Identity authentication method and apparatus, terminal device, and storage medium
A technology of identity authentication and ID card, which is applied in the fields of devices, terminal equipment and storage media, and identity authentication methods, can solve problems such as large manpower consumption, heavy audit workload, and uselessness, so as to enhance rigor, safety, and guarantee Legitimate interests, the effect of reducing labor costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
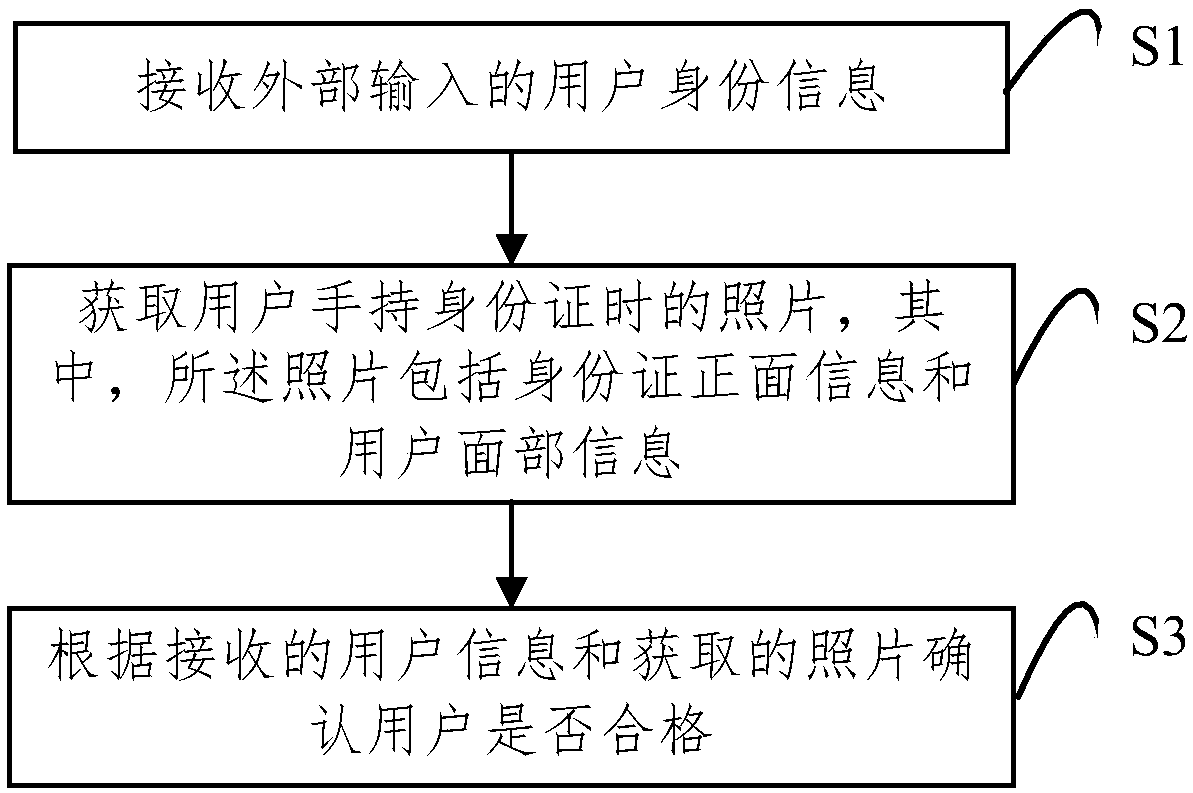
[0043] figure 1 It is a flow chart of the identity authentication method provided by Embodiment 2 of the present invention. According to different requirements, the execution sequence in the flowchart can be changed, and some steps can be omitted.
[0044] In this embodiment, the identity authentication method can be applied to a server, and the function for secure payment provided by the method of the present invention can be directly integrated on the electronic device, or a software development kit (Software Development Kit, SDK) runs on the server.
[0045] Such as figure 1 As shown, the identity authentication method specifically includes the following steps. According to different requirements, the order of the steps in the flowchart can be changed, and some steps can be omitted.
[0046] S1. Receive user identity information input from the outside.
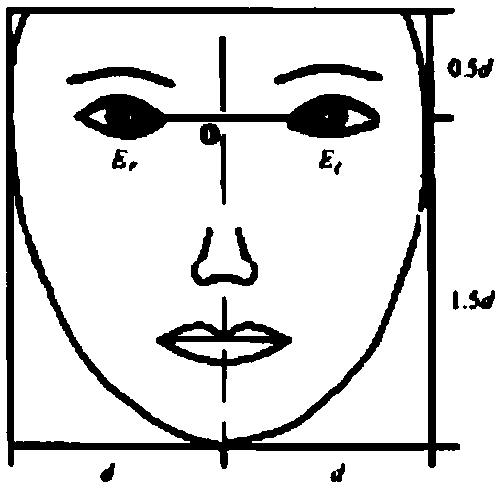
[0047]In this embodiment, the user identity information input from the outside may be received through the input and ...
