Third-party-based request encryption method and system between user and server
An encryption method and encryption system technology, applied in the field of computer network security verification access, can solve the problems of increasing the size of the third-party APP, data leakage, and high development costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
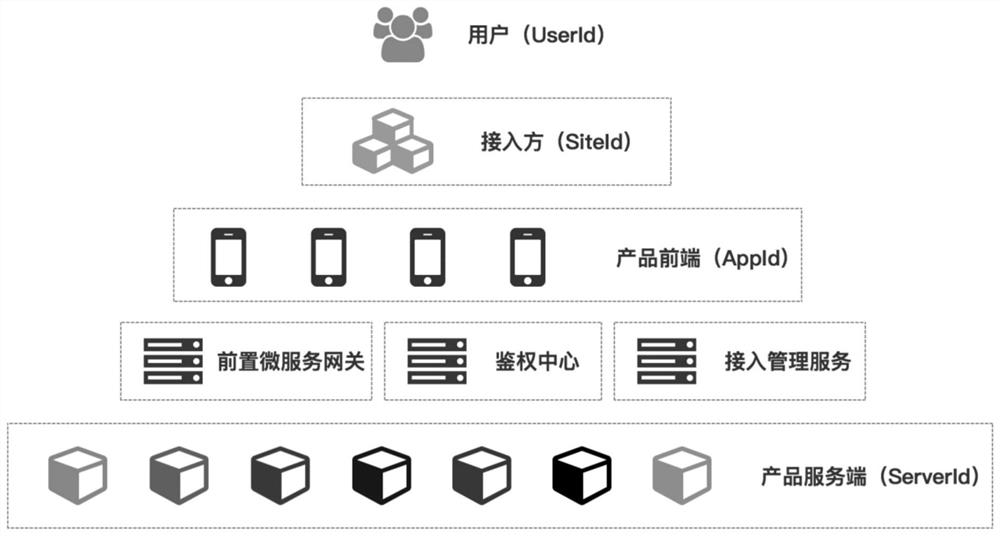
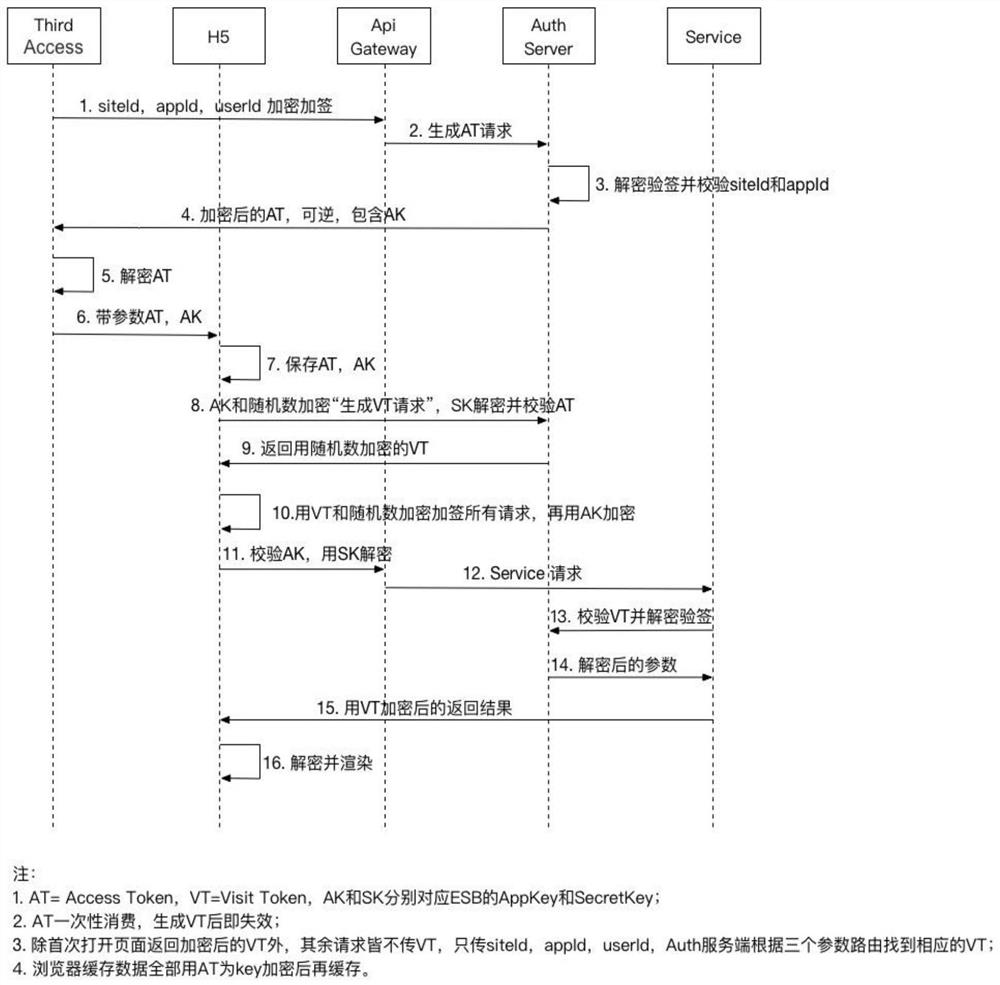
[0035] Such as Figure 1 to Figure 2 As shown, the third-party security access method in the form of H5 application of the service provider includes the third-party backend, the H5 end of the service provider, the gateway server of the service provider, the authentication end of the service provider, and the backend of the service provider. Include the following steps:
[0036] A. The user of the third-party client clicks an entry request to enter the service application provided by the service provider, and notifies the third-party backend of the message;
[0037] B. The third-party backend initiates a request to the service provider to generate an access key AT (Access Token, referred to as AT) through the service provider gateway server, and the service provider generates the access key AT and passes it through the service provider gateway The server returns to the third-party backend;
[0038] C. After the third-party backend receives the encrypted AT, it decrypts the AT...
Embodiment 2
[0045] The request encryption system between the user and the service provider based on the third party, including the third-party backend, the H5 terminal of the service provider, and the gateway server of the service provider, among which:
[0046] The third-party backend is used to receive the message that the user of the third-party client clicks on an entry to request to enter the service application provided by the service provider, and initiates the process of generating the access key AT to the service provider through the service provider gateway server The request is also used to decrypt the AT after receiving the encrypted AT, reverse the AT to obtain the AK, and open the URL address of the service provider's H5 terminal in the third-party webView through the parameters AT and AK;
[0047] The H5 end of the service provider is used by the service provider to generate the access key AT and send it back to the third-party backend through the service provider’s gateway ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com