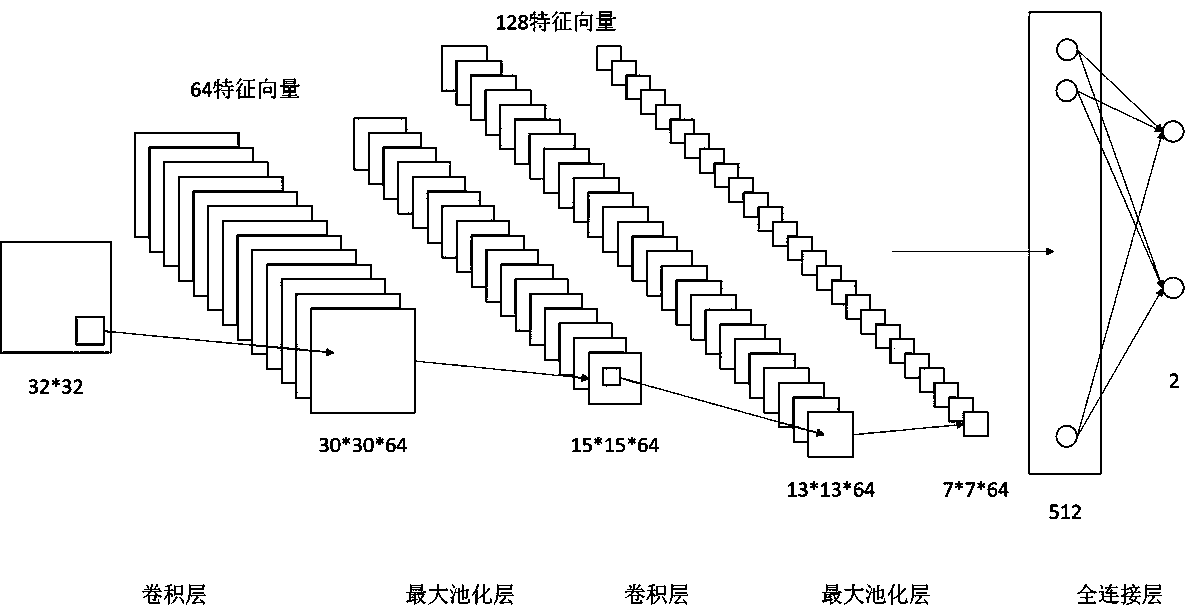
HTTP tunnel Trojan horse detection method based on deep learning
A deep learning and detection method technology, applied in the field of HTTP tunneling Trojan detection based on deep learning, can solve the problems of high false positive rate or false negative rate, lack of versatility, insufficient information utilization, etc. The effect of low reporting rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0032] Embodiment 1: First, capture network traffic data packets at the network egress. Then, check and verify the captured data packets from two aspects: one is to verify the headers of each layer of the data packets, keep the data packets that meet the protocol specification, and set the filtering rules to discard the data packets except HTTP packets; The second is to filter the data packets communicated between the hosts in the internal network, and keep the data packets communicated between the internal network hosts and the external network. The internal network refers to the detection object network of the Trojan horse communication detection system. Finally, retain the data packets that have passed the inspection, extract the packet summary information and the transport layer payload, and store them in the data packet queue.
[0033] Take out the data packets in turn from the data packet queue, read the source IP address field, destination IP address field, protocol typ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com