Embodiment 3
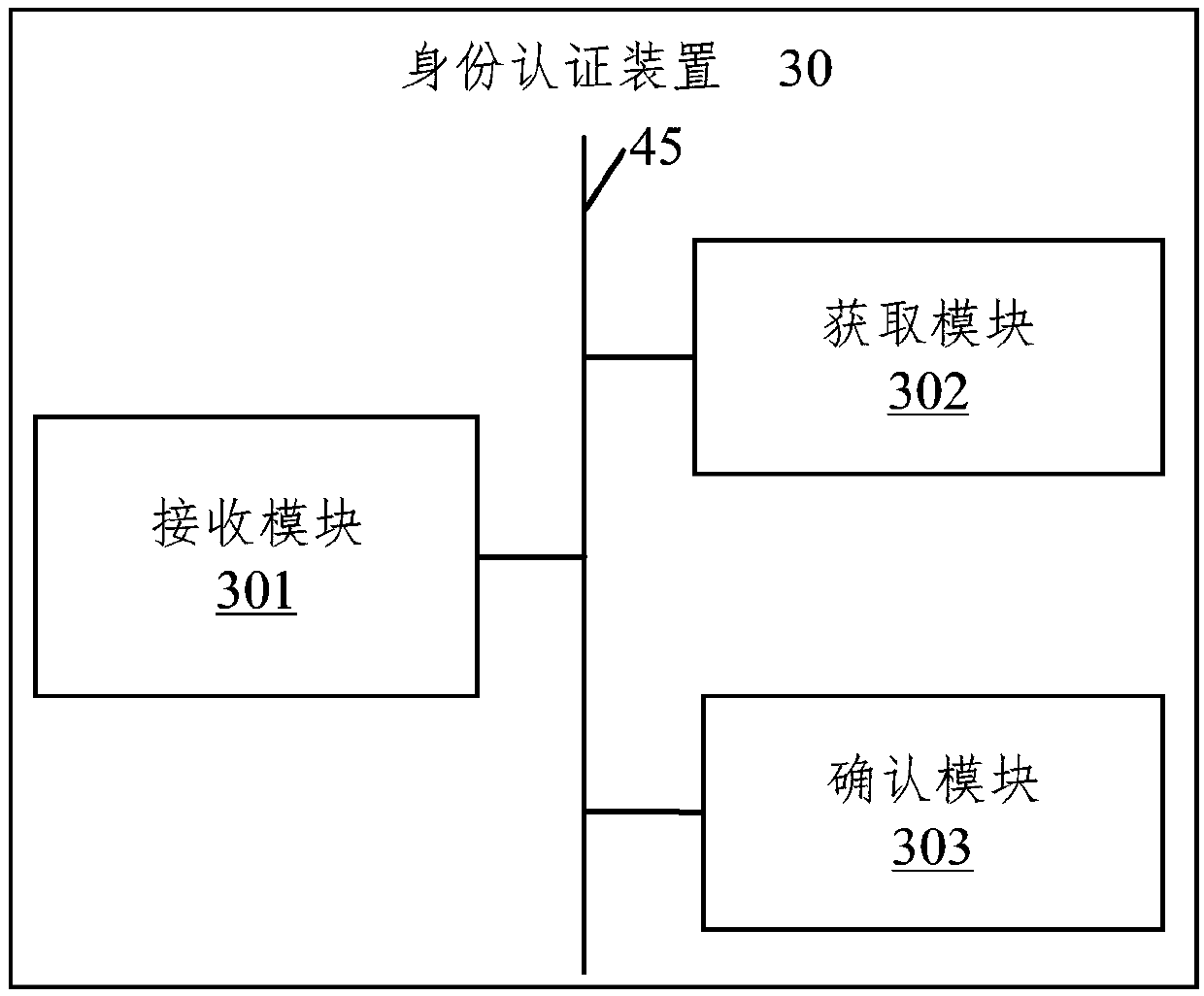
[0093] image 3 It is a functional block diagram of a preferred embodiment of the identity authentication device of the present invention.
[0094] In some embodiments, the identity authentication device 30 runs in a terminal device. The identity authentication device 30 may include a plurality of functional modules composed of program code segments. The program codes of each program segment in the identity authentication device 30 can be stored in a memory, and executed by at least one processor to execute (see figure 1 and its related description) identity authentication function.
[0095] In this embodiment, the identity authentication device 30 can be divided into multiple functional modules according to the functions it performs. The functional modules may include: a receiving module 301 , an acquiring module 302 and a confirming module 303 . The module referred to in the present invention refers to a series of computer program segments that can be executed by at leas...
Embodiment 4
[0141] Figure 4 It is a schematic diagram of a terminal device provided in Embodiment 4 of the present invention.
[0142] The terminal device 4 includes: a communication unit 41 , a memory 42 , at least one processor 43 , a computer program 44 stored in the memory 42 and executable on the at least one processor 43 , and at least one communication bus 45 .
[0143] When the at least one processor 43 executes the computer program 44, the steps in the above embodiment of the method for intelligently recognizing pictures are realized.
[0144] Exemplarily, the computer program 44 may be divided into one or more modules / units, and the one or more modules / units are stored in the memory 42 and executed by the at least one processor 43, To complete the present invention. The one or more modules / units may be a series of computer program instruction segments capable of accomplishing specific functions, and the instruction segments are used to describe the execution process of the co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com