Two-party collaborative signature method based on SM2 algorithm for resisting energy analysis attack
An energy analysis attack and signed message technology, applied to the public key and key distribution of secure communication, can solve the problems of signature algorithm failure, security risks, parameter generation errors, etc., to ensure correctness and validity, and resist energy analysis. The effect of attacking, ensuring correctness and validity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
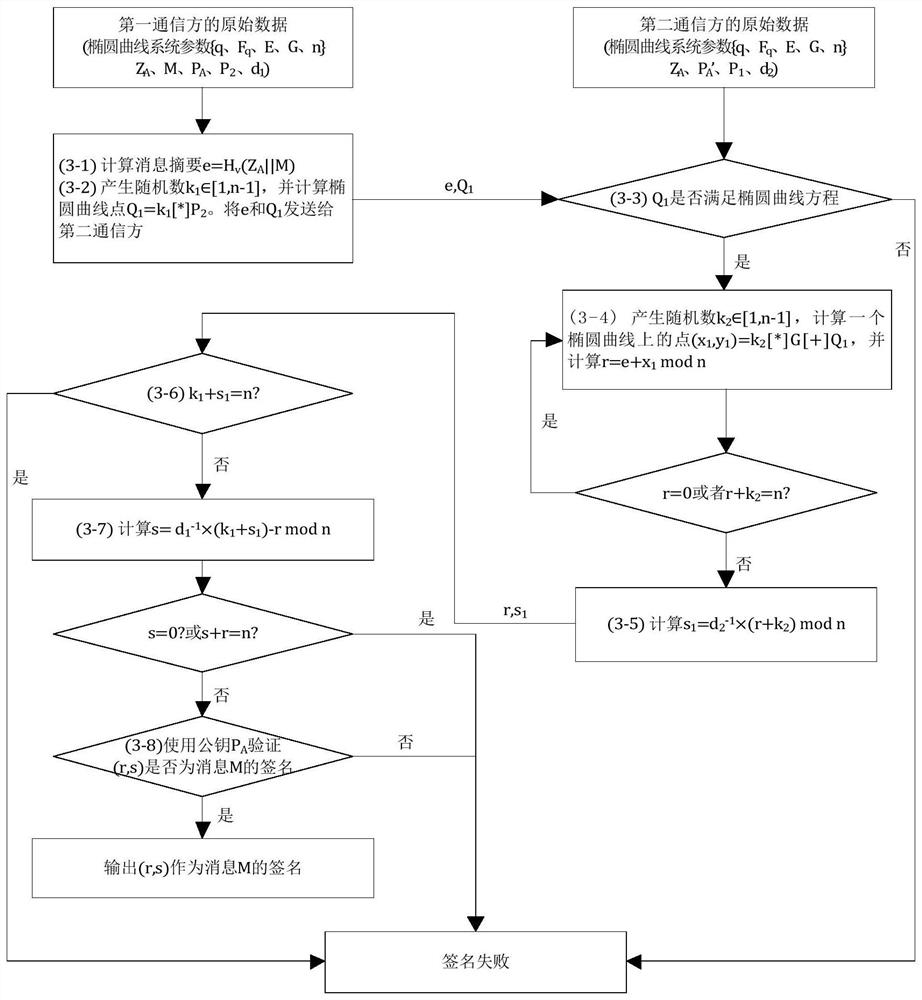
[0050] The two-party cooperative signature method based on SM2 against energy analysis attack proposed by the present invention comprises the following steps:
[0051] (1) User A, the first communication party and the second communication party jointly discuss the public parameters required to generate the signature process, and the public parameters include the elliptic curve related parameters q and F of the SM2 algorithm q . q is a finite field containing q elements, E is an elliptic curve defining Fq, and G is a base point on an elliptic curve of order n;
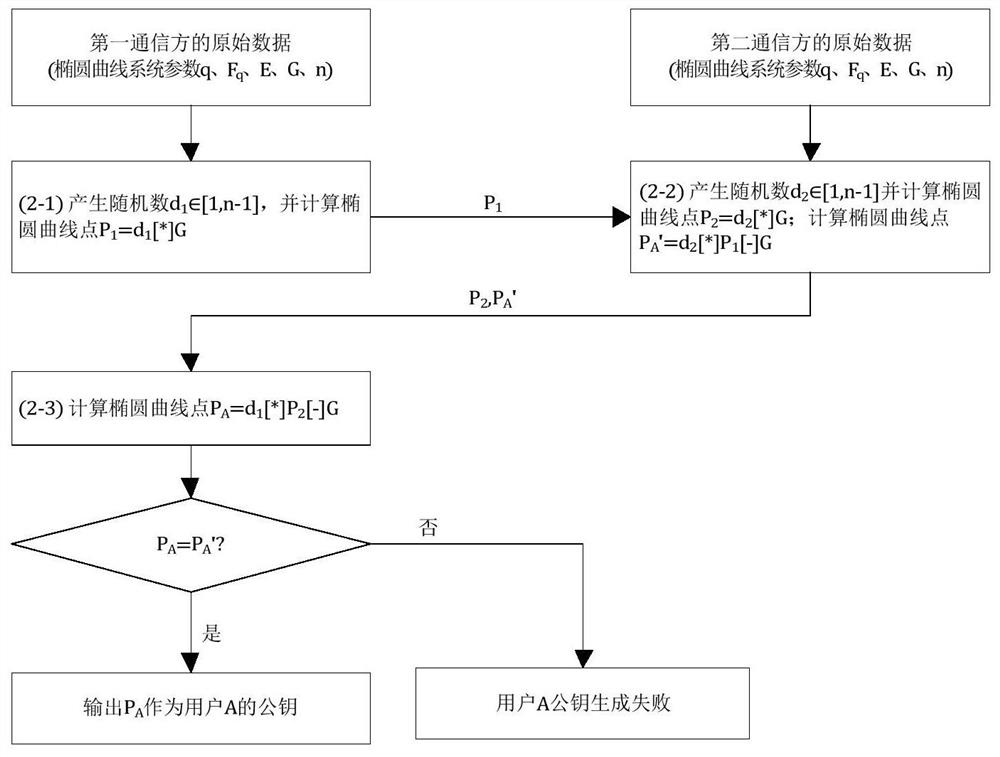
[0052] (2) The first communication party and the second communication party respectively generate their own sub-keys and jointly generate the public key of user A. The flow chart is as follows figure 1 shown, including the following steps:
[0053] (2-1) The first communication party uses a random number generator to generate a random number d 1 , d 1 ∈[1,n-1], and the random number d 1 As the sub-private key of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com