Secure Communication Method Based on Packet Vertical Random Split and Path Separation Transmission
A technology of secure communication and segmentation, which is applied in the transmission system, digital transmission system, data exchange through path configuration, etc., can solve the problem of being unable to resist quantum computing deciphering and analysis attacks, and achieve the goal of improving transmission security and low investment cost Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
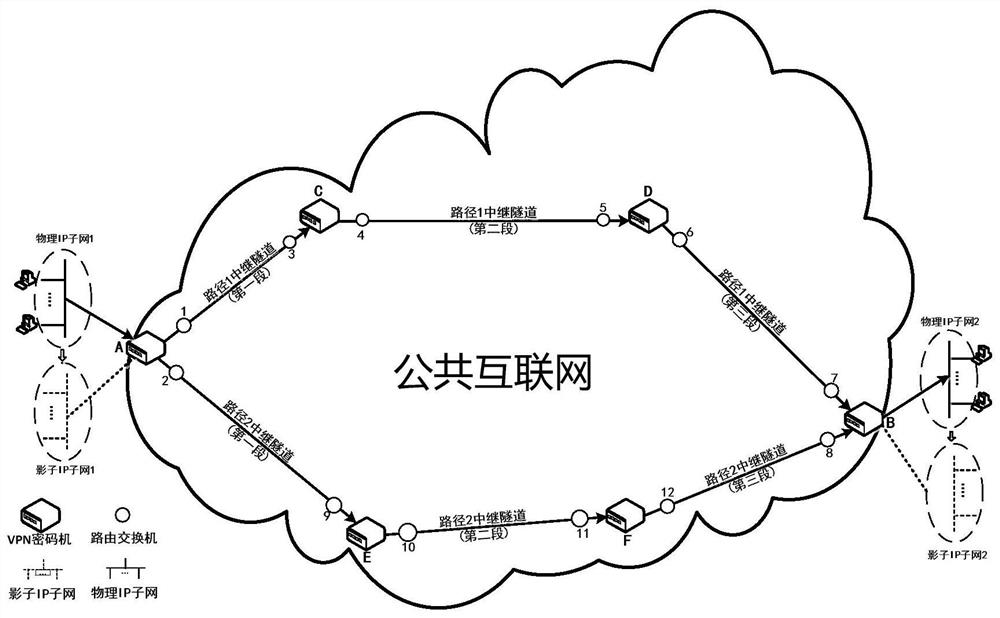
[0036] (1) Technical principle scheme
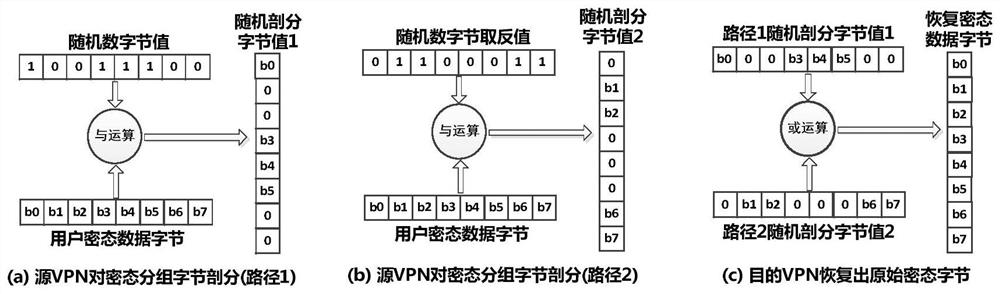
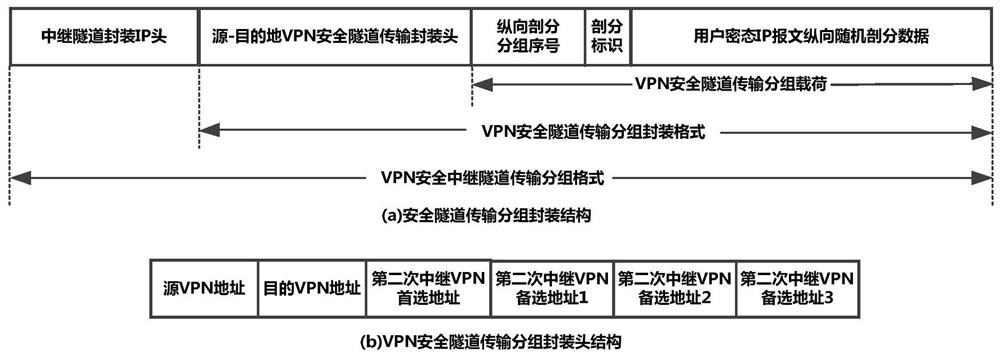
[0037] The core concept of the new high-security and confidential communication method proposed by the present invention is mainly based on the transmission control technology of group vertical random segmentation and path separation, and adopts triple security tunnel encapsulation and three-segment security tunnel relay. For each IP plaintext group, the encryption protection of the end-end security tunnel between the source-destination host, the longitudinal random segmentation of the encrypted IP message at the user end, and the communication encryption protection of the source-destination VPN security tunnel , path separation transmission and encryption protection of each safe relay tunnel, a total of five safe and confidential communication protection mechanisms. And through the vertical random partition and path separation transmission control mechanism, the security of the end-to-end key distribution protocol between user hosts is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com