Pseudo base station identification and defense method and terminal
A pseudo base station and terminal technology, applied in the field of communication, can solve the problems of 3/4G pseudo base stations that cannot be authenticated and cannot send spam or fraudulent text messages, so as to improve the level of security access, improve security, and be highly targeted Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0048] see figure 2 , Embodiment 1 of the present invention provides a method for defending against a fake base station, and the method is executed by a terminal. The terminal (or terminal, user equipment) here refers to the equipment corresponding to the network side equipment, which may include mobile phones, tablet computers, PCs and other various wireless communication services of various generations of operators (such as 2G, 3G, 4G) devices. "Network side equipment" refers to the equipment provided by the operator to cooperate with the terminal to complete wireless communication, which may include base stations and various core network side equipment. In this application, "pseudo-base stations" also belong to network-side equipment and are provided by criminals.
[0049] It should be noted that, in each embodiment of the present invention, for the terminal, it does not care about the specific hardware and software implementation of the network-side device, and the term...
Embodiment 2
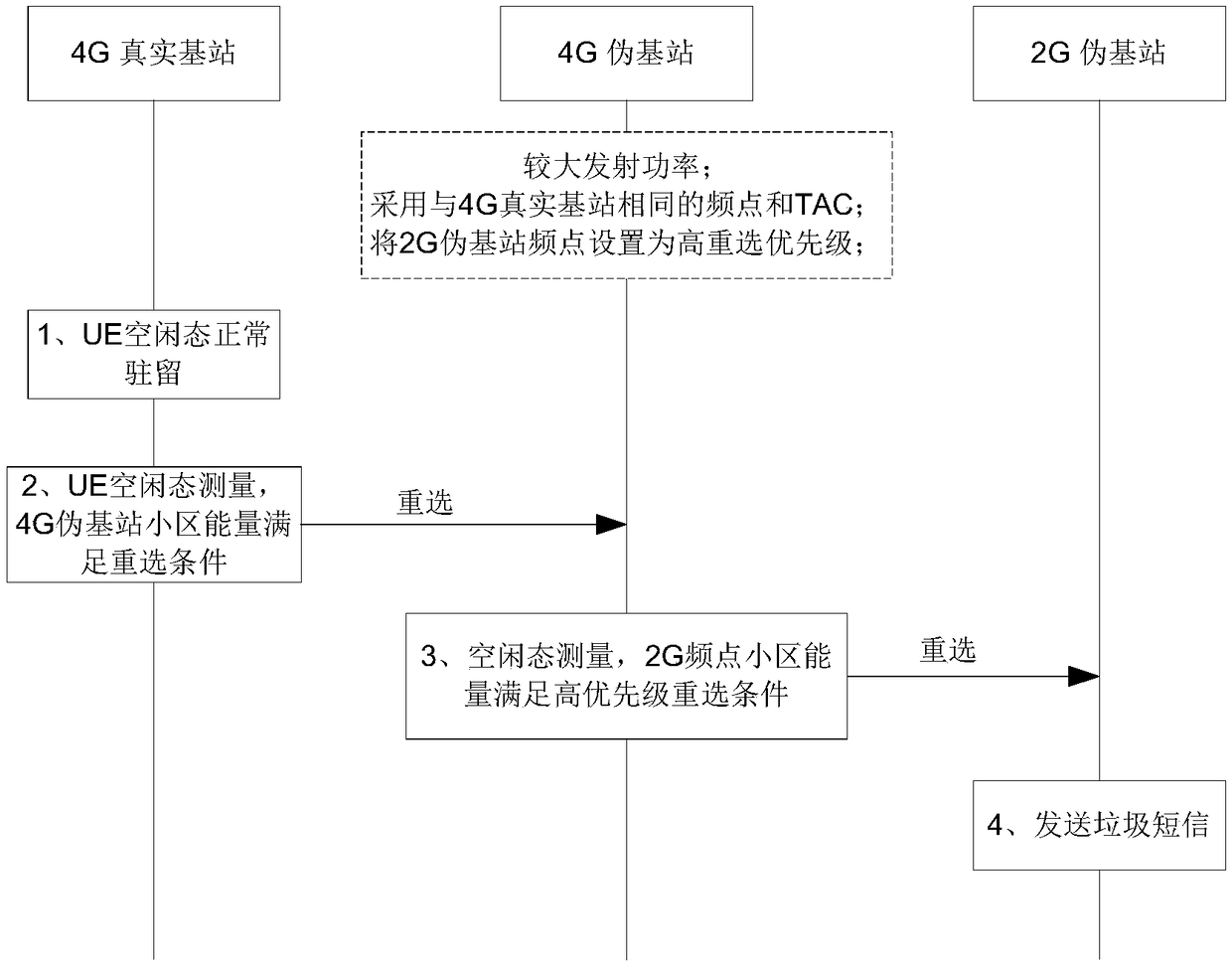
[0065] Based on the foregoing embodiments, this embodiment introduces system message configuration. It can be seen from the above-mentioned embodiments that in order to enable the terminal to reselect preferentially or select the pseudo base station itself when performing cell reselection (hereinafter referred to as "reselection") or cell selection (hereinafter referred to as "selection"), the pseudo base station will intentionally set the system The value of the message configuration is configured as a value for priority reselection or selection, and the range of this value is different from the normal value. It is an abnormal value. Therefore, when such an abnormal configuration is detected, there is a large The probability is caused by the pseudo base station, which can be preliminarily judged as a pseudo base station (referred to as "candidate pseudo base station" in the present invention). Various examples will be used to illustrate in detail below. For the convenience of...
