Malicious Android software detection method for dynamic code loading based on hybrid analysis
A technology for malware and detection methods, applied in computer security devices, instruments, computing, etc., can solve the problem that the possibility of malware spreading cannot be ignored, and achieve the effect of improving accuracy and effectiveness and protecting security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
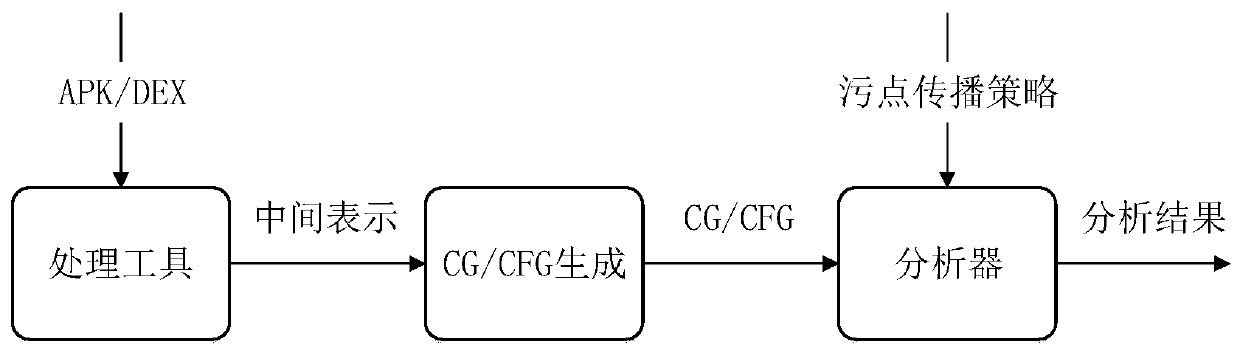
[0027] The invention realizes the real-time monitoring of the security of the external code dynamically loaded by the Android application.
[0028] Technical scheme of the present invention is as follows:
[0029] 1) Intercept dynamically loaded code
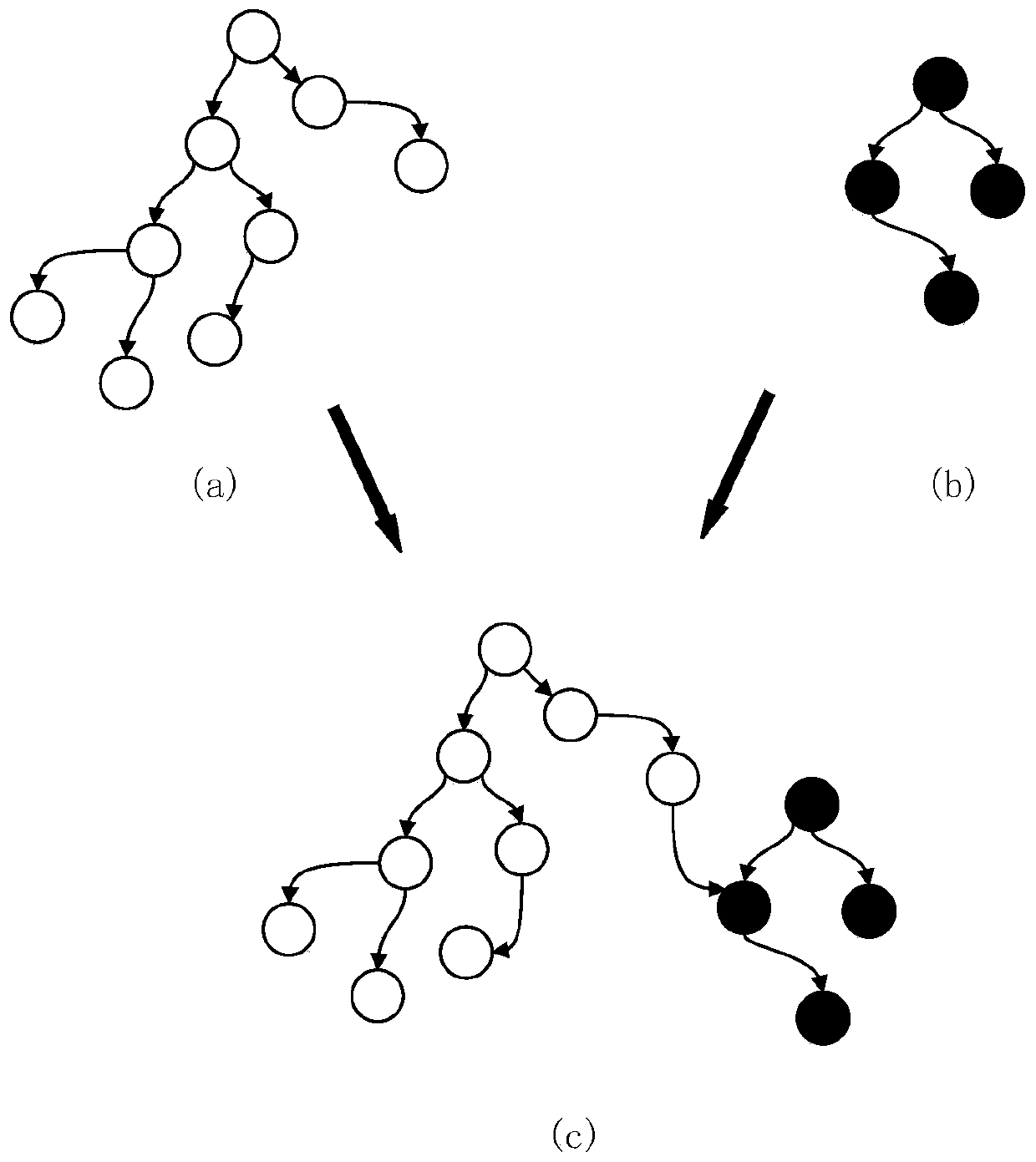
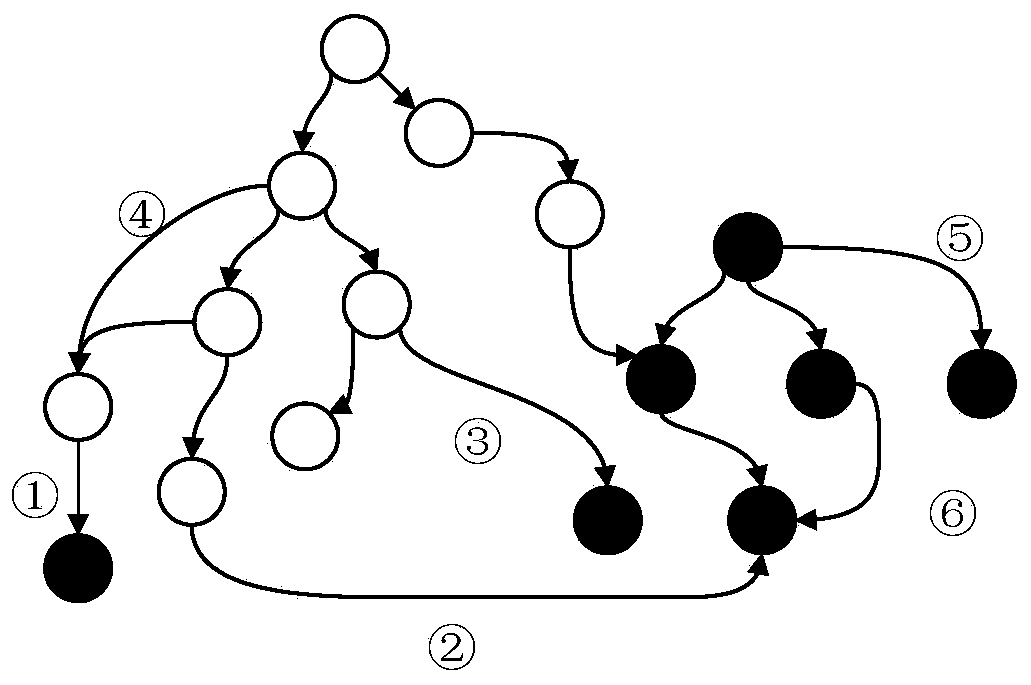
[0030] In order to detect the security of the code dynamically loaded by the application at runtime, an interception module is placed on the user's device. This module uses the API Hook technology, which can be used to modify the entry of the code to load the API method, and point the entry to our custom method. In the defined method, we modified the original code logic of the method. When the application loads code dynamically using the loader, the Hook module can intercept and extract the dynamically loaded code. The intercepted code can be sent to the server for auditing.
[0031] After intercepting the dynamic code loading behavior of the application, first extract the code address to be loaded by the application, and fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com