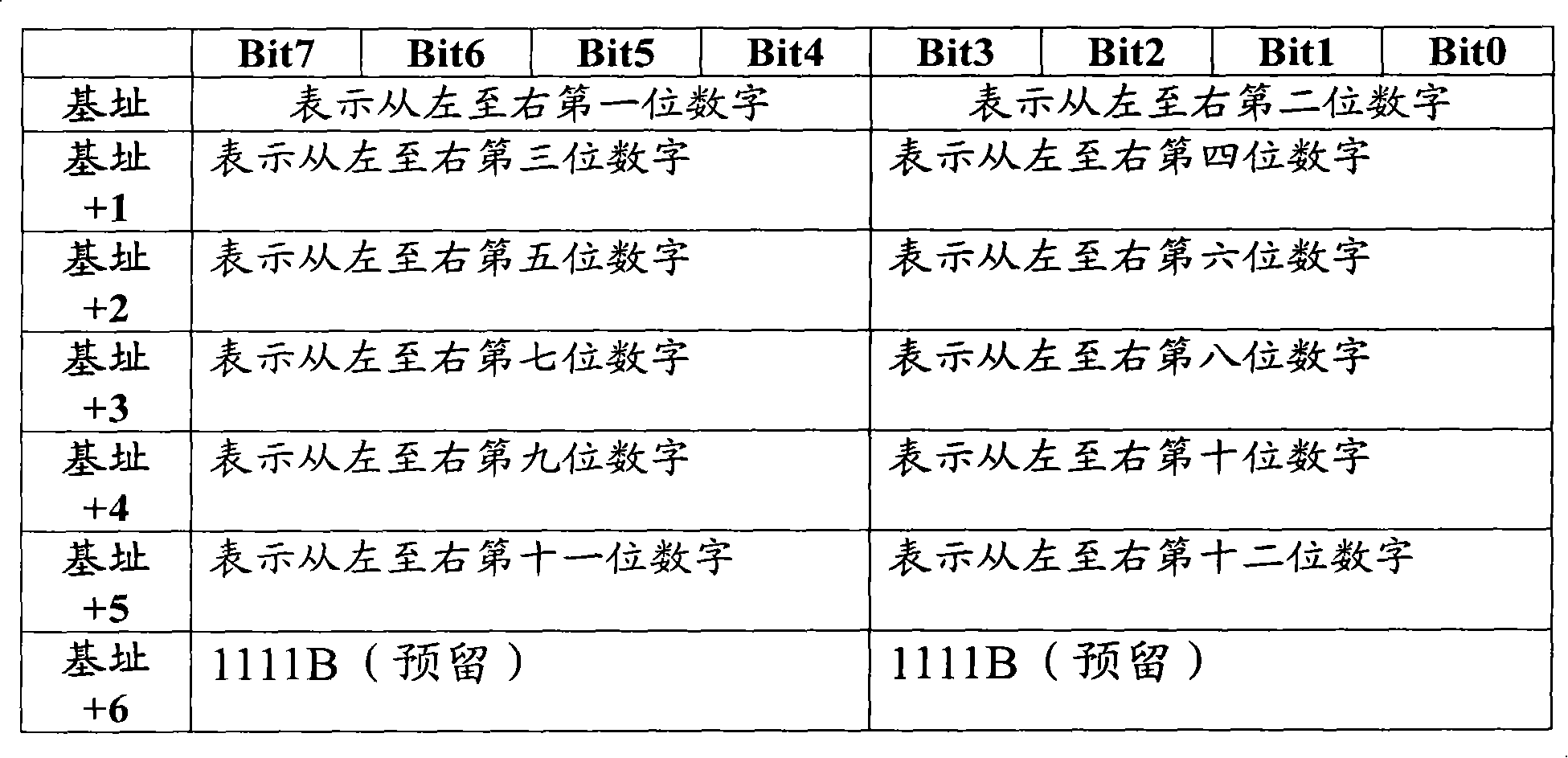
Storage device and method for single-board testing information
InactiveCN101193327AEnsure correctnessEnsure uniquenessElectronic circuit testingTransmission monitoringInformation analysisMonoboard
The invention provides a device for storing the veneer test information and a method thereof. The device comprises a nonvolatile storage unit used for storing the veneer test information from the veneer and ensuring the impossibility of the data loss when the power-down happens, a control processing unit used for providing the read-write function of the nonvolatile storage unit and the control function of a communication interface unit of a host computer and the communication interface unit used for realizing the transmission of the test information between the host computer and a lower computer. The advantages of the invention are in that: 1. the veneer test information can be stored in the veneer and the correctness and uniqueness of the test information are ensured. 2. the test information can be acquired conveniently and the acquisition mode is flexible. The test information can be reported to the host computer to carry out the query through the communication interface and also can be directly read to carry