A source node position privacy protection method based on Sink and a grid in a WSN
A privacy protection, source node technology, applied in location-based services, security devices, network topology, etc., can solve the problem of not being able to better protect the privacy of source node location, and achieve the goal of reducing communication overhead and increasing security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0067] The present invention will be further described below in conjunction with accompanying drawing.
[0068] Step (1) Network initialization:
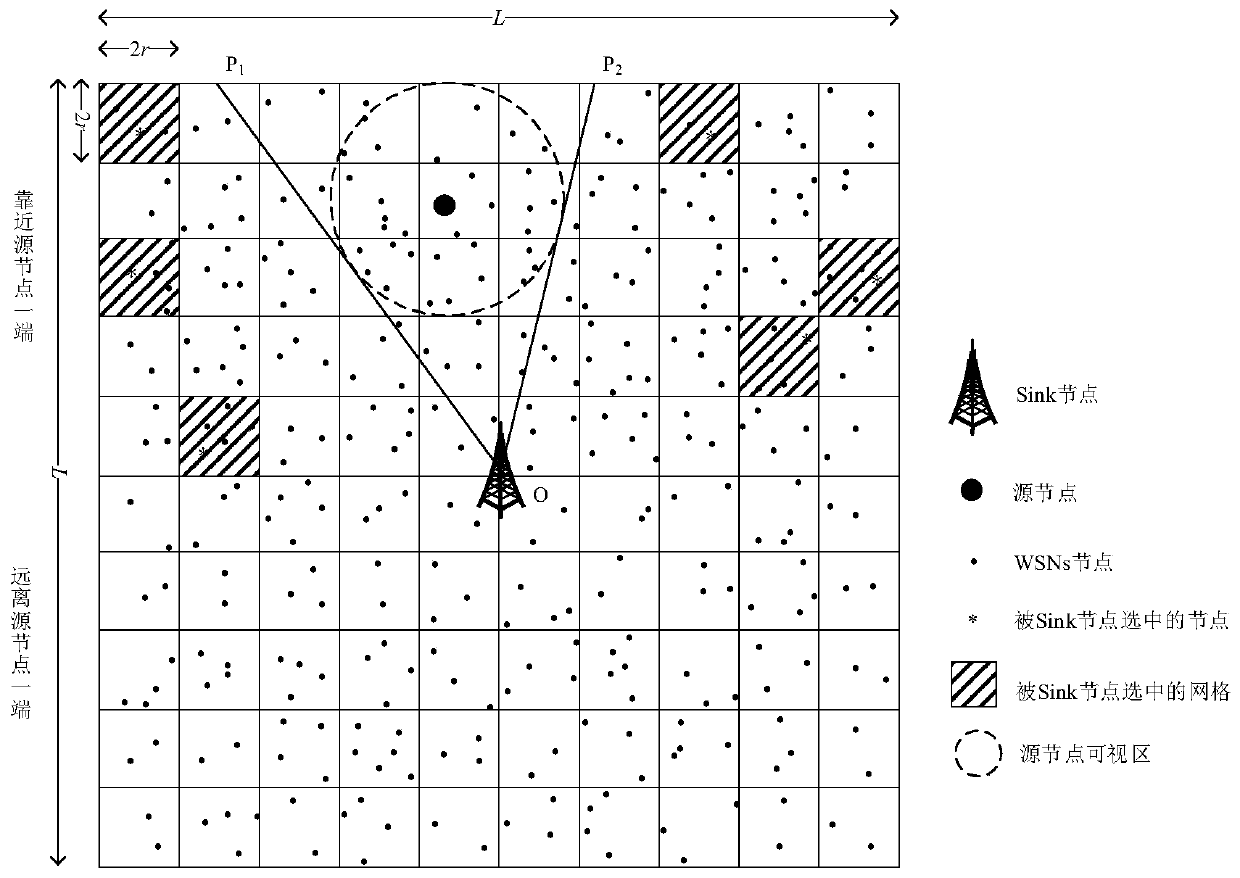
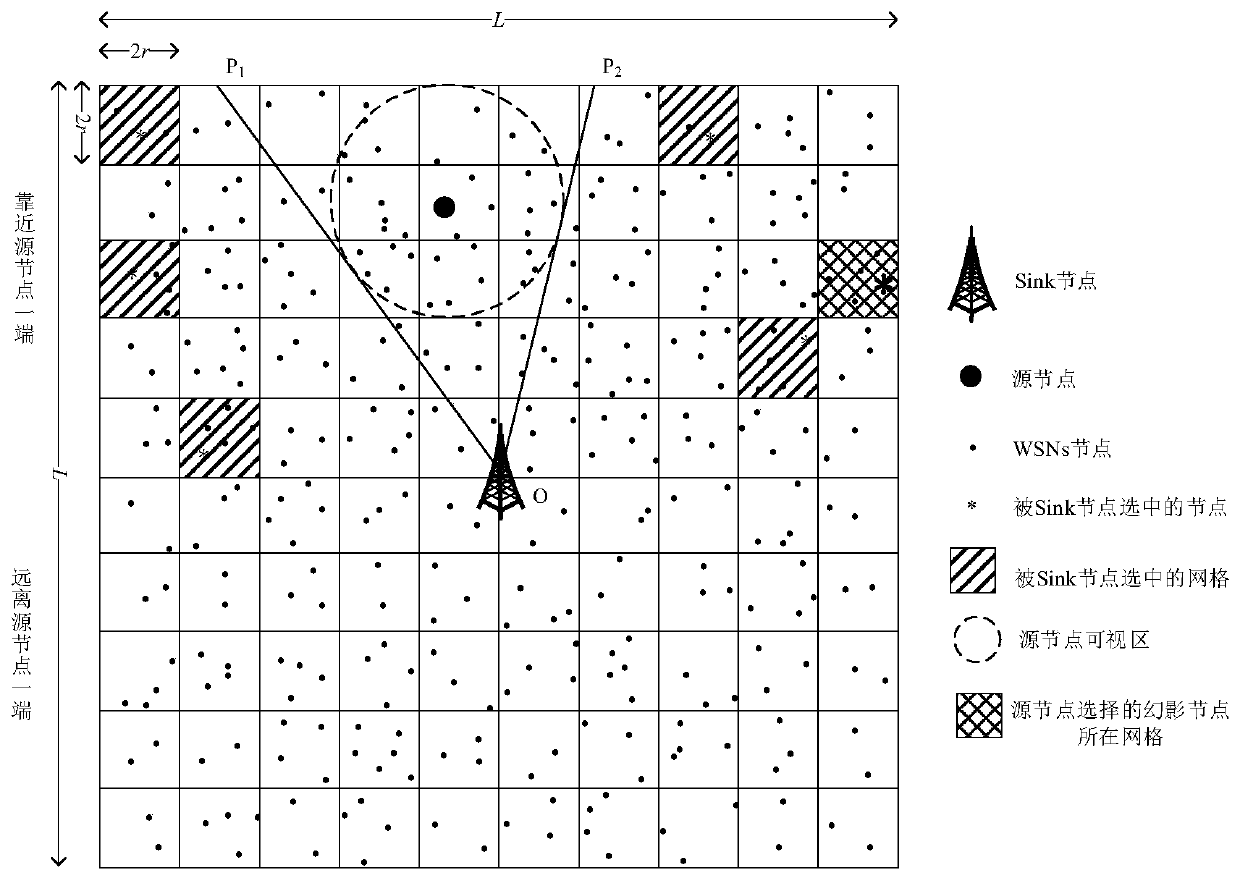
[0069] Pre-deploy the nodes in the network. After the pre-deployment is completed, each node can master its own basic information. The basic information of itself includes the identity ID number and the grid number; The hop count of the Sink node Hop Sender,sink , Send a broadcast message with three parameters of the grid number where the node is located;
[0070] After the network initialization is completed, each node obtains the ID number of the neighbor node, the grid number and the minimum hops away from the Sink node, and according to the minimum hops between the node itself and the Sink node and the minimum hops between the neighbor node and the Sink node, the Neighbor nodes are divided into three categories: near-hop neighbor nodes (minimum hops from the node itself to the Sink node > minimum hops from the neighbor node to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com