Embodiment 3
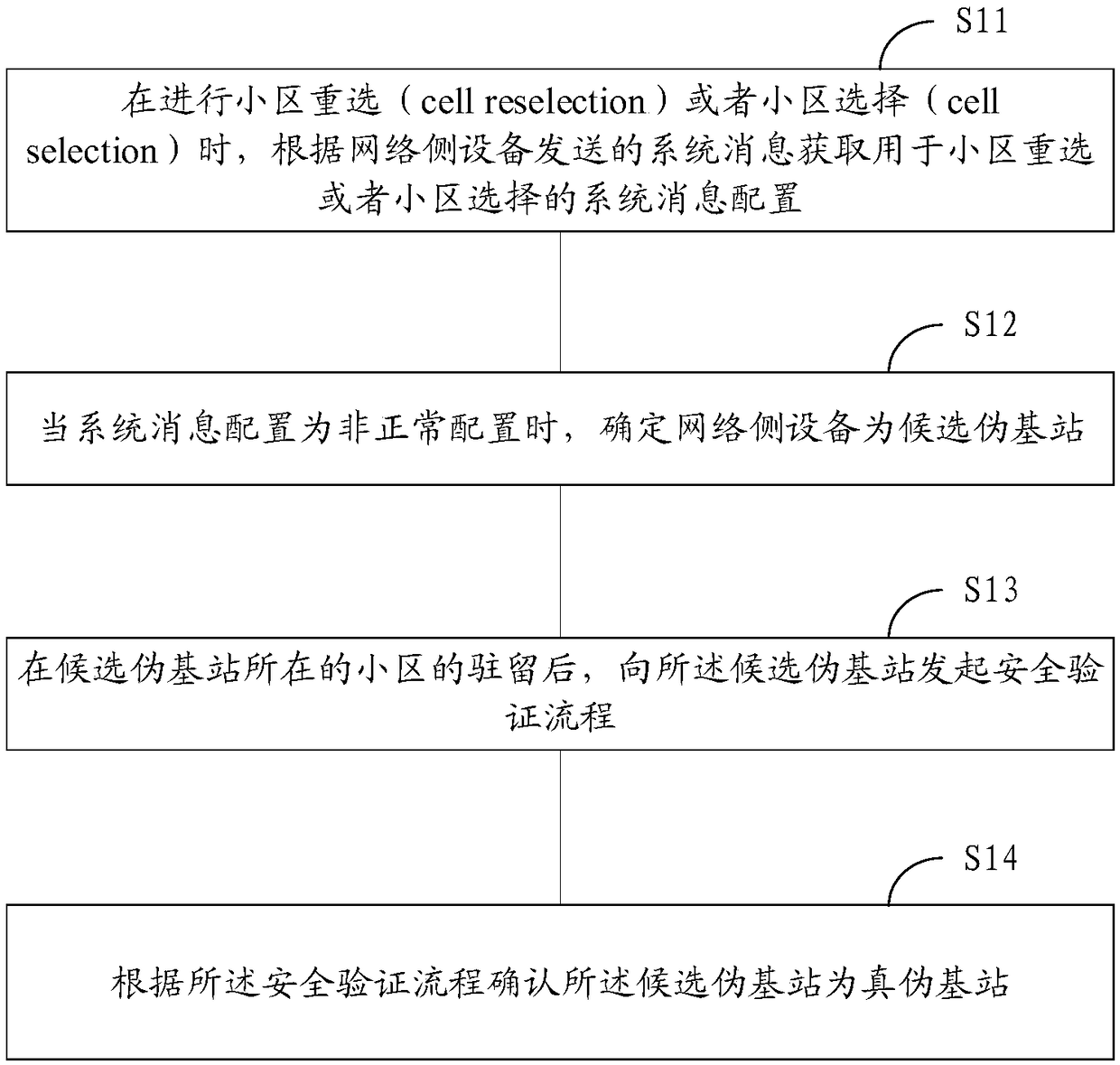
[0103] Based on the above embodiments, after the candidate pseudo base station is determined, an implementation manner is to directly regard the candidate pseudo base station as a real pseudo base station, and then start various defense measures in Embodiment 4. In this embodiment, in order to prevent misjudgment, the various defense measures in the fourth implementation are not directly implemented, but the security verification process is further initiated, and the candidate pseudo base station is further confirmed according to the security verification process. Defensive measures are implemented after the real and fake base stations are detected.
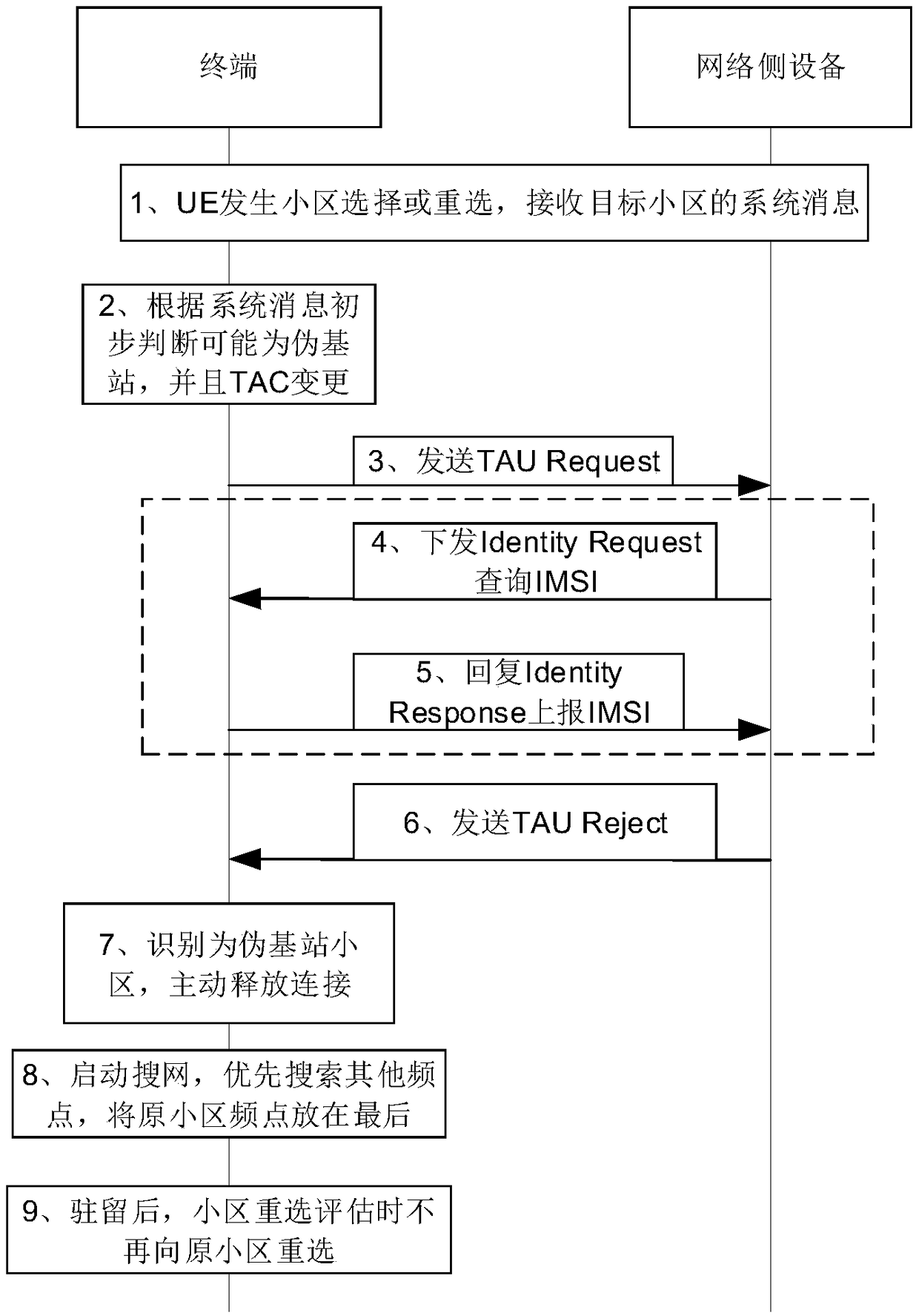
[0104] This embodiment specifically introduces the NAS process. After the terminal determines that the network-side device interacting with it (in this embodiment, also referred to as "the network") is a candidate pseudo base station through various methods mentioned in the above-mentioned embodiments, the terminal may choose to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com