out the query through the veneer software. The invention is suitable under a plurality of conditions such as the production test management, single board repair, on-site equipment maintenance, etc. and is not restricted by the network and the database software. 3. the contents of the stored information are complete so as to be convenient for the information analysis.
Owner:ZTE CORP
Data synchronization method and device
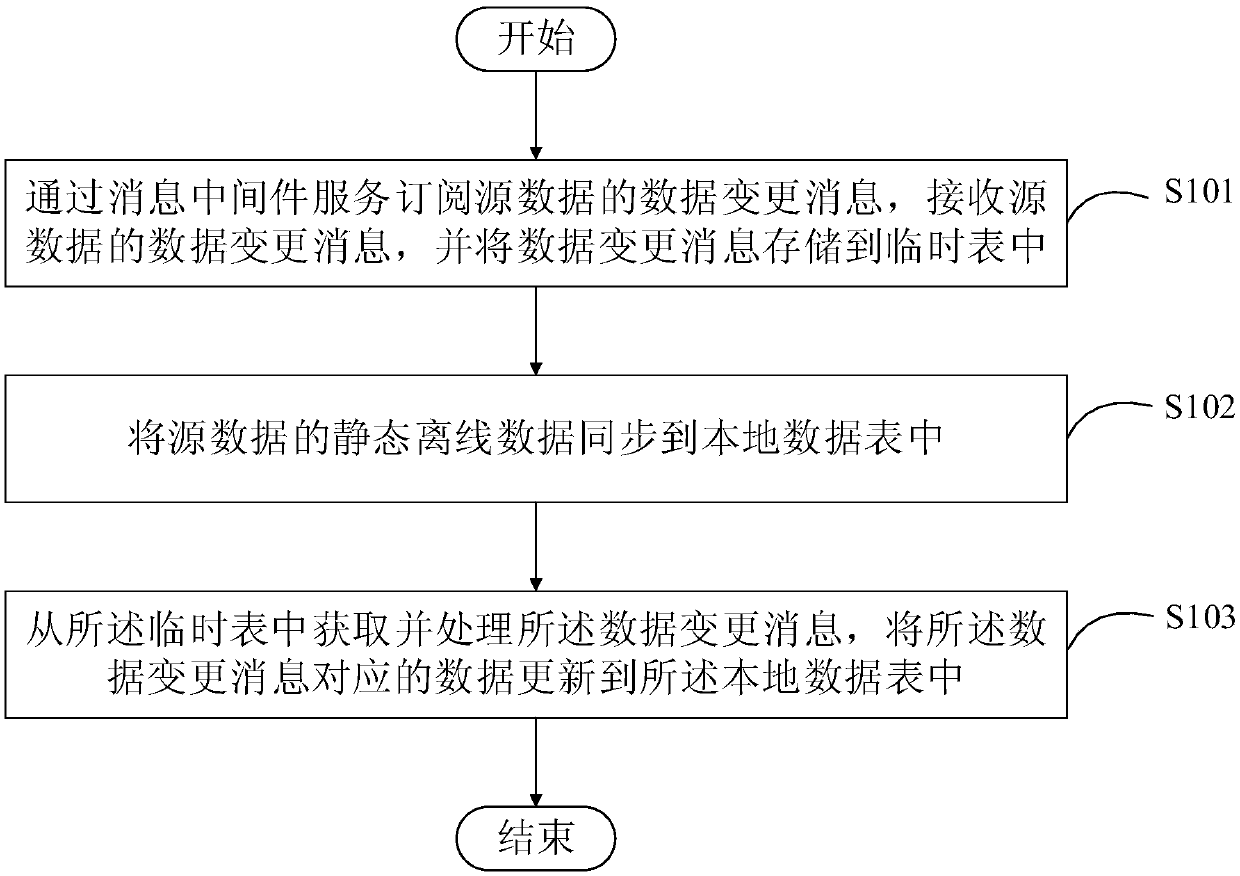
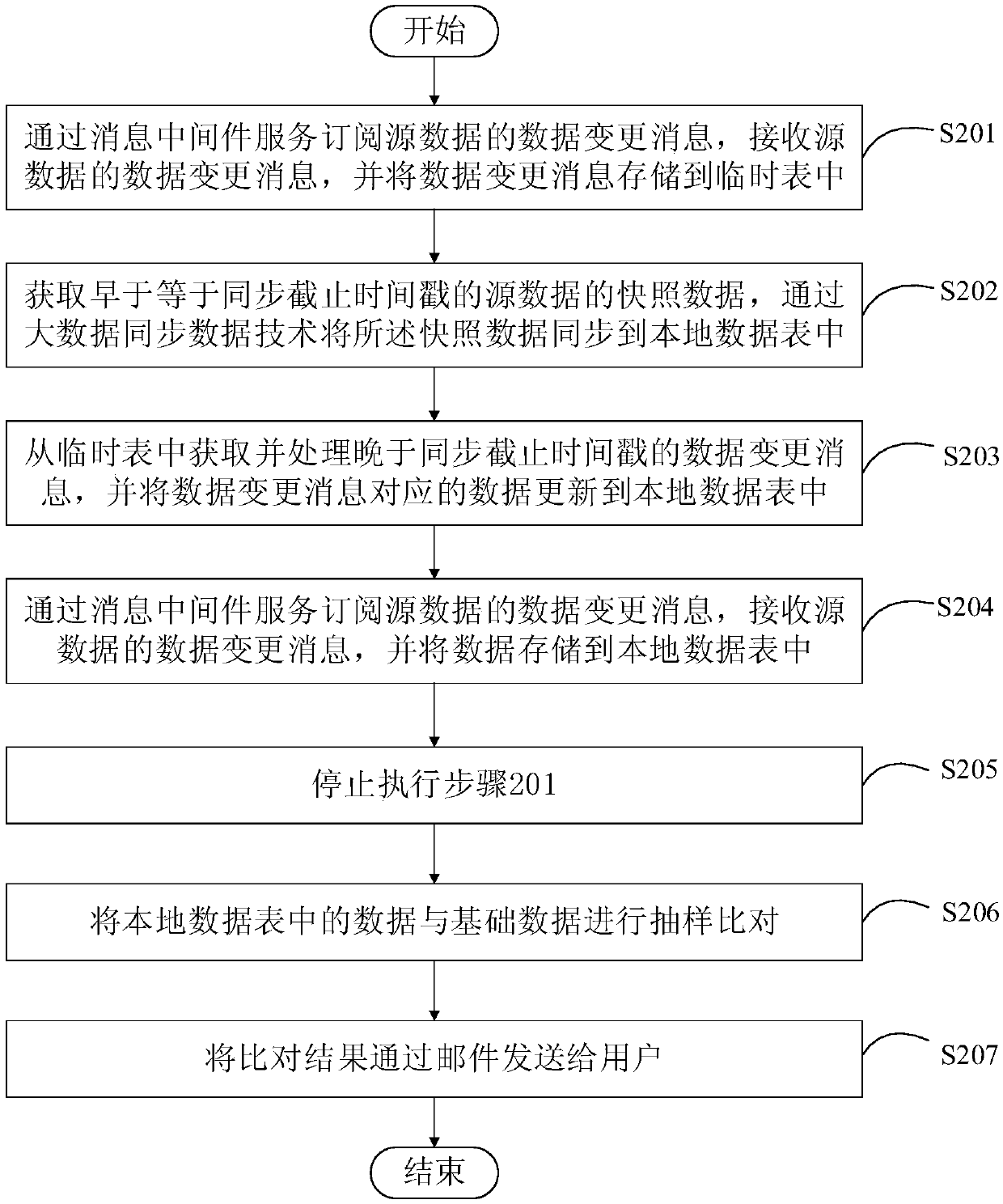
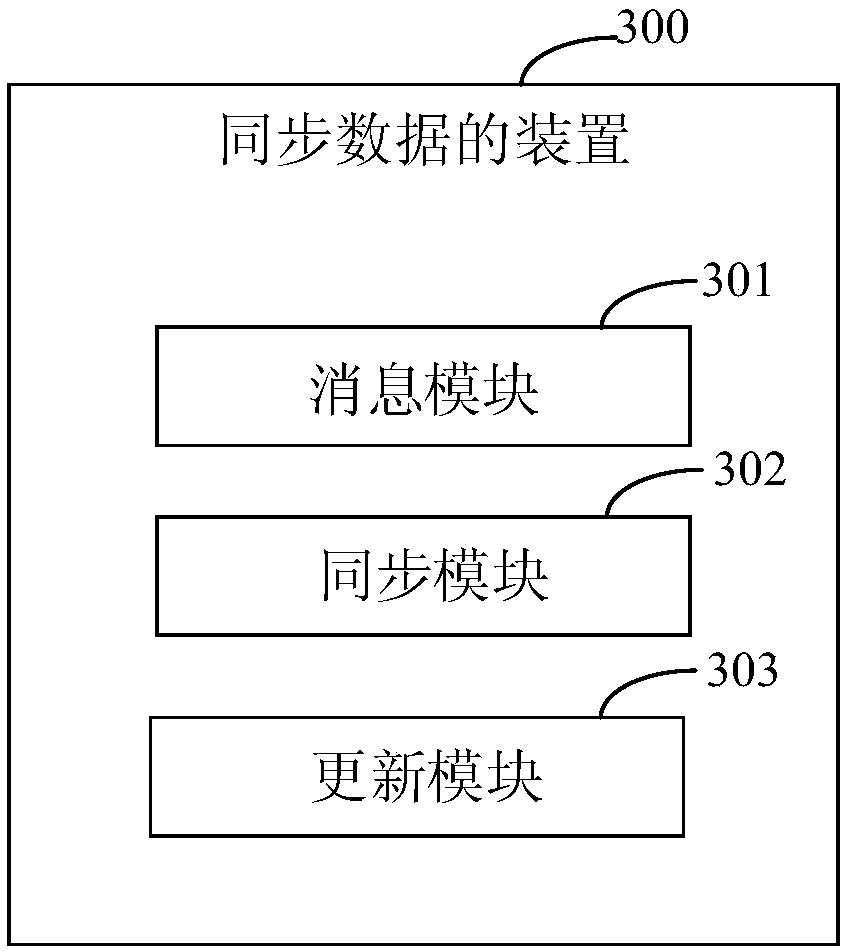
PendingCN110858197AMeet the performance problems of real-time processingSolve the lossDatabase updatingDatabase distribution/replicationData synchronizationDatasheet
The invention discloses a data synchronization method and device, and relates to the technical field of computers. One specific embodiment of the method comprises the following steps: serving a data change message of subscription source data through message middleware, receiving the data change message of the source data, and storing the data change message in a temporary table; synchronizing thestatic offline data of the source data to a local data table; and obtaining and processing the data change message from the temporary table, and updating data corresponding to the data change messageto the local data table. According to the embodiment, the problem that comparison resources are wasted can be solved.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
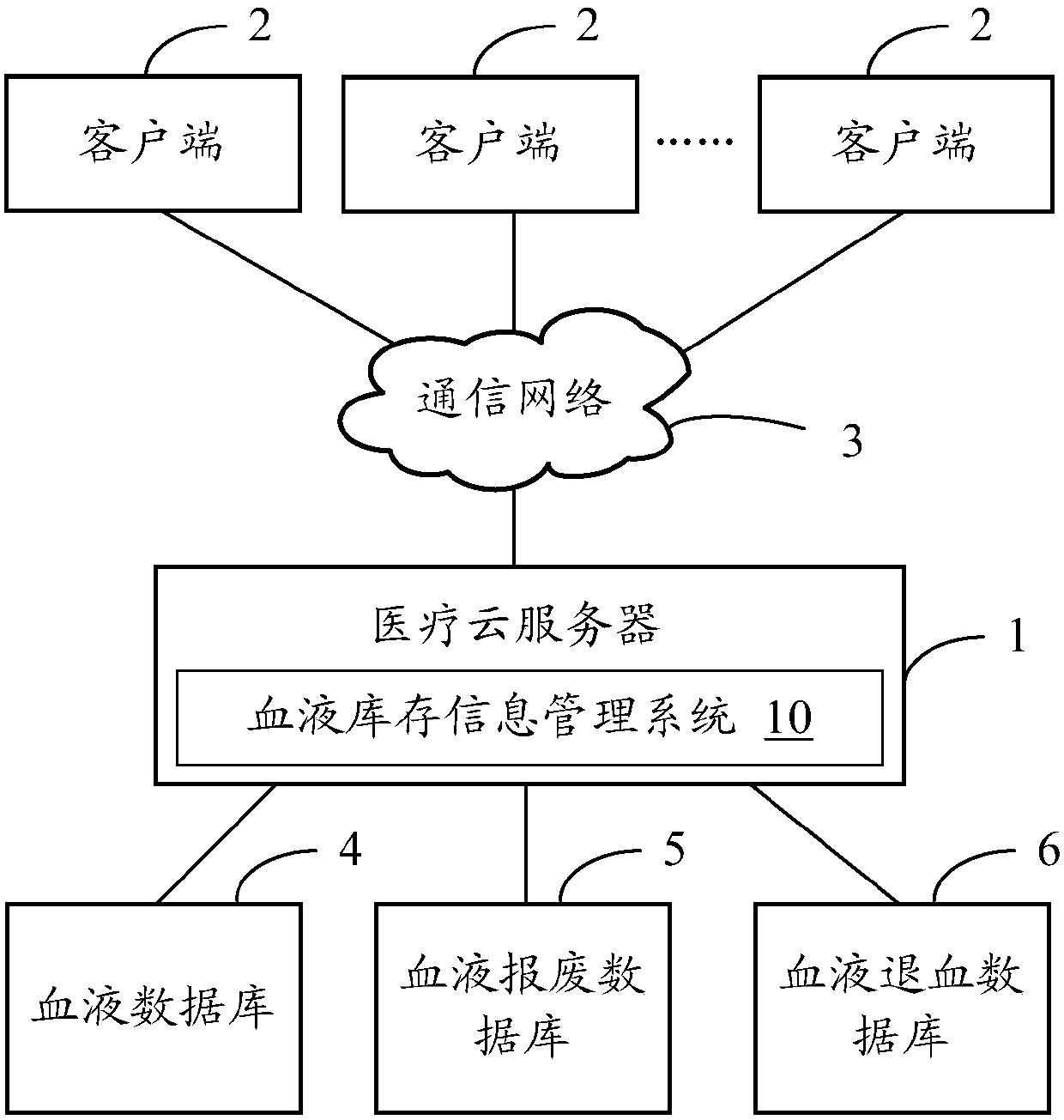
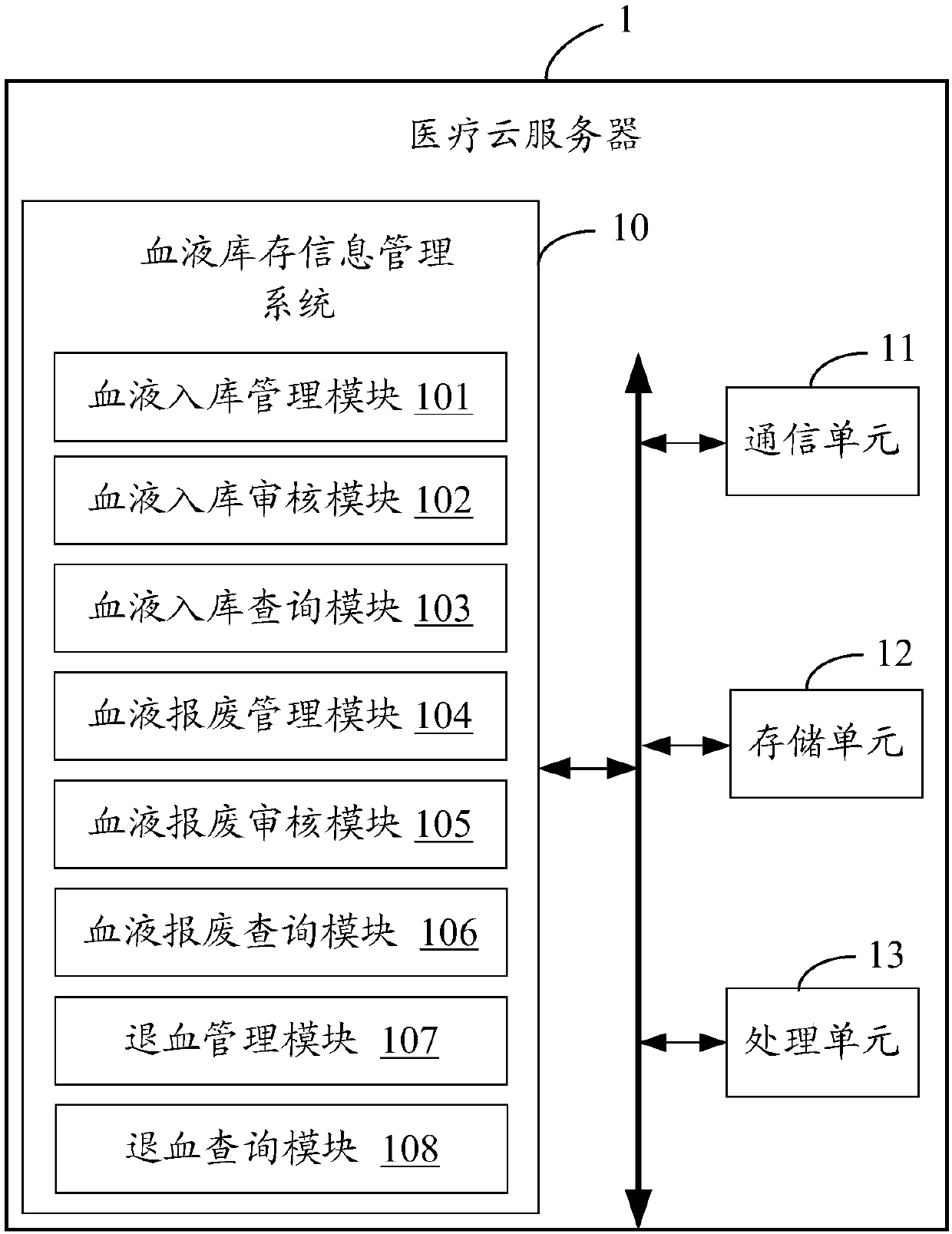
Blood inventory information management system
InactiveCN107622789AGuaranteed reasonablenessEnsure consistencyCo-operative working arrangementsHealthcare resources and facilitiesBlood managementInternal medicine
The invention provides a blood inventory information management system, which comprises a blood warehouse-in management module, a blood warehouse-in auditing module, a blood warehouse-in query module,a blood rejection management module, a blood rejection auditing module, a blood rejection query module, a blood return management module and a blood return query module. Thus, blood warehouse-in management, blood warehouse-in auditing, blood warehouse-in query, blood rejection management, blood rejection query, blood return management and blood return query can be realized, the blood inventory and the use condition are managed in all directions, effective blood management is facilitated, and the probability of blood accidents can be effectively reduced.
Owner:ANYCHECK INFORMATION TECH +1
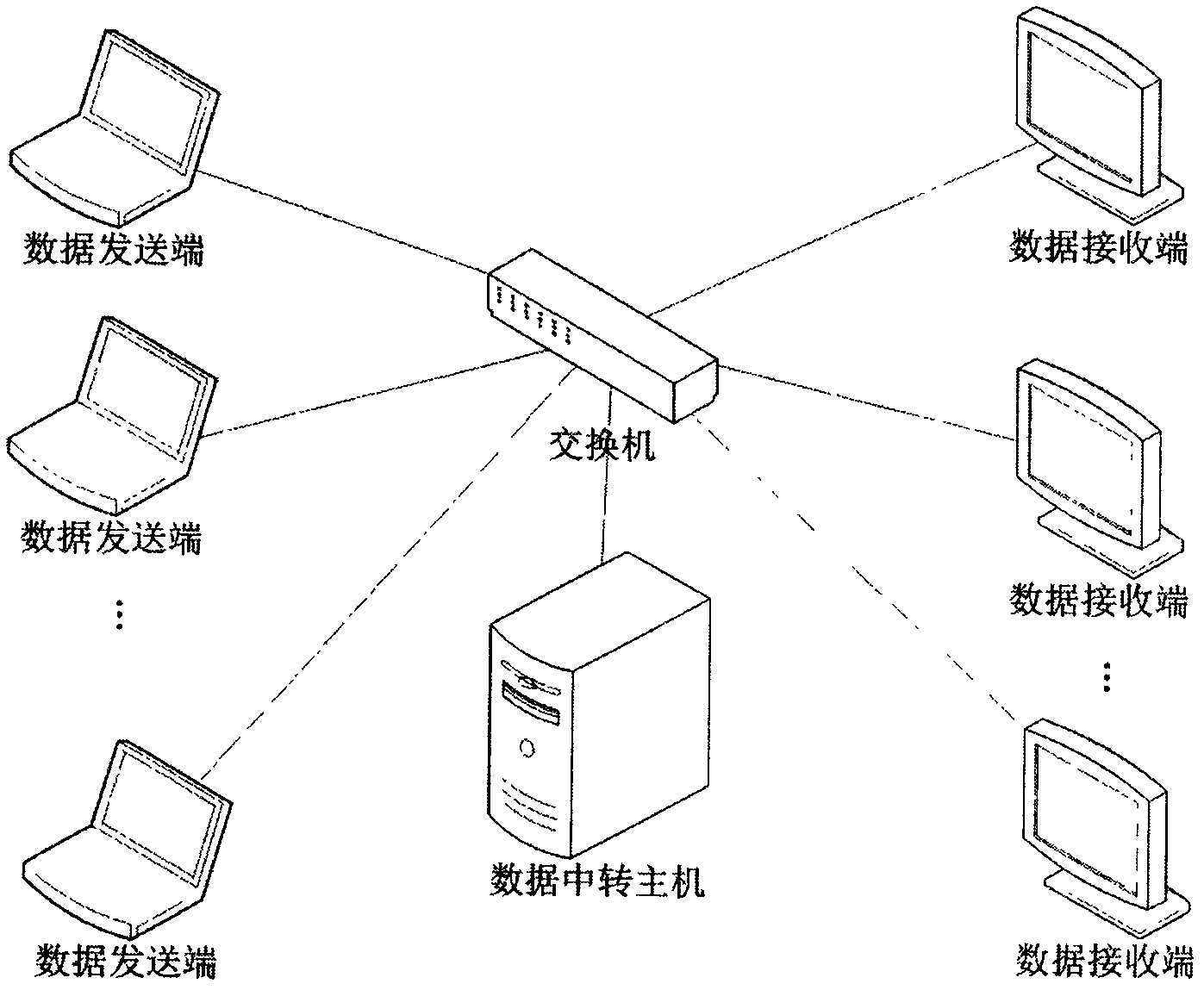
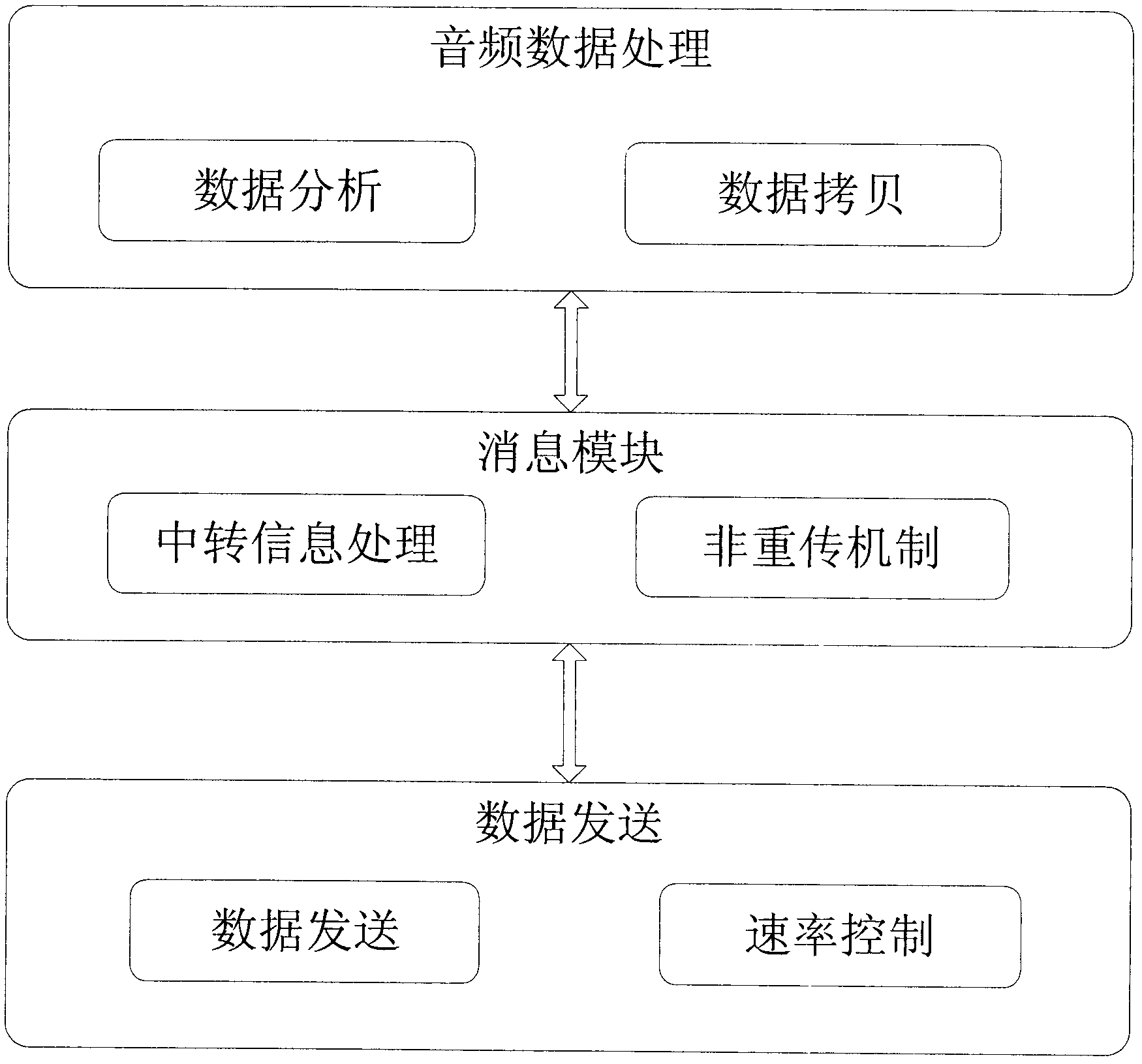
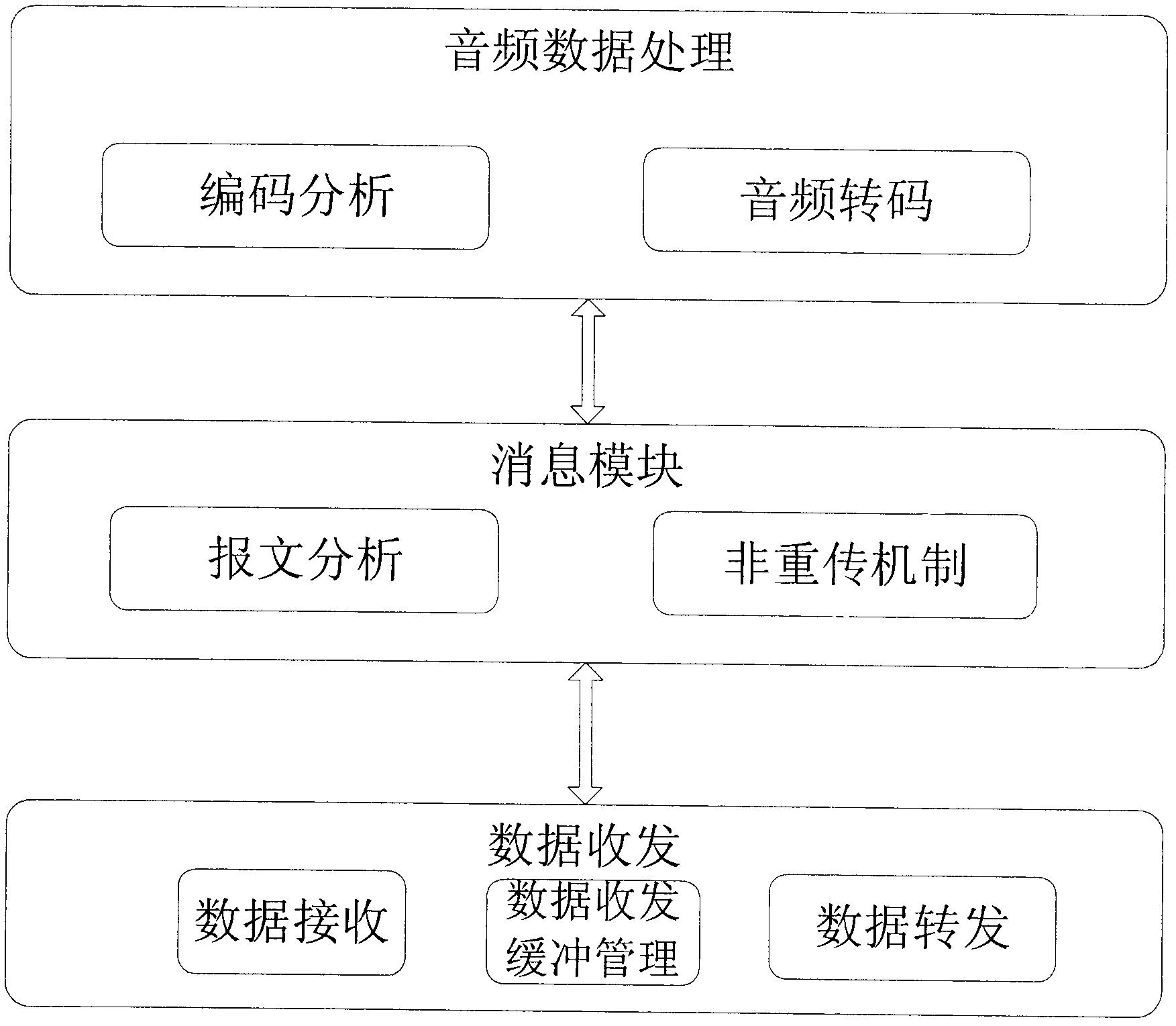
Soft real-time application-oriented verification system under multi-core virtualized environment
InactiveCN102075526AEnsure correctnessEnsure effectivenessData switching networksSoftware simulation/interpretation/emulationVirtualizationVerification system
The invention relates to a soft real-time application-oriented verification system under multi-core virtualized environment, which consists of a data receiving terminal, a data transfer host and a data sending terminal, wherein the data sending terminal consists of an audio data processing module, a message module and a data sending module; the data transfer host consists of a voice data processing module, a message module and a data transceiving module; the data receiving terminal consists of a data receiving module and an audio data processing module; and audio data is sent by the data sending terminal, is subjected to voice format conversion and forwarding at the data transfer host, and is received and stored finally by the data receiving terminal. In the system, the data transfer hostis in the multi-core virtualized environment, and the processing operation of the data transfer host meets the characteristic of soft real-time application, so the running characteristic of the soft real-time application under the multi-core virtualized environment is verified.
Owner:BEIHANG UNIV
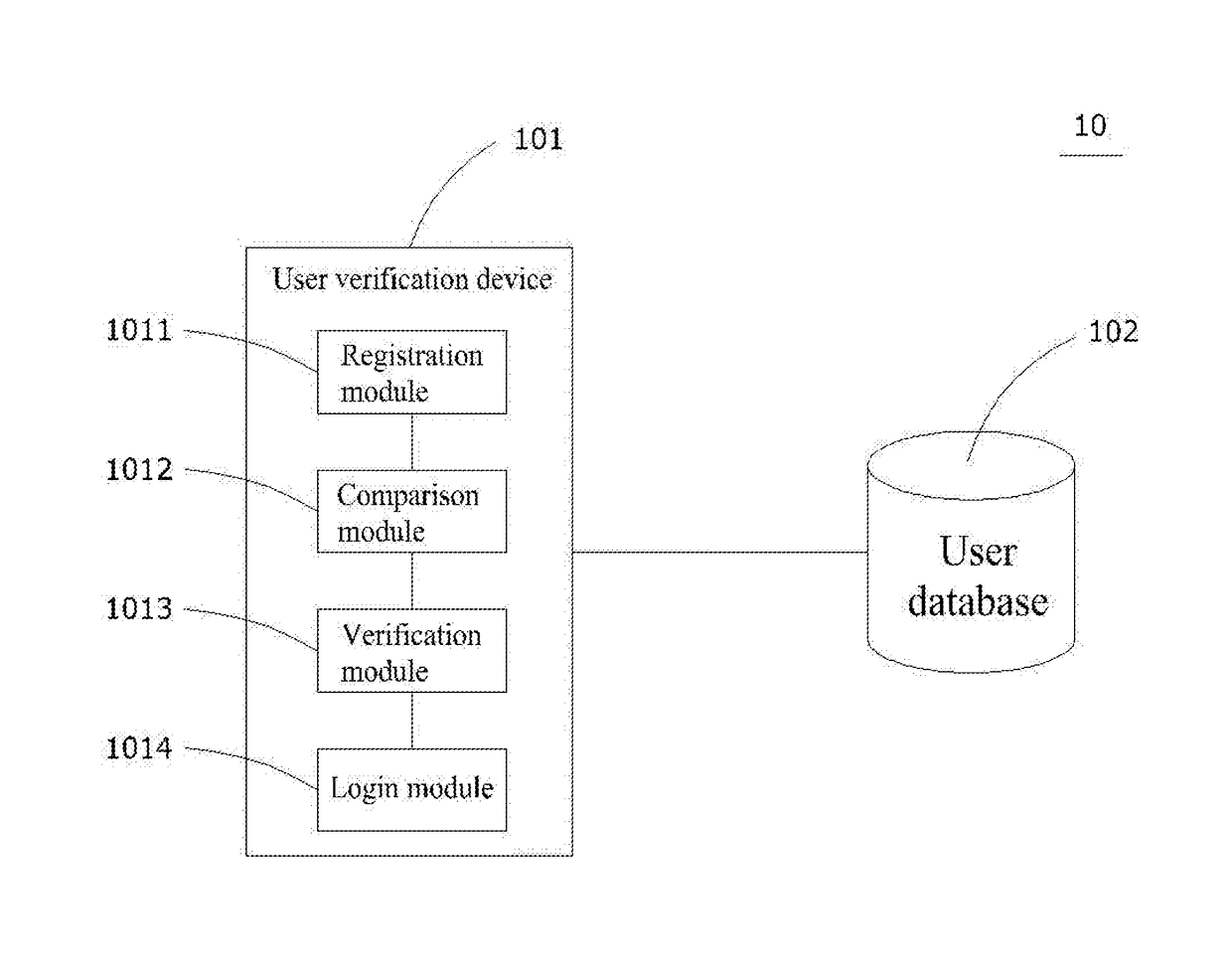
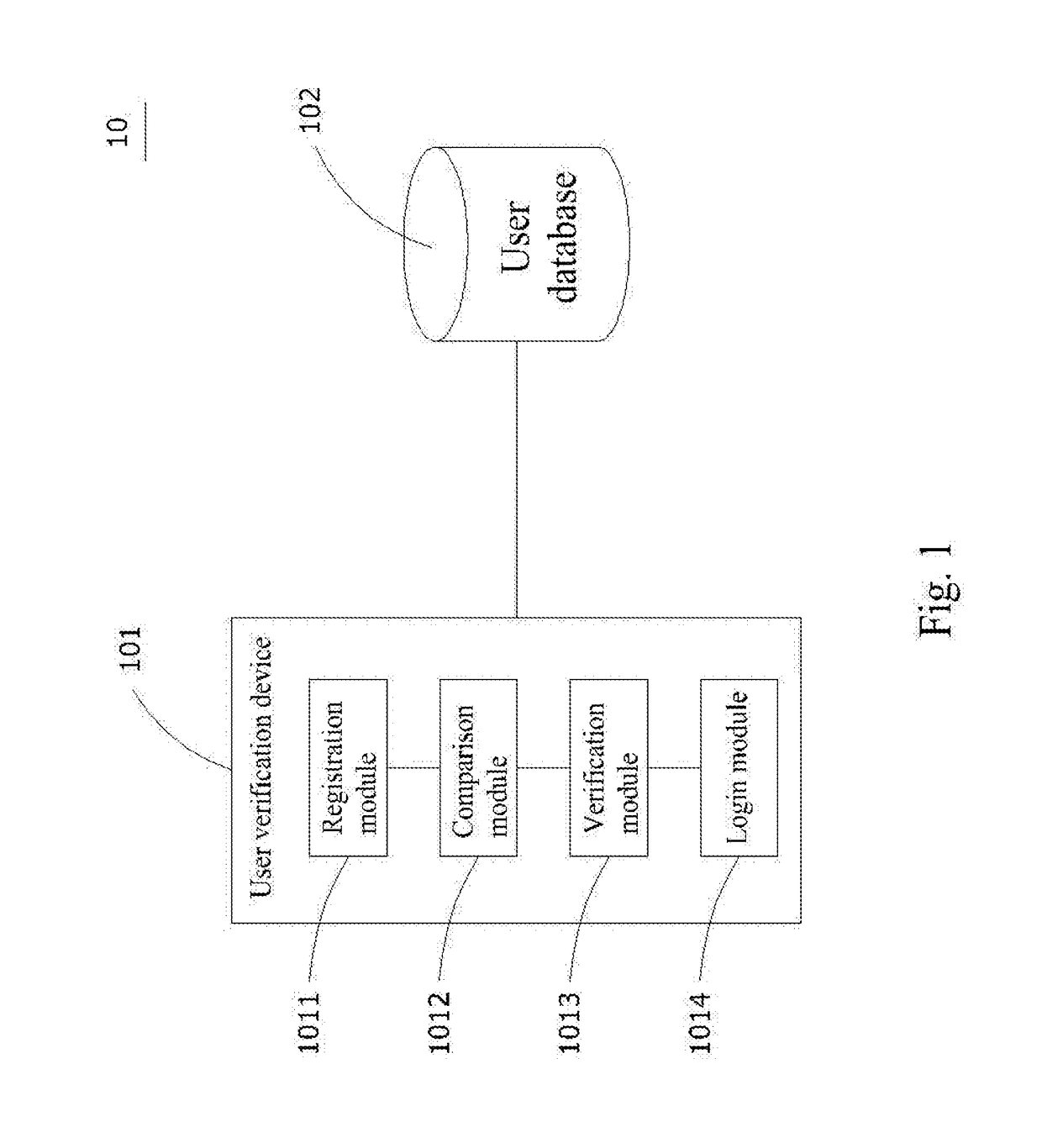
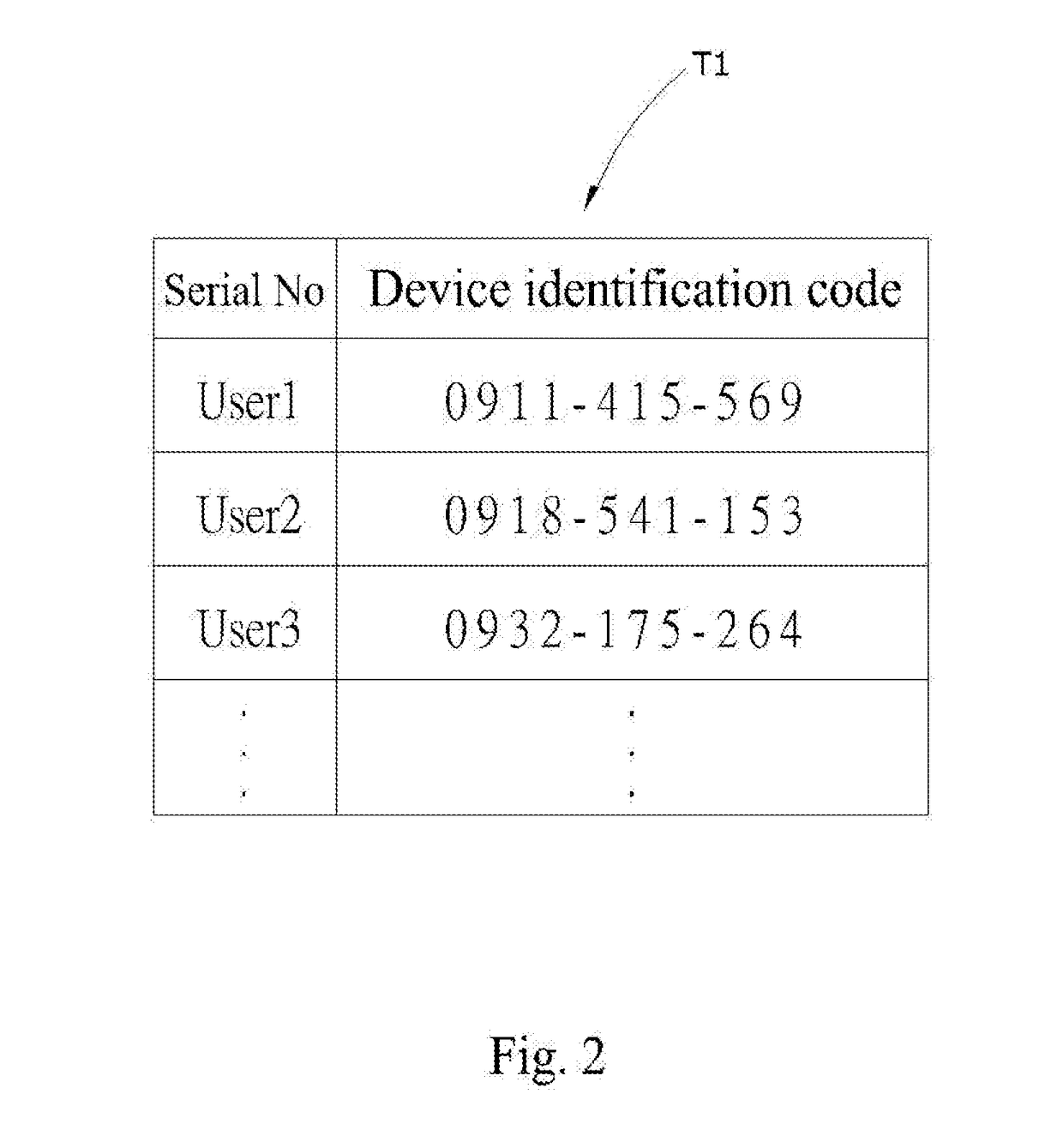
User verification system and its implementing method
ActiveUS20170078882A1Ensure correctnessEnsure validitySecurity arrangementSecuring communicationUser verificationMobile device
The invention discloses a user verification system and its implementing method. When a mobile device connects to a registration module of the user verification device to execute registration procedure, the unregistered identification code of mobile device will be sent to the user verification device. Then, a comparison module will search and verify the unregistered identification code in the user database. If there is no matching identification codes, the registration procedure would be completed, on the contrary, a verification module will send the verification massage to mobile devices that have the same identification code. Someone who responses the verification message would proceed to execute registration and login procedures. Therefore, the invention could prevent users from being annoyed with the complex verification procedure and reduce the cost of sending verification messages.
Owner:USA CANAL SOFTWARE CO LTD
Two-party collaborative signature method based on SM2 algorithm for resisting energy analysis attack
ActiveCN112422288ADefense against analytics attacksEnsure correctnessKey distribution for secure communicationPublic key for secure communicationAlgorithmPassword
The invention belongs to the technical field of passwords, and particularly relates to a two-party collaborative signature method based on an SM2 algorithm for resisting an energy analysis attack. Themethod comprises the following steps: 1) initializing signature parameters; 2) the two communication parties generate a sub-key and a user public key; 3) generating a collaborative signature. Two cooperative parties and a user agree with public parameters used in a cooperative signature process; the two cooperative parties generate and store SM2 sub-keys and collaborate to generate a user publickey; the two cooperative parties cooperate to complete message signature; any party cannot obtain the sub-private key of the opposite party, so that the security of the SM2 signature private key is improved. Compared with an existing collaborative signature scheme based on an SM2 algorithm, the invention has the advantages that 1) verification of signature parameters, a user public key and a signature result is added, and the effectiveness of collaborative signature is ensured; and 2) the generated collaborative signature result can effectively resist an energy analysis attack.
Owner:UNIVERSITY OF CHINESE ACADEMY OF SCIENCES
Multi-constellation GNSS fusion high-precision dynamic positioning method under complex environmental conditions
ActiveCN109116392AQuick selectionFast realization of high-precision dynamic positioningSatellite radio beaconingDecompositionSimulation
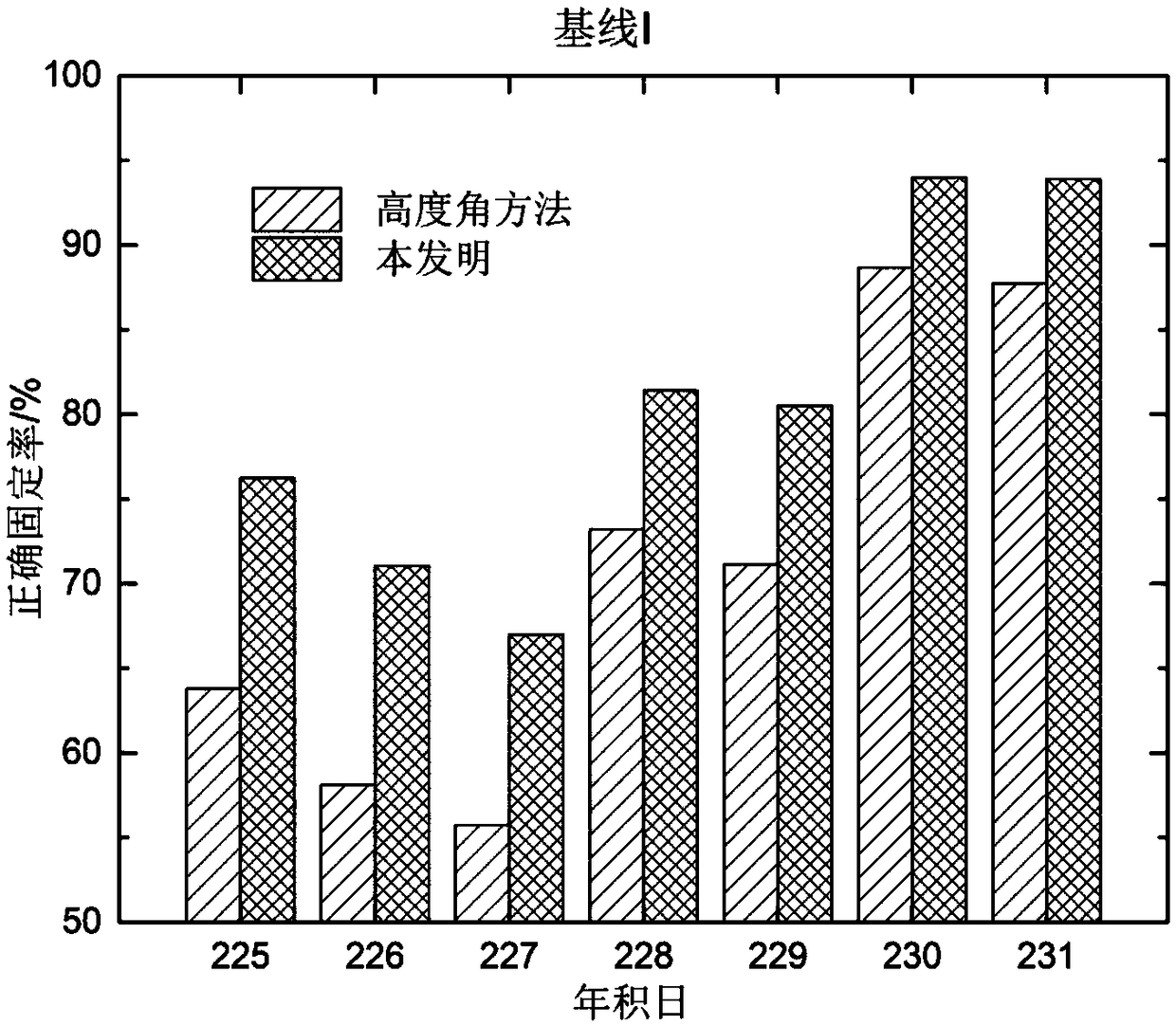
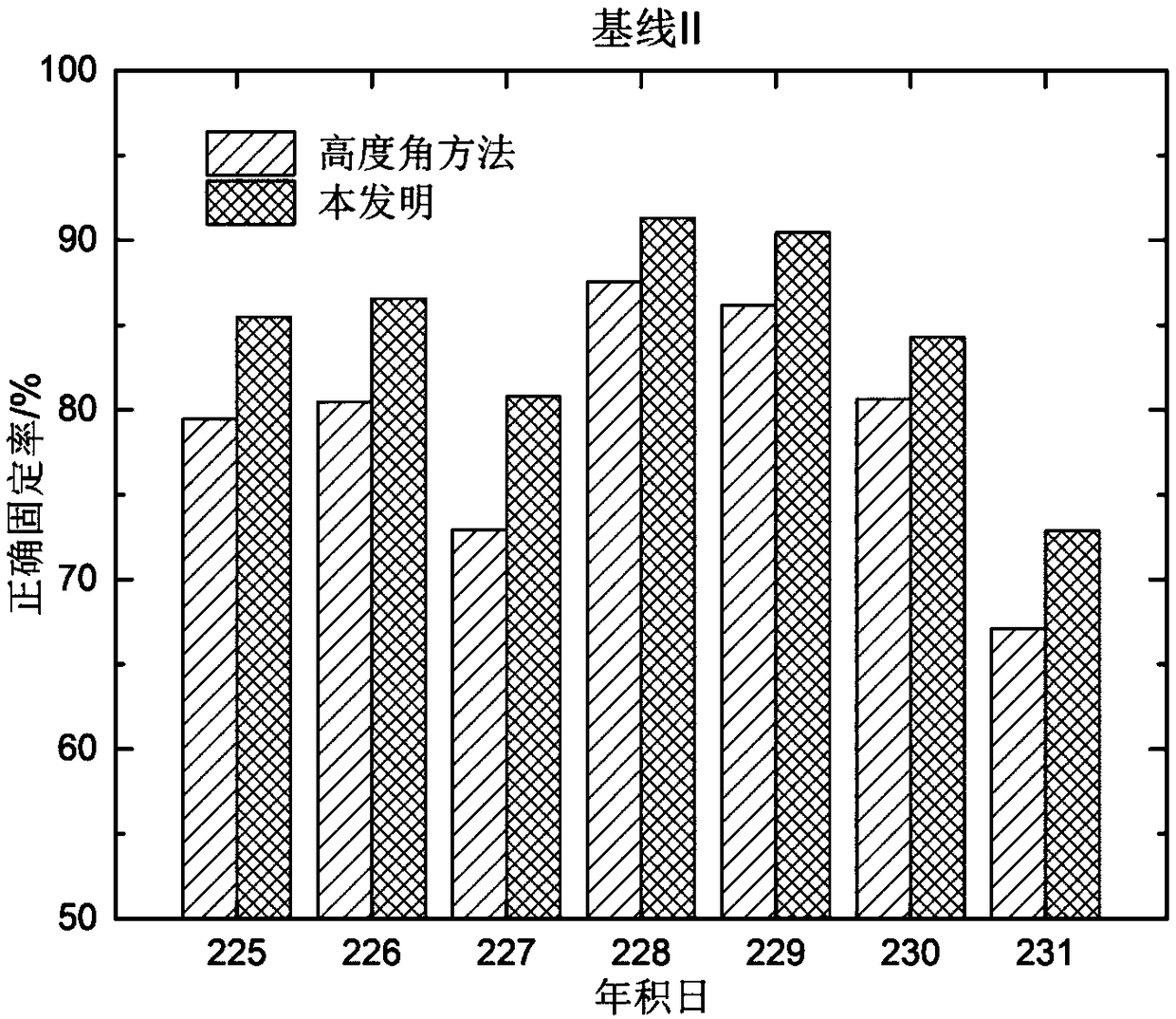
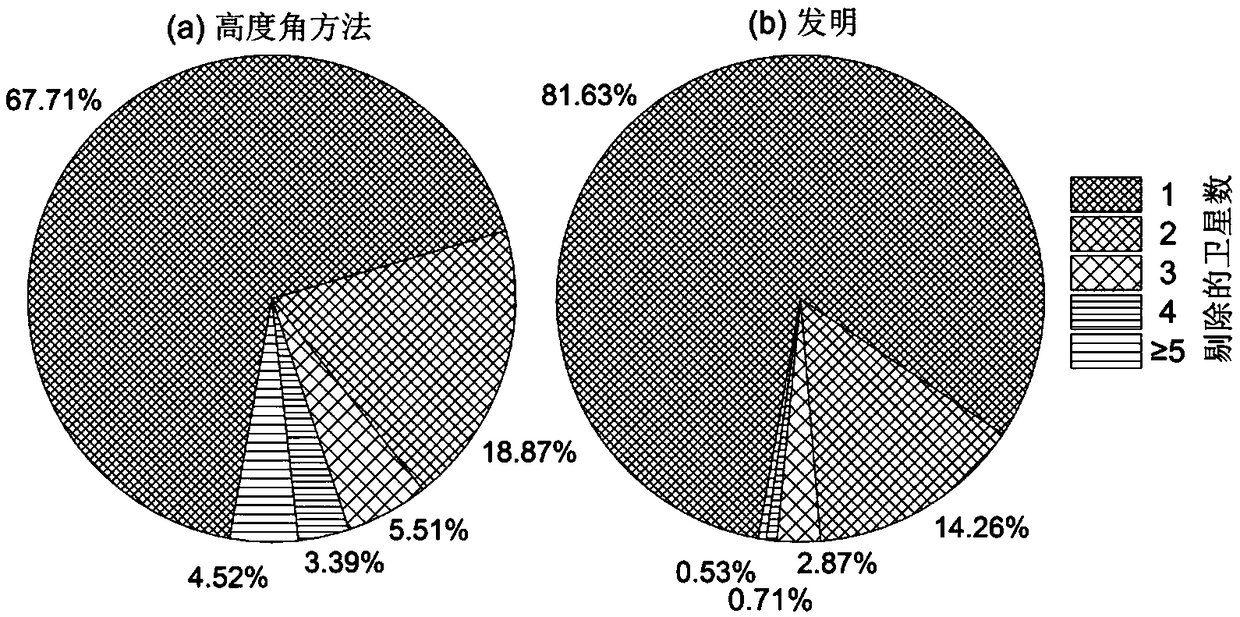
The invention discloses a multi-constellation GNSS fusion high-precision dynamic positioning method under complex environmental conditions. The method comprises the following steps of step1, acquiringa floating point ambiguity solution set b<^> and a variance-covariance matrix Qb<^>, decomposing the b<^> and the Qb<^> and acquiring a whole cycle ambiguity value, if the whole cycle ambiguity valuesatisfies a setting requirement, entering into a step4, otherwise, entering into a step2; step2, removing the ambiguity of an ith satellite from the b<^>, then carrying out ambiguity decomposition, and acquiring the distance sni between a Ratio value ratioi and a floating point ambiguity, and an optimal whole cycle ambiguity; step3, grouping the ratioi and the sni according to a setting thresholdvalue, and then determining an optimal ambiguity subset, and according to the optimal ambiguity subset, carrying out whole cycle ambiguity calculation and acquiring a whole cycle ambiguity value; andstep4, according to the whole cycle ambiguity value, carrying out GNSS fixed solution calculation, and acquiring a GNSS dynamic positioning result. In the invention, the influence of the floating point ambiguity with a large deviation on ambiguity decomposition can be effectively avoided, the ambiguity can be rapidly fixed, and the correctness and the reliability of a GNSS positioning result areensured.
Owner:SOUTHWEST JIAOTONG UNIV
Load shedding method and system for safety automatic device based GOOSE information
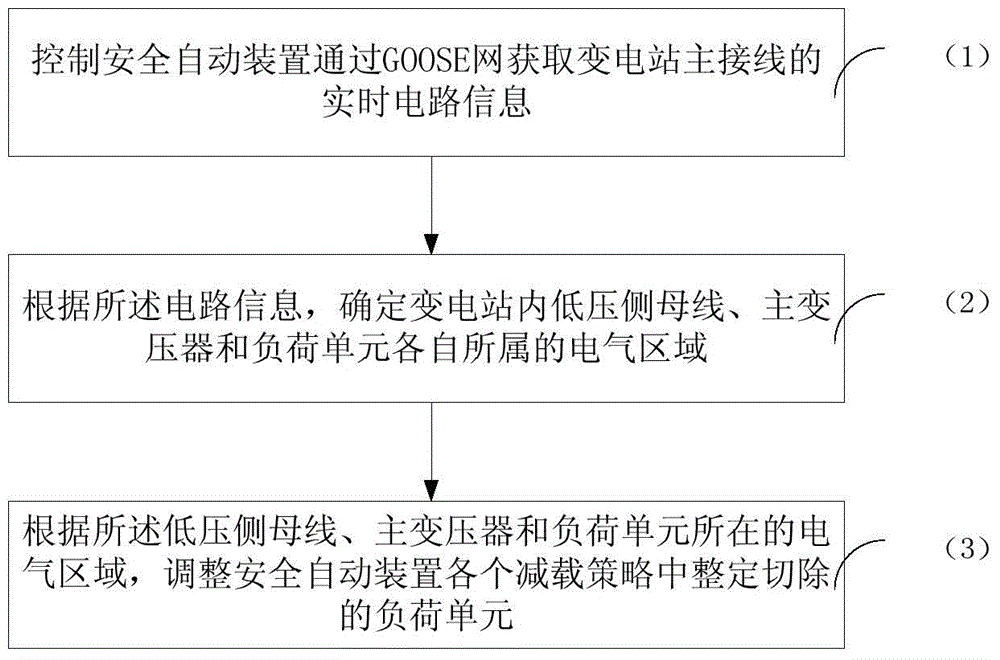
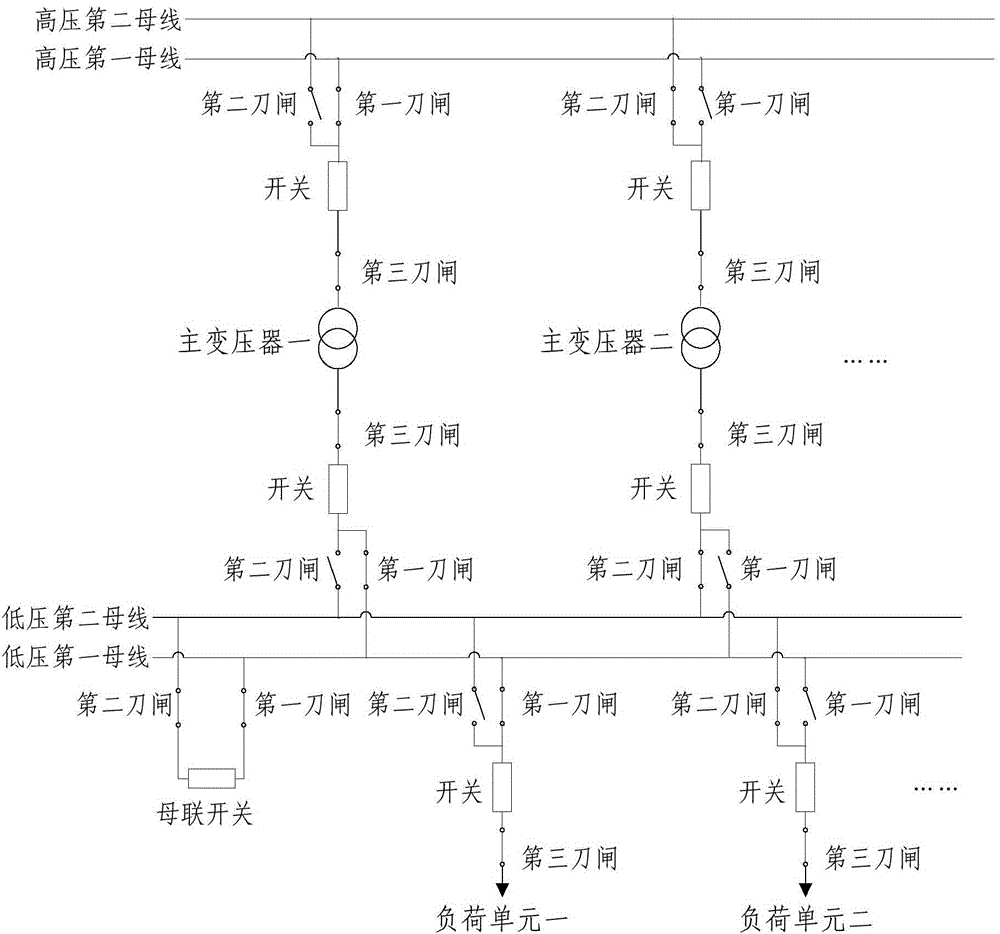
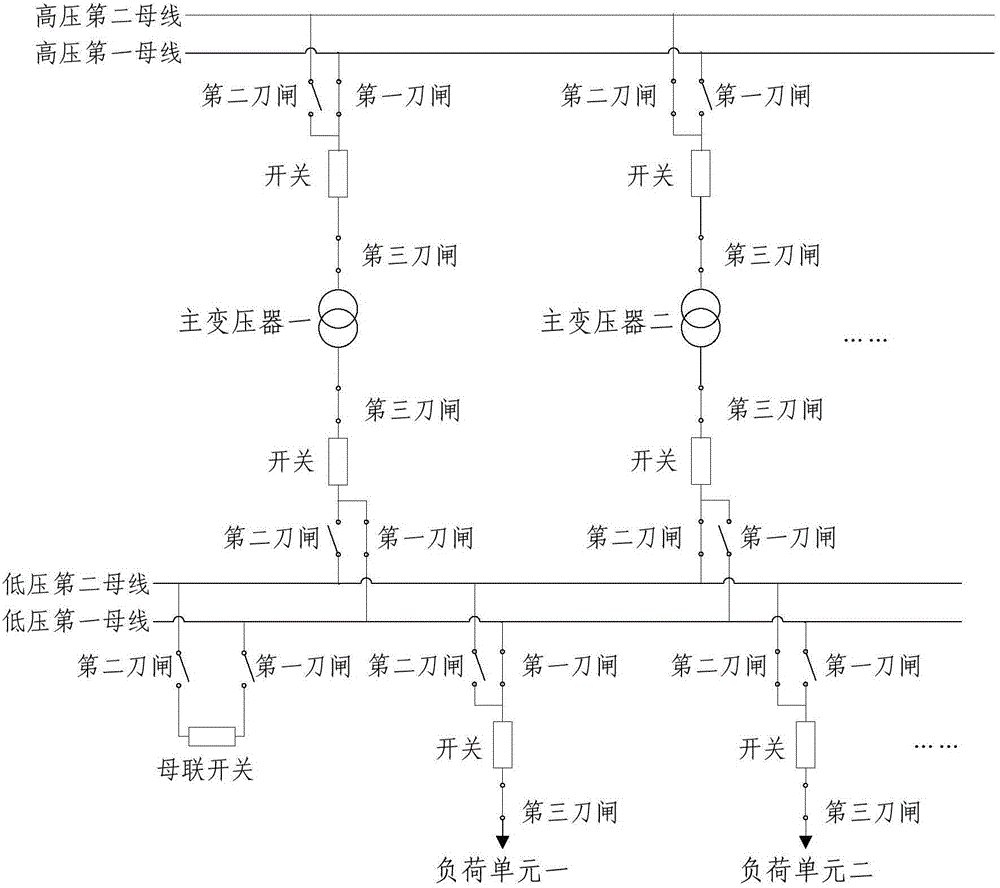
ActiveCN104638769ARealize automatic adjustmentAvoid the risk of false load removalCircuit arrangementsInformation technology support systemTime informationLoad Shedding
The invention provides a load shedding method and system for a safety automatic device based GOOSE information. The method comprises the following steps: controlling the safety automatic device to acquire the real-time circuit information of a main wiring of a transformation station via a GOOSE network; determining electric regions to which low-voltage side buses, main transformers and load units belong respectively in the transformation station according to the circuit information; adjusting load units adjusted and removed in each load shedding strategy of the safety automatic device according to the electric regions to which the low-voltage side buses, the main transformers and the load units belong. According to the scheme of the invention, automatic adjustment of the load shedding strategy of the safety automatic device for a digital transformer station can be realized, the risk of wrong load removal of the safety automatic device is avoided, and the correctness and reliability of the strategy of the safety automatic device are effectively ensured.
Owner:POWER DISPATCHING CONTROL CENT OF GUANGDONG POWER GRID CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com