Fraud call detection method and device
A detection method and call list technology, which is applied to security devices, telephone communications, electrical components, etc., can solve problems such as poor operability, weak practicability of fraudulent calls, and inability to adapt to types and methods of fraud, and achieve operability strong effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
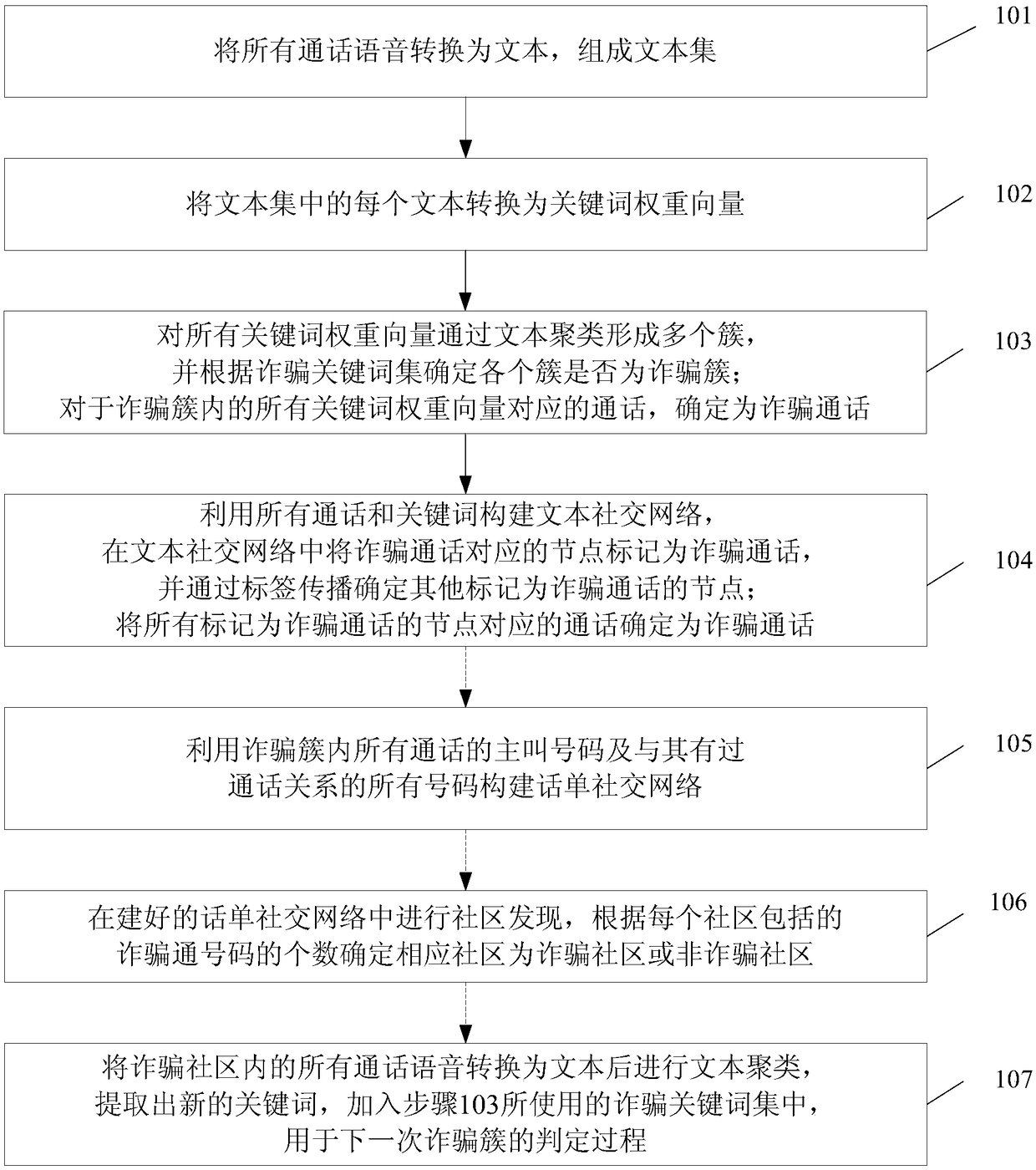
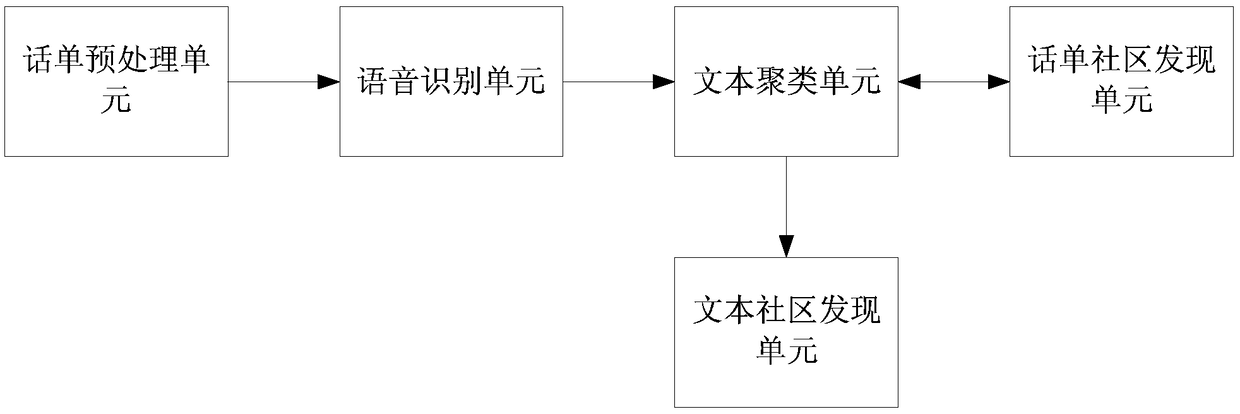
[0040] In order to make the purpose, technical means and advantages of the present application clearer, the present application will be further described in detail below in conjunction with the accompanying drawings.
[0041] Nodes in complex networks identify individuals in the system, and edges identify relationships between individuals, such as social network, food chain, World Wide Web, urban transportation network, and power grid. Community structure is a common feature in complex networks. Communities reflect the local characteristics of individual behaviors in the network and their interrelationships. The entire complex network is composed of many communities. Community discovery is a complex and meaningful process that plays an important role in studying the properties of complex networks. In recent years, the discovery and analysis of community structures in complex networks has attracted the attention of many scholars, and many community discovery algorithms have als...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com