A large-capacity IP address interception method and device
An IP address, high-capacity technology, applied in the field of network security, can solve problems such as rising access delays and destroying user experience, and achieve the effects of reducing usage, improving comprehensiveness, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
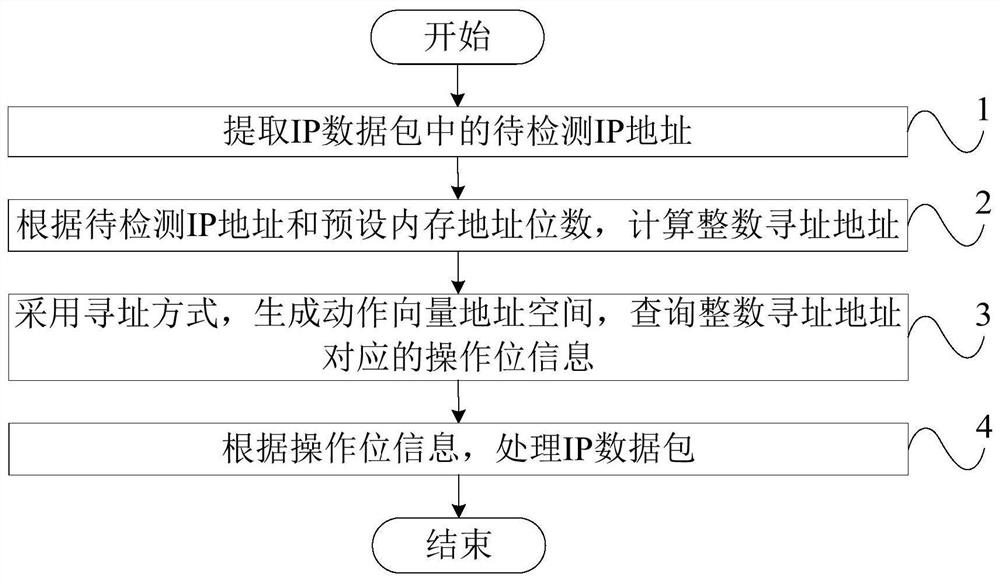
[0022] Such as figure 1 As shown, the present embodiment provides a large-capacity IP address interception method, comprising: Step 1, extracting the IP address to be detected in the IP data packet, wherein any IP address to be detected includes a source IP address and a destination IP address;
[0023] Specifically, in the current standard "server-client" network model, the "server" that provides website services to the outside world is the destination, and the host that carries the common user "client" is the source. When a malicious network attacker attacks and accesses a server, it will inevitably expose its own fixed IP address. By analyzing the data packet and extracting the source IP address and destination IP address fields according to the transmission protocol structure, on the one hand, the source IP address is used to prevent attackers from submitting attack payloads to the server. On the other hand, use the destination IP address to prevent the server from initia...
Embodiment 2
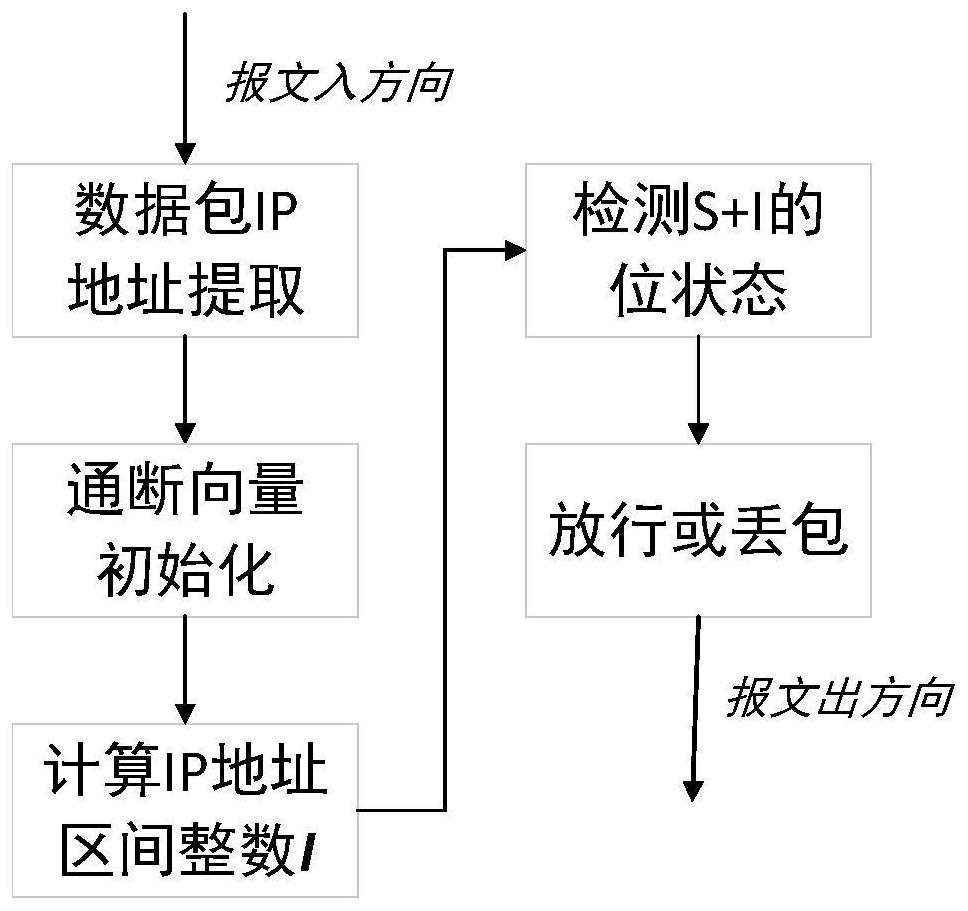
[0052] Such as figure 2 As shown, this embodiment provides another method for intercepting large-capacity IP addresses. First, the source IP address and destination IP address in the IP data packet should be extracted. The IP address can be regarded as an integer in the interval [0,4294967296), which is denoted as 1 hereinafter. May wish to set the attacker's IP address as 1.2.3.4, then its corresponding IP address I is:
[0053] I=(((1*256+2)*256+3)*256+4)=16909060.
[0054] A bit-addressable motion vector starts at address S. Then the address space where the IP address I is located at [S, S+4294967296) is the memory space occupied by the motion vector. In the initial all-pass state, it is advisable to define "the bit state is 0" as the pass state, and "the bit state is 1" as the packet loss state. For the attacker's IP address I, the bit status of the address S+I can be detected to determine whether the IP data packet is allowed to pass.
[0055] This method can reduce...
Embodiment 3
[0057] Such as image 3 As shown, the present embodiment provides a large-capacity IP address interception device 100, including: an address extraction module 101, a calculation module 102, an action decision module 103 and an action execution module 104; the address extraction module 101 is used to extract IP addresses to be detected, wherein any IP address to be detected includes a source IP address and a destination IP address;
[0058] Specifically, in the current standard "server-client" network model, the "server" that provides website services to the outside world is the destination, and the host that carries the common user "client" is the source. When a malicious network attacker attacks and accesses a server, it will inevitably expose its own fixed IP address. By analyzing the data packet and extracting the source IP address and destination IP address fields according to the transmission protocol structure, on the one hand, the source IP address is used to prevent